Step 5 – Establish trust between PRIV and CORP forests
For each CORP domain such as contoso.local, the PRIV and CONTOSO domain controllers need to be bound by a trust. This lets users in the PRIV domain to access resources on the CORP domain.
Connect each domain controller to its counterpart
Before establishing trust, each domain controller must be configured for DNS name resolution for its counterpart, based on the other domain controller/DNS server’s IP address.
If the domain controllers or server with the MIM software are deployed as virtual machines, ensure that there are no other DNS servers which are providing domain naming services to those computers.
- If the virtual machines have multiple network interfaces, including network interfaces connected to public networks, you may need to temporarily disable those connections or override the Windows network interface settings. It's important to make sure that a DHCP-supplied DNS server address is not used by any virtual machines.
Verify that each existing CORP domain controller is able to route names to the PRIV forest. On each domain controller outside of the PRIV forest, such as CORPDC, launch PowerShell, and type the following command:
nslookup -qt=ns priv.contoso.local.Check that the output indicates a nameserver record for the PRIV domain with the correct IP address.
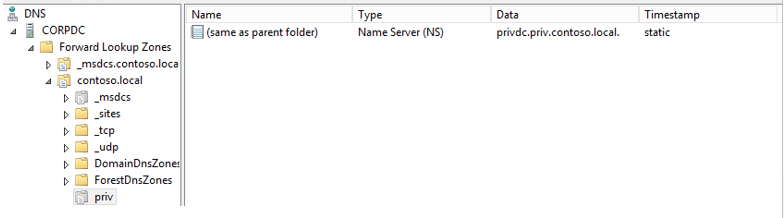
If the domain controller is unable to route the PRIV domain, use DNS Manager (located in Start > Application Tools > DNS) to configure DNS name forwarding for the PRIV domain to PRIVDC’s IP address. If it is a superior domain (e.g., contoso.local), expand the nodes for this domain controller and its domain, such as CORPDC > Forward Lookup Zones > contoso.local, and ensure a key named priv is present as a Name Server (NS) type.
Establish trust on PAMSRV
On PAMSRV, establish one-way trust with each domain such as CORPDC so that the CORP domain controllers trust the PRIV forest.
Sign in to PAMSRV as a PRIV domain administrator (PRIV\Administrator).
Launch PowerShell.
Type the following PowerShell commands for each existing forest. Enter the credential for the CORP domain administrator (CONTOSO\Administrator) when prompted.
$ca = get-credential New-PAMTrust -SourceForest "contoso.local" -Credentials $caType the following commands for each domain in the existing forests.
netdom trust contoso.local /domain:priv.contoso.local /enablesidhistory:yes /usero:contoso\administrator /passwordo:Pass@word1 netdom trust contoso.local /domain:priv.contoso.local /quarantine:no /usero:contoso\administrator /passwordo:Pass@word1 netdom trust contoso.local /domain:priv.contoso.local /enablepimtrust:yes /usero:contoso\administrator /passwordo:Pass@word1
Give read access to existing Active Directory forests
For each existing forest, enable read access to AD by PRIV administrators and the monitoring service.
Sign in to the existing CORP forest domain controller, (CORPDC), as a domain administrator for the top-level domain in that forest (Contoso\Administrator).
Launch Active Directory Users and Computers.
Right click on the domain contoso.local and select Delegate Control.
On the Selected Users and Groups tab, click Add.
On the Select Users, Computers, or Groups window, click Locations and change the location to priv.contoso.local. On the object name, type Domain Admins and click Check Names. When a popup appears, enter the username priv\administrator and its password.
After Domain Admins, add "; MIMMonitor". Once the names Domain Admins and MIMMonitor are underlined, click OK, then click Next.
In the list of common tasks, select Read all user information, then click Next and Finish.
Close Active Directory Users and Computers.
Open a PowerShell window.
Use
netdomto ensure SID history is enabled and SID filtering is disabled. Type:netdom trust contoso.local /quarantine:no /domain priv.contoso.local netdom trust /enablesidhistory:yes /domain priv.contoso.localThe output should say either Enabling SID history for this trust or SID history is already enabled for this trust.
The output should also indicate that SID filtering is not enabled for this trust. See Disable SID filter quarantining for more information.
Start the Monitoring and Component services
Sign in to PAMSRV as a PRIV domain administrator (PRIV\Administrator).
Launch PowerShell.
Type the following PowerShell commands.
net start "PAM Component service" net start "PAM Monitoring service"
In the next step, you will move a group to PAM.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for