Notikumi
9. apr. 15 - 10. apr. 12
Kodējiet nākotni ar AI un sazinieties ar Java vienaudžiem un ekspertiem JDConf 2025.
Reģistrējieties tūlītŠī pārlūkprogramma vairs netiek atbalstīta.
Jauniniet uz Microsoft Edge, lai izmantotu jaunāko līdzekļu, drošības atjauninājumu un tehniskā atbalsta sniegtās priekšrocības.
The objective of this article is to demonstrate the steps to be performed in Smartsheet and Microsoft Entra ID to configure Microsoft Entra ID to automatically provision and de-provision users and/or groups to Smartsheet. For important details on what this service does, how it works, and frequently asked questions, see Automate user provisioning and deprovisioning to SaaS applications with Microsoft Entra ID.
The scenario outlined in this article assumes that you already have the following prerequisites:
Before configuring Smartsheet for automatic user provisioning with Microsoft Entra ID, you will need to enable SCIM provisioning on Smartsheet.
Sign in as a System Admin in the Smartsheet portal and navigate to Account > Admin Center.

In the Admin Center page click on the Menu option to expose the Menu panel.

Navigate to Menu > Settings > Domains & User Auto-Provisioning.

To add a new domain click on Add Domain and follow instructions.Once the domain is added make sure it gets verified as well.
Generate the Secret Token required to configure automatic user provisioning with Microsoft Entra ID by navigating Smartsheet portal and then navigating to Account > Apps and Integrations.
Choose API Access. Click Generate new access token.

Define the name of the API Access Token. Click OK.

Copy the API Access Token and save it as this will be the only time you can view it. This is required in the Secret Token field in Microsoft Entra ID.

Add Smartsheet from the Microsoft Entra application gallery to start managing provisioning to Smartsheet. If you have previously setup Smartsheet for SSO you can use the same application. However it is recommended that you create a separate app when testing out the integration initially. Learn more about adding an application from the gallery here.
The Microsoft Entra provisioning service allows you to scope who will be provisioned based on assignment to the application and or based on attributes of the user / group. If you choose to scope who will be provisioned to your app based on assignment, you can use the following steps to assign users and groups to the application. If you choose to scope who will be provisioned based solely on attributes of the user or group, you can use a scoping filter as described here.
Start small. Test with a small set of users and groups before rolling out to everyone. When scope for provisioning is set to assigned users and groups, you can control this by assigning one or two users or groups to the app. When scope is set to all users and groups, you can specify an attribute based scoping filter.
To ensure parity in user role assignments between Smartsheet and Microsoft Entra ID, it is recommended to utilize the same role assignments populated in the full Smartsheet user list. To retrieve this user list from Smartsheet, navigate to Account Admin > User Management > More Actions > Download User List (csv).
To access certain features in the app, Smartsheet requires a user to have multiple roles. To learn more about user types and permissions in Smartsheet, go to User Types and Permissions.
If a user has multiple roles assigned in Smartsheet, you MUST ensure that these role assignments are replicated in Microsoft Entra ID to avoid a scenario where users could lose access to Smartsheet objects permanently. Each unique role in Smartsheet MUST be assigned to a different group in Microsoft Entra ID. The user MUST then be added to each of the groups corresponding to roles desired.
If you need additional roles, you can update the application manifest to add new roles.
This section guides you through the steps to configure the Microsoft Entra provisioning service to create, update, and disable users and/or groups in Smartsheet based on user and/or group assignments in Microsoft Entra ID.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications
In the applications list, select Smartsheet.
Select the Provisioning tab.
Set the Provisioning Mode to Automatic.

Under the Admin Credentials section, input the SCIM 2.0 base URL of https://scim.smartsheet.com/v2 and Access Token value retrieved earlier from Smartsheet in Secret Token respectively. Click Test Connection to ensure Microsoft Entra ID can connect to Smartsheet. If the connection fails, ensure your Smartsheet account has SysAdmin permissions and try again.

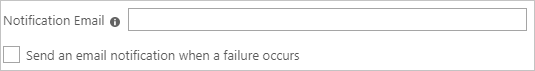
In the Notification Email field, enter the email address of a person or group who should receive the provisioning error notifications and check the checkbox - Send an email notification when a failure occurs.
Click Save.
Under the Mappings section, select Synchronize Microsoft Entra users to Smartsheet.
Review the user attributes that are synchronized from Microsoft Entra ID to Smartsheet in the Attribute Mapping section. The attributes selected as Matching properties are used to match the user accounts in Smartsheet for update operations. Select the Save button to commit any changes.
| Attribute | Type | Supported for filtering |
|---|---|---|
| userName | String | ✓ |
| active | Boolean | |
| title | String | |
| name.givenName | String | |
| name.familyName | String | |
| phoneNumbers[type eq "work"].value | String | |
| phoneNumbers[type eq "mobile"].value | String | |
| phoneNumbers[type eq "fax"].value | String | |
| emails[type eq "work"].value | String | |
| externalId | String | |
| roles | String | |
| urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:department | String | |
| urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:division | String | |
| urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:costCenter | String | |
| urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:manager | String |
To configure scoping filters, refer to the following instructions provided in the Scoping filter article.
To enable the Microsoft Entra provisioning service for Smartsheet, change the Provisioning Status to On in the Settings section.

Define the users and/or groups that you would like to provision to Smartsheet by choosing the desired values in Scope in the Settings section.
When you are ready to provision, click Save.

This operation starts the initial synchronization of all users and/or groups defined in Scope in the Settings section. The initial sync takes longer to perform than subsequent syncs, which occur approximately every 40 minutes as long as the Microsoft Entra provisioning service is running.
Once you've configured provisioning, use the following resources to monitor your deployment:
https://scim.smartsheet.com/v2 for SmartSheet integration under Admin Credentials section.Notikumi
9. apr. 15 - 10. apr. 12
Kodējiet nākotni ar AI un sazinieties ar Java vienaudžiem un ekspertiem JDConf 2025.
Reģistrējieties tūlītApmācība
Modulis
Implement and monitor the integration of enterprise apps for SSO - Training
Deploying and monitoring enterprise applications to Azure solutions can ensure security. Explore how to deploy on-premises and cloud based apps to users.
Sertifikācija
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Dokumentācija
Learn about attribute mappings for Software as a Service (SaaS) apps in Microsoft Entra Application Provisioning. Learn what attributes are and how you can modify them to address your business needs.
What is automated app user provisioning in Microsoft Entra ID - Microsoft Entra ID
An introduction to how you can use Microsoft Entra ID to automatically provision, deprovision, and continuously update user accounts across multiple third-party applications.
Plan an automatic user provisioning deployment for Microsoft Entra ID - Microsoft Entra ID
Guidance for planning and executing automatic user provisioning in Microsoft Entra ID