Događaj
9. tra 15 - 10. tra 12
Programirajte budućnost s umjetnom inteligencijom i povežite se s Java kolegama i stručnjacima na JDConfu 2025.
Registrirajte se odmahOvaj preglednik više nije podržan.
Prijeđite na Microsoft Edge, gdje vas čekaju najnovije značajke, sigurnosna ažuriranja i tehnička podrška.
This article shows you how to assign users and groups to an enterprise application in Microsoft Entra ID. When you assign a user to an application, the application appears in the user's My Apps portal for easy access. If the application exposes app roles, you can also assign a specific app role to the user.
When you assign a group to an application, only users in the group have access. The assignment doesn't cascade to nested groups.
Group-based assignment requires Microsoft Entra ID P1 or P2 edition. Group-based assignment is supported for Security groups, Microsoft 365 groups, and Distribution groups whose SecurityEnabled setting is set to True only. Nested group memberships aren't currently supported. For more licensing requirements for the features discussed in this article, see the Microsoft Entra pricing page.
For greater control, certain types of enterprise applications can be configured to require user assignment. For more information on requiring user assignment for an app, see Manage access to an application. Applications that require users to be assigned to the application must have their permissions consented by an administrator, even if the user consent policies for your directory would otherwise allow a user to consent on behalf of themselves.
Napomena
If you encounter limitations when managing groups through the portal, such as with application access policy groups, consider using alternative methods like PowerShell or Microsoft Graph API.
To assign users to an enterprise application, you need:
To assign a user or group account to an enterprise application:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > All applications.
Enter the name of the existing application in the search box, and then select the application from the search results.
Select Users and groups, and then select Add user/group.
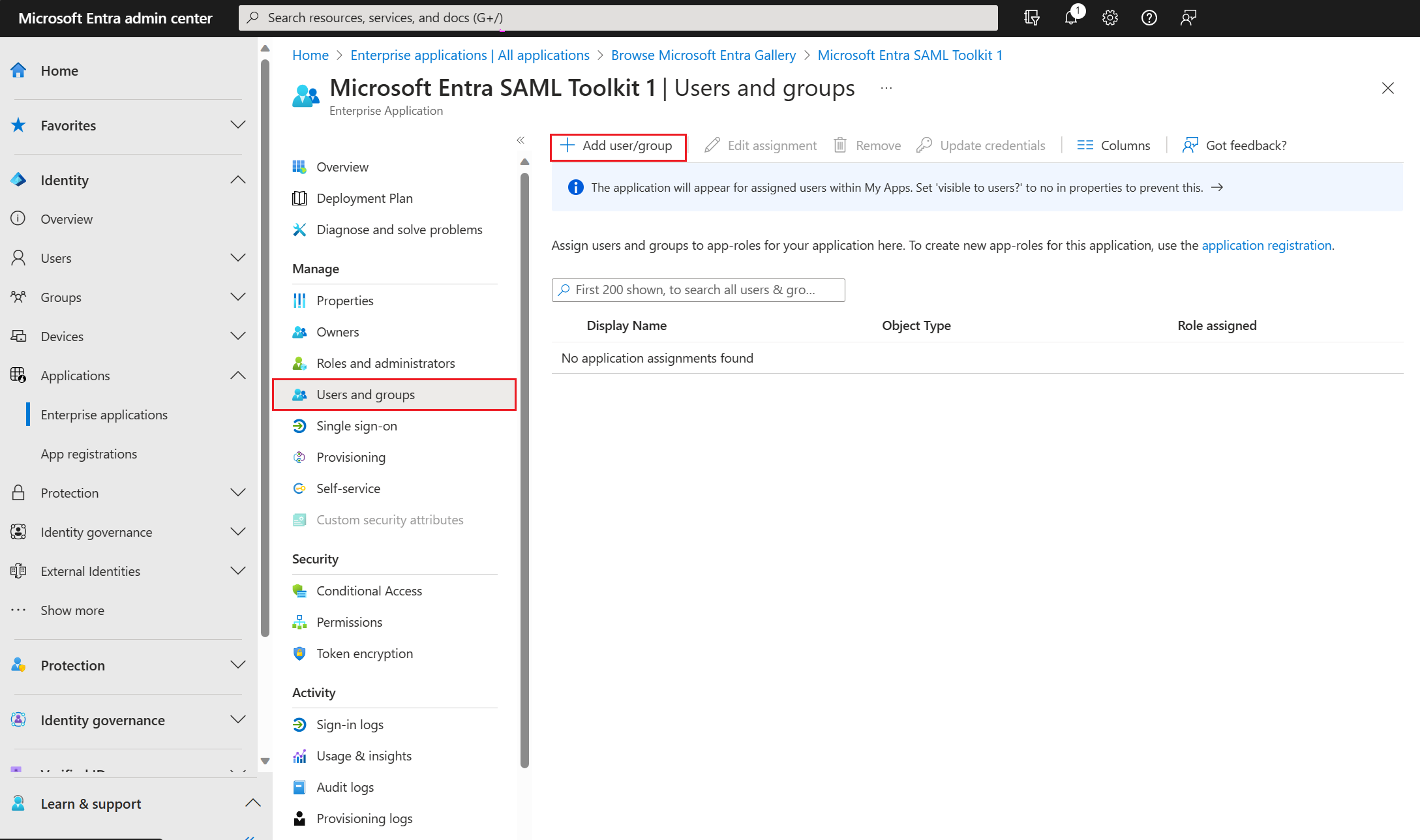
On the Add Assignment pane, select None Selected under Users and groups.
Search for and select the user or group that you want to assign to the application. For example, contosouser1@contoso.com or contosoteam1@contoso.com.
Select Select.
Under Select a role, select the role that you want to assign to the user or group. If you haven't defined any roles yet, the default role is Default Access.
On the Add Assignment pane, select Assign to assign the user or group to the application.
Sign in as at least a Cloud Application Administrator.
Use the following script to assign a user to an application:
connect-entra -scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
# Assign the values to the variables
$username = "<Your user's UPN>"
$app_name = "<Your App's display name>"
$app_role_name = "<App role display name>"
# Get the user to assign, and the service principal for the app to assign to
$user = Get-EntraUser -ObjectId "$username"
$sp = Get-EntraServicePrincipal -Filter "displayName eq '$app_name'"
$appRole = $sp.AppRoles | Where-Object { $_.DisplayName -eq $app_role_name }
# Assign the user to the app role
New-EntraUserAppRoleAssignment -ObjectId $user.ObjectId -PrincipalId $user.ObjectId -ResourceId $sp.ObjectId -Id $appRole.Id
This example assigns the user Britta Simon to the Microsoft Workplace Analytics application using PowerShell.
In PowerShell, assign the corresponding values to the variables $username, $app_name, and $app_role_name.
connect-entra -scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
$username = "britta.simon@contoso.com"
$app_name = "Workplace Analytics"
In this example, we don't know what is the exact name of the application role we want to assign to Britta Simon. Run the following commands to get the user ($user) and the service principal ($sp) using the user UPN and the service principal display names.
$user = Get-EntraUser -ObjectId "$username"
$sp = Get-EntraServicePrincipal -Filter "displayName eq '$app_name'"
Run the following command to find the app roles exposed by the service principal
$appRoles = $sp.AppRoles
# Display the app roles
$appRoles | ForEach-Object {
Write-Output "AppRole: $($_.DisplayName) - ID: $($_.Id)"
}
Napomena
The default AppRole ID is 00000000-0000-0000-0000-000000000000. This role is assigned when no specific AppRole is defined for a service principal.
Assign the AppRole name to the $app_role_name variable. In this example, we want to assign Britta Simon the Analyst (Limited access) Role.
$app_role_name = "Analyst (Limited access)"
$appRole = $sp.AppRoles | Where-Object { $_.DisplayName -eq $app_role_name }
Run the following command to assign the user to the app role.
New-EntraUserAppRoleAssignment -ObjectId $user.ObjectId -PrincipalId $user.ObjectId -ResourceId $sp.ObjectId -Id $appRole.Id
To assign a group to an enterprise app, replace Get-EntraUser with Get-EntraGroup and replace New-EntraUserAppRoleAssignment with New-EntraGroupAppRoleAssignment.
For more information on how to assign a group to an application role, see the documentation for New-EntraGroupAppRoleAssignment.
Open an elevated Windows PowerShell command prompt.
Sign in as at least a Cloud Application Administrator.
Use the following script to remove a user and role from an application.
connect-entra -scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
# Store the proper parameters
$user = Get-Entrauser -ObjectId "<objectId>"
$spo = Get-EntraServicePrincipal -ObjectId "<objectId>"
#Get the ID of role assignment
$assignments = Get-EntraServicePrincipalAppRoleAssignedTo -ObjectId $spo.ObjectId | Where {$_.PrincipalDisplayName -eq $user.DisplayName}
#if you run the following, it will show you what is assigned what
$assignments | Select *
#To remove the App role assignment run the following command.
Remove-EntraServicePrincipalAppRoleAssignment -ObjectId $spo.ObjectId -AppRoleAssignmentId $assignments.ObjectId
Use the following script to remove all users and groups assigned to the application.
connect-entra -scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
#Retrieve the service principal object ID.
$app_name = "<Your App's display name>"
$sp = Get-EntraServicePrincipal -Filter "displayName eq '$app_name'"
# Get Microsoft Entra App role assignments using objectId of the Service Principal
$assignments = Get-EntraServicePrincipalAppRoleAssignedTo -ObjectId $sp.ObjectId -All
# Remove all users and groups assigned to the application
$assignments | ForEach-Object {
if ($_.PrincipalType -eq "User") {
Remove-EntraUserAppRoleAssignment -ObjectId $_.PrincipalId -AppRoleAssignmentId $_.ObjectId
} elseif ($_.PrincipalType -eq "Group") {
Remove-EntraGroupAppRoleAssignment -ObjectId $_.PrincipalId -AppRoleAssignmentId $_.ObjectId
}
}
Open an elevated Windows PowerShell command prompt.
Run Connect-MgGraph -Scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All" and sign in as at least a Cloud Application Administrator.
Use the following script to assign a user to an application:
#Assign the values to the variables
$userId = "<Your user's ID>"
$app_name = "<Your App's display name>"
$app_role_name = "<App role display name>"
$sp = Get-MgServicePrincipal -Filter "displayName eq '$app_name'"
#Get the user, the service principal and appRole.
$params = @{
"PrincipalId" =$userId
"ResourceId" =$sp.Id
"AppRoleId" =($sp.AppRoles | Where-Object { $_.DisplayName -eq $app_role_name }).Id
}
#Assign the user to the AppRole
New-MgUserAppRoleAssignment -UserId $userId -BodyParameter $params |
Format-List Id, AppRoleId, CreationTime, PrincipalDisplayName,
PrincipalId, PrincipalType, ResourceDisplayName, ResourceId
This example assigns the user Britta Simon to the Microsoft Workplace Analytics application using Microsoft Graph PowerShell.
In PowerShell, assign the corresponding values to the variables $userId, $app_name, and $app_role_name.
# Assign the values to the variables
$userId = "<Britta Simon's user ID>"
$app_name = "Workplace Analytics"
In this example, we don't know the exact name of the application role we want to assign to Britta Simon. Run the following command to get the service principal ($sp) using the service principal display name.
# Get the service principal for the app
$sp = Get-MgServicePrincipal -Filter "displayName eq '$app_name'"
Run the following command to find the app roles exposed by the service principal.
# Get the app roles exposed by the service principal
$appRoles = $sp.AppRoles
# Display the app roles
$appRoles | ForEach-Object {
Write-Output "AppRole: $($_.DisplayName) - ID: $($_.Id)"
}
Napomena
The default AppRole ID is 00000000-0000-0000-0000-000000000000. This role is assigned when no specific AppRole is defined for a service principal.
Assign the role name to the $app_role_name variable. In this example, we want to assign Britta Simon the Analyst (Limited access) Role.
# Assign the values to the variables
$app_role_name = "Analyst (Limited access)"
$appRoleId = ($sp.AppRoles | Where-Object { $_.DisplayName -eq $app_role_name }).Id
Prepare the parameters and run the following command to assign the user to the app role.
# Prepare parameters for the role assignment
$params = @{
"PrincipalId" = $userId
"ResourceId" = $sp.Id
"AppRoleId" = $appRoleId
}
# Assign the user to the app role
New-MgUserAppRoleAssignment -UserId $userId -BodyParameter $params |
Format-List Id, AppRoleId, CreationTime, PrincipalDisplayName,
PrincipalId, PrincipalType, ResourceDisplayName, ResourceId
To assign a group to an enterprise app, replace Get-MgUser with Get-MgGroup and replace New-MgUserAppRoleAssignment with New-MgGroupAppRoleAssignment.
For more information on how to assign a group to an application role, see the documentation for New-MgGroupAppRoleAssignment.
Open an elevated Windows PowerShell command prompt.
Run Connect-MgGraph -Scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All" and sign in as at least a Cloud Application Administrator.
Get the user and the service principal
$user = Get-MgUser -UserId <userid>
$sp = Get-MgServicePrincipal -ServicePrincipalId <ServicePrincipalId>
Get the ID of the role assignment
$assignments = Get-MgServicePrincipalAppRoleAssignedTo -ServicePrincipalId $sp.Id | Where {$_.PrincipalDisplayName -eq $user.DisplayName}
Run the following command to show the list of users assigned to the application
$assignments | Select *
Run the following command to remove the AppRole assignment.
Remove-MgServicePrincipalAppRoleAssignedTo -AppRoleAssignmentId '<AppRoleAssignment-id>' -ServicePrincipalId $sp.Id
Run the following command to remove all users and groups assigned to the application.
$assignments | ForEach-Object {
if ($_.PrincipalType -in ("user", "Group")) {
Remove-MgServicePrincipalAppRoleAssignedTo -ServicePrincipalId $sp.Id -AppRoleAssignmentId $_.Id }
}
To assign users and groups to an application, sign in to Graph Exploreras at least a Cloud Application Administrator.
You need to consent to the following permissions:
Application.ReadWrite.All, and AppRoleAssignment.ReadWrite.All.
To grant an app role assignment, you need three identifiers:
principalId: The ID of the user or group to which you're assigning the app role.resourceId: The ID of the resource servicePrincipal that defines the app role.appRoleId: The ID of the appRole (defined on the resource service principal) to assign to a user or group.Get the enterprise application. Filter by DisplayName.
GET https://graph.microsoft.com/v1.0/servicePrincipals?$filter=displayName eq '{appDisplayName}'
Record the following values from the response body:
Napomena
The default AppRole ID is 00000000-0000-0000-0000-000000000000. This role is assigned when no specific AppRole is defined for a service principal.
Get the user by filtering by the user's principal name. Record the object ID of the user.
GET https://graph.microsoft.com/v1.0/users/{userPrincipalName}
Assign the user to the application.
POST https://graph.microsoft.com/v1.0/servicePrincipals/{resource-servicePrincipal-id}/appRoleAssignedTo
{
"principalId": "aaaaaaaa-bbbb-cccc-1111-222222222222",
"resourceId": "a0a0a0a0-bbbb-cccc-dddd-e1e1e1e1e1e1",
"appRoleId": "00000000-0000-0000-0000-000000000000"
}
In the example, both the resource-servicePrincipal-id and resourceId represent the enterprise application.
To unassign all users and groups from the application, run the following query.
Get the enterprise application. Filter by displayName.
GET https://graph.microsoft.com/v1.0/servicePrincipals?$filter=displayName eq '{appDisplayName}'
Get the list of appRoleAssignments for the application.
GET https://graph.microsoft.com/v1.0/servicePrincipals/{id}/appRoleAssignedTo
Remove the appRoleAssignments by specifying the appRoleAssignment ID.
DELETE https://graph.microsoft.com/v1.0/servicePrincipals/{resource-servicePrincipal-id}/appRoleAssignedTo/{appRoleAssignment-id}
Microsoft Graph Explorer doesn't support batch deletion of app role assignments directly. You need to delete each assignment individually. However, you can automate this process using Microsoft Graph PowerShell to iterate through and remove each assignment
Događaj
9. tra 15 - 10. tra 12
Programirajte budućnost s umjetnom inteligencijom i povežite se s Java kolegama i stručnjacima na JDConfu 2025.
Registrirajte se odmahObuka
Modul
Manage Microsoft Entra application access - Training
This module focuses on effectively managing identities and enhancing security in Microsoft Enterprise Identity, ensuring that users, groups, and external identities are protected against security threats and unauthorized access.
Certifikacija
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Dokumentacija
Properties of an enterprise application - Microsoft Entra ID
Learn about the properties of an enterprise application in Microsoft Entra ID.
Configure enterprise application properties - Microsoft Entra ID
Learn how to configure the properties of an enterprise to how users access and interact with the application.
Manage access to apps - Microsoft Entra ID
Describes how Microsoft Entra ID enables organizations to specify the apps to which each user has access.