Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft HoloLens 2 devices support the Windows Defender Application Control (WDAC) CSP, which replaces the AppLocker CSP.
Using Windows PowerShell and Microsoft Intune, you can use the WDAC CSP to allow or block specific apps from opening on Microsoft HoloLens 2 devices. For example, you might want to allow or prevent an app from opening on HoloLens 2 devices in your organization.
This feature applies to:
- HoloLens 2 devices running Windows Holographic for Business
- Windows
The WDAC CSP is based on the Windows Defender Application Control (WDAC) feature. You can also use multiple WDAC policies.
This article shows you how to:
- Use Windows PowerShell to create WDAC policies.
- Use Windows PowerShell to convert the WDAC policy rules to XML, update the XML, and then convert the XML to a binary file.
- In Microsoft Intune, create a custom device configuration profile, add this WDAC policy binary file, and apply the policy to your HoloLens 2 devices.
In Intune, you must create a custom configuration profile to use the Windows Defender Application Control (WDAC) CSP.
Use the steps in this article as a template to allow or deny specific apps from opening on HoloLens 2 devices.
Prerequisites
Be familiar with Windows PowerShell. For information on the execution policy options, go to Windows PowerShell about_Execution_Policies.
To configure the Intune policy, at a minimum, sign into the Intune admin center as a member of the Policy and Profile Manager built-in Intune role.
For information on the Intune built-in roles, and what they can do, go to:
Create a user group or devices group with your HoloLens 2 devices. For information on groups, go to User groups vs. device groups.
Step 1 - Create the WDAC policy using Windows PowerShell
This example uses Windows PowerShell to create a Windows Defender Application Control (WDAC) policy. The policy prevents specific apps from opening.
On your desktop computer, open the Windows PowerShell app.
Get information about the installed application package on your desktop computer and HoloLens:
$package1 = Get-AppxPackage -name *<applicationname>*For example, enter:
$package1 = Get-AppxPackage -name Microsoft.MicrosoftEdgeNext, confirm the package has application attributes:
$package1App details similar to the following attributes are shown:
Name : Microsoft.MicrosoftEdge Publisher : CN=Microsoft Corporation, O=Microsoft Corporation, L=Redmond, S=Washington, C=US Architecture : Neutral ResourceId : Version : 44.20190.1000.0 PackageFullName : Microsoft.MicrosoftEdge_44.20190.1000.0_neutral__8wekyb3d8bbwe InstallLocation : C:\Windows\SystemApps\Microsoft.MicrosoftEdge_8wekyb3d8bbwe IsFramework : False PackageFamilyName : Microsoft.MicrosoftEdge_8wekyb3d8bbwe PublisherId : 8wekyb3d8bbwe IsResourcePackage : False IsBundle : False IsDevelopmentMode : False NonRemovable : True IsPartiallyStaged : False SignatureKind : System Status : OkCreate a WDAC policy, and add the app package to the DENY rule:
$rule = New-CIPolicyRule -Package $package1 -DenyRepeat steps 2 and 3 for any other applications you want to DENY:
$rule += New-CIPolicyRule -Package $package<2..n> -DenyFor example, enter:
$package2 = Get-AppxPackage -name *windowsstore* $rule += New-CIPolicyRule -Package $package<2..n> -DenyConvert the WDAC policy to newPolicy.xml:
Note
You can block apps that are only installed on HoloLens devices. For more information, go to package family names for apps on HoloLens.
New-CIPolicy -rules $rule -f .\newPolicy.xml -UserPEsTo target all versions of an app, in newPolicy.xml, be sure
PackageVersion="65535.65535.65535.65535"is in Deny node:<Deny ID="ID_DENY_D_1" FriendlyName="Microsoft.WindowsStore_8wekyb3d8bbwe FileRule" PackageFamilyName="Microsoft.WindowsStore_8wekyb3d8bbwe" PackageVersion="65535.65535.65535.65535" />For
PackageFamilyNameRules, you can use the following versions:- Allow: Enter
PackageVersion, 0.0.0.0, which means "Allow this version and above". - Deny: Enter
PackageVersion, 65535.65535.65535.65535, which means "Deny this version and below".
- Allow: Enter
If you plan to deploy and run any apps that didn't originate from the Microsoft Store, such as line of business apps (see App Management), then explicitly allow these apps by adding their signer to the WDAC policy.
Note
Using WDAC and LOB apps is currently only available in Windows Insiders features for HoloLens.
For example, you plan on deploying
ATestApp.msix.ATestApp.msixis signed by theTestCert.cercertificate. Use the following Windows PowerShell script to add the signer to the WDAC policy:Add-SignerRule -FilePath .\newPolicy.xml -CertificatePath .\TestCert.cer -UserMerge newPolicy.xml with the default policy that's on your desktop computer. This step creates mergedPolicy.xml. For example, allow the Windows, WHQL signed drivers, and Store signed apps to run:
Merge-CIPolicy -PolicyPaths .\newPolicy.xml,C:\Windows\Schemas\codeintegrity\examplepolicies\DefaultWindows_Audit.xml -o mergedPolicy.xmlDisable the Audit mode rule in mergedPolicy.xml. When you merge, audit mode is automatically turned on:
Set-RuleOption -o 3 -Delete .\mergedPolicy.xmlEnable the InvalidateEAs on a reboot rule in mergedPolicy.xml:
Set-RuleOption -o 15 .\mergedPolicy.xmlFor information on these rules, go to Understand WDAC policy rules and file rules.
Convert mergedPolicy.xml to binary format. This step creates compiledPolicy.bin. In Step 2 - Create an Intune policy and deploy the policy to HoloLens 2 devices, you add this compiledPolicy.bin binary file to an Intune policy.
ConvertFrom-CIPolicy .\mergedPolicy.xml .\compiledPolicy.bin
Step 2 - Create an Intune policy and deploy the policy to HoloLens 2 devices
In this step, you create a custom device configuration profile in Intune. In the custom policy, you add the compiledPolicy.bin binary file you created in Step 1 - Create the WDAC policy using Windows PowerShell. Then, use Intune to deploy the policy to HoloLens 2 devices.
In the Microsoft Intune admin center, create a Windows custom device configuration profile.
For the specific steps, go to Create a custom profile using OMA-URI in Intune.
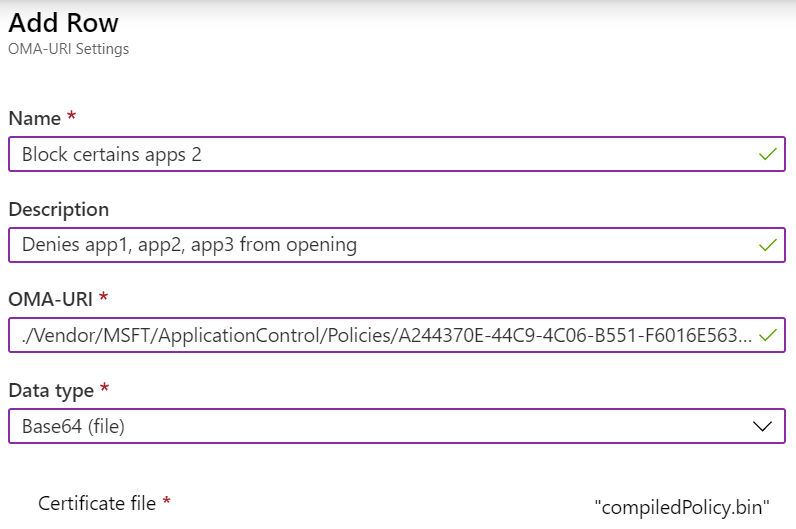
When you create the profile, enter the following settings:
OMA-URI: Enter
./Vendor/MSFT/ApplicationControl/Policies/<PolicyGUID>/Policy. Replace<PolicyGUID>with the PolicyTypeID node in the mergedPolicy.xml file you created in step 6.Using our example, enter
./Vendor/MSFT/ApplicationControl/Policies/A244370E-44C9-4C06-B551-F6016E563076/Policy.The policy GUID must match the PolicyTypeID node in the mergedPolicy.xml file (created in step 6).
The OMA-URI uses the ApplicationControl CSP. For information on the nodes in this CSP, go to ApplicationControl CSP.
Data type: Set to Base64 file. It automatically converts the file from bin to base64.
Certificate file: Upload the compiledPolicy.bin binary file (created in step 10).
Your settings look similar to the following settings:
When the profile is assigned to your HoloLens 2 group, check the profile status. After the profile successfully applies, reboot the HoloLens 2 devices.