Kaganapan
Abr 9, 3 PM - Abr 10, 12 PM
Code ang Hinaharap sa AI at kumonekta sa mga kabarkada at eksperto sa Java sa JDConf 2025.
Magparehistro NaHindi na suportado ang browser na ito.
Mag-upgrade sa Microsoft Edge para samantalahin ang mga pinakabagong tampok, update sa seguridad, at teknikal na suporta.
If your organization is federated with Microsoft Entra ID, use Microsoft Entra multifactor authentication or Active Directory Federation Services (AD FS) to secure resources that are accessed by Microsoft Entra ID. Use the following procedures to secure Microsoft Entra resources with either Microsoft Entra multifactor authentication or Active Directory Federation Services.
Note
Set the domain setting federatedIdpMfaBehavior to enforceMfaByFederatedIdp (recommended) or SupportsMFA to $True. The federatedIdpMfaBehavior setting overrides SupportsMFA when both are set.
To secure your cloud resource, set up a claims rule so that Active Directory Federation Services emits the multipleauthn claim when a user performs two-step verification successfully. This claim is passed on to Microsoft Entra ID. Follow this procedure to walk through the steps:
Open AD FS Management.
On the left, select Relying Party Trusts.
Right-select on Microsoft Office 365 Identity Platform and select Edit Claim Rules.

On Issuance Transform Rules, select Add Rule.

On the Add Transform Claim Rule Wizard, select Pass Through or Filter an Incoming Claim from the drop-down and select Next.
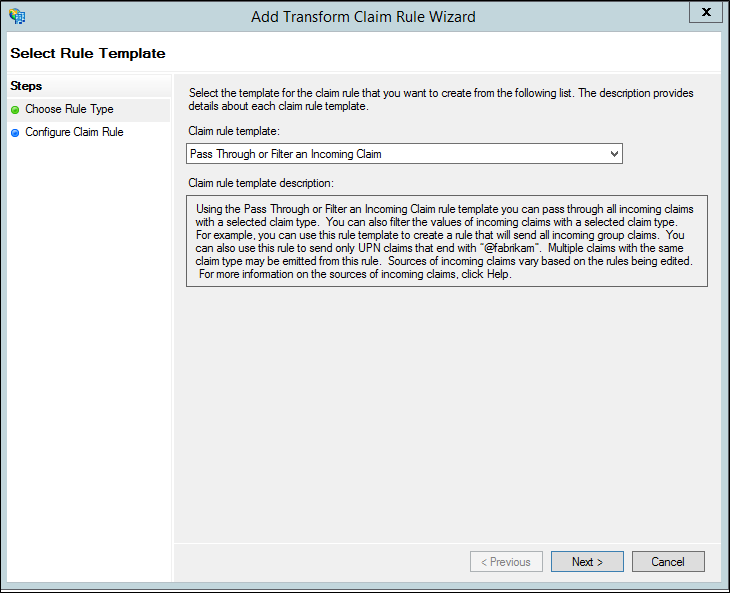
Give your rule a name.
Select Authentication Methods References as the Incoming claim type.
Select Pass through all claim values.

Select Finish. Close the AD FS Management console.
Trusted IPs allow administrators to bypass two-step verification for specific IP addresses, or for federated users who have requests originating from within their own intranet. The following sections describe how to configure the bypass using Trusted IPs. This is achieved by configuring AD FS to use a pass-through or filter an incoming claim template with the Inside Corporate Network claim type.
This example uses Microsoft 365 for our Relying Party Trusts.
The first thing we need to do is to configure the AD FS claims. Create two claims rules, one for the Inside Corporate Network claim type and an additional one for keeping our users signed in.
Open AD FS Management.
On the left, select Relying Party Trusts.
Right-select on Microsoft Office 365 Identity Platform and select Edit Claim Rules…

On Issuance Transform Rules, select Add Rule.

On the Add Transform Claim Rule Wizard, select Pass Through or Filter an Incoming Claim from the drop-down and select Next.

In the box next to Claim rule name, give your rule a name. For example: InsideCorpNet.
From the drop-down, next to Incoming claim type, select Inside Corporate Network.

Select Finish.
On Issuance Transform Rules, select Add Rule.
On the Add Transform Claim Rule Wizard, select Send Claims Using a Custom Rule from the drop-down and select Next.
In the box under Claim rule name: enter Keep Users Signed In.
In the Custom rule box, enter:
c:[Type == "https://schemas.microsoft.com/2014/03/psso"]
=> issue(claim = c);
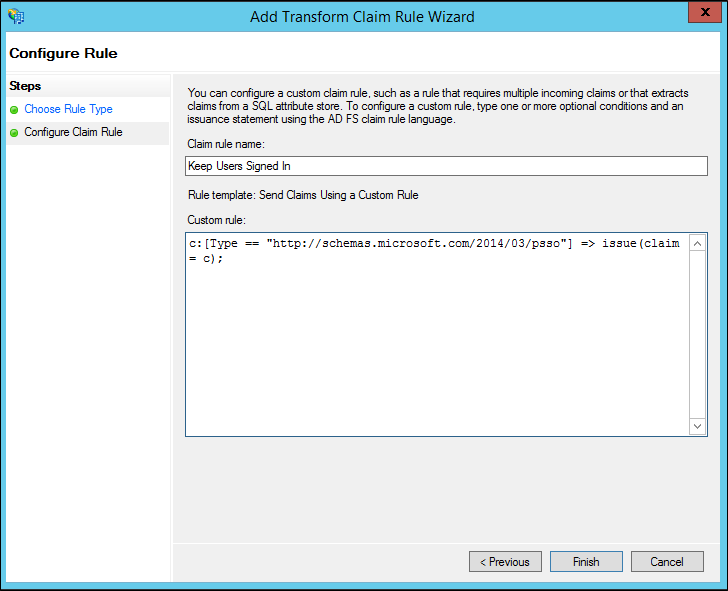
Select Finish.
Select Apply.
Select Ok.
Close AD FS Management.
Now that the claims are in place, we can configure trusted IPs.
Sign in to the Microsoft Entra admin center as at least an Authentication Policy Administrator.
Browse to Conditional Access > Named locations.
From the Conditional Access - Named locations blade, select Configure MFA trusted IPs

On the Service Settings page, under trusted IPs, select Skip multifactor-authentication for requests from federated users on my intranet.
Select save.
That's it! At this point, federated Microsoft 365 users should only have to use MFA when a claim originates from outside the corporate intranet.
Kaganapan
Abr 9, 3 PM - Abr 10, 12 PM
Code ang Hinaharap sa AI at kumonekta sa mga kabarkada at eksperto sa Java sa JDConf 2025.
Magparehistro NaPagsasanay
Module
Secure Microsoft Entra users with multifactor authentication - Training
Learn how to use multifactor authentication with Microsoft Entra ID to harden your user accounts.
Sertipikasyon
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Dokumentasyon
Two-step verification Microsoft Entra multifactor authentication and ADFS - Microsoft Entra ID
This is the Microsoft Entra multifactor authentication page that describes how to get started with Microsoft Entra multifactor authentication and AD FS.
Migrate to Microsoft Entra multifactor authentication with federations - Microsoft Entra ID
Step-by-step guidance to move from MFA Server on-premises to Microsoft Entra multifactor authentication with federation
Configure AD FS and Microsoft Entra multifactor authentication
Learn more about configuring Microsoft Entra multifactor authentication as authentication provider using AD FS.