הערה
הגישה לדף זה מחייבת הרשאה. באפשרותך לנסות להיכנס או לשנות מדריכי כתובות.
הגישה לדף זה מחייבת הרשאה. באפשרותך לנסות לשנות מדריכי כתובות.
חל על: Advanced Threat Analytics גירסה 1.9
מאמר זה מסביר את היסודות של אופן העבודה עם Advanced Threat Analytics.
סקור פעילויות חשודות על קו הזמן של ההתקפה
לאחר הכניסה למסוף ATA, אתה עובר באופן אוטומטי לקו הזמן הפתוח של פעילויות חשודות. פעילויות חשודות מפורטות בסדר כרונולוגי כאשר הפעילויות החשודות החדשות ביותר מופיעות בראש ציר הזמן. לכל פעילות חשודה יש את המידע הבא:
ישויות המעורבות, כולל משתמשים, מחשבים, שרתים, בקרי תחום ומשאבים.
שעות ומסגרת זמן של הפעילויות החשודות.
חומרת הפעילות החשודה, גבוהה, בינונית או נמוכה.
מצב: פתוח, סגור או מודחק.
היכולת
שתף את הפעילות החשודה עם אנשים אחרים בארגון שלך באמצעות דואר אלקטרוני.
יצא את הפעילות החשודה ל- Excel.
הערה
- בעת ריחוף עם העכבר מעל משתמש או מחשב, מוצג פרופיל מצומצם של ישות המספק מידע נוסף אודות הישות וכולל את מספר הפעילויות החשודות שאליהן הישות מקושרת.
- אם תלחץ על ישות, היא ת מעביר אותך לפרופיל הישות של המשתמש או המחשב.
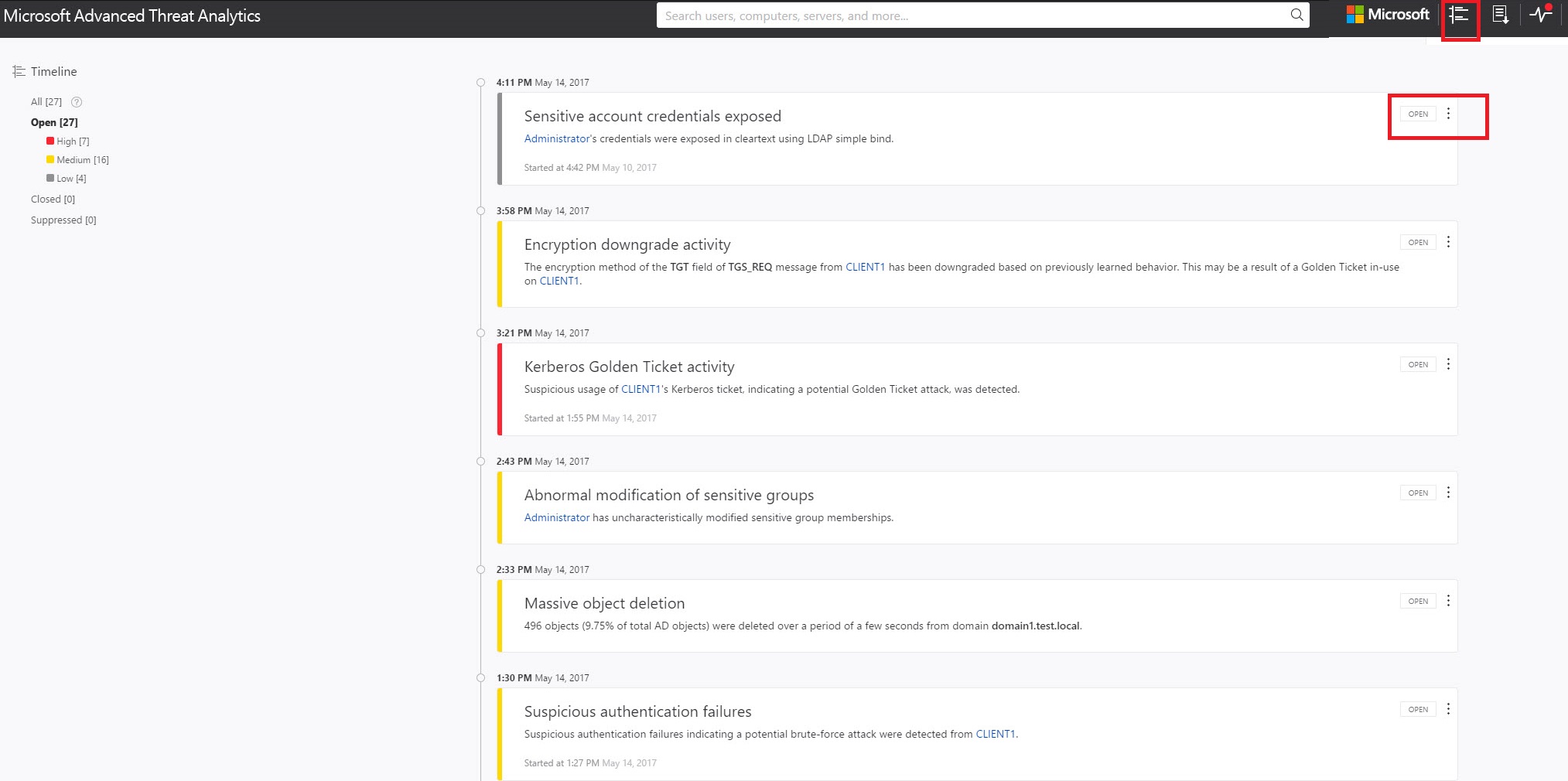
סנן רשימת פעילויות חשודות
כדי לסנן את רשימת הפעילויות החשודות:
בחלונית סנן לפי בצד הימני של המסך, בחר אחת מהאפשרויות הבאות: הכל, פתיחה, סגורה או מודחקת.
כדי לסנן עוד יותר את הרשימה, בחר גבוהה, בינונית או נמוכה.
חומרת פעילות חשודה
נמוך
מציין פעילויות חשודות שעלולות להוביל לתקיפות המיועדות למשתמשים או תוכנות זדוניים לקבל גישה לנתונים ארגוניים.
בינוני
ציון פעילויות חשודות שעלולות לסכן זהויות ספציפיות להתקפות חמורות יותר שעלולות לגרום לגניבת זהויות או להסלמה עם הרשאות
גבוהה
ציון פעילויות חשודות שעלולות להוביל לגניבת זהות, להסלמה של הרשאות או להתקפות אחרות עם השפעה גבוהה
תיקון פעילויות חשודות
באפשרותך לשנות את המצב של פעילות חשודה על-ידי לחיצה על המצב הנוכחי של הפעילות החשודה ובחירה באחת מהאפשרויות הבאות: 'פתוח', 'מודחק', 'סגור' או 'נמחק'. לשם כך, לחץ על שלוש הנקודות בפינה השמאלית העליונה של פעילות חשודה ספציפית כדי לחשוף את רשימת הפעולות הזמינות.

מצב פעילות חשודה
פתיחה: כל הפעילויות החשודות החדשות מופיעות ברשימה זו.
סגור: משמש למעקב אחר פעילויות חשודות שזיהית, חקרת ותקןת לצורך צמצום.
הערה
אם אותה פעילות מזוהה שוב בתוך פרק זמן קצר, ATA עשוי לפתוח מחדש פעילות סגורה.
העלם: המשמעות של העלמת פעילות היא שברצונך להתעלם ממנה בשלב זה, ותתריע שוב רק אם קיים מופע חדש. משמעות הדבר היא שאם ישנה התראה דומה, ATA לא פותח אותה מחדש. אך אם ההתראה נעצרת למשך שבעה ימים, ולאחר מכן היא מופיעה שוב, תקבל התראה נוספת.
מחיקה: אם תמחק התראה, היא תימחק מהמערכת, ממסד הנתונים ולא תוכל לשחזר אותה. לאחר שתלחץ על מחק, תוכל למחוק את כל הפעילויות החשודות מאותו סוג.
אל תכלול: היכולת לא לכלול ישות בגידול סוג מסוים של התראות. לדוגמה, באפשרותך להגדיר ש- ATA לא יכלול ישות ספציפית (משתמש או מחשב) בהתראות שוב עבור סוג מסוים של פעילות חשודה, כגון מנהל מערכת ספציפי שמפעיל קוד מרוחק או סורק אבטחה שמפעיל מחדש DNS. בנוסף להיכולת להוסיף אי-הכללות ישירות בפעילות החשודה כפי שהיא מזוהה בשורת הזמן, באפשרותך גם לעבור לדף 'קביעת תצורה' אל 'אי-הכללה ', ועבור כל פעילות חשודה, באפשרותך להוסיף ולהסיר באופן ידני ישויות או רשתות משנה שלא נכללו (לדוגמה, עבור Pass-the-Ticket).
הערה
רק מנהלי מערכת של ATA יכולים לשנות את דפי התצורה.