Muistiinpano
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää kirjautua sisään tai vaihtaa hakemistoa.
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää vaihtaa hakemistoa.
APPLIES TO: Premium
Network isolation is an optional feature of an API Management workspace gateway. This article provides network resource requirements when you integrate or inject your gateway in an Azure virtual network. Some requirements differ depending on the desired inbound and outbound access mode. The following modes are supported:
- Virtual network integration: public inbound access, private outbound access
- Virtual network injection: private inbound access, private outbound access
For background about networking options in API Management, see Use a virtual network to secure inbound or outbound traffic for Azure API Management.
Note
- The network configuration of a workspace gateway is independent of the network configuration of the API Management instance.
- Currently, a workspace gateway can only be configured in a virtual network when the gateway is created. You can't change the gateway's network configuration or settings later.
Network location
The virtual network must be in the same region and Azure subscription as the API Management instance.
Dedicated subnet
- The subnet used for virtual network integration or injection can only be used by a single workspace gateway. It can't be shared with another Azure resource.
Subnet size
- Minimum: /27 (32 addresses)
- Maximum: /24 (256 addresses) - recommended
Subnet delegation
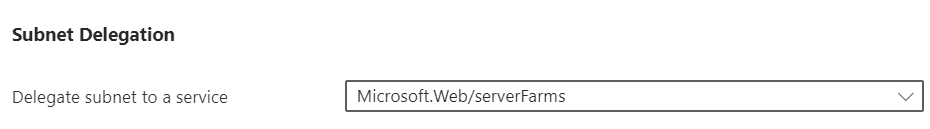
The subnet must be delegated as follows to enable the desired inbound and outbound access.
For information about configuring subnet delegation, see Add or remove a subnet delegation.
For virtual network integration, the subnet needs to be delegated to the Microsoft.Web/serverFarms service.
Note
The Microsoft.Web resource provider must be registered in the subscription so that you can delegate the subnet to the service. For steps to register a resource provider using the portal, see Register resource provider.
For more information about configuring subnet delegation, see Add or remove a subnet delegation.
Network security group
A network security group (NSG) must be associated with the subnet. To set up a network security group, see Create a network security group.
- Configure the rules in the following table to allow outbound access to Azure Storage and Azure Key Vault, which are dependencies for API Management.
- Configure other outbound rules you need for the gateway to reach your API backends.
- Configure other NSG rules to meet your organization’s network access requirements. For example, NSG rules can also be used to block outbound traffic to the internet and allow access only to resources in your virtual network.
| Direction | Source | Source port ranges | Destination | Destination port ranges | Protocol | Action | Purpose |
|---|---|---|---|---|---|---|---|
| Outbound | VirtualNetwork | * | Storage | 443 | TCP | Allow | Dependency on Azure Storage |
| Outbound | VirtualNetwork | * | AzureKeyVault | 443 | TCP | Allow | Dependency on Azure Key Vault |
Important
- Inbound NSG rules do not apply when you integrate a workspace gateway in a virtual network for private outbound access. To enforce inbound NSG rules, use virtual network injection instead of integration.
- This differs from networking in the classic Premium tier, where inbound NSG rules are enforced in both external and internal virtual network injection modes. Learn more
DNS settings for virtual network injection
For virtual network injection, you have to manage your own DNS to enable inbound access to your workspace gateway.
While you have the option to use a private or custom DNS server, we recommend:
- Configure an Azure DNS private zone.
- Link the Azure DNS private zone to the virtual network.
Learn how to set up a private zone in Azure DNS.
Note
If you configure a private or custom DNS resolver in the virtual network used for injection, you must ensure name resolution for Azure Key Vault endpoints (*.vault.azure.net). We recommend configuring an Azure private DNS zone, which doesn't require additional configuration to enable it.
Access on default hostname
When you create an API Management workspace, the workspace gateway is assigned a default hostname. The hostname is visible in the Azure portal on the workspace gateway's Overview page, along with its private virtual IP address. The default hostname is in the format <gateway-name>-<random hash>.gateway.<region>-<number>.azure-api.net. Example: team-workspace-123456abcdef.gateway.uksouth-01.azure-api.net.
Note
The workspace gateway only responds to requests to the hostname configured on its endpoint, not its private VIP address.
Configure DNS record
Create an A record in your DNS server to access the workspace from within your virtual network. Map the endpoint record to the private VIP address of your workspace gateway.
For testing purposes, you might update the hosts file on a virtual machine in a subnet connected to the virtual network in which API Management is deployed. Assuming the private virtual IP address for your workspace gateway is 10.1.0.5, you can map the hosts file as shown in the following example. The hosts mapping file is at %SystemDrive%\drivers\etc\hosts (Windows) or /etc/hosts (Linux, macOS).
| Internal virtual IP address | Gateway hostname |
|---|---|
| 10.1.0.5 | teamworkspace.gateway.westus.azure-api.net |