Continually improve your security posture
We’ve learned how we can combine and use a selection of security tools and features from the cloud to the chip, to strengthen the security posture of our organization’s Windows devices. But the threat and vulnerability landscape changes frequently, and security features and configurations naturally need to change as well to meet the challenge. So, you’ll be continually improving your organization’s security posture across your devices and systems. To do this, you’ll need to:
- Monitor your security posture periodically.
- Deploy new features and configurations to improve your posture.
Microsoft Intune helps you achieve this, and much more, with less.
Monitor your security posture
To monitor your security posture effectively, you can take a two-pronged approach:
- Check your Microsoft Secure Score for a quick automated evaluation.
- Run Zero Trust assessments for a manual and granular evaluation of your security posture.
Measure your security posture
Traditionally, the biggest hurdle to improving your organization’s security posture has been its inability to accurately measure it. This is because it takes a lot of time to compare an organization’s security configurations with best practices, new and well-known risks, or other organization’s security configurations in the same industry. Often, the data hasn’t even been available, so there has been no way to compare. Additionally, for an effective measurement, security across the organization must be tracked continuously over time, and there have often been no means to facilitate this. Now there are tools like Microsoft Secure Score and Zero Trust online assessments that serve you to solve that problem.
We recommend you use [Microsoft Secure Score]/microsoft-365/security/defender/microsoft-secure-score?view=o365-worldwide&preserve-view=true) to get a quick objective overall measurement for your organization’s security posture: your security score. It scrutinizes your organization’s configurations, and even user behavior, and compares them against the Microsoft baseline.
Checking your score in Microsoft Defender XDR at least monthly is a good start. To do this, go to the Microsoft Secure Score overview page in Microsoft Defender XDR. You’ll see your Secure Score as a percentage:
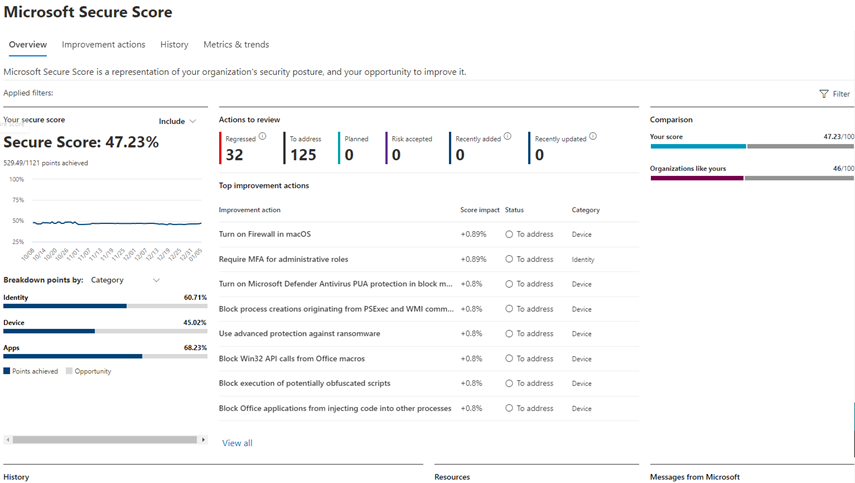
From here, you would do the following:
- Use the breakdown details to see how your points are split across the different layers such as identity, devices, and apps.
- Use the prioritized improvement actions recommended to you, to improve your secure score. Next to each of these actions you’ll also see how it will impact and increase your secure score.
- Use the History and Metrics & trends tabs to track your secure score over time and gain insights into how different activity has affected your score.
Next, you can use the Microsoft Zero Trust assessment tool to evaluate the security posture of each part of your environment from the evolving Zero Trust perspective. To use the assessment tool, you choose a pillar from the list of pillars, including identities, apps, endpoints, and more:
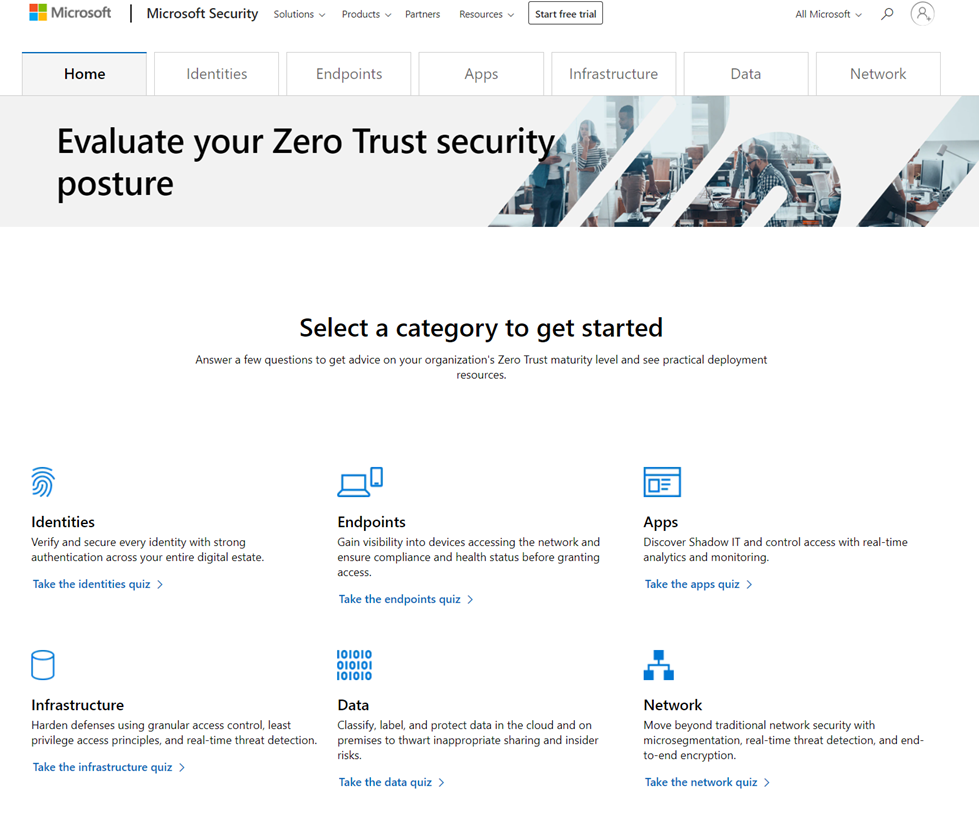
After you’ve selected a pillar, you’ll then answer specific questions about that part of your environment in a quiz format. For example, here are some questions you might be expected to answer to assess your apps pillar:
- Are you enforcing policy-based access controls for your applications?
- Is administrative access to applications provided Just-In-Time/Just-Enough-Privilege to reduce risk of permanent permissions?
Once you’ve answered all the questions, you’ll get information about your current security posture, such as whether you are at the getting started, advanced, or optimal stage with Zero Trust. You’ll also get specific recommendations to help you improve and optimize your security posture.
To assess your environment from chip to cloud, you’d perform this process for each pillar one at a time. This will enable you to comprehensively evaluate and continually improve your security posture.
Deploy the latest security features
This module includes just a selection of the basic security features, a lot of which are included by default in the latest Windows devices and builds. However, there are and will be more! As part of your journey to improve your security posture, you would want to keep up with and deploy the latest security features. This way, you can continue to optimize your security posture. These features come in the form of servicing updates that can address newly discovered vulnerabilities and threats for devices, apps, the operating system, identities, and more. They also provide improvements to facilitate the productivity of users.
Of course, to benefit from any new features like these, you’d have to deploy regular updates that provide them to you, using the familiar plan, prepare, deploy Windows servicing process where the last deployment stage consists of an initial pilot and broad deployment.
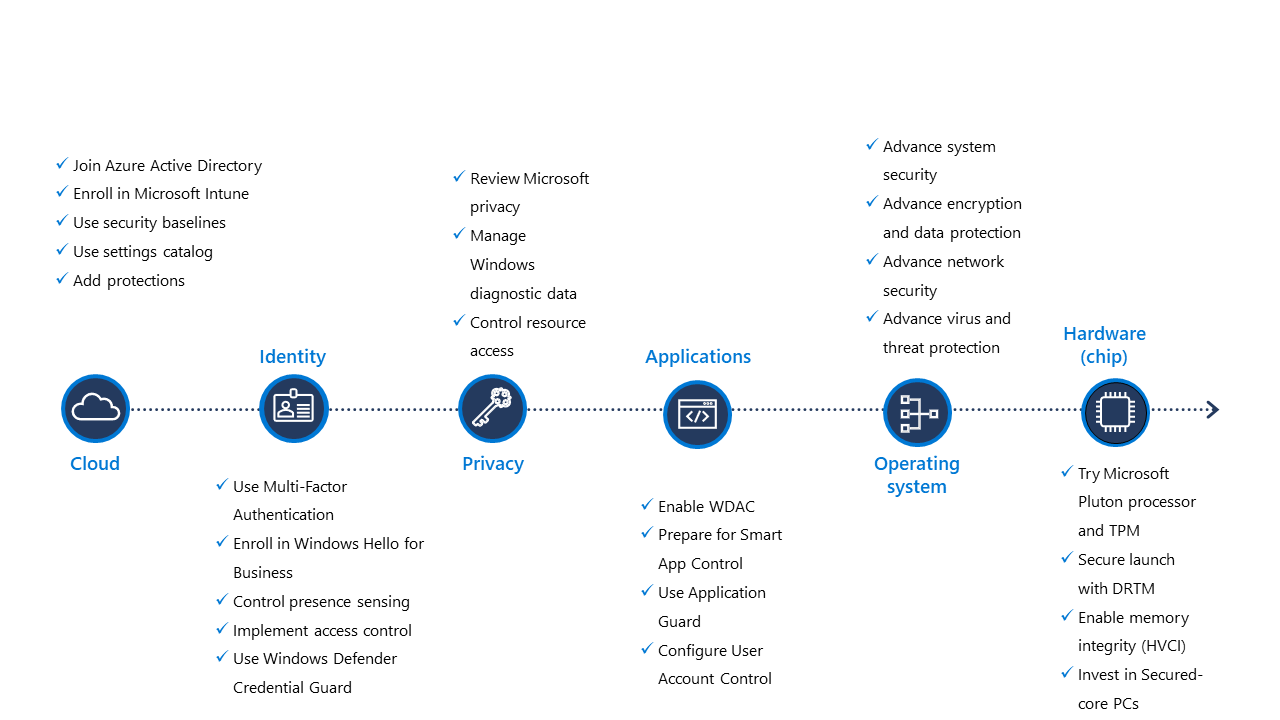
Layered security model recap
We’ve advanced our security posture through the layered security model step by step, so now’s a good time to recap the key points we can take away from it all.
Supporting the principles of Zero Trust, the Microsoft Intune tools help you ensure that all parts of your Windows technology stack, from the chip all the way to the cloud, work together to face emerging threats, strengthen your security posture, as well as your organization’s productivity. The security layers include:
- Connected cloud services for intelligent protections and safeguards
- Secured identities
- Precise privacy controls
- Robust application security
- Operating system security
- Enhanced hardware
Additionally, the layered security model makes it easier to understand the components and tools involved in securing your organization’s environment and the state of your security posture as a result. Individual components and tools across every layer can be updated or configured with Modern Device Management, such as Microsoft Intune, to meet emerging threats and improve productivity. And ultimately, it empowers you to take a “Never trust, always verify” stance to all components and tools across your environment.
This module ultimately challenges some common beliefs about the journey to security through servicing, which may keep IT pros from optimizing their security posture. The take-away message that underlies these security features, levels, and stages is to take full advantage of all of the nuts and bolts that servicing offers, including feature updates, to help keep you protected and productive on your journey to a strong security posture.