Integrate Key Vault with Azure Private Link
Azure Private Link Service enables you to access Azure Services (for example, Azure Key Vault, Azure Storage, and Azure Cosmos DB) and Azure hosted customer/partner services over a Private Endpoint in your virtual network.
An Azure Private Endpoint is a network interface that connects you privately and securely to a service powered by Azure Private Link. The private endpoint uses a private IP address from your VNet, effectively bringing the service into your VNet. All traffic to the service can be routed through the private endpoint, so no gateways, NAT devices, ExpressRoute or VPN connections, or public IP addresses are needed. Traffic between your virtual network and the service traverses over the Microsoft backbone network, eliminating exposure from the public Internet. You can connect to an instance of an Azure resource, giving you the highest level of granularity in access control.
For more information, see What is Azure Private Link?
Prerequisites
To integrate a key vault with Azure Private Link, you'll need:
- A key vault.
- An Azure virtual network.
- A subnet in the virtual network.
- Owner or contributor permissions for both the key vault and the virtual network.
Your private endpoint and virtual network must be in the same region. When you select a region for the private endpoint using the portal, it will automatically filter only virtual networks that are in that region. Your key vault can be in a different region.
Your private endpoint uses a private IP address in your virtual network.
Establish a private link connection to Key Vault using the Azure portal
First, create a virtual network by following the steps in Create a virtual network using the Azure portal
You can then either create a new key vault, or establish a private link connection to an existing key vault.
Create a new key vault and establish a private link connection
You can create a new key vault with the Azure portal, Azure CLI, or Azure PowerShell.
After configuring the key vault basics, select the Networking tab and follow these steps:
Disable public access by toggling off the radio button.
Select the "+ Create a private endpoint" Button to add a private endpoint.
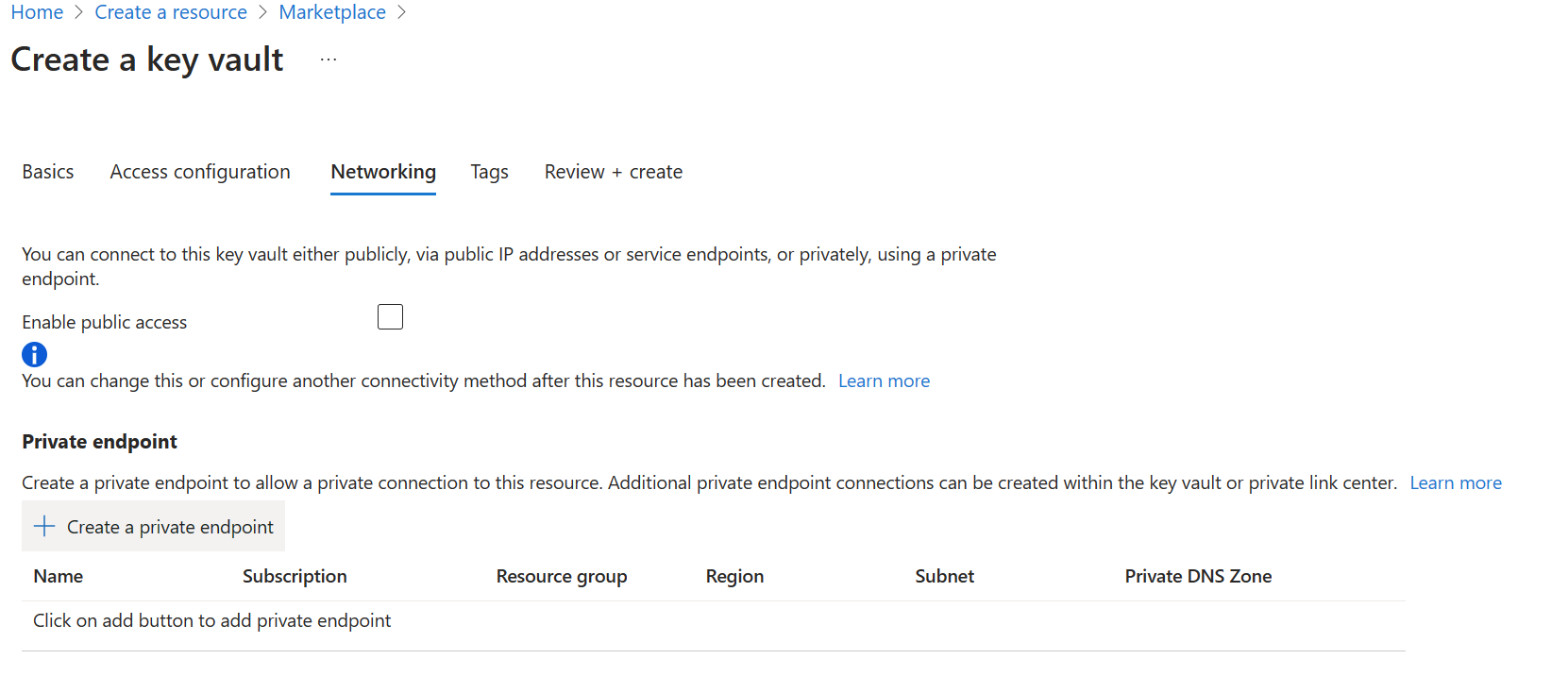
In the "Location" field of the Create Private Endpoint Blade, select the region in which your virtual network is located.
In the "Name" field, create a descriptive name that will allow you to identify this private endpoint.
Select the virtual network and subnet you want this private endpoint to be created in from the dropdown menu.
Leave the "integrate with the private zone DNS" option unchanged.
Select "Ok".
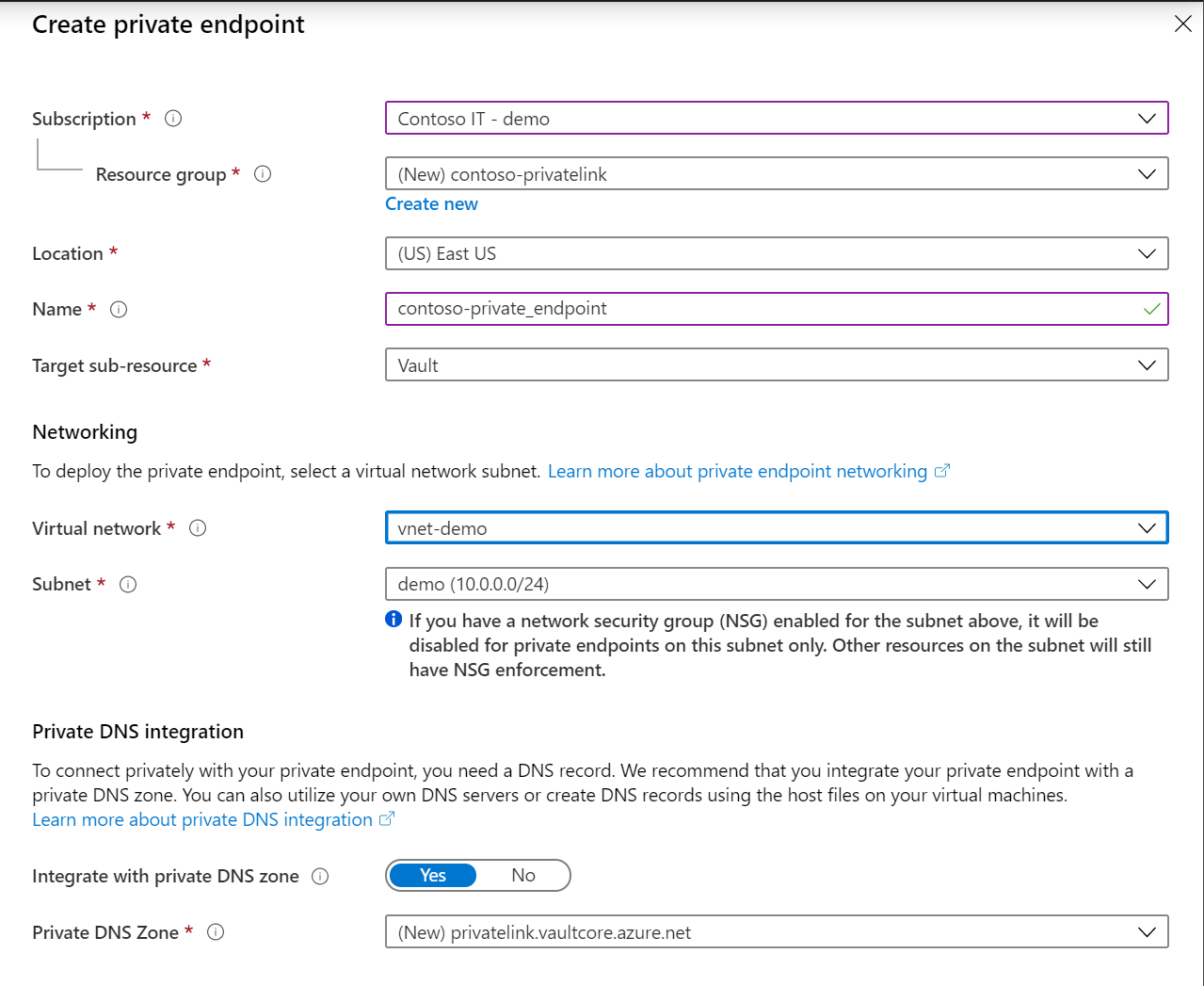
You'll now be able to see the configured private endpoint. You can now delete and edit this private endpoint. Select the "Review + Create" button and create the key vault. It will take 5-10 minutes for the deployment to complete.
Establish a private link connection to an existing key vault
If you already have a key vault, you can create a private link connection by following these steps:
Sign in to the Azure portal.
In the search bar, type in "key vaults".
Select the key vault from the list to which you want to add a private endpoint.
Select the "Networking" tab under Settings.
Select the "Private endpoint connections" tab at the top of the page.
Select the "+ Create" button at the top of the page.
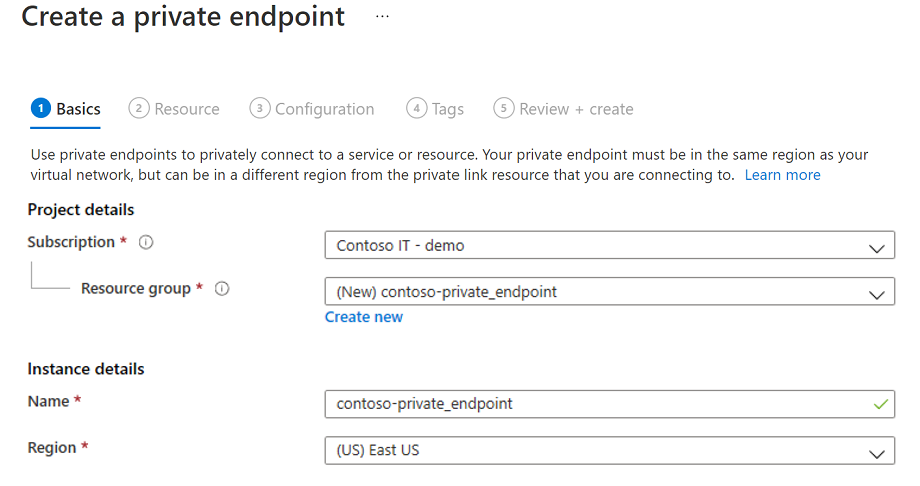
Under "Project Details", select the Resource Group that contains the virtual network that you created as a prerequisite for this tutorial. Under "Instance details", enter "myPrivateEndpoint" as the Name, and select the same location as the virtual network that you created as a prerequisite for this tutorial.
You can choose to create a private endpoint for any Azure resource in using this blade. You can either use the dropdown menus to select a resource type and select a resource in your directory, or you can connect to any Azure resource using a resource ID. Leave the "integrate with the private zone DNS" option unchanged.
Advance to the "Resources" blade. For "Resource type", select "Microsoft.KeyVault/vaults"; for "Resource", select the key vault you created as a prerequisite for this tutorial. "Target sub-resource" will auto-populate with "vault".
Advance to the "Virtual Network". Select the virtual network and subnet that you created as a prerequisite for this tutorial.
Advance through the "DNS" and "Tags" blades, accepting the defaults.
On the "Review + Create" blade, select "Create".
When you create a private endpoint, the connection must be approved. If the resource for which you're creating a private endpoint is in your directory, you'll be able to approve the connection request provided you have sufficient permissions; if you're connecting to an Azure resource in another directory, you must wait for the owner of that resource to approve your connection request.
There are four provisioning states:
| Service action | Service consumer private endpoint state | Description |
|---|---|---|
| None | Pending | Connection is created manually and is pending approval from the Private Link resource owner. |
| Approve | Approved | Connection was automatically or manually approved and is ready to be used. |
| Reject | Rejected | Connection was rejected by the private link resource owner. |
| Remove | Disconnected | Connection was removed by the private link resource owner, the private endpoint becomes informative and should be deleted for cleanup. |
How to manage a private endpoint connection to Key Vault using the Azure portal
Log in to the Azure portal.
In the search bar, type in "key vaults"
Select the key vault that you want to manage.
Select the "Networking" tab.
If there are any connections that are pending, you'll see a connection listed with "Pending" in the provisioning state.
Select the private endpoint you wish to approve
Select the approve button.
If there are any private endpoint connections you want to reject, whether it's a pending request or existing connection, select the connection and select the "Reject" button.
Validate that the private link connection works
You should validate that the resources within the same subnet of the private endpoint resource are connecting to your key vault over a private IP address, and that they have the correct private DNS zone integration.
First, create a virtual machine by following the steps in Create a Windows virtual machine in the Azure portal
In the "Networking" tab:
- Specify Virtual network and Subnet. You can create a new virtual network or select an existing one. If selecting an existing one, make sure the region matches.
- Specify a Public IP resource.
- In the "NIC network security group", select "None".
- In the "Load balancing", select "No".
Open the command line and run the following command:
nslookup <your-key-vault-name>.vault.azure.net
If you run the ns lookup command to resolve the IP address of a key vault over a public endpoint, you'll see a result that looks like this:
c:\ >nslookup <your-key-vault-name>.vault.azure.net
Non-authoritative answer:
Name:
Address: (public IP address)
Aliases: <your-key-vault-name>.vault.azure.net
If you run the ns lookup command to resolve the IP address of a key vault over a private endpoint, you'll see a result that looks like this:
c:\ >nslookup your_vault_name.vault.azure.net
Non-authoritative answer:
Name:
Address: 10.1.0.5 (private IP address)
Aliases: <your-key-vault-name>.vault.azure.net
<your-key-vault-name>.privatelink.vaultcore.azure.net
Troubleshooting Guide
Check to make sure the private endpoint is in the approved state.
- You can check and fix this in Azure portal. Open the Key Vault resource, and select the Networking option.
- Then select the Private endpoint connections tab.
- Make sure connection state is Approved and provisioning state is Succeeded.
- You may also navigate to the private endpoint resource and review same properties there, and double-check that the virtual network matches the one you're using.
Check to make sure you have a Private DNS Zone resource.
- You must have a Private DNS Zone resource with the exact name: privatelink.vaultcore.azure.net.
- To learn how to set this up please see the following link. Private DNS Zones
Check to make sure the Private DNS Zone is linked to the Virtual Network. This may be the issue if you're still getting the public IP address returned.
- If the Private Zone DNS isn't linked to the virtual network, the DNS query originating from the virtual network will return the public IP address of the key vault.
- Navigate to the Private DNS Zone resource in the Azure portal and select the virtual network links option.
- The virtual network that will perform calls to the key vault must be listed.
- If it's not there, add it.
- For detailed steps, see the following document Link Virtual Network to Private DNS Zone
Check to make sure the Private DNS Zone isn't missing an A record for the key vault.
- Navigate to the Private DNS Zone page.
- Select Overview and check if there's an A record with the simple name of your key vault (i.e. fabrikam). Don't specify any suffix.
- Make sure you check the spelling, and either create or fix the A record. You can use a TTL of 600 (10 mins).
- Make sure you specify the correct private IP address.
Check to make sure the A record has the correct IP Address.
- You can confirm the IP address by opening the Private Endpoint resource in Azure portal.
- Navigate to the Microsoft.Network/privateEndpoints resource, in the Azure portal (not the Key Vault resource)
- In the overview page look for Network interface and select that link.
- The link will show the Overview of the NIC resource, which contains the property Private IP address.
- Verify that this is the correct IP address that is specified in the A record.
If you're connecting from an on-premises resource to a Key Vault, ensure you have all required conditional forwarders in the on-premises environment enabled.
- Review Azure Private Endpoint DNS configuration for the zones needed, and make sure you have conditional forwarders for both
vault.azure.netandvaultcore.azure.neton your on-premises DNS. - Ensure that you have conditional forwarders for those zones that route to an Azure Private DNS Resolver or some other DNS platform with access to Azure resolution.
- Review Azure Private Endpoint DNS configuration for the zones needed, and make sure you have conditional forwarders for both
Limitations and Design Considerations
Limits: See Azure Private Link limits
Pricing: See Azure Private Link pricing.
Limitations: See Azure Private Link service: Limitations
Next Steps
- Learn more about Azure Private Link
- Learn more about Azure Key Vault