SSO, Identity Flow, Authorization In Cloud Applications and Services – Challenges and Solution Approaches
Regardless of the physical deployment the high level schema of canonical cloud application can be described as follows.
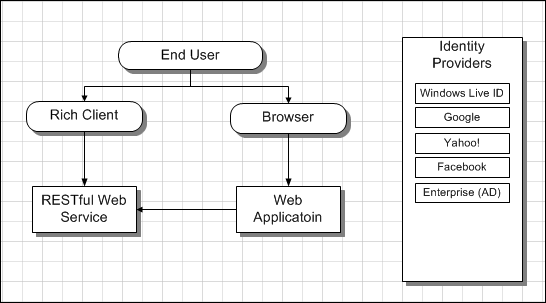
Key characteristics
- End user can have existing identities managed by industry strength identity providers such as Windows Live ID, Google, Yahoo!, Facebook, or enterprise Active Directory.
- End user interacts with the system that requires authentication and authorization via Web Browser, or…
- End user interacts with the system that requires authentication and authorization via Rich Client running either on desktop, smartphone, or inside browser (Silverlight, JavaScript, etc)
- Web Application might interact with downstream web services that require authentication and authorization.
Following are the security related challenges and solution approaches when designing your system that fits the key characteristics above.
Challenge |
Approach |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
What other questions left unasked and unanswered? Share in comments section below, please.
Related Books
- Programming Windows Identity Foundation (Dev - Pro)
- A Guide to Claims-Based Identity and Access Control (Patterns & Practices) – free online version
- Developing More-Secure Microsoft ASP.NET 2.0 Applications (Pro Developer)
- Ultra-Fast ASP.NET: Build Ultra-Fast and Ultra-Scalable web sites using ASP.NET and SQL Server
- Advanced .NET Debugging
- Debugging Microsoft .NET 2.0 Applications
Related Info
- Windows Identity Foundation (WIF) SDK Help Overhaul
- Windows Identity Foundation (WIF) Configuration Sections in ASP.NET Web.Config
- Windows Identity Foundation (WIF) and Azure AppFabric Access Control (ACS) Service Survival Guide
- Azure AppFabric Access Control Service (ACS) v 2.0 High Level Architecture – Web Application
- Azure AppFabric Access Control Service (ACS) v 2.0 High Level Architecture – REST Web Service Application Scenario
- Windows Identity Foundation (WIF) Explained – Web Browser Sign-In Flow (WS-Federation Passive Requestor Profile)
- Protocols Supported By Windows Identity Foundation (WIF)
- Windows Identity Foundation (WIF) By Example Part I – How To Get Started.
- Windows Identity Foundation (WIF) By Example Part II – How To Migrate Existing ASP.NET Web Application To Claims Aware
- Windows Identity Foundation (WIF) By Example Part III – How To Implement Claims Based Authorization For ASP.NET Application
- Identity Developer Training Kit
- A Guide to Claims-Based Identity and Access Control – Code Samples
- A Guide to Claims-Based Identity and Access Control — Book Download