Manage the configuration server for physical server disaster recovery
You set up an on-premises configuration server when you use the Azure Site Recovery service for disaster recovery of physical servers to Azure. The configuration server coordinates communications between on-premises machines and Azure, and manages data replication. This article summarizes common tasks for managing the configuration server after it's been deployed.
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. To get started, see Install Azure PowerShell. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
Prerequisites
The table summarizes the prerequisites for deploying the on-premises configuration server machine.
| Component | Requirement |
|---|---|
| CPU cores | 8 |
| RAM | 16 GB |
| Number of disks | 3, including the OS disk, process server cache disk, and retention drive for failback |
| Disk free space (process server cache) | 600 GB |
| Disk free space (retention disk) | 600 GB |
| Operating system | Windows Server 2012 R2 Windows Server 2016 |
| Operating system locale | English (US) |
| VMware vSphere PowerCLI version | Not required |
| Windows Server roles | Don't enable these roles: - Active Directory Domain Services - Internet Information Services - Hyper-V |
| Group policies | Don't enable these group policies: - Prevent access to the command prompt - Prevent access to registry editing tools - Trust logic for file attachments - Turn on Script Execution Learn more |
| IIS | - No pre-existing default website - Enable Anonymous Authentication - Enable FastCGI setting - No pre-existing website/application listening on port 443 |
| NIC type | VMXNET3 (when deployed as a VMware VM) |
| IP address type | Static |
| Internet access | The server needs access to these URLs: - *.accesscontrol.windows.net - *.backup.windowsazure.com - *.store.core.windows.net - *.blob.core.windows.net - *.hypervrecoverymanager.windowsazure.com - https://management.azure.com - *.services.visualstudio.com - https://dev.mysql.com/get/Downloads/MySQLInstaller/mysql-installer-community-5.7.20.0.msi (not required for Scale-out Process Servers) - time.nist.gov - time.windows.com |
| Ports | 443 (Control channel orchestration) 9443 (Data transport) |
Download the latest installation file
The latest version of the configuration server installation file is available in the Site Recovery portal. Additionally, it can be downloaded directly from the Microsoft Download Center.
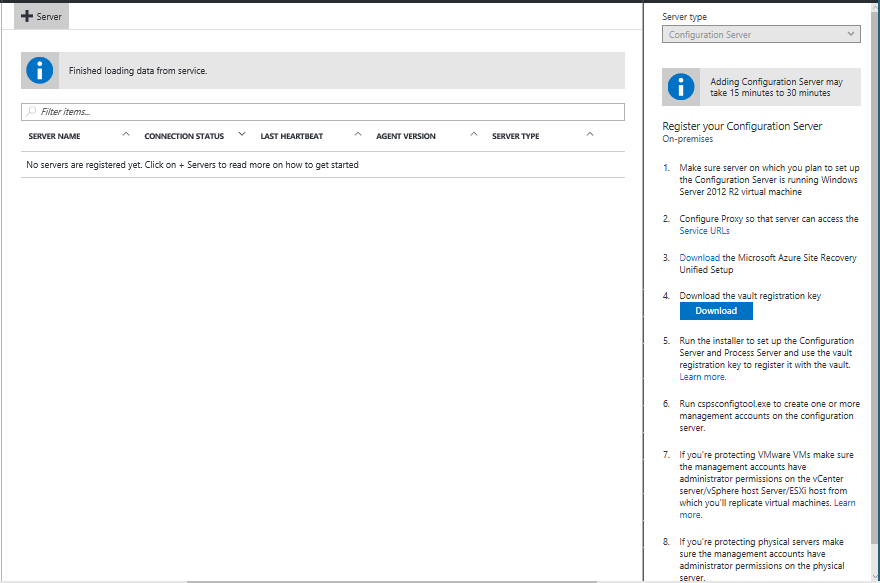
Log on to the Azure portal and browse to your Recovery Services Vault.
Browse to Site Recovery Infrastructure > Configuration Servers (under For VMware & Physical Machines).
Click the +Servers button.
On the Add Server page, click the Download button to download the Registration key. You need this key during the Configuration Server installation to register it with Azure Site Recovery service.
Click the Download the Microsoft Azure Site Recovery Unified Setup link to download the latest version of the Configuration Server.
Install and register the server
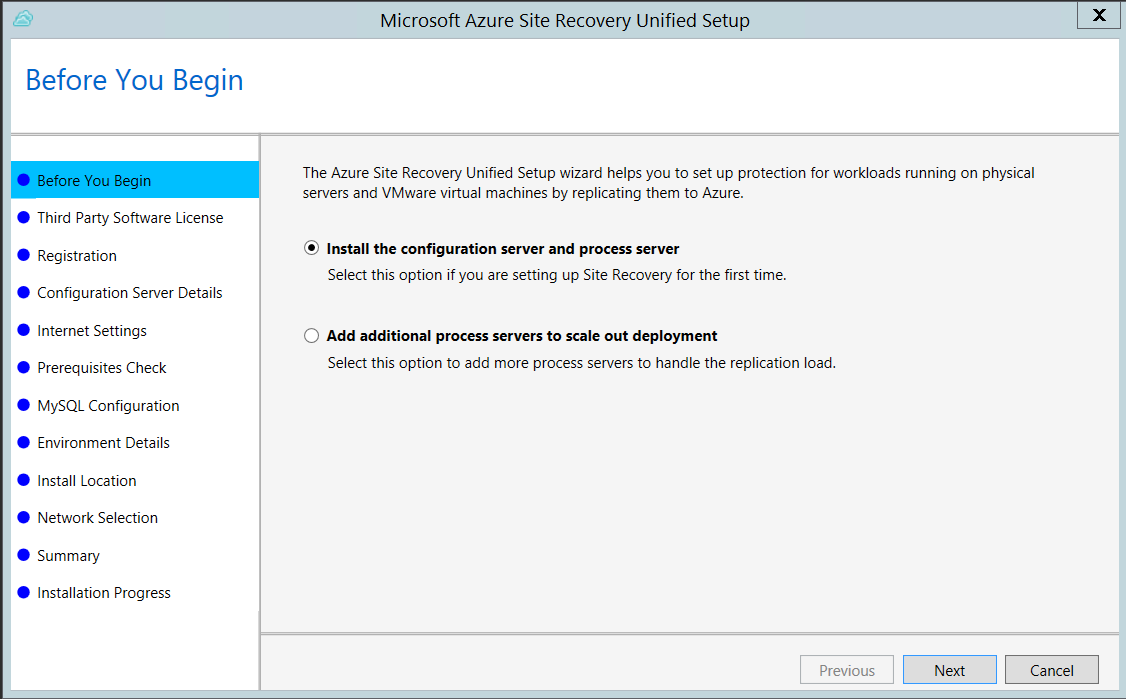
Run the Unified Setup installation file.
In Before You Begin, select Install the configuration server and process server.
In Third Party Software License, click I Accept to download and install MySQL.
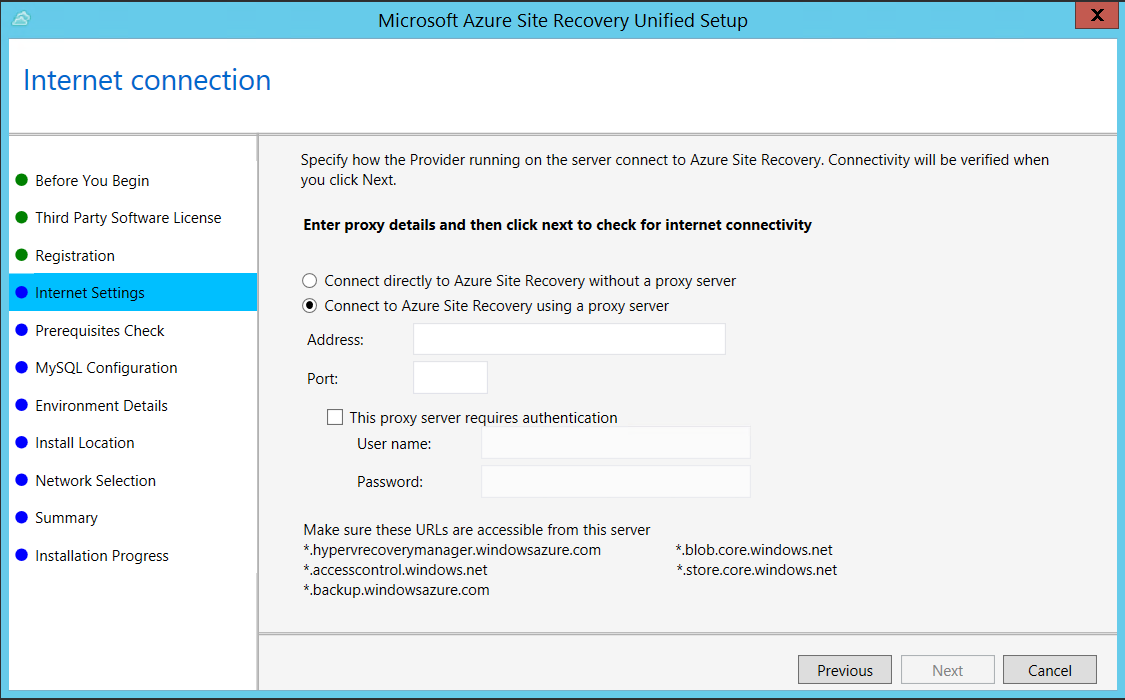
In Internet Settings, specify how the Provider running on the configuration server connects to Azure Site Recovery over the Internet. Make sure you've allowed the required URLs.
- If you want to connect with the proxy that's currently set up on the machine, select Connect to Azure Site Recovery using a proxy server.
- If you want the Provider to connect directly, select Connect directly to Azure Site Recovery without a proxy server.
- If the existing proxy requires authentication, or if you want to use a custom proxy for the Provider connection, select Connect with custom proxy settings, and specify the address, port, and credentials.
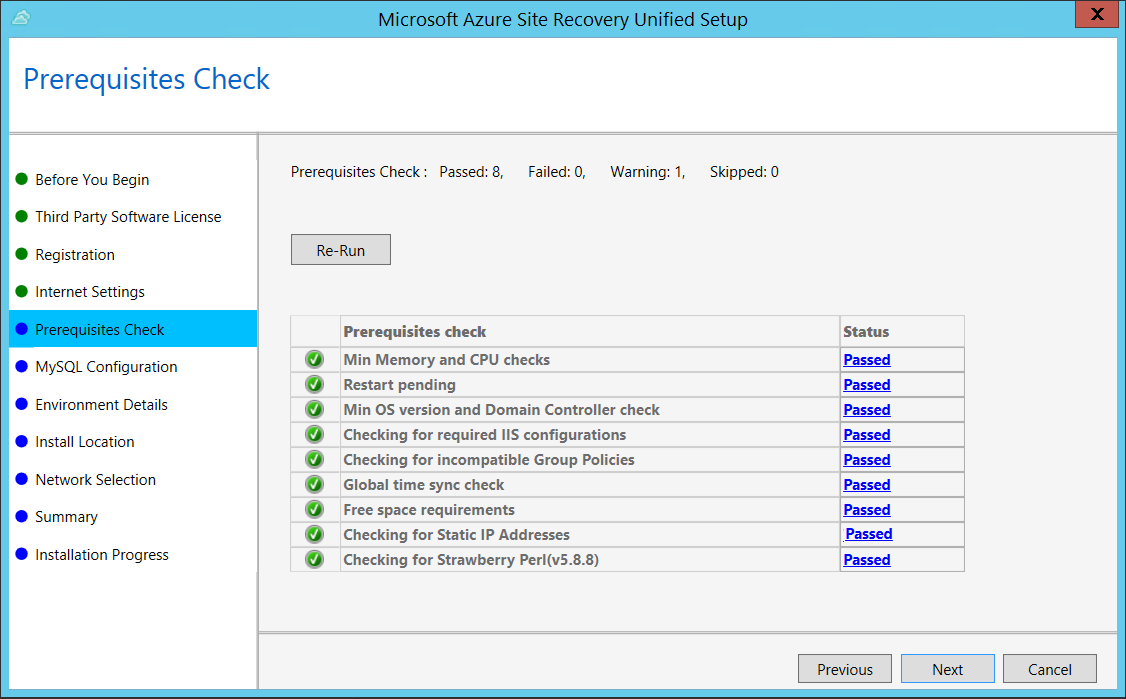
In Prerequisites Check, Setup runs a check to make sure that installation can run. If a warning appears about the Global time sync check, verify that the time on the system clock (Date and Time settings) is the same as the time zone.
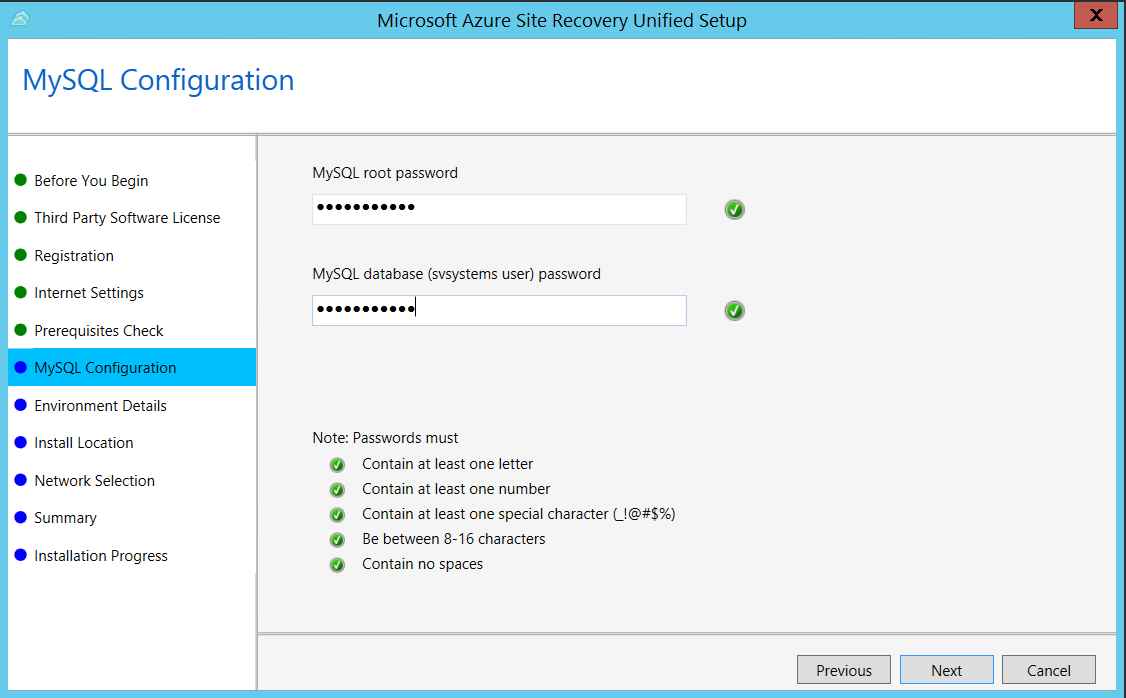
In MySQL Configuration, create credentials for logging on to the MySQL server instance that is installed.
In Environment Details, select whether you're going to replicate VMware VMs. If you are, then Setup checks that PowerCLI 6.0 is installed.
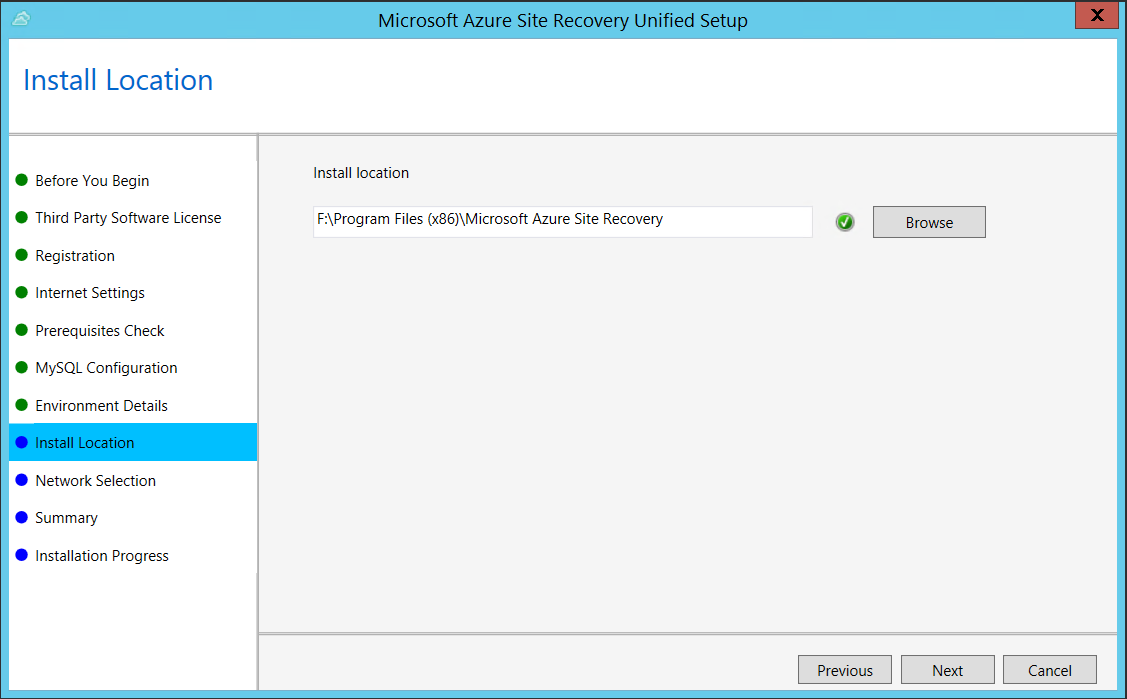
In Install Location, select where you want to install the binaries and store the cache. The drive you select must have at least 5 GB of disk space available, but we recommend a cache drive with at least 600 GB of free space.
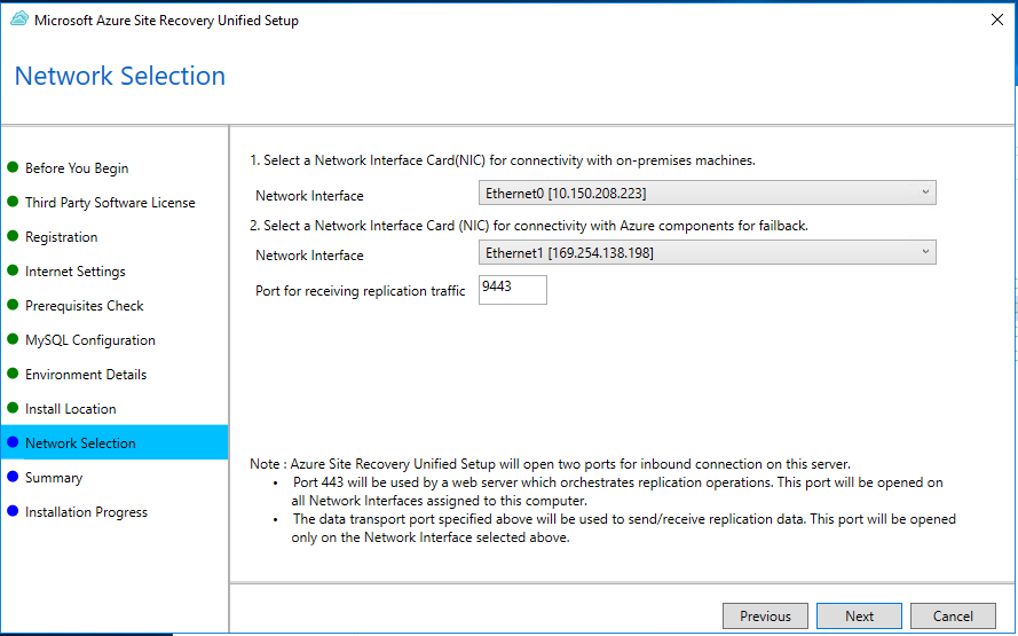
In Network Selection, first select the NIC that the in-built process server uses for discovery and push installation of mobility service on source machines, and then select the NIC that Configuration Server uses for connectivity with Azure. Port 9443 is the default port used for sending and receiving replication traffic, but you can modify this port number to suit your environment's requirements. In addition to the port 9443, we also open port 443, which is used by a web server to orchestrate replication operations. Do not use port 443 for sending or receiving replication traffic.
In Summary, review the information and click Install. When installation finishes, a passphrase is generated. You will need this when you enable replication, so copy it and keep it in a secure location.
After registration finishes, the server is displayed on the Settings > Servers blade in the vault.
Install from the command line
Run the installation file as follows:
UnifiedSetup.exe [/ServerMode <CS/PS>] [/InstallDrive <DriveLetter>] [/MySQLCredsFilePath <MySQL credentials file path>] [/VaultCredsFilePath <Vault credentials file path>] [/EnvType <VMWare/NonVMWare>] [/PSIP <IP address to be used for data transfer] [/CSIP <IP address of CS to be registered with>] [/PassphraseFilePath <Passphrase file path>]
Sample usage
MicrosoftAzureSiteRecoveryUnifiedSetup.exe /q /x:C:\Temp\Extracted
cd C:\Temp\Extracted
UNIFIEDSETUP.EXE /AcceptThirdpartyEULA /servermode "CS" /InstallLocation "D:\" /MySQLCredsFilePath "C:\Temp\MySQLCredentialsfile.txt" /VaultCredsFilePath "C:\Temp\MyVault.vaultcredentials" /EnvType "VMWare"
Parameters
| Parameter Name | Type | Description | Values |
|---|---|---|---|
| /ServerMode | Required | Specifies whether both the configuration and process servers should be installed, or the process server only | CS PS |
| /InstallLocation | Required | The folder in which the components are installed | Any folder on the computer |
| /MySQLCredsFilePath | Required | The file path in which the MySQL server credentials are stored | The file should be the format specified below |
| /VaultCredsFilePath | Required | The path of the vault credentials file | Valid file path |
| /EnvType | Required | Type of environment that you want to protect | VMware NonVMware |
| /PSIP | Required | IP address of the NIC to be used for replication data transfer | Any valid IP Address |
| /CSIP | Required | The IP address of the NIC on which the configuration server is listening on | Any valid IP Address |
| /PassphraseFilePath | Required | The full path to location of the passphrase file | Valid file path |
| /BypassProxy | Optional | Specifies that the configuration server connects to Azure without a proxy | To do get this value from Venu |
| /ProxySettingsFilePath | Optional | Proxy settings (The default proxy requires authentication, or a custom proxy) | The file should be in the format specified below |
| DataTransferSecurePort | Optional | Port number on the PSIP to be used for replication data | Valid Port Number (default value is 9433) |
| /SkipSpaceCheck | Optional | Skip space check for cache disk | |
| /AcceptThirdpartyEULA | Required | Flag implies acceptance of third-party EULA | |
| /ShowThirdpartyEULA | Optional | Displays third-party EULA. If provided as input all other parameters are ignored |
Create file input for MYSQLCredsFilePath
The MySQLCredsFilePath parameter takes a file as input. Create the file using the following format and pass it as input MySQLCredsFilePath parameter.
[MySQLCredentials]
MySQLRootPassword = "Password"
MySQLUserPassword = "Password"
Create file input for ProxySettingsFilePath
ProxySettingsFilePath parameter takes a file as input. Create the file using the following format and pass it as input ProxySettingsFilePath parameter.
[ProxySettings]
ProxyAuthentication = "Yes/No"
Proxy IP = "IP Address"
ProxyPort = "Port"
ProxyUserName="UserName"
ProxyPassword="Password"
Modify proxy settings
You can modify proxy settings for the configuration server machine as follows:
Log on to the configuration server.
Launch the cspsconfigtool.exe using the shortcut on your desktop.
Click the Vault Registration tab.
Download a new vault registration file from the portal, and provide it as input to the tool.
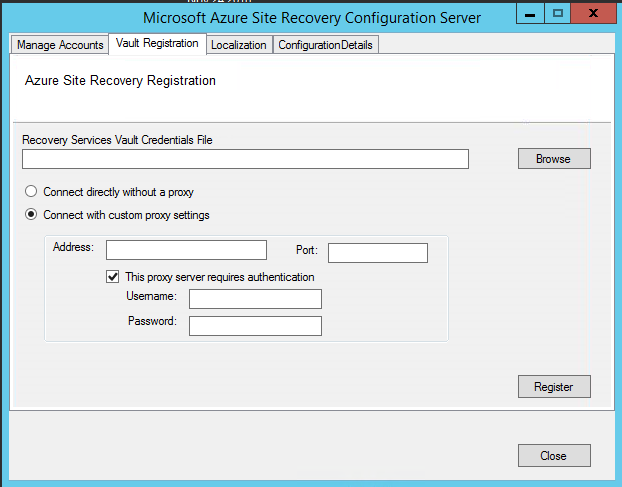
Provide the new proxy details and click the Register button.
Open an Admin PowerShell command window.
Run the following command:
$Pwd = ConvertTo-SecureString -String MyProxyUserPassword Set-OBMachineSetting -ProxyServer http://myproxyserver.domain.com -ProxyPort PortNumber –ProxyUserName domain\username -ProxyPassword $Pwd net stop obengine net start obengineWarning
If you have additional process servers attached to the configuration server, you need to fix the proxy settings on all the scale-out process servers in your deployment.
Reregister a configuration server with the same vault
Log in to your Configuration Server.
Launch the cspsconfigtool.exe using the shortcut on your desktop.
Click the Vault Registration tab.
Download a new registration file from the portal and provide it as input to the tool.

Provide the Proxy Server details and click the Register button.
Open an Admin PowerShell command window.
Run the following command
$Pwd = ConvertTo-SecureString -String MyProxyUserPassword Set-OBMachineSetting -ProxyServer http://myproxyserver.domain.com -ProxyPort PortNumber –ProxyUserName domain\username -ProxyPassword $Pwd net stop obengine net start obengineWarning
If you have multiple process server, you need to reregister them.
Register a configuration server with a different vault
Warning
The following step disassociates the configuration server from the current vault, and the replication of all protected virtual machines under the configuration server is stopped.
Log onto the configuration server
from an admin command prompt, run the command:
reg delete HKLM\Software\Microsoft\Azure Site Recovery\Registration net stop draLaunch the cspsconfigtool.exe using the shortcut on your desktop.
Click the Vault Registration tab.
Download a new registration file from the portal and provide it as input to the tool.
Provide the Proxy Server details and click the Register button.
Open an Admin PowerShell command window.
Run the following command
$pwd = ConvertTo-SecureString -String MyProxyUserPassword Set-OBMachineSetting -ProxyServer http://myproxyserver.domain.com -ProxyPort PortNumber –ProxyUserName domain\username -ProxyPassword $pwd net stop obengine net start obengine
Upgrade a configuration server
You run update rollups to update the configuration server. Updates can be applied for up to N-4 versions. For example:
- If you're running 9.7, 9.8, 9.9, or 9.10 - you can upgrade directly to 9.11.
- If you're running 9.6 or earlier, and you want to upgrade to 9.11, you must first upgrade to version 9.7. before 9.11.
Links to update rollups for upgrading to all versions of the configuration server are available in the wiki updates page.
Upgrade the server as follows:
- Download the update installer file to the configuration server.
- Double-click to run the installer.
- The installer detects the current version running on the machine.
- Click OK to confirm, and run the upgrade.
Delete or unregister a configuration server
Warning
Ensure the following before you start decommissioning your Configuration Server.
- Disable protection for all virtual machines under this Configuration Server.
- Disassociate and Delete all Replication policies from the Configuration Server.
- Delete all vCenters servers/vSphere hosts that are associated to the Configuration Server.
Delete the Configuration Server from Azure portal
- In Azure portal, browse to Site Recovery Infrastructure > Configuration Servers from the Vault menu.
- Click the configuration server that you want to decommission.
- On the Configuration Server's details page, click the Delete button.
- Click Yes to confirm the deletion of the server.
Uninstall the configuration server and its dependencies
Tip
If you plan to reuse the Configuration Server with Azure Site Recovery again, then you can skip to step 4 directly
- Log on to the Configuration Server as an Administrator.
- Open up Control Panel > Program > Uninstall Programs
- Uninstall the programs in the following sequence:
- Microsoft Azure Recovery Services Agent
- Microsoft Azure Site Recovery Mobility Service/Master Target server
- Microsoft Azure Site Recovery Provider
- Microsoft Azure Site Recovery Configuration Server/Process Server
- Microsoft Azure Site Recovery Configuration Server Dependencies
- MySQL Server 5.7
- Run the following command from and admin command prompt.
reg delete HKLM\Software\Microsoft\Azure Site Recovery\Registration
Delete or unregister a configuration server (PowerShell)
Install Azure PowerShell module
Login into to your Azure account using the command
Connect-AzAccount –UseDeviceAuthenticationSelect the subscription under which the vault is present
Get-AzSubscription –SubscriptionName <your subscription name> | Select–AzSubscriptionNow set up your vault context
$vault = Get–AzRecoveryServicesVault –Name <name of your vault> Set-AzRecoveryServicesAsrVaultContext –Vault $vaultGet select your configuration server
$Fabric = Get–AzRecoveryServicesAsrFabric –FriendlyName <name of your configuration server>Delete the Configuration Server
Remove–AzRecoveryServicesAsrFabric –Fabric $Fabric –Force
Note
The -Force option in the Remove-AzRecoveryServicesAsrFabric can be used to force the removal/deletion of the Configuration server.
Renew TLS/SSL certificates
The configuration server has an inbuilt web server, which orchestrates activities of the Mobility service, process servers, and master target servers connected to it. The web server uses a TLS/SSL certificate to authenticate clients. The certificate expires after three years, and can be renewed at any time.
Check expiry
For configuration server deployments before May 2016, certificate expiry was set to one year. If you have a certificate is going to expire, the following occurs:
- When the expiry date is two months or less, the service starts sending notifications in the portal, and by email (if you subscribed to Azure Site Recovery notifications).
- A notification banner appears on the vault resource page. Click the banner for more details.
- If you see an Upgrade Now button, this indicates that there are some components in your environment that haven't been upgraded to 9.4.xxxx.x or higher versions. Upgrade components before you renew the certificate. You can't renew on older versions.
Renew the certificate
- In the vault, open Site Recovery Infrastructure > Configuration Server, and click the required configuration server.
- The expiry date appears under Configuration Server health
- Click Renew Certificates.
Common issues
Installation failures
| Sample error message | Recommended action |
|---|---|
| ERROR Failed to load Accounts. Error: System.IO.IOException: Unable to read data from the transport connection when installing and registering the CS server. | Ensure that TLS 1.0 is enabled on the computer. |
Registration failures
Registration failures can be debugged by reviewing the logs in the %ProgramData%\ASRLogs folder.
| Sample error message | Recommended action |
|---|---|
| 09:20:06:InnerException.Type: SrsRestApiClientLib.AcsException,InnerException. Message: ACS50008: SAML token is invalid. Trace ID: 1921ea5b-4723-4be7-8087-a75d3f9e1072 Correlation ID: 62fea7e6-2197-4be4-a2c0-71ceb7aa2d97> Timestamp: 2016-12-12 14:50:08Z |
Ensure that the time on your system clock is not more than 15 minutes off the local time. Rerun the installer to complete the registration. |
| 09:35:27 :DRRegistrationException while trying to get all disaster recovery vault for the selected certificate: : Threw Exception.Type:Microsoft.DisasterRecovery.Registration.DRRegistrationException, Exception.Message: ACS50008: SAML token is invalid. Trace ID: e5ad1af1-2d39-4970-8eef-096e325c9950 Correlation ID: abe9deb8-3e64-464d-8375-36db9816427a Timestamp: 2016-05-19 01:35:39Z |
Ensure that the time on your system clock is not more than 15 minutes off the local time. Rerun the installer to complete the registration. |
| 06:28:45:Failed to create certificate 06:28:45:Setup cannot proceed. A certificate required to authenticate to Site Recovery cannot be created. Rerun Setup |
Ensure that you're running setup as a local administrator. |
Next steps
Review the tutorials for setting up disaster recovery of physical servers to Azure.