עבודה עם מסוף ATA
חל על: Advanced Threat Analytics גירסה 1.9
השתמש במסוף ATA כדי לנטר פעילות חשודה שזוהתה על-ידי ATA ולהגיב עליה.
הקלדת המקש ? מספקת קיצורי מקשים עבור נגישות בפורטל ATA.
הפעלת גישה למסוף ATA
כדי להיכנס בהצלחה למסוף ATA, עליך להיכנס באמצעות משתמש שהוקצה לו תפקיד ATA מתאים כדי לגשת למסוף ATA. לקבלת מידע נוסף אודות בקרת גישה מבוססת תפקידים (RBAC) ב- ATA, ראה עבודה עם קבוצות תפקידים של ATA.
כניסה למסוף ATA
הערה
החל מ- ATA 1.8, תהליך הכניסה למסוף ATA מושג באמצעות כניסה יחידה.
בשרת ATA Center, לחץ על סמל Microsoft ATA Console בשולחן העבודה או פתח דפדפן ונווט אל מסוף ATA.

הערה
באפשרותך גם לפתוח דפדפן מתוך מרכז ATA או שער ATA ולגלוש לכתובת ה- IP שאת תצורתה קבעת בהתקנת מרכז ATA עבור מסוף ATA.
אם המחשב שבו מותקן מרכז ה- ATA והמחשב ממנו אתה מנסה לגשת למסוף ATA מחוברים שניהם לתחום, ATA תומך בכניסה יחידה המשולבת עם אימות Windows - אם כבר נכנסת למחשב שלך, ATA משתמש אסימוני זה כדי להיכנס למסוף ATA. באפשרותך גם להיכנס באמצעות כרטיס חכם. ההרשאות שלך ב- ATA תואמות לתפקיד מנהל המערכת שלך.
הערה
הקפד להיכנס למחשב שבו ברצונך לגשת למסוף ATA באמצעות שם המשתמש והסיסמה של מנהל המערכת של ATA. לחלופין, באפשרותך להפעיל את הדפדפן כמשתמש אחר או לצאת מ- Windows ולהיכנס עם משתמש מנהל המערכת של ATA. כדי לבקש ממסוף ה- ATA לבקש אישורים, גש לקונסולה באמצעות כתובת IP ואתה מתבקש להזין אישורים.
כדי להיכנס באמצעות SSO, ודא שאתר מסוף ATA מוגדר כאתר אינטרא-נט מקומי בדפדפן שלך ושתלגשת אליו באמצעות שם קצר או אירוח מקומי.
הערה
בנוסף לרישום כל פעילות חשודה והתראה של תקינות, כל שינוי תצורה שאתה מבצע במסוף ATA מוזמן ביומן האירועים של Windows במחשב של מרכז ATA, תחת יומן יישומים ושירותים ולאחר מכן Microsoft ATA. כל כניסה למסוף ATA מביקורת גם כן.
תצורה המשפיעה על שער ATA נרשמת גם ביומן האירועים של Windows במחשב שער ATA.
מסוף ATA
מסוף ATA מספק לך תצוגה מהירה של כל הפעילויות החשודות בסדר כרונולוגי. הוא מאפשר לך להסתעף לפרטים של פעילות כלשהי ולבצע פעולות בהתבסס על פעילויות אלה. הקונסולה מציגה גם התראות והודעות כדי להדגיש בעיות ברשת ATA או פעילויות חדשות שנראה חשודות.
אלה הם הרכיבים העיקריים של מסוף ATA.
קו זמן תקיפה
זהו דף היעד המוגדר כברירת מחדל שאתה נלקח אל כאשר אתה נכנס למסוף ATA. כברירת מחדל, כל הפעילויות החשודות הפתוחות מוצגות בשורת זמן התקיפה. באפשרותך לסנן את קו זמן התקיפה כדי להציג פעילויות חשודות, פעילויות 'הכל', 'פתוח', 'מבוטל' או 'מודחק'. באפשרותך גם לראות את החומרה שהוקצתה לכל פעילות.
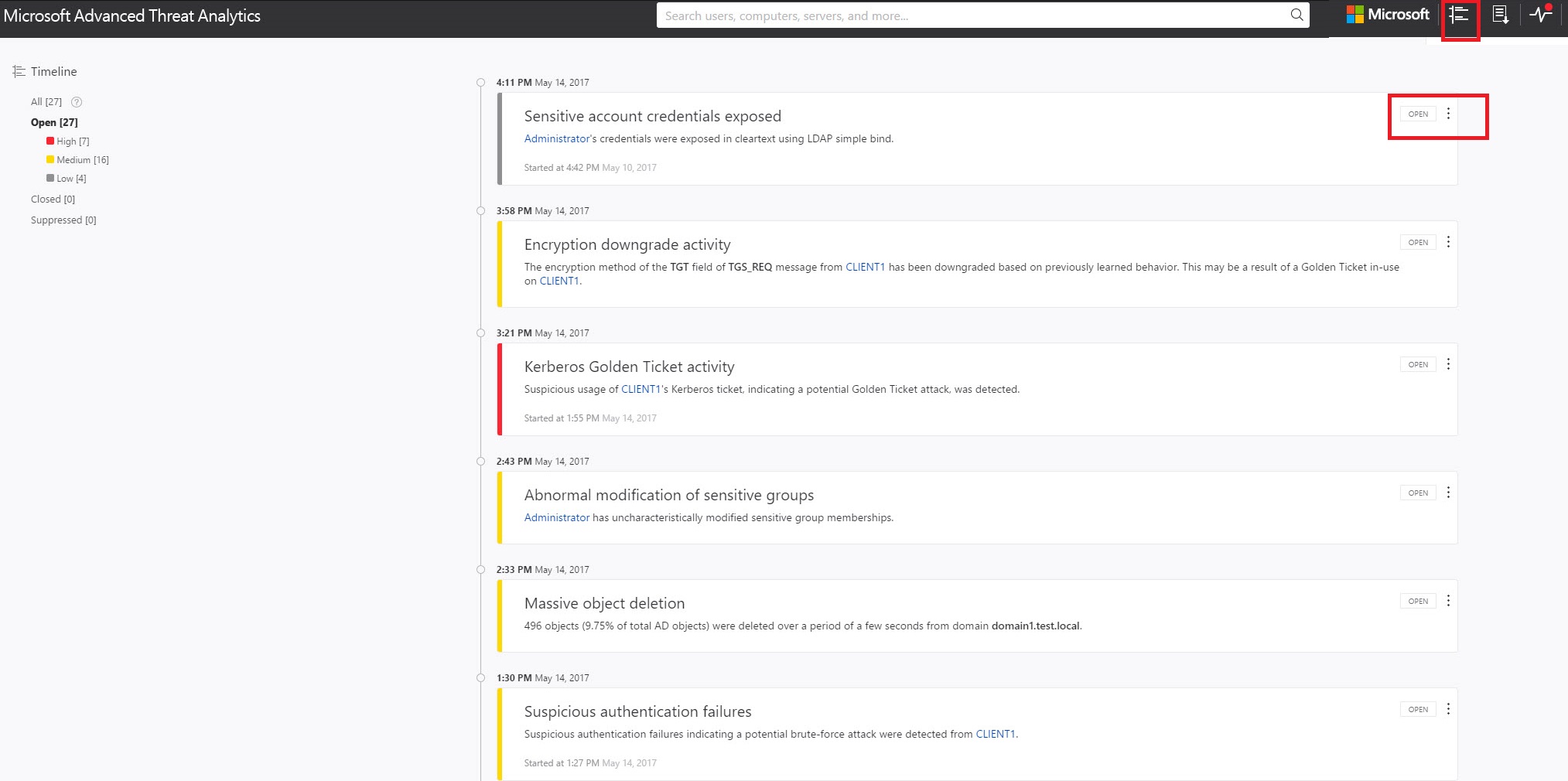
לקבלת מידע נוסף, ראה עבודה עם פעילויות חשודות.
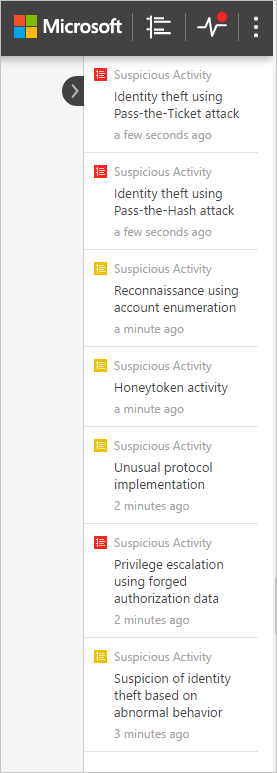
סרגל ההודעות
כאשר מזוהה פעילות חשודה חדשה, סרגל ההודעות נפתח באופן אוטומטי בצד שמאל. אם קיימות פעילויות חשודות חדשות מאז הפעם האחרונה שנכנסת, סרגל ההודעות ייפתח לאחר שתיכנס בהצלחה. באפשרותך ללחוץ על החץ משמאל בכל עת כדי לגשת אל סרגל ההודעות.
מה חדש
לאחר שגירסה חדשה של ATA מופצת, החלון מה חדש מופיע בפינה השמאלית העליונה כדי לעדכן אותך מה נוסף בגירסה העדכנית ביותר. הוא גם מספק לך קישור להורדת הגירסה.
לוח סינון
באפשרותך לסנן את הפעילויות החשודות המוצגות בשורת זמן התקיפה או מוצגות בכרטיסיה פעילויות חשודות בפרופיל הישות בהתבסס על מצב וחומרה.
סרגל החיפוש
בתפריט העליון, באפשרותך למצוא סרגל חיפוש. באפשרותך לחפש משתמש, מחשב או קבוצות ספציפיים ב- ATA. כדי לנסות זאת, פשוט התחל להקליד.
מרכז הבריאות
מרכז הבריאות מספק לך התראות כאשר משהו אינו פועל כראוי בפריסת ATA.
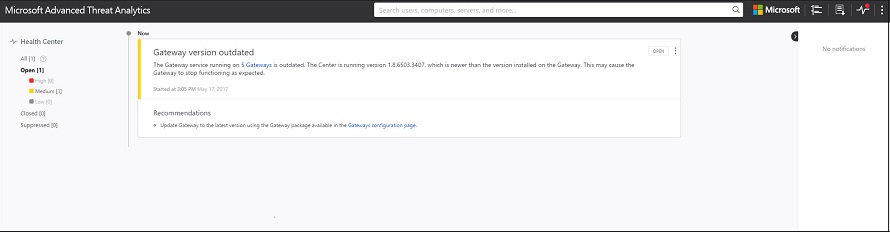
בכל פעם שהמערכת נתקלת בבעיה, כגון שגיאת קישוריות או שער ATA מנותק, סמל מרכז התקינות מיידע אותך על-ידי הצגת נקודה אדומה.
קבוצות רגישות
רשימת הקבוצות הבאה נחשבת לרגישה על-ידי ATA. כל ישות שהוא חבר בקבוצות אלה נחשבת לרגישה:
- בקרי תחום לקריאה בלבד של ארגון
- מנהלי תחום
- בקרי תחום
- מנהלי סכימה,
- מנהלי מערכת ארגוניים
- מדיניות קבוצתית של היוצרים
- בקרי תחום לקריאה בלבד
- מנהלי מערכת
- משתמשים מתקדמים
- מפעילי חשבון
- אופרטורים של שרת
- אופרטורים להדפסה,
- מפעילי גיבוי,
- משכפלים (משכפלים)
- משתמשי שולחן עבודה מרוחק
- אופרטורים של תצורת רשת
- בונה יחסי אמון של יער נכנס
- מנהלי DNS
פרופיל מצומצם
אם אתה מרחף עם העכבר מעל ישות, בכל מקום בקונסולה שבה מוצגת ישות בודדת, כגון משתמש או מחשב, נפתח פרופיל מצומצם באופן אוטומטי המציג את המידע הבא אם זמין:

Name
תמונה
דואר אלקטרוני
טלפון
מספר פעילויות חשודות לפי חומרה