View Defender for Office 365 reports in the Microsoft Defender portal
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
In organizations with Microsoft Defender for Office 365 Plan 1 or Plan 2 (for example, Microsoft 365 E5 or Microsoft Business Premium) a variety of security-related reports are available. If you have the necessary permissions, you can view and download these reports in the Microsoft Defender portal.
The reports are available in the Microsoft Defender portal at https://security.microsoft.com on the Email & collaboration reports page at Reports > Email & collaboration > Email & collaboration reports. Or, to go directly to the Email & collaboration reports page, use https://security.microsoft.com/emailandcollabreport.
Summary information for each report is available on the page. Identify the report you want to view, and then select View details for that report.
The rest of this article describes the reports that are exclusive to Defender for Office 365.
Note
Email security reports that don't require Defender for Office 365 are described in View email security reports in the Microsoft Defender portal.
For reports that have been deprecated or replaced, see the table in Email security report changes in the Microsoft Defender portal.
Reports that are related to mail flow are now in the Exchange admin center (EAC). For more information about these reports, see Mail flow reports in the new Exchange admin center.
Watch this short video to learn how you can use reports to understand the effectiveness of Defender for Office 365 in your organization.
Safe Attachments file types report
Note
This report has been deprecated. The same information is available in the Threat protection status report.
Safe Attachments message disposition report
Note
This report has been deprecated. The same information is available in the Threat protection status report.
Mail latency report
The Mail latency report shows you an aggregate view of the mail delivery and detonation latency experienced within your Defender for Office 365 organization. Mail delivery times in the service are affected by many factors, and the absolute delivery time in seconds is often not a good indicator of success or a problem. A slow delivery time on one day might be considered an average delivery time on another day, or vice-versa. This report tries to qualify message delivery based on statistical data about the observed delivery times of other messages.
Client-side latency and network latency aren't included in the results.
On the Email & collaboration reports page at https://security.microsoft.com/emailandcollabreport, find Mail latency report, and then select View details. Or, to go directly to the report, use https://security.microsoft.com/mailLatencyReport.
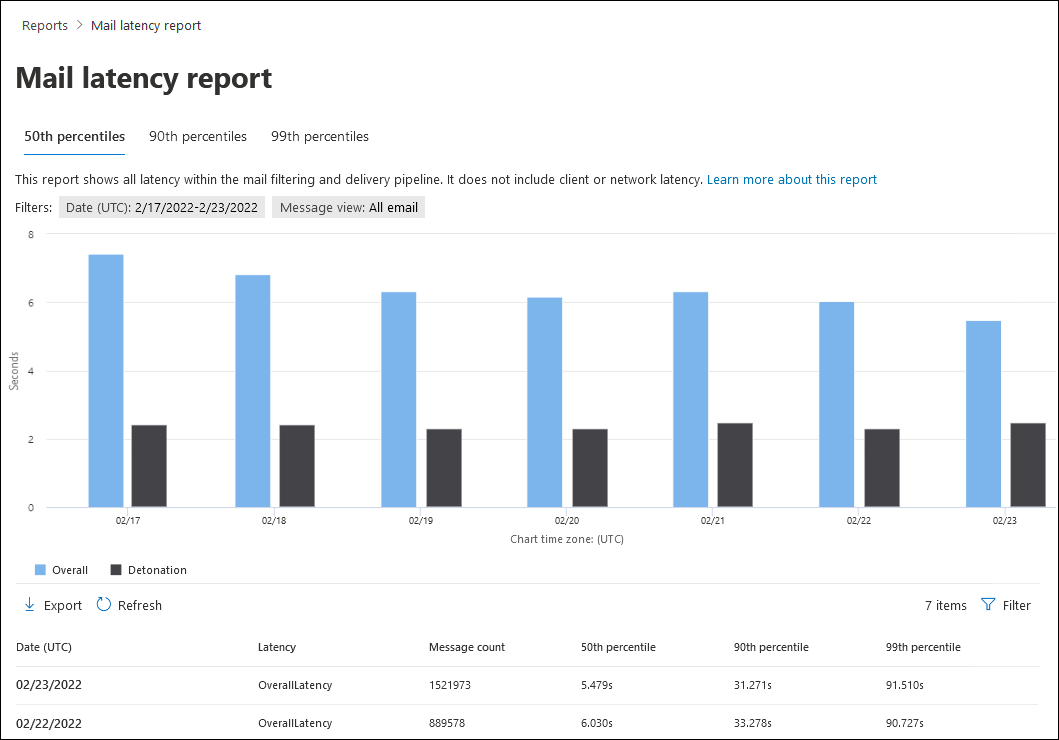
On the Mail latency report page, the following tabs are available:
- 50th percentile: The middle for message delivery times. You can consider this value as an average delivery time. This tab is selected by default.
- 90th percentile: Indicates a high latency for message delivery. Only 10% of messages took longer than this value to deliver.
- 99th percentile: Indicates the highest latency for message delivery.
Regardless of the tab you select, the chart shows messages organized into the following categories:
- Overall
- Detonation (these values are explained in the
 Filter values)
Filter values)
Hover over a category in the chart to see a breakdown of the latency in each category.
In the details table below the chart, the following information is available:
- Date (UTC)
- Latency
- Message count
- 50th percentile
- 90th percentile
- 99th percentile
Select ![]() Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
- Date (UTC): Start date and End date
- Message view: Select one of tne of the following values:
- All email
- Detonated email: After you select this value, select one of the following values that appears:
- Inline detonation: Links and attachments in messages are fully tested by Safe Links and Safe Attachments before delivery.
- Asynchronous detonation: Dynamic delivery of attachments by Safe Attachments and links in email tested by Safe Links after delivery.
When you're finished configuring the filters, select Apply, Cancel, or ![]() Clear filters.
Clear filters.
On the Mail latency report page, the ![]() Export action is available.
Export action is available.
Post-delivery activities report
The Post-delivery activities report shows information about email messages that removed from user mailboxes after delivery by zero-hour auto purge (ZAP). For more information about ZAP, see Zero-hour auto purge (ZAP) in Exchange Online.
The report shows real-time information with updated threat information.
On the Email & collaboration reports page at https://security.microsoft.com/emailandcollabreport, find Post-delivery activities, and then select View details. Or, to go directly to the report, use https://security.microsoft.com/reports/ZapReport.
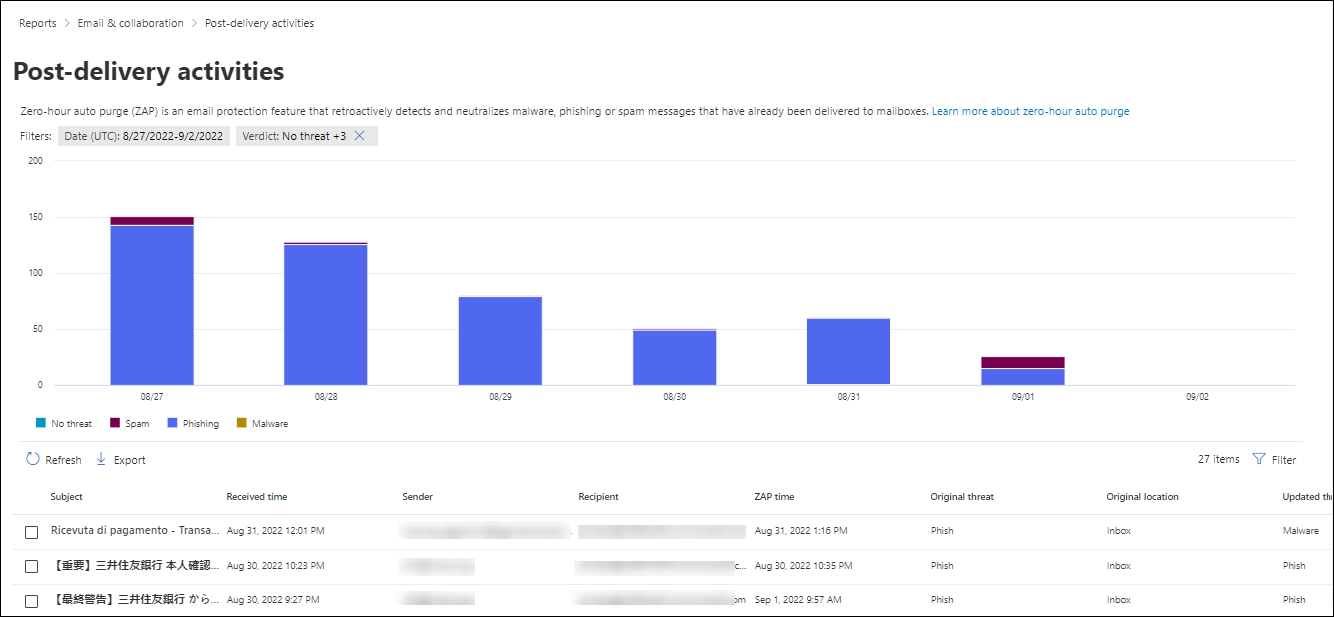
On the Post-delivery activities page, the chart shows the following information for the specified date range:
- No threat: The number of unique delivered messages that were found to be not spam by ZAP.
- Spam: The number of unique messages that were removed from mailboxes by ZAP for spam.
- Phishing: The number of unique messages that were removed from mailboxes by ZAP for phishing.
- Malware: The number of unique messages that were removed from mailboxes by ZAP for phishing.
The details table below the graph shows the following information:
Subject
Received time
Sender
Recipient
ZAP time
Original threat
Original location
Updated threat
Updated delivery location
Detection technology
To see all columns, you likely need to do one or more of the following steps:
- Horizontally scroll in your web browser.
- Narrow the width of appropriate columns.
- Zoom out in your web browser.
Select ![]() Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
- Date (UTC): Start date and End date.
- Updated threat: Select one ore mor of the following values:
- No threat
- Spam
- Phishing
- Malware
When you're finished configuring the filters, select Apply, Cancel, or ![]() Clear filters.
Clear filters.
On the Post delivery activities page, the ![]() Create schedule and
Create schedule and ![]() Export actions are available.
Export actions are available.
Threat protection status report
The Threat protection status report is a single view that brings together information about malicious content and malicious email detected and blocked by Exchange Online Protection (EOP) and Defender for Office 365. For more information, see Threat protection status report.
Top senders and recipients report
The Top senders and recipients report show the top recipients for EOP and Defender for Office 365 protection features. For more information, see Top senders and recipients report.
URL protection report
The URL protection report provides summary and trend views for threats detected and actions taken on URL clicks as part of Safe Links. This report doesn't have click data from users if Track user clicks in the effective Safe Links policy isn't selected.
On the Email & collaboration reports page at https://security.microsoft.com/emailandcollabreport, find URL protection report, and then select View details. Or, to go directly to the report, use https://security.microsoft.com/URLProtectionActionReport.
The available views in the URL threat protection report are described in the following subsections.
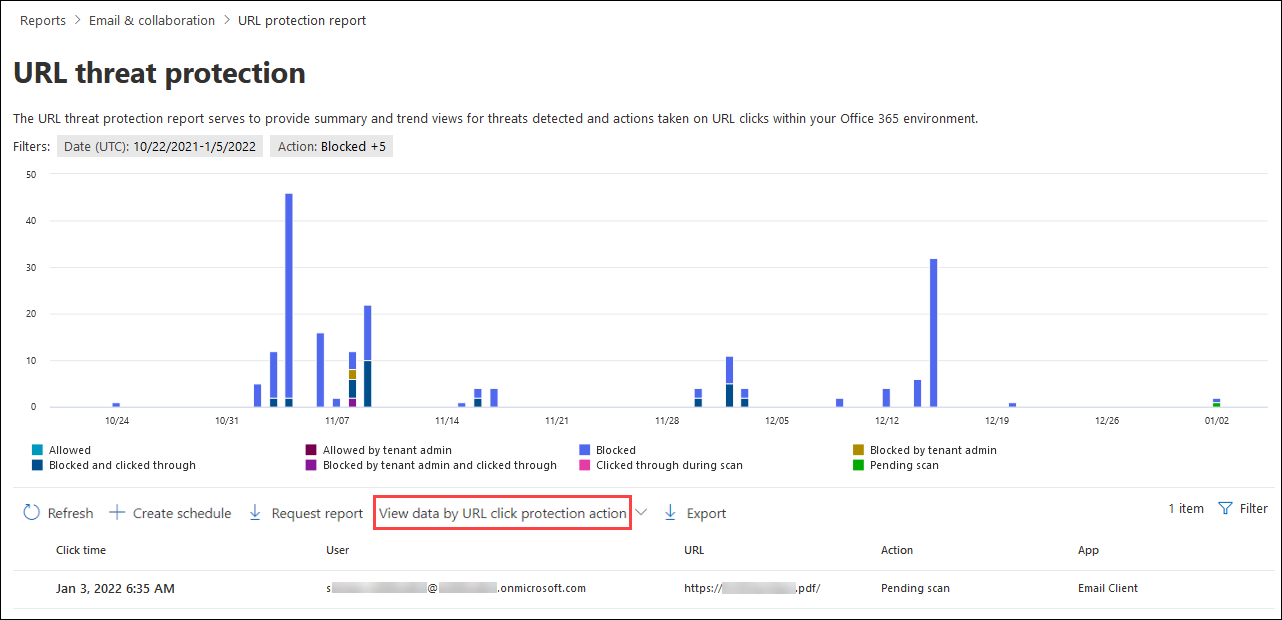
View data by URL click protection action in the URL protection report
The View data by URL click protection action view shows the number of URL clicks by users in the organization and the results of the click:
- Allowed: Clicks allowed.
- Allowed by tenant admin: Clicks allowed in Safe Links policies.
- Blocked: Click blocked.
- Blocked by tenant admin: The Clicks blocked in Safe Links policies.
- Blocked and clicked through: Blocked clicks where users click through to the blocked URL.
- Blocked by tenant admin and clicked through: Admin has blocked the link, but the user clicked through.
- Clicked through during scan: Clicks where users click through the pending scan page to the URL.
- Pending scan: Clicks on URLs that are pending a scan verdict.
A click indicates that the user has clicked through the block page to the malicious website (admins can disable click through in Safe Links policies).
The details table below the chart provides the following near-real-time view of all clicks that happened within the organization for the last 30 days:
- Click time
- User
- URL
- Action
- App
- Tags: For more information about user tags, see User tags.
Select ![]() Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
- Date (UTC): Start date and End date.
- Action: The same URL click protection actions as previously described. By default, Allowed and Allowed by tenant admin aren't selected.
- Evaluation: Select Yes or No. For more information, see Try Microsoft Defender for Office 365.
- Domains (separated by commas): The URL domains listed in the report results.
- Recipients (separated by commas)
- Tag: Leave the value All or remove it, double-click in the empty box, and then select Priority account. For more information about user tags, see User tags.
When you're finished configuring the filters, select Apply, Cancel, or ![]() Clear filters.
Clear filters.
On the URL threat protection page, the ![]() Create schedule,
Create schedule, ![]() Request report, and
Request report, and ![]() Export actions are available.
Export actions are available.
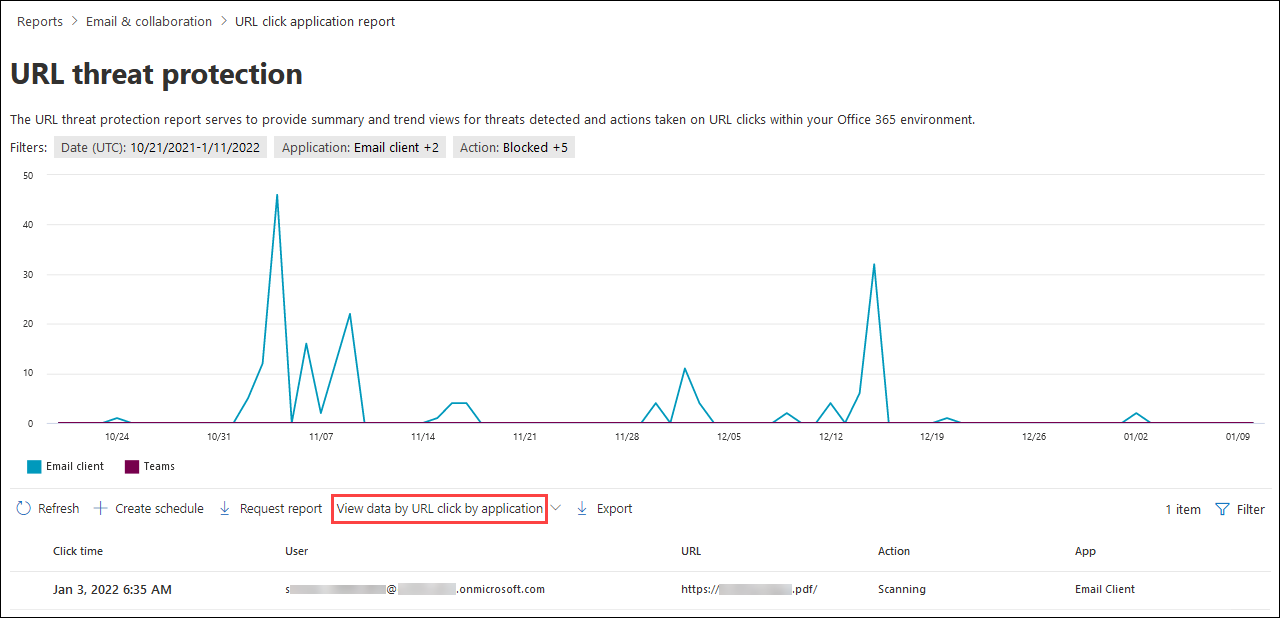
View data by URL click by application in the URL protection report
Tip
URL clicks by guest users are available in the report. Guest user accounts might be compromised or access malicious content inside the organization.
The View data by URL click by application view shows the number of URL clicks by apps that support Safe Links:
- Email client
- Teams
- Office document
The details table below the chart provides the following near-real-time view of all clicks that happened within the organization for the last seven days:
- Click time
- User
- URL
- Action: The same URL click protection actions as previously described for the View data by URL click protection action view.
- App
- Tags: For more information about user tags, see User tags.
Select ![]() Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
Filter to modify the report and the details table by selecting one or more of the following values in the flyout that opens:
- Date (UTC): Start date and End date.
- Application: The same click by application values as previously described.
- Action: The same values as shown in the View data by URL click protection action view. By default, Allowed and Allowed by tenant admin aren't selected.
- Evaluation: Select Yes or No. For more information, see Try Microsoft Defender for Office 365.
- Domains (separated by commas): The URL domains listed in the report results.
- Recipients (separated by commas)
- Tag: Leave the value All or remove it, double-click in the empty box, and then select Priority account. For more information about user tags, see User tags.
When you're finished configuring the filters, select Apply, Cancel, or ![]() Clear filters.
Clear filters.
On the URL threat protection page, the ![]() Create schedule,
Create schedule, ![]() Request report, and
Request report, and ![]() Export actions are available.
Export actions are available.
Additional reports to view
In addition to the reports described in this article, the following tables describe other available reports that are available:
| Report | Article |
|---|---|
| Explorer (Microsoft Defender for Office 365 Plan 2) or real-time detections (Microsoft Defender for Office 365 Plan 1) | Threat Explorer (and real-time detections) |
| Email security reports that don't require Defender for Office 365 | View email security reports in the Microsoft Defender portal |
| Mail flow reports in the Exchange admin center (EAC) | Mail flow reports in the new Exchange admin center |
PowerShell reporting cmdlets:
| Report | Article |
|---|---|
| Top senders and recipients | Get-MailTrafficSummaryReport |
| Top malware | Get-MailTrafficSummaryReport |
| Threat protection status | Get-MailTrafficATPReport |
| Safe Links | Get-SafeLinksAggregateReport |
| Compromised users | Get-CompromisedUserAggregateReport |
| Mail flow status | Get-MailflowStatusReport |
| Spoofed users | Get-SpoofMailReport |
| Post delivery activity summary | Get-AggregateZapReport |
| Post delivery activity details | Get-DetailZapReport |
What permissions are needed to view the Defender for Office 365 reports?
See What permissions are needed to view these reports?
What if the reports aren't showing data?
If you don't see data in the reports, check the report filters and double-check that your policies are set up correctly. Safe Links policies and Safe Attachments policies from Built-in protection, preset security policies, or custom policies need to be in effect and acting on messages. For more information, see the following articles: