הערה
הגישה לדף זה מחייבת הרשאה. באפשרותך לנסות להיכנס או לשנות מדריכי כתובות.
הגישה לדף זה מחייבת הרשאה. באפשרותך לנסות לשנות מדריכי כתובות.
חל על: Advanced Threat Analytics גירסה 1.9
ATA מספק זיהוי עבור השלבים השונים הבאים של מתקפה מתקדמת: סיור מחדש, פשרה באישור, תנועה רוחבית, הסלמת הרשאה, פיקוח על תחום ואחרים. זיהויים אלה מיועדים לזהות התקפות מתקדמות ואיומים פנימיים לפני שהם עלולים לגרום נזק לארגון שלך. הזיהוי של כל שלב התוצאה היא מספר פעילויות חשודות הרלוונטיות לשלב המדובר, שבו כל פעילות חשודה מתאם לטעמים שונים של מתקפות אפשריות. שלבים אלה בשרשרת ה- Kill שבהם ATA מספק כעת זיהויים מסומנים בתמונה הבאה:
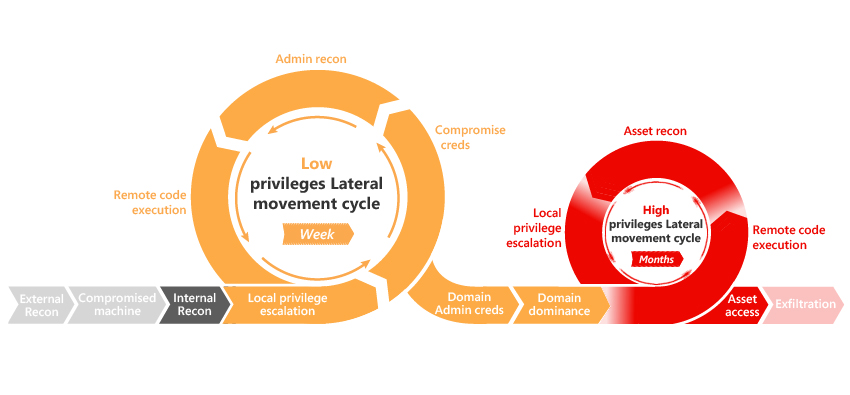
לקבלת מידע נוסף, ראה עבודה עם פעילויות חשודות ומדריך הפעילות החשודה של ATA.
מה עכשיו?
לקבלת מידע נוסף אודות האופן שבו ATA מתאים לרשת שלך: ארכיטקטורת ATA
כדי להתחיל לפרוס את ATA: התקנת ATA