Use Azure Monitor managed service for Prometheus as data source for Grafana using managed system identity
Azure Monitor managed service for Prometheus allows you to collect and analyze metrics at scale using a Prometheus-compatible monitoring solution. The most common way to analyze and present Prometheus data is with a Grafana dashboard. This article explains how to configure Prometheus as a data source for both Azure Managed Grafana and self-hosted Grafana running in an Azure virtual machine using managed system identity authentication.
For information on using Grafana with Active Directory, see Configure self-managed Grafana to use Azure Monitor managed Prometheus with Microsoft Entra ID.
Azure Managed Grafana
The following sections describe how to configure Azure Monitor managed service for Prometheus as a data source for Azure Managed Grafana.
Important
This section describes the manual process for adding an Azure Monitor managed service for Prometheus data source to Azure Managed Grafana. You can achieve the same functionality by linking the Azure Monitor workspace and Grafana workspace as described in Link a Grafana workspace.
Configure system identity
Your Grafana workspace requires the following settings:
- System managed identity enabled
- Monitoring Data Reader role for the Azure Monitor workspace
Both of these settings are configured by default when you created your Grafana workspace and linked it to an Azure Monitor workspace. Verify these settings on the Identity page for your Grafana workspace.
Configure from Grafana workspace
Use the following steps to allow access all Azure Monitor workspaces in a resource group or subscription:
Open the Identity page for your Grafana workspace in the Azure portal.
If Status is No, change it to Yes.
Select Azure role assignments to review the existing access in your subscription.
If Monitoring Data Reader isn't listed for your subscription or resource group:
Select + Add role assignment.
For Scope, select either Subscription or Resource group.
For Role, select Monitoring Data Reader.
Select Save.
Configure from Azure Monitor workspace
Use the following steps to allow access to only a specific Azure Monitor workspace:
Open the Access Control (IAM) page for your Azure Monitor workspace in the Azure portal.
Select Add role assignment.
Select Monitoring Data Reader and select Next.
For Assign access to, select Managed identity.
Select + Select members.
For Managed identity, select Azure Managed Grafana.
Select your Grafana workspace and then select Select.
Select Review + assign to save the configuration.
Create Prometheus data source
Azure Managed Grafana supports Azure authentication by default.
Open the Overview page for your Azure Monitor workspace in the Azure portal.
Copy the Query endpoint, which you'll need in a step below.
Open your Azure Managed Grafana workspace in the Azure portal.
Select on the Endpoint to view the Grafana workspace.
Select Configuration and then Data source.
Select Add data source and then Prometheus.
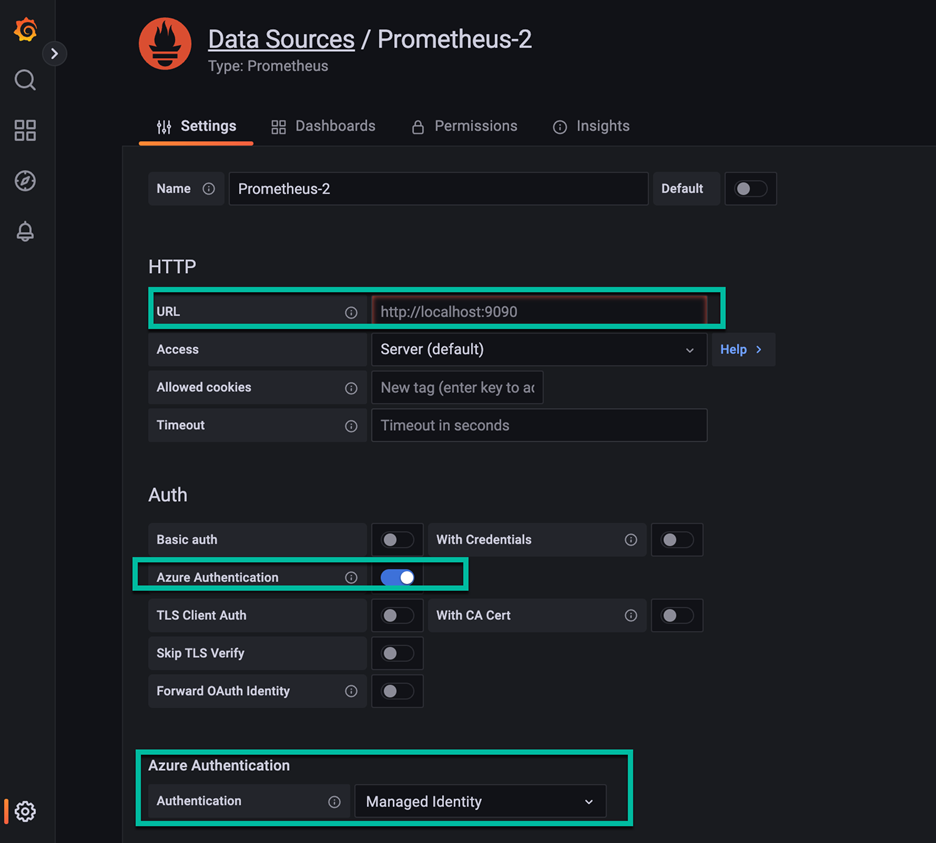
For URL, paste in the query endpoint for your Azure Monitor workspace.
Select Azure Authentication to turn it on.
For Authentication under Azure Authentication, select Managed Identity.
Scroll to the bottom of the page and select Save & test.
Self-managed Grafana
The following sections describe how to configure Azure Monitor managed service for Prometheus as a data source for self-managed Grafana on an Azure virtual machine.
Configure system identity
Azure virtual machines support both system assigned and user assigned identity. The following steps configure system assigned identity.
Configure from Azure virtual machine
Use the following steps to allow access all Azure Monitor workspaces in a resource group or subscription:
Open the Identity page for your virtual machine in the Azure portal.
If Status is No, change it to Yes.
Select Save.
Select Azure role assignments to review the existing access in your subscription.
If Monitoring Data Reader isn't listed for your subscription or resource group:
Select + Add role assignment.
For Scope, select either Subscription or Resource group.
For Role, select Monitoring Data Reader.
Select Save.
Configure from Azure Monitor workspace
Use the following steps to allow access to only a specific Azure Monitor workspace:
Open the Access Control (IAM) page for your Azure Monitor workspace in the Azure portal.
Select Add role assignment.
Select Monitoring Data Reader and select Next.
For Assign access to, select Managed identity.
Select + Select members.
For Managed identity, select Virtual machine.
Select your Grafana workspace and then click Select.
Select Review + assign to save the configuration.
Create Prometheus data source
Versions 9.x and greater of Grafana support Azure Authentication, but it's not enabled by default. To enable this feature, you need to update your Grafana configuration. To determine where your Grafana.ini file is and how to edit your Grafana config, review the Configure Grafana document from Grafana Labs. Once you know where your configuration file lives on your VM, make the following update:
Locate and open the Grafana.ini file on your virtual machine.
Under the
[auth]section of the configuration file, change theazure_auth_enabledsetting totrue.Under the
[azure]section of the configuration file, change themanaged_identity_enabledsetting totrueOpen the Overview page for your Azure Monitor workspace in the Azure portal.
Copy the Query endpoint, which you'll need in a step below.
Open your Azure Managed Grafana workspace in the Azure portal.
Click on the Endpoint to view the Grafana workspace.
Select Configuration and then Data source.
Click Add data source and then Prometheus.
For URL, paste in the query endpoint for your Azure Monitor workspace.
Select Azure Authentication to turn it on.
For Authentication under Azure Authentication, select Managed Identity.
Scroll to the bottom of the page and click Save & test.
Frequently asked questions
This section provides answers to common questions.
I am missing all or some of my metrics. How can I troubleshoot?
You can use the troubleshooting guide for ingesting Prometheus metrics from the managed agent here.
Why am I missing metrics that have two labels with the same name but different casing?
Azure managed Prometheus is a case insensitive system. It treats strings, such as metric names, label names, or label values, as the same time series if they differ from another time series only by the case of the string. For more information, see Prometheus metrics overview.
I see some gaps in metric data, why is this occurring?
During node updates, you might see a 1-minute to 2-minute gap in metric data for metrics collected from our cluster level collectors. This gap occurs because the node that the data runs on is being updated as part of a normal update process. This update process affects cluster-wide targets such as kube-state-metrics and custom application targets that are specified. This occurs when your cluster is updated manually or via autoupdate. This behavior is expected and occurs due to the node it runs on being updated. This behavior doesn't affect any of our recommended alert rules.
Next steps
Palaute
Tulossa pian: Vuoden 2024 aikana poistamme asteittain GitHub Issuesin käytöstä sisällön palautemekanismina ja korvaamme sen uudella palautejärjestelmällä. Lisätietoja on täällä: https://aka.ms/ContentUserFeedback.
Lähetä ja näytä palaute kohteelle