Service-to-service authentication with Azure Data Lake Storage Gen1 using Microsoft Entra ID
Azure Data Lake Storage Gen1 uses Microsoft Entra ID for authentication. Before authoring an application that works with Data Lake Storage Gen1, you must decide how to authenticate your application with Microsoft Entra ID. The two main options available are:
- End-user authentication
- Service-to-service authentication (this article)
Both these options result in your application being provided with an OAuth 2.0 token, which gets attached to each request made to Data Lake Storage Gen1.
This article talks about how to create an Microsoft Entra web application for service-to-service authentication. For instructions on Microsoft Entra application configuration for end-user authentication, see End-user authentication with Data Lake Storage Gen1 using Microsoft Entra ID.
Prerequisites
- An Azure subscription. See Get Azure free trial.
Step 1: Create an Active Directory web application
Create and configure a Microsoft Entra web application for service-to-service authentication with Azure Data Lake Storage Gen1 using Microsoft Entra ID. For instructions, see Create a Microsoft Entra application.
While following the instructions at the preceding link, make sure you select Web App / API for application type, as shown in the following screenshot:

Step 2: Get application ID, authentication key, and tenant ID
When programmatically logging in, you need the ID for your application. If the application runs under its own credentials, you also need an authentication key.
For instructions on how to retrieve the application ID and authentication key (also called the client secret) for your application, see Get application ID and authentication key.
For instructions on how to retrieve the tenant ID, see Get tenant ID.
Step 3: Assign the Microsoft Entra application to the Azure Data Lake Storage Gen1 account file or folder
Sign on to the Azure portal. Open the Data Lake Storage Gen1 account that you want to associate with the Microsoft Entra application you created earlier.
In your Data Lake Storage Gen1 account blade, click Data Explorer.

In the Data Explorer blade, click the file or folder for which you want to provide access to the Microsoft Entra application, and then click Access. To configure access to a file, you must click Access from the File Preview blade.

The Access blade lists the standard access and custom access already assigned to the root. Click the Add icon to add custom-level ACLs.

Click the Add icon to open the Add Custom Access blade. In this blade, click Select User or Group, and then in Select User or Group blade, look for the Microsoft Entra application you created earlier. If you have many groups to search from, use the text box at the top to filter on the group name. Click the group you want to add and then click Select.
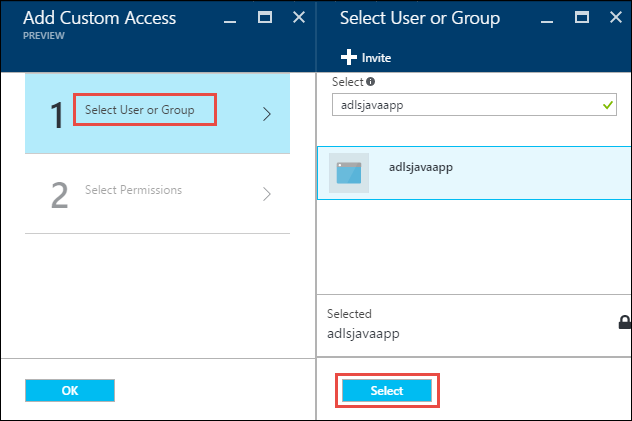
Click Select Permissions, select the permissions and whether you want to assign the permissions as a default ACL, access ACL, or both. Click OK.

For more information about permissions in Data Lake Storage Gen1, and Default/Access ACLs, see Access Control in Data Lake Storage Gen1.
In the Add Custom Access blade, click OK. The newly added groups, with the associated permissions, are listed in the Access blade.

Note
If you plan on restricting your Microsoft Entra application to a specific folder, you will also need to give that same Microsoft Entra application Execute permission to the root to enable file creation access via the .NET SDK.
Note
If you want to use the SDKs to create a Data Lake Storage Gen1 account, you must assign the Microsoft Entra web application as a role to the Resource Group in which you create the Data Lake Storage Gen1 account.
Step 4: Get the OAuth 2.0 token endpoint (only for Java-based applications)
Sign on to the Azure portal and click Active Directory from the left pane.
From the left pane, click App registrations.
From the top of the App registrations blade, click Endpoints.

From the list of endpoints, copy the OAuth 2.0 token endpoint.

Next steps
In this article, you created a Microsoft Entra web application and gathered the information you need in your client applications that you author using .NET SDK, Java, Python, REST API, etc. You can now proceed to the following articles that talk about how to use the Microsoft Entra native application to first authenticate with Data Lake Storage Gen1 and then perform other operations on the store.
- Service-to-service authentication with Data Lake Storage Gen1 using Java
- Service-to-service authentication with Data Lake Storage Gen1 using .NET SDK
- Service-to-service authentication with Data Lake Storage Gen1 using Python
- Service-to-service authentication with Data Lake Storage Gen1 using REST API