Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Idle session timeout isn't available for Microsoft 365 operated by 21Vianet.
Use idle session timeout to configure a policy on how long users are inactive in your organization before they're signed out of Microsoft 365 web apps. This helps protect sensitive company data and adds another layer of security for end users who work on noncompany or shared devices.
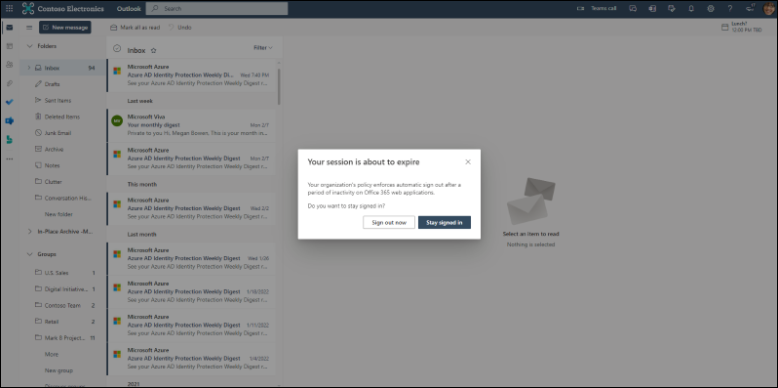
When a user reaches the set idle timeout session, they get a notification that they're about to be signed out. They have to select to stay signed in or they're automatically signed out of all Microsoft 365 web apps.
Important
Idle session timeout doesn't affect your Microsoft 365 desktop and mobile apps.
Turn on Idle session timeout
You must be a member of the Security admin, Application admin, or Cloud Application admin roles to see the idle session timeout setting. The Global admin role is required for initial activation of Idle Session Timeout. All other noted roles can deactivate and/or modify timeout duration settings.
In the Microsoft 365 admin center, select Org Settings -> Security & privacy tab and select Idle session timeout.
On the Idle Session Timeout, select the toggle to turn it on. You can choose a default setting or choose your own custom time. It takes a few minutes before idle session is turned on in your organization.
Note
If you set up idle session timeout policies for Outlook web app and SharePoint, turning on idle session timeout in the Microsoft 365 admin center overrides the Outlook web app and SharePoint settings.
Idle session timeout is one of the many security measures in Microsoft 365. To learn about other security tasks in Microsoft 365, see Top security tasks in Microsoft 365.
What users see
When a user is inactive in Microsoft 365 web apps for the time period you chose, they see the following prompt. They have to select Stay signed in or they're signed out.
Details about idle session timeout
The following Microsoft 365 web apps are supported. More web apps will be added soon.
Outlook Web App
OneDrive
SharePoint
Microsoft Fabric
Microsoft365.com and other start pages
Microsoft 365 web apps (Word, Excel, PowerPoint)
Microsoft 365 Admin Center
Microsoft 365 Defender Portal
Microsoft Purview portal
Activity refers to any client-side user interaction happening in the context of the web app. For example, mouse clicks and keyboard presses.
Idle session timeout works on a per-browser session basis. A user’s activity on Microsoft Edge is treated differently than their activity in other browsers such as Google Chrome. Users are signed out from all tabs corresponding to their account within that browser session.
Once you turn on idle session timeout, it applies to your entire organization and can't be scoped to specific users, organizational units, or groups. Use Microsoft Entra Conditional Access policies for different users and groups to access SharePoint and Exchange Online.
Users must be inactive on all Microsoft 365 web app tabs for the configured duration. For example, if a user is active on a tab in Outlook web app, while inactive on another tab in SharePoint, they're considered active and aren't signed out.
Users don’t get signed out in these cases:
- If they get single sign-on (SSO) into the web app from the device joined account.
- If they selected Stay signed in at the time of sign-in. For more info on hiding this option for your organization, see Add branding to your organization's sign-in page.
- If they're on a managed device, that is compliant or joined to a domain and using a supported browser, like Microsoft Edge, or Google Chrome with the Microsoft Single Sign On extension.
Trigger idle session timeout only on unmanaged devices
By default, the idle session timeout feature triggers on all device types if the other conditions are met. For this feature to trigger only on an unmanaged device, an eligible Microsoft Entra ID P1 or P2 subscription is required. You also need to add a Conditional Access policy in the Microsoft Entra admin center.
Idle session timeout on unmanaged devices
For idle session timeout to get triggered only on unmanaged devices, you need to add a Conditional Access policy in the Microsoft Entra admin center.
On the Conditional Access | Policies page of the Microsoft Entra admin center, select New policy and enter a name for the policy.
Select Users or workload identities, and then select All users.
Select Cloud apps or actions, Select apps, and search for Office 365. Select Office 365, and then Select.
Select Conditions, Client apps, Configure to Yes, Browser, and then select Done.
Select Session, Use app enforced restrictions, and then Select.
Turn on the policy and select Create.
Frequently asked questions
Are there any browsers or browser scenarios in which idle session timeout feature doesn't work?
Idle session timeout isn't supported when third party cookies are disabled in the browser. Users don't see any sign-out prompts. We recommend keeping tracking prevention setting to Balanced (Default) for Microsoft Edge, and third-party cookies enabled in your other browsers. Microsoft 365 web apps and services stopped supporting Internet Explorer 11 on August 17, 2021.
How should I prepare if my organization is already using existing Outlook web app and SharePoint idle timeout policies?
If you're already using existing Outlook web app and SharePoint idle timeout policies, you can still turn on idle session timeout feature. When you turn on the idle timeout policy, it takes precedence over the existing Outlook web app and SharePoint Online policies. We're planning to deprecate the existing Outlook web app and SharePoint policies soon. To better prepare your organization, we recommend you turn on idle session timeout.
What happens if I'm inactive on an included Microsoft 365 web app, but active on a Microsoft web app or SaaS web app that doesn't have idle session time out turned on?
The following Microsoft 365 web apps are supported.
Outlook Web App
OneDrive
SharePoint
Microsoft Fabric
Microsoft365.com and other start pages
Microsoft 365 web apps (Word, Excel, PowerPoint)
Microsoft 365 admin center
Microsoft 365 Defender Portal
Microsoft Purview portal
If you're working on a different web app with the same account, the activity in that web app isn't applied to the idle session timeout.
I'm active in Azure portal, but I'm logged out of other Microsoft 365 Apps for inactivity. Why am I logged out?
Azure portal supports a similar inactivity feature, but is tracked in the Azure portal.
Note
When initially activated within the Azure portal, the timeout duration by default inherits from Microsoft 365 admin center idle session timeout setting. However, the timeout policy for the Azure portal can be explicitly configured within the portal itself. For more information, see Azure portal: Signing-Out + Notification.
I'm using Microsoft Fabric, how does Idle Session Timeout impact long-running Fabric Notebook executions?
If you are using a non-managed device where Idle Session Timeout is enabled, long-running interactive Fabric Notebook executions may be affected if a user goes inactive beyond the set tenant-wide session timeout policy. This is a pro-active measure to ensure idle devices are not accessible by outside parties. To mitigate, we advise users to not go inactive within M365 web apps while long-running executions are running.
I want to make changes to the idle session timeout policy or delete it. How can I do that?
Update the policy:
In the Microsoft 365 admin center, select Settings > Org settings, go to the Security & Privacy tab and select Idle session timeout.
In the dropdown menu, select a different timeout value and then Save.
Delete the policy:
In the Microsoft 365 admin center, select Settings > Org settings, go to the Security & Privacy tab and select Idle session timeout.
Uncheck Turn on to set the period of inactivity for users to be signed off of Microsoft 365 web apps and select Save.