Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
If you are like Microsoft and suddenly find yourself supporting a primarily home-based workforce, we want to help you ensure your organization is working as securely as possible. This article prioritizes tasks to help security teams implement the most important security capabilities as quickly as possible.
If you're a small or medium-size organization using one of Microsoft's business plans, see these resources instead:
- Best practices for securing Microsoft 365 for business plans
- Microsoft 365 for Campaigns (includes a recommended security configuration for Microsoft 365 Business)
For customers using our enterprise plans, Microsoft recommends you complete the tasks listed in the following table that apply to your service plan. Instead of purchasing a Microsoft 365 enterprise plan, if you're combining subscriptions, note the following items:
- Microsoft 365 E3 includes Enterprise Mobility + Security (EMS) E3 and Microsoft Entra ID P1
- Microsoft 365 E5 includes EMS E5 and Microsoft Entra ID P2
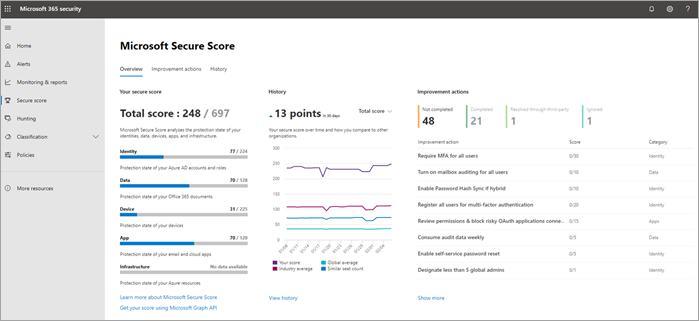
Before you begin, check your Microsoft 365 Secure Score in the Microsoft Defender portal. From a centralized dashboard, you can monitor and improve the security for your Microsoft 365 identities, data, apps, devices, and infrastructure. You're given points for configuring recommended security features, performing security-related tasks (such as viewing reports), or addressing recommendations with a third-party application or software. The recommended tasks in this article will raise your score.
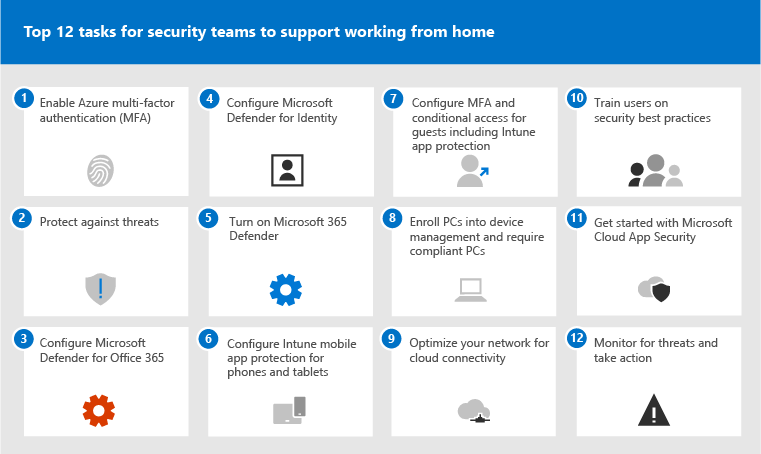
1: Enable Microsoft Entra multifactor authentication (MFA)
The single best thing you can do to improve security for employees working from home is to turn on MFA. If you don't already have processes in place, treat this condition as an emergency pilot and make sure you have support folks ready to help employees who get stuck. As you probably can't distribute hardware security devices, use Windows Hello biometrics and smartphone authentication apps like Microsoft Authenticator.
Normally, Microsoft recommends you give users 14 days to register their device for multifactor authentication before requiring MFA. However, if your workforce is suddenly working from home, go ahead and require MFA as a security priority and be prepared to help users who need it.
Applying these policies takes only a few minutes, but be prepared to support your users over the next several days.
| Plan | Recommendation |
|---|---|
| Microsoft 365 plans (without Microsoft Entra ID P1 or P2) | Enable Security defaults in Microsoft Entra ID. Security defaults in Microsoft Entra ID include MFA for users and administrators. |
| Microsoft 365 E3 (with Microsoft Entra ID P1) | Use Common Conditional Access policies to configure the following policies: |
| Microsoft 365 E5 (with Microsoft Entra ID P2) | Taking advantage of feature in Microsoft Entra ID, begin to implement Microsoft's recommended set of Conditional Access and related policies like:
|
2: Protect against threats
All Microsoft 365 plans with cloud mailboxes include Exchange Online Protection (EOP) features, including:
- Anti-malware.
- Anti-spam.
- Anti-spoofing in anti-phishing policies.
Default settings for these EOP features are automatically assigned to all recipients via default policies. But, to bump up the EOP protection level to Microsoft's recommended Standard or Strict security settings based on observations in the datacenters, turn on and assign the Standard preset security policy (for most users) and/or the Strict preset security policy (for admins and other high-risk users). As new protection capabilities are added and as the security landscape changes, the EOP settings in preset security policies are automatically updated to our recommended settings.
For instructions, see Use the Microsoft Defender portal to assign Standard and Strict preset security policies to users.
The differences between Standard and Strict are summarized in the table here. The comprehensive settings for Standard and Strict EOP settings are described in the tables here.
3: Configure Microsoft Defender for Office 365
Microsoft Defender for Office 365 (included with Microsoft 365 E5 and Office 365 E5) provides additional safeguards:
- Safe Attachments and Safe Links protection: Protects your organization from unknown threats in real time by using intelligent systems that inspect files, attachments, and links for malicious content. These automated systems include a robust detonation platform, heuristics, and machine learning models.
- Safe Attachments for SharePoint, OneDrive, and Microsoft Teams: Protects your organization when users collaborate and share files, by identifying and blocking malicious files in team sites and document libraries.
- Impersonation protection in anti-phishing policies: Applies machine learning models and advanced impersonation-detection algorithms to avert phishing attacks.
- Priority account protection: Priority accounts is a tag that you apply to a select number of high-value user accounts. Then, you can use the Priority tag as a filter in alerts, reports, and investigations. In Defender for Office 365 Plan 2 (included in Microsoft 365 E5), priority account protection offers additional heuristics for priority accounts that are tailored to company executives (regular employees don't benefit from this specialized protection).
For an overview of Defender for Office 365, including a summary of plans, see Defender for Office 365.
The Built-in protection preset security policy gives Safe Links and Safe Attachments protection to all recipients by default, but you can specify exceptions.
As in the previous section, to bump up the Defender for Office 365 protection level to Microsoft's recommended Standard or Strict security settings based on observations in the datacenters, turn on and assign the Standard preset security policy (for most users) and/or the Strict preset security policy (for admins and other high-risk users). As new protection capabilities are added and as the security landscape changes, the Defender for Office 365 settings in preset security policies are automatically updated to our recommended settings.
The users that you select for Defender for Office 365 protection in preset security policies get Microsoft's recommended Standard or Strict security settings for Safe Attachments and Safe Links. You also need to add entries and optional exceptions for user impersonation and domain impersonation protection.
For instructions, see Use the Microsoft Defender portal to assign Standard and Strict preset security policies to users.
The differences between Defender for Office 365 protection settings in Standard and Strict are summarized in the table here. The comprehensive settings for Standard and Strict Defender for Office 365 protection settings are described in the tables here.
You can turn on and turn off Safe Attachments for SharePoint, OneDrive, and Microsoft Teams independently of preset security policies (it's on by default). To verify, see Turn on Safe Attachments for SharePoint, OneDrive, and Microsoft Teams.
After you identify users as priority accounts, they get priority account protection if it's turned on (it's on by default). To verify, see Configure and review priority account protection in Microsoft Defender for Office 365.
4: Configure Microsoft Defender for Identity
Microsoft Defender for Identity is a cloud-based security solution that uses on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Focus on this item next because it protects your on-premises and cloud infrastructure, has no dependencies or prerequisites, and can provide immediate benefit.
- See Microsoft Defender for Identity Quickstarts to get setup quickly
- Watch Video: Introduction to Microsoft Defender for Identity
- Review the three phases of Microsoft Defender for Identity deployment
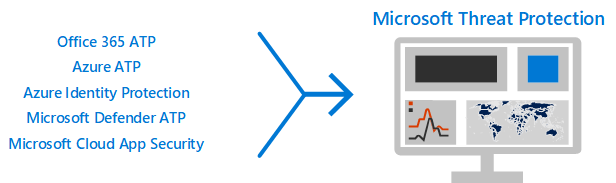
5: Turn on Microsoft Defender XDR
Now that you have Microsoft Defender for Office 365 and Microsoft Defender for Identity configured, you can view the combined signals from these capabilities in one dashboard. Microsoft Defender XDR brings together alerts, incidents, automated investigation and response, and advanced hunting across workloads (Microsoft Defender for Identity, Defender for Office 365, Microsoft Defender for Endpoint, and Microsoft Defender for Cloud Apps) into a single pane in the Microsoft Defender portal.
After you configure one or more of your Defender for Office 365 services, turn on MTP. New features are added continually to MTP; consider opting in to receive preview features.
6: Configure Intune mobile app protection for phones and tablets
Microsoft Intune Mobile Application Management (MAM) allows you to manage and protect your organization's data on phones and tablets without managing these devices. Here's how it works:
- You create an App Protection Policy (APP) that determines which apps on a device are managed and what behaviors are allowed (such as preventing data from a managed app from being copied to an unmanaged app). You create one policy for each platform (iOS, Android).
- After creating the app protection policies, you enforce these by creating a conditional access rule in Microsoft Entra ID to require approved apps and APP data protection.
APP protection policies include many settings. Fortunately, you don't need to learn about every setting and weigh the options. Microsoft makes it easy to apply a configuration of settings by recommending starting points. The Data protection framework using app protection policies includes three levels you can choose from.
Even better, Microsoft coordinates this app protection framework with a set of conditional access and related policies we recommend all organizations use as a starting point. If you implemented MFA using the guidance in this article, you're half way there!
To configure mobile app protection, use the guidance in Common identity and device access policies:
- Use the Apply APP data protection policies guidance to create policies for iOS and Android. Level 2 (enhanced data protection) is recommended for baseline protection.
- Create a conditional access rule to Require approved apps and APP protection.
7: Configure MFA and conditional access for guests, including Intune mobile app protection
Next, let's ensure you can continue to collaborate and work with guests. If you're using the Microsoft 365 E3 plan and you implemented MFA for all users, you're set.
If you're using the Microsoft 365 E5 plan and you're taking advantage of Azure Identity Protection for risk-based MFA, you need to make a couple of adjustments (because Microsoft Entra ID Protection doesn't extend to guests):
- Create a new conditional access rule to require MFA always for guests and external users.
- Update the risk-based MFA conditional access rule to exclude guests and external users.
Use the guidance in Updating the common policies to allow and protect guest and external access to understand how guest access works with Microsoft Entra ID and to update the affected policies.
The Intune mobile app protection policies you created, together with the conditional access rule to require approved apps and APP protection, apply to guests accounts and help protect your organization's data.
Note
If you already enrolled PCs into device management to require compliant PCs, you'll also need to exclude guest accounts from the conditional access rule that enforces device compliance.
8: Enroll PCs into device management and require compliant PCs
There are several methods to enroll your workforce's devices. Each method depends on the device's ownership (personal or corporate), device type (iOS, Windows, Android), and management requirements (resets, affinity, locking). This investigation can take a bit of time to sort out. See: Enroll devices in Microsoft Intune.
The quickest way to get going is to Set up automatic enrollment for Windows 10 devices.
You can also take advantage of these tutorials:
- Use Autopilot to enroll Windows devices in Intune
- Use Apple's Corporate Device Enrollment features in Apple Business Manager (ABM) to enroll iOS/iPadOS devices in Intune
After enrolling devices, use the guidance in Common identity and device access policies to create these policies:
- Define device-compliance policies: The recommended settings for Windows 10 include requiring antivirus protection. If you have Microsoft 365 E5, use Microsoft Defender for Endpoint to monitor the health of employee devices. Be sure compliance policies for other operating systems include antivirus protection and end-point protection software.
- Require compliant PCs: This is the conditional access rule in Microsoft Entra ID that enforces the device compliance policies.
Only one organization can manage a device, so be sure to exclude guest accounts from the conditional access rule in Microsoft Entra ID. If you don't exclude guest and external users from policies that require device compliance, these policies will block these users. For more information, see Updating the common policies to allow and protect guest and external access.
9: Optimize your network for cloud connectivity
If you're rapidly enabling the bulk of your employees to work from home, this sudden switch of connectivity patterns can have a significant impact on the corporate network infrastructure. Many networks were scaled and designed before cloud services were adopted. In many cases, networks are tolerant of remote workers, but weren't designed to be used remotely by all users simultaneously.
Network elements are suddenly put under enormous strain due to the load of the entire business using them. For example:
- VPN concentrators.
- Central network egress equipment (such as proxies and data loss prevention devices).
- Central internet bandwidth.
- Backhaul MPLS circuits
- NAT capability.
The end result is poor performance and productivity coupled with a poor experience for users who are adapting to working from home.
Some of the protections that have traditionally been provided by routing traffic back through a corporate network are now provided by the cloud apps that your users are accessing. If you reach this step in this article, you've implemented a set of sophisticated cloud security controls for Microsoft 365 services and data. With these controls in place, you may be ready to route remote users' traffic directly to Office 365. If you still require a VPN link for access to other applications, you can greatly improve your performance and user experience by implementing split tunneling. Once you achieve agreement in your organization, this optimization can be accomplished within a day by a well-coordinated network team.
For more information, see:
- Overview: Optimize connectivity for remote users using VPN split tunneling
- Implementing VPN split tunneling for Office 365
Recent blog articles on this topic:
- How to quickly optimize traffic for remote staff & reduce the load on your infrastructure
- Alternative ways for security professionals and IT to achieve modern security controls in today's unique remote work scenarios
10: Train users
Training users can save your users and security operations team a lot of time and frustration. Savvy users are less likely to open attachments or click links in questionable email messages, and they're more likely to avoid suspicious websites.
The Harvard Kennedy School Cybersecurity Campaign Handbook provides excellent guidance on establishing a strong culture of security awareness within your organization, including training users to identify phishing attacks.
Microsoft 365 provides the following resources to help inform users in your organization:
| Concept | Resources |
|---|---|
| Microsoft 365 | Customizable learning pathways These resources can help you put together training for end users in your organization |
| Microsoft 365 security | Learning module: Secure your organization with built-in, intelligent security from Microsoft 365 This module enables you to describe how Microsoft 365 security features work together and to articulate the benefits of these security features. |
| Multifactor authentication | Two-step verification: What is the additional verification page? This article helps end users understand what multifactor authentication is and why it's being used at your organization. |
In addition to this guidance, Microsoft recommends that your users take the actions described in this article: The keys to the kingdom - securing your devices and accounts. These actions include:
- Using strong passwords
- Protecting devices
- Enabling security features on Windows 10 and Mac PCs (for unmanaged devices)
Microsoft also recommends that users protect their personal email accounts by taking the actions recommended in the following articles:
11: Get started with Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your cloud services. Once you get started with Defender for Cloud Apps, anomaly detection policies are automatically enabled. But, Defender for Cloud Apps has an initial learning period of seven days during which not all anomaly detection alerts are raised.
Get started with Defender for Cloud Apps now. Later you can set up more sophisticated monitoring and controls.
- Quickstart: Get started with Defender for Cloud Apps
- Get instantaneous behavioral analytics and anomaly detection
- Learn more about Microsoft Defender for Cloud Apps
- Review new features and capabilities
- See basic setup instructions
12: Monitor for threats and take action
Microsoft 365 includes several ways to monitor status and take appropriate actions. Your best starting point is the Microsoft Defender portal, where you can view your organization's Microsoft Secure Score, and any alerts or entities that require your attention.
Next steps
Congratulations! You've quickly implemented some of the most important security protections and your organization is much more secure. Now you're ready to go even further with threat protection capabilities (including Microsoft Defender for Endpoint), data classification and protection capabilities, and securing administrative accounts. For a deeper, methodical set of security recommendations for Microsoft 365, see Microsoft 365 Security for Business Decision Makers (BDMs).
Also visit Microsoft's new Defender for Cloud in Security documentation.