Muistiinpano
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää kirjautua sisään tai vaihtaa hakemistoa.
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää vaihtaa hakemistoa.
As a developer, you need to feel confident and secure to move at speed. The need for security starts as soon as you clone your code. In this article, you learn how to develop using Zero Trust principles so that you can innovate quickly and securely. The Zero Trust security strategy and approach for designing and implementing applications comprises these principles:
- Verify explicitly. Always authenticate and authorize based on all available data points.
- Use least privilege access. Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.
- Assume breach. Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Embedding security into your workflow helps you to:
- Pinpoint security vulnerabilities more quickly.
- Provide more secure developer tooling.
- Create connections to improve collaboration between security and development teams.
Innovate and secure your workflow as you create code
Microsoft's unified solution, illustrated in the following diagram, bridges across DevOps and SecOps teams to help you accelerate and secure code-to-cloud development.
Our solution to safeguard DevOps relies on two main components: providing developers with tooling to power innovation and securing the developer workflow as developers create code. Watch the Accelerate and secure your code to cloud development session from Microsoft Build 2022 to learn how these components can secure your development environment.
Implement the following best practices that work together in Azure and GitHub to secure your development solution.
- Because security starts when developers clone code, enable DevSecOps with Azure and GitHub to bridge across DevOps and SecOps teams and secure your development environments.
- Provide flexible and powerful developer tools for any developer, language, and stack with Visual Studio and Visual Studio Code.
- Simplify new developer onboarding and collaboration with an entire development lifecycle tool in the cloud using GitHub Codespaces and Microsoft Dev Box.
- Include built-in intellectual property protection for code that you no longer disperse into multiple locations. Help your teams collaborate, develop, automate, and deploy code wherever they want with GitHub Actions and Azure Pipelines.
- Get security guidance and continuous security feedback within the developer workflow with code scanning, secret scanning, and dependency review using GitHub Advanced Security.
- Instill zero-trust security throughout your organization using identity management services in Microsoft Entra ID.
Fit Zero Trust security into your development lifecycle
From precommit to commit through deploy then operate and monitor, you need security solutions in place throughout all of your development lifecycle stages.
Precommit stage
- Threat modeling
- IDE security plug-in
- Precommit hooks
- Secure coding standards
- Peer review
Eighty-five percent of code defects appear during the development precommitment phase, mostly due to human error. Focus on security before you commit your code by writing your code in Visual Studio Code, Visual Studio, or GitHub Codespaces to identify vulnerabilities and secure code. Use peer reviews to encourage secure coding practices.
Commit (CI) stage
- Static code analysis
- Security unit tests
- Dependency management
- Credential scanning
During the commit stage, use extensive security methods to review your code (including static code analysis) and scan your code as you check it into your source control. Use credential scanning (also known as secret scanning or token scanning) to expose credentials that you might inadvertently introduce into the codebase. Catch insecure dependencies before you introduce them to your environment with dependency review.
Deploy (CD) stage
- Infrastructure as code (IaC) scanning
- Dynamic security scanning
- Cloud configuration checks
- Security acceptance tests
During the deploy stage, look at the overall health of your codebase and perform high-level security scanning to identify risks. Perform cloud configuration checks, infrastructures code checks, and security acceptance tests to ensure alignment with organizational security goals.
Operate and monitor stage
- Continuous monitoring
- Threat intelligence
- Blameless postmortems
During the operate and monitor phase, use continuous monitoring and threat intelligence to mitigate overall dependency vulnerabilities that you might inherit over time. Perform postmortems to take away lessons learned and continue iterating through your DevOps cycle.
Implement dependency, code, and secret scanning
To make securing code easier for developers, use native and automated capabilities to provide continuous feedback with continuous security features throughout your development lifecycle. Provide overall security to developers and communities with GitHub Advanced Security dependency scanning, code scanning, and secret scanning.
Dependency scanning
- Integrated review of dependencies
- Alerts and security updates
Get risk levels of dependencies and automated fixes to vulnerable dependencies in your codebase with continuous dependency scanning. As a continuous process, it nudges your developers in the right direction in a friendly and nonobtrusive way.
Code scanning
- Extensible framework for code scanning
- Integrated within the developer workflow
- Backed by industry leading CodeQL engine
Implement code scanning as you generate code with no other steps to run at separate locations. Ease fixes early in your development lifecycle by viewing scanning results in your familiar GitHub user experience.
Secret scanning
- Scan for leaked secrets in public and private repos
- Partnership with 40+ providers
- Push protection
- Move from remediation to prevention
- Check for high-confidence secrets
- Enable protection with one select
Scan your code for hardcoded credentials and tokens with secret scanning. Push protection scans for secrets and tokens before you push to your codebase. Check for high-confidence secrets as developers push code, blocking the push when GitHub identifies a secret.
Manage and secure workload identities
- Lifecycle management
- Access governance
- Secure adaptive access
Get visibility into the activity of your workload identities and enable periodic cleanup. Determine who owns workload identities and how you keep this information up to date across organization changes. Track when you have last used workload identities, when you last issued tokens and when tokens expire.
To mitigate the potential for leaked secrets and credentials, periodically conduct access reviews. Require users to review their workload identities and remove unnecessary access privileges. Have users report overprivileged and underutilized access privileges. Discuss how you protect workload identities from breach. Enable conditional access to ensure that access is originating from expected resources.
Secure identities with GitHub OIDC and Microsoft Entra Workload ID Federation
To further secure your organization, use GitHub OpenID Connect (OIDC) with Microsoft Entra Workload Identity Federation and minimize the need to store and access secrets. Securely manage Azure server principal secrets and other long-lived cloud credentials resources to minimize service downtime due to expired credentials. Integrate with developer platforms, like GitHub Actions, to securely build your apps.
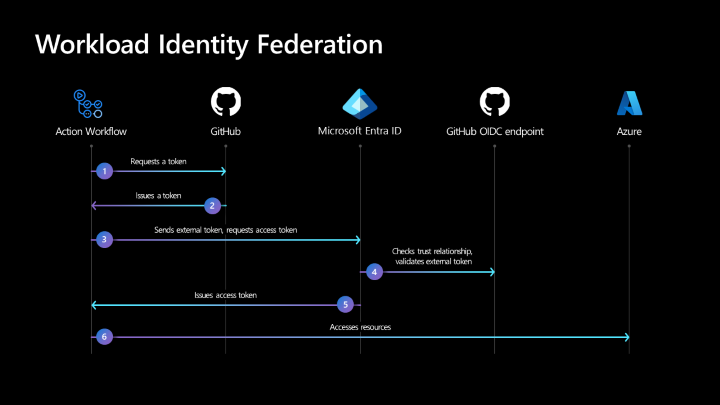
Our recommended Workload Identity Federation workflow, illustrated in the following diagram, comprises six steps.
- Set up trust in Microsoft Entra ID and request a token.
- Configure the GitHub workflow to allow actions to get the token.
- GitHub workflow sends a request to Azure ID.
- Microsoft Entra ID validates the trust on the application and fetches the keys to validate the token.
- Microsoft Entra ID accesses and issues the token.
- The deploy action uses the Microsoft Entra access token to deploy to resources in Azure.
Watch April Edwards, Senior Cloud Advocate and DevOps Practice Lead, demo the Workload Identity Federation workflow. The demonstration begins at the 19:14 mark in the Microsoft Build 2022 session, Accelerate and secure your code to cloud development.
Next steps
- Sign up for Azure Developer CLI, an open-source tool that accelerates the time it takes to get started on Azure.
- Configure Azure to trust GitHub's OIDC as a federated identity. OpenID Connect (OIDC) allows your GitHub Actions workflows to access resources in Azure without needing to store the Azure credentials as long-lived GitHub secrets.
- Implement Zero Trust principles as described in memorandum 22-09 (in support of US executive order 14028, Improving the Nation's Cyber Security) by using Microsoft Entra ID as a centralized identity management system.
- Accelerate and secure your code with Azure DevOps with tools that give developers the fastest and most secure code to cloud experience.
- Secure the developer environment helps you to implement Zero Trust principles in your development environments with best practices for least privilege, branch security, and trusting tools, extensions, and integrations.
- Secure DevOps environments for Zero Trust describes best practices for securing your DevOps environments for preventing hackers from compromising developer boxes, infecting release pipelines with malicious scripts, and gaining access to production data via test environments.
- Customize tokens describes the information that you can receive in Microsoft Entra tokens. It explains how to customize tokens to improve flexibility and control while increasing application zero trust security with least privilege.
- Configure group claims and app roles in tokens shows you how to configure your apps with app role definitions and assign security groups to app roles. These methods help to improve flexibility and control while increasing application zero trust security with least privilege.