Note
Ang pag-access sa pahinang ito ay nangangailangan ng pahintulot. Maaari mong subukang mag-sign in o magpalit ng mga direktoryo.
Ang pag-access sa pahinang ito ay nangangailangan ng pahintulot. Maaari mong subukang baguhin ang mga direktoryo.
Firewall reporting in the Microsoft Defender portal enables you to view Windows firewall reporting from a centralized location.
What do you need to know before you begin?
You open the Microsoft Defender portal at https://security.microsoft.com. To go directly to the Firewall page, use https://security.microsoft.com/firewall.
You need to be assigned permissions before you can do the procedures in this article. In Microsoft Entra ID you need to be a member of the Global Administrator* or Security Administrator roles.
Important
* Microsoft strongly advocates for the principle of least privilege. Assigning accounts only the minimum permissions necessary to perform their tasks helps reduce security risks and strengthens your organization's overall protection. Global Administrator is a highly privileged role that you should limit to emergency scenarios or when you can't use a different role.
Your devices must be running Windows 10 or later, or Windows Server 2012 R2 or later. For Windows Server 2012 R2 and Windows Server 2016 to appear in firewall reports, these devices must be onboarded using the modern unified solution package. For more information, see New functionality in the modern unified solution for Windows Server 2012 R2 and 2016.
To onboard devices to the Microsoft Defender for Endpoint service, see onboarding guidance.
For the Microsoft Defender portal to start receiving data, you must enable Audit Events for Windows Defender Firewall with Advanced Security. See the following articles:
Enable these events by using Group Policy Object Editor, Local Security Policy, or the auditpol.exe commands. For more information, see documentation about auditing and logging. The two PowerShell commands are as follows:
auditpol /set /subcategory:"Filtering Platform Packet Drop" /failure:enableauditpol /set /subcategory:"Filtering Platform Connection" /failure:enable
Here's an example query:
param ( [switch]$remediate ) try { $categories = "Filtering Platform Packet Drop,Filtering Platform Connection" $current = auditpol /get /subcategory:"$($categories)" /r | ConvertFrom-Csv if ($current."Inclusion Setting" -ne "failure") { if ($remediate.IsPresent) { Write-Host "Remediating. No Auditing Enabled. $($current | ForEach-Object {$_.Subcategory + ":" + $_.'Inclusion Setting' + ";"})" $output = auditpol /set /subcategory:"$($categories)" /failure:enable if($output -eq "The command was successfully executed.") { Write-Host "$($output)" exit 0 } else { Write-Host "$($output)" exit 1 } } else { Write-Host "Remediation Needed. $($current | ForEach-Object {$_.Subcategory + ":" + $_.'Inclusion Setting' + ";"})." exit 1 } } } catch { throw $_ }
The process
Note
Make sure to follow the instructions from previous the section and properly configure your devices to participate in the preview program.
After events are enabled, Microsoft Defender for Endpoint begins to monitor data, which includes:
- Remote IP
- Remote Port
- Local Port
- Local IP
- Computer Name
- Process across inbound and outbound connections
Admins can now see Windows host firewall activity here. Additional reporting can be facilitated by downloading the Custom Reporting script to monitor the Windows Defender Firewall activities using Power BI.
It can take up to 12 hours before the data is reflected.
Supported scenarios
- Firewall reporting
- From "Computers with a blocked connection" to device (requires Defender for Endpoint Plan 2)
- Drill into advanced hunting (preview refresh) (requires Defender for Endpoint Plan 2)
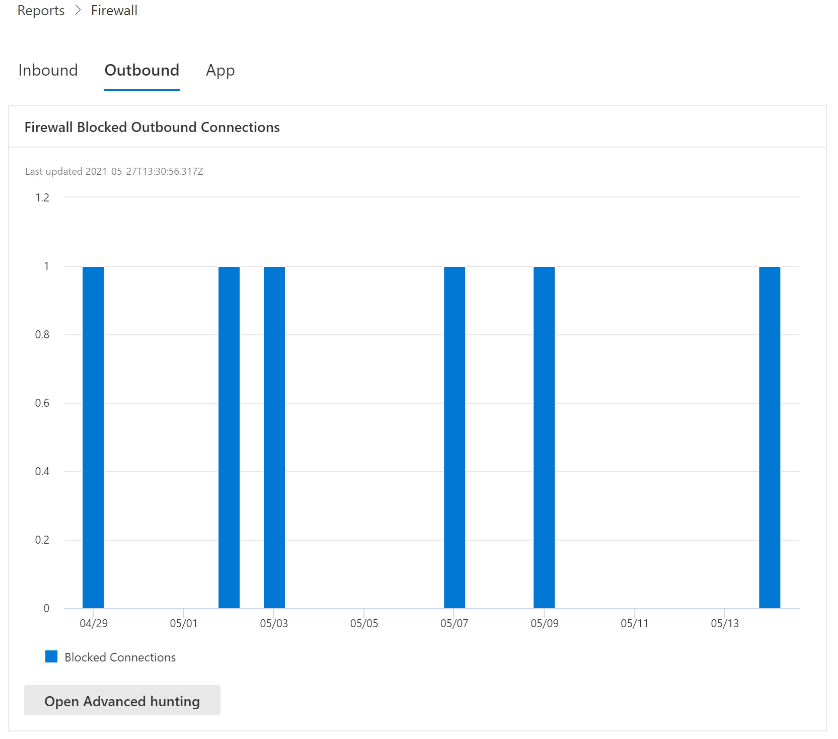
Firewall reporting
Here are some examples of the firewall report pages in the Microsoft Defender portal. The Firewall page contains the Inbound, Outbound, and App tabs. You access this page at Reports > Endpoints section > Firewall or directly at https://security.microsoft.com/firewall.
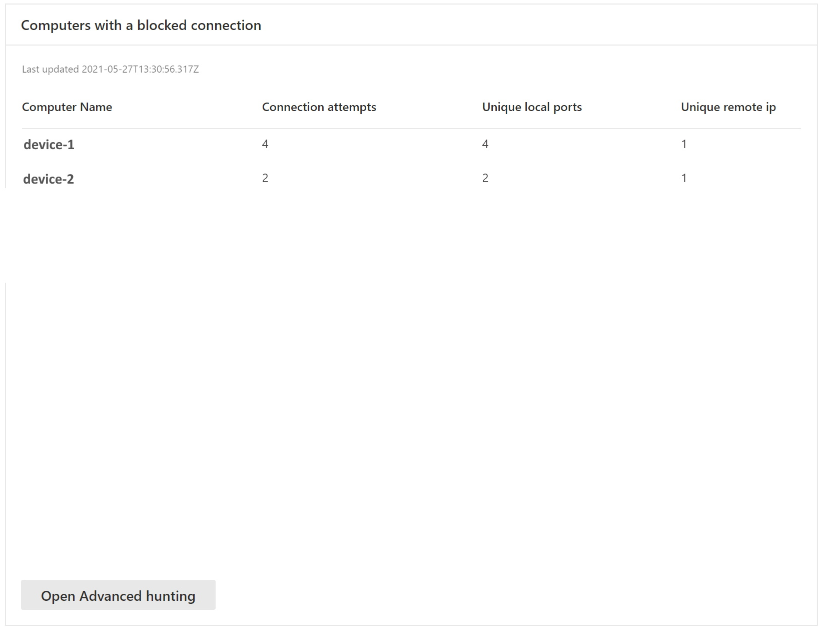
From "Computers with a blocked connection" to device
Note
This feature requires Defender for Endpoint Plan 2.
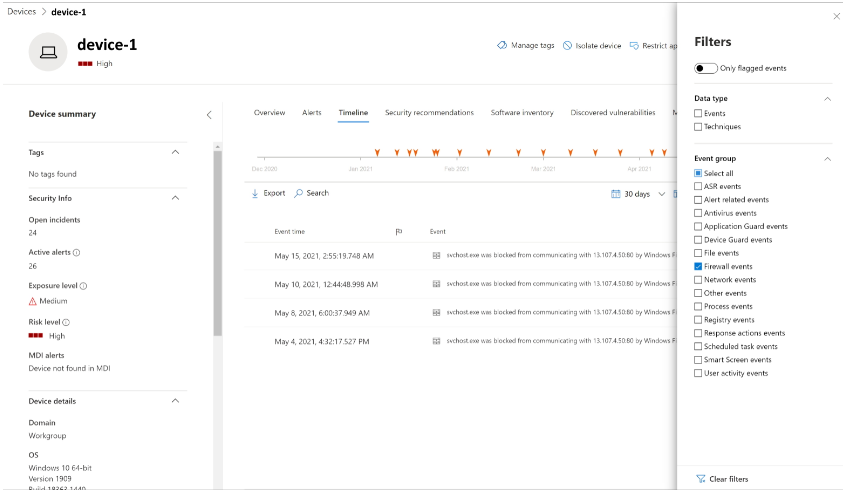
Cards support interactive objects. You can drill into the activity of a device by clicking on the device name, which will launch the Microsoft Defender portal in a new tab, and take you directly to the Device Timeline tab.
You can now select the Timeline tab, which will give you a list of events associated with that device.
After clicking on the Filters button on the upper right-hand corner of the viewing pane, select the type of event you want. In this case, select Firewall events and the pane will be filtered to Firewall events.
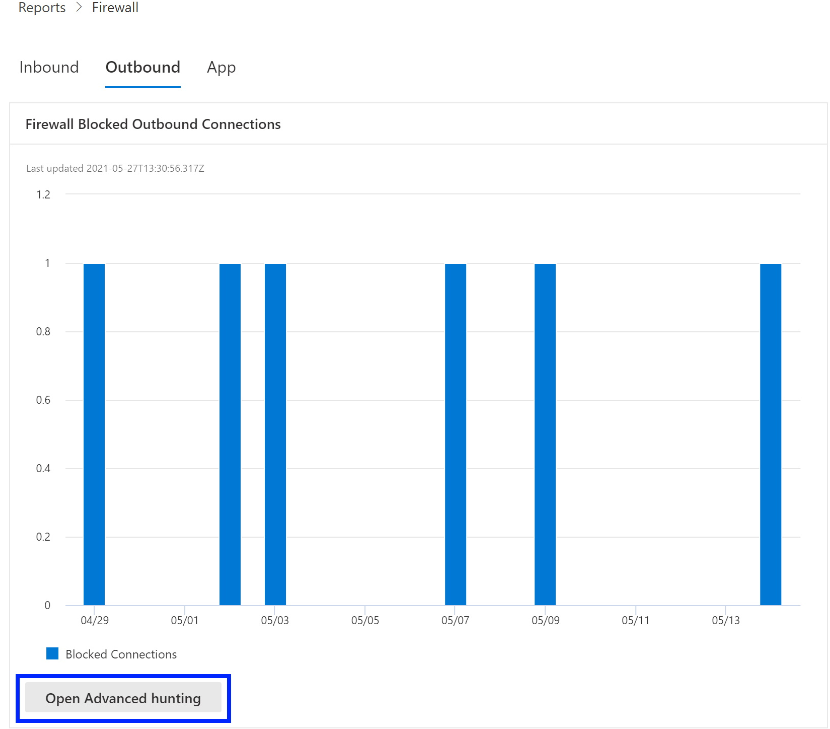
Drill into advanced hunting (preview refresh)
Note
This feature requires Defender for Endpoint Plan 2.
Firewall reports support drilling from the card directly into Advanced Hunting by clicking the Open Advanced hunting button. The query is prepopulated.
The query can now be executed, and all related Firewall events from the last 30 days can be explored.
For more reporting, or custom changes, the query can be exported into Power BI for further analysis. Custom reporting can be facilitated by downloading the Custom Reporting script to monitor the Windows Defender Firewall activities using Power BI.
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.