Analyze your first incident in Microsoft Defender XDR
Applies to:
- Microsoft Defender XDR
Understanding the context that surrounds incidents is essential in analyzing attacks. Combining your expertise and experience with Microsoft Defender XDR's features and capabilities ensure faster resolution of incidents and your organization's safety from cyber attacks.
Today's threats on data security - business email compromise (BEC), malware like backdoors and ransomware, organizational breaches, and nation-state attacks – require quick, intelligent, and decisive action from incident responders. Tools like Microsoft Defender XDR allow response teams to detect, triage, and investigate incidents through its single-pane-of-glass experience and find the information needed to make these timely decisions.
Investigation tasks
Investigations usually involve responders viewing several apps while simultaneously checking various threat intelligence sources. Sometimes investigations are extended to hunting down other threats. Documenting facts and solutions in an attack investigation is an additional important task that provides history and context for other investigators' use or for later investigations. These investigation tasks are simplified when using Microsoft Defender XDR through the following:
Pivoting – the portal aggregates important attack information contextualized across the Defender workloads enabled in your organization. The portal consolidates all information across a single attack's components (file, URL, mailbox, a user account, or device), showing relationships and timeline of activities. With all the information available in a page, the portal allows incident responders to pivot across related entities and events to find the information they need to make decisions.
Hunting – threat hunters can find known and possible threats within an organization through the portal's advanced hunting capability using Kusto queries. If you're new to Kusto, use the guided mode to hunt for threats.
Insight – where applicable, incident responders can view actions to previously detected event and alerts to aid present investigations. Additional insights are also automatically added to events and alerts through Microsoft's own threat intelligence efforts and from sources like the MITRE ATT&CK® framework and VirusTotal.
Collaboration – security operations teams can view each team members' decisions and actions on past and present incidents and alerts through portal features like comments, tagging, flagging, and assignment. Further collaboration with Microsoft's managed detection and response service through Defender Experts for XDR and Defender Experts for Hunting are also available when an organization requires an augmented response.
Attack overview
The attack story provides incident responders a full, contextualized overview what happened in an attack. Responders can view all related alerts and events, including the automated remediation actions taken by Microsoft Defender XDR to mitigate an attack.
From the attack story, you can dive deeper into the details of an attack by exploring the tabs available on the incident page. You can quickly remediate common attacks like phishing, password spray, and malicious app compromise through incident response playbooks accessible within the portal. These playbooks contain detection, response, and mitigation guidance that support incident investigations.
This video of how to investigate an attack in Microsoft Defender XDR and how to use the portal's features in your investigation walks you through the attack story and the incident page.
Investigating threats
Complex threats like adversary-in-the-middle attacks and ransomware often require manual investigation. An incident responder tackling these complicated attacks looks for the following crucial information:
- Presence of malware or suspicious use of tools and apps
- Clues about any communication channels or entry points used by any malicious or suspicious entity
- Clues pointing to possible identity compromise
- Identifying what the impact is on the organization's data and security posture
The following sections contain tutorials and videos of Microsoft Defender XDR features that aid incident response teams in investigating various complex attacks.
Ransomware investigations
Ransomware continues to be a significant threat to organizations. Microsoft has the following resources to help you investigate and respond to ransomware attacks:
- Guides: From detection to protection: Microsoft's guide to combating ransomware attacks
- Tutorial: Ransomware investigation playbook
- Video: Investigating ransomware attacks in Microsoft Defender XDR (part 1)
- Video: Investigating ransomware attacks in Microsoft Defender XDR (part 2)
Email-based attacks analysis
Identifying and tracking modified, created, or stolen identities are essential to investigating phishing and BEC attacks. Use the following resources when investigating these attacks:
- Tutorial: Investigate malicious email
- Tutorial: Investigate users
- Tutorial: Investigate a user account
- Blog: Total Identity Compromise: Microsoft Incident Response lessons on securing Active Directory Identity compromise can also be investigated using Defender for Identity signals.
- Tutorial: Example of a phishing email attack
- Tutorial: Example of an identity-based attack
The following videos discuss how to investigate phishing and BEC attacks in Microsoft Defender XDR:
- Video: Investigating BEC and AiTM phishing in Microsoft Defender XDR
- Video: Defending against spearphishing and phishing using Defender for Office 365
Investigate an identity compromise and know what you can do to contain an attack through this video:
Malware analysis
A malicious file's information and capabilities are key to investigating malware. Microsoft Defender XDR, in most cases, can detonate the file to show critical data including hash, metadata, prevalence within the organization, and file capabilities based on MITRE ATT&CK® techniques. This removes the need to do black box testing or static analysis of files. You can view file information from the incident graph, or by viewing an alert process tree, an artifact timeline, or a device timeline.
The following resources provide details on how to use the portal's capabilities in investigating files:
- Tutorial: Investigate files
- Video: Investigating malware in Microsoft Defender XDR
Risky apps analysis and cloud-based threats prevention
Malicious actors can exploit cloud-based apps. Apps can inadvertently leak sensitive information through abuse or misuse. Incident responders investigating and protecting apps in cloud environments can use the following resources where Defender for Cloud Apps is deployed in their organizations:
- Tutorial: Investigate malicious and compromised apps
- Tutorial: Investigate risky OAuth apps
- Tutorial: Protect cloud apps
- Tutorial: Protect apps in real time
Discover how you can protect your cloud apps in real time with this video of the Defender for Cloud Apps workload:
- Video: Protecting cloud apps and related files through Defender for Cloud Apps
Breach analysis
Nation-state attacks, attacks against critical infrastructure, and organizational breaches often require an attacker to establish communication points once they are in a network. Incident responders look for clues by identifying suspicious traffic or exchanges between a source and a destination. Microsoft has the following tutorials for investigating communication components:
- Investigate domains and URLs
- Investigate an IP address
- Investigate connection events that occur behind forward proxies
- Investigate suspicious user and device activities through Defender for Identity
- Identify and investigate lateral movement paths in Defender for Identity
- Investigate devices in the Defender for Endpoint devices list
Attackers often use vulnerabilities to gain access to an organization. Some ransomware attacks initially take advantage of unpatched vulnerabilities like the Log4Shell vulnerability. The following resources help incident responders identify vulnerabilities and vulnerable devices in their organization through the Defender for Vulnerability Management service:
- Tutorial: Identify vulnerabilities in your organization
- Tutorial: Hunt for exposed devices
- Tutorial: Assess your organization's risk through the Exposure score
- Video: Threat and vulnerability management via Defender Vulnerability Management
Breaches also happen through various devices like phones and tablets that connect to your organization's network. Incident responders can further investigate these devices within the portal. The following video talks about the top threats from mobile devices and how you can investigate these:
- Mobile threat defense in Microsoft Defender XDR
Resources for threat intelligence and hunting
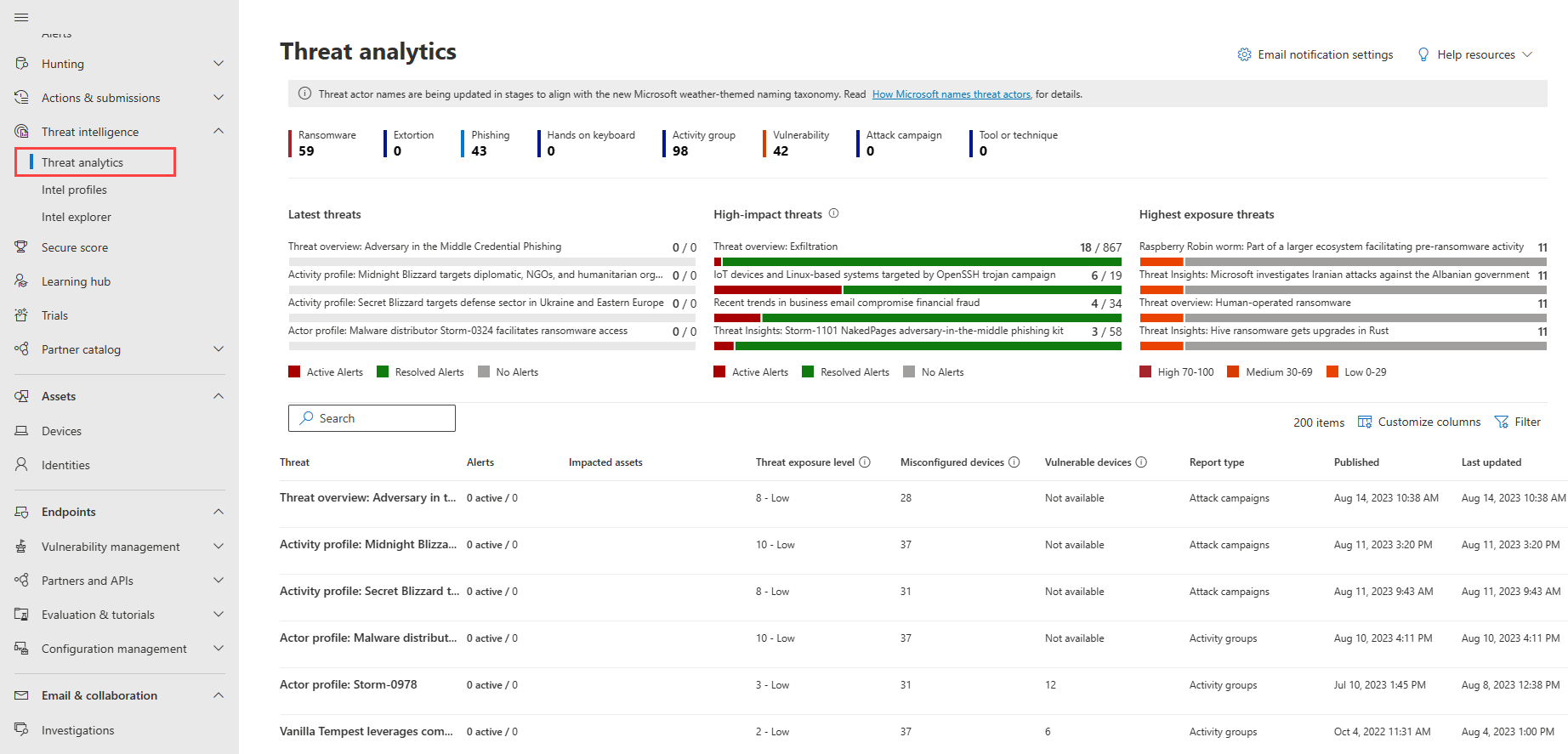
Microsoft Defender XDR's built-in threat intelligence capabilities and hunting aid incident response teams in performing proactive protection against emerging threats and attacks. You have direct access to the latest information on emerging threats and attacks through the portal's Threat analytics.
Use the intelligence in Threat analytics to deep dive into new threats with the following video:
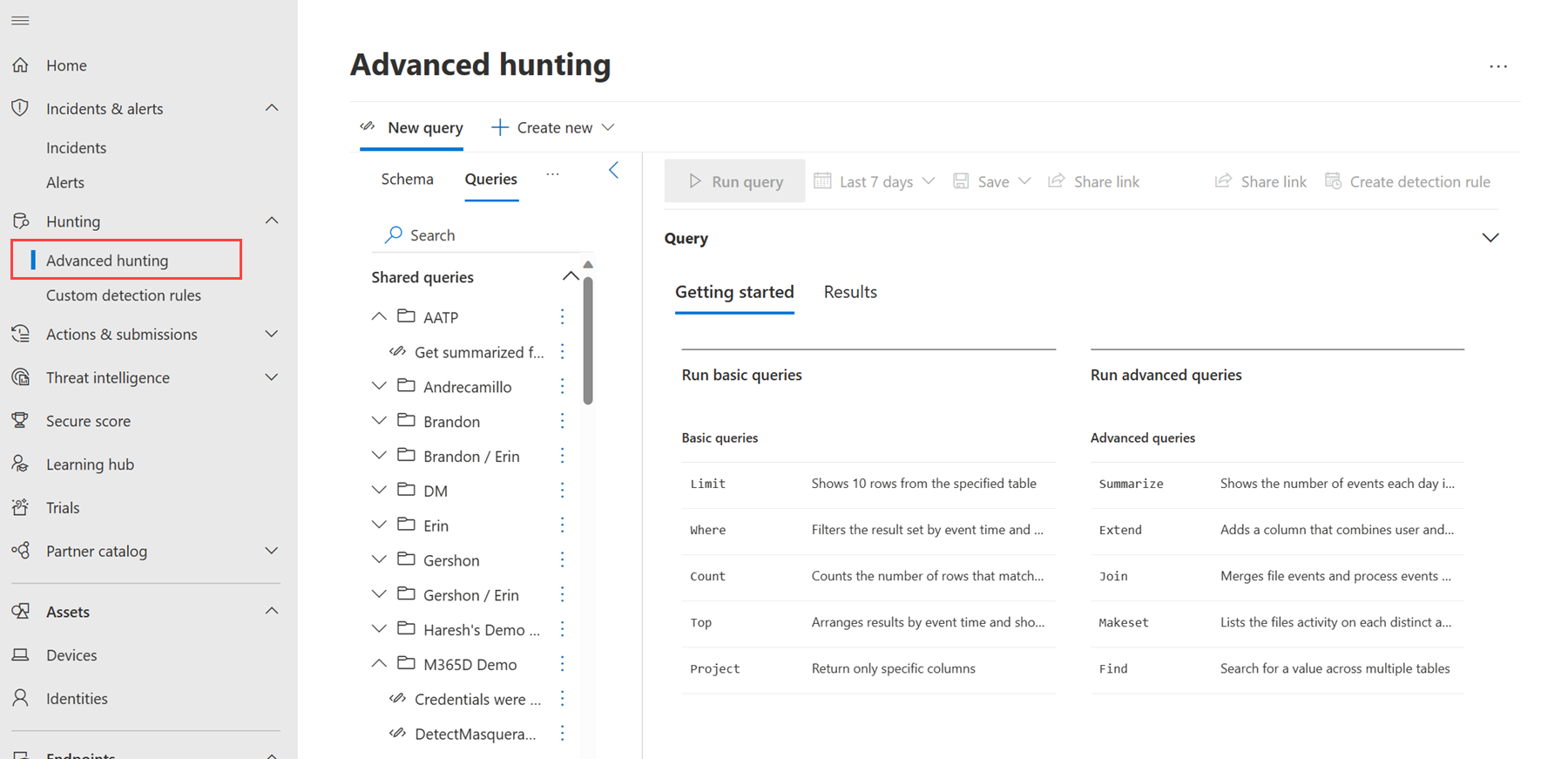
Proactively hunt for threats within the organization using the portal's built-in advanced hunting capability.
The following resources provide more information on how to use advanced hunting:
- Learn the Kusto query language
- Build hunting queries using the guided mode
- Hunt for threats across entities
Extend your threat intelligence with the latest security research and changes from Microsoft security research teams:
Collaborate with Microsoft's experts for incident response and threat hunting to enhance your security operations teams' capabilities. Know more about our experts and how to engage them in the following resources:
Next step
- Remediate your first incident
- Explore the portal's features through video demos in the Microsoft Defender XDR Virtual Ninja Training
See also
- Understand incidents
- Investigate incidents
- Investigate alerts
- Learn the portal's features and functions through the Microsoft Defender XDR Ninja training
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.