Notitie
Voor toegang tot deze pagina is autorisatie vereist. U kunt proberen u aan te melden of de directory te wijzigen.
Voor toegang tot deze pagina is autorisatie vereist. U kunt proberen de mappen te wijzigen.
Wat is alternatieve aanmeldings-id?
In de meeste scenario's gebruiken gebruikers hun UPN (User Principal Names) om zich aan te melden bij hun account. In sommige omgevingen vanwege bedrijfsbeleid of on-premises line-of-business-toepassingsafhankelijkheden gebruiken de gebruikers mogelijk een andere vorm van aanmelding.
Notitie
De aanbevolen procedures van Microsoft zijn om UPN aan te sluiten op het primaire SMTP-adres. In dit artikel wordt het kleine percentage klanten behandeld dat UPN's niet kan herstellen om overeen te komen.
Ze kunnen bijvoorbeeld hun e-mail-id gebruiken voor aanmelding en het kan afwijken van hun UPN. Dit is met name gebruikelijk in scenario's waarin hun UPN niet routeerbaar is. Overweeg een gebruiker Jane Doe met UPN jdoe@contoso.local en e-mailadres jdoe@contoso.com. Jane is misschien niet eens op de hoogte van de UPN, omdat ze haar e-mail-id altijd heeft gebruikt om zich aan te melden. Het gebruik van een andere aanmeldingsmethode in plaats van UPN vormt een alternatieve id. Zie de gebruikerspopulatie van Microsoft Entra UserPrincipalName voor meer informatie over hoe de UPN wordt gemaakt.
Met Active Directory Federation Services (AD FS) kunnen federatieve toepassingen met AD FS zich aanmelden met een alternatieve id. Hiermee kunnen beheerders een alternatief opgeven voor de standaard-UPN die moet worden gebruikt voor aanmelding. AD FS ondersteunt al het gebruik van elke vorm van gebruikers-id die wordt geaccepteerd door Active Directory Domain Services (AD DS). Wanneer ad FS is geconfigureerd voor een alternatieve id, kunnen gebruikers zich aanmelden met behulp van de geconfigureerde alternatieve id-waarde, zoals e-mail-id. Met de alternatieve id kunt u SaaS-providers zoals Office 365 gebruiken zonder uw on-premises UPN's te wijzigen. Hiermee kunt u ook line-of-business-servicetoepassingen ondersteunen met door de consument ingerichte identiteiten.
Alternatieve id in Microsoft Entra-id
Een organisatie moet in de volgende scenario's mogelijk een alternatieve id gebruiken:
- De on-premises domeinnaam is niet routeerbaar, zoals
contoso.local, en als gevolg hiervan is de standaard user principal name niet routeerbaar (jdoe@contoso.local). Bestaande UPN kan niet worden gewijzigd vanwege afhankelijkheden van lokale toepassingen of bedrijfsbeleid. Voor Microsoft Entra-id en Office 365 moeten alle domeinachtervoegsels die zijn gekoppeld aan de Microsoft Entra-adreslijst, volledig internetrouteerbaar zijn. - De on-premises UPN is niet hetzelfde als het e-mailadres van de gebruiker. Om zich aan te melden bij Office 365, gebruiken gebruikers hun e-mailadres, en de UPN kan niet worden gebruikt vanwege organisatorische beperkingen. In de bovenstaande scenario's kunnen gebruikers zich met een alternatieve ID via AD FS bij Microsoft Entra ID aanmelden zonder uw on-premises UPN's te wijzigen.
Alternatieve aanmeldings-id configureren
Gebruik Microsoft Entra Connect We raden u aan om microsoft Entra Connect te gebruiken om alternatieve aanmeldings-id voor uw omgeving te configureren.
- Voor een nieuwe configuratie van Microsoft Entra Connect, zie Verbinding maken met Microsoft Entra ID voor gedetailleerde instructies over hoe u een alternatieve ID kunt configureren en een AD FS-farm kunt instellen.
- Zie Voor bestaande Microsoft Entra Connect-installaties de gebruikersaanmeldingsmethode wijzigen voor instructies over het wijzigen van de aanmeldingsmethode in AD FS
Wanneer Microsoft Entra Connect details over de AD FS-omgeving krijgt, wordt automatisch gecontroleerd op de aanwezigheid van de juiste KB op uw AD FS en wordt AD FS geconfigureerd voor alternatieve ID, inclusief alle benodigde juiste claimregels voor de Microsoft Entra Federation Trust. Er is geen extra stap vereist buiten de wizard om alternatieve id te configureren.
Notitie
Microsoft raadt het gebruik van Microsoft Entra Connect aan om alternatieve aanmeldings-id te configureren.
Alternatieve id handmatig configureren
Als u alternatieve aanmeldings-id wilt configureren, moet u de volgende taken uitvoeren:
Configureer de vertrouwensrelaties van uw AD FS-claimprovider om een alternatieve aanmeldings-id in te schakelen.
Als u Windows Server 2012 R2 hebt, moet u ervoor zorgen dat u KB2919355 geïnstalleerd op alle AD FS-servers. U kunt het downloaden via Windows Update Services of rechtstreeks downloaden.
Werk de AD FS-configuratie bij door de volgende PowerShell-cmdlet uit te voeren op een van de federatieservers in uw farm (als u een WID-farm hebt, moet u deze opdracht uitvoeren op de primaire AD FS-server in uw farm):
Set-AdfsClaimsProviderTrust -TargetIdentifier "AD AUTHORITY" -AlternateLoginID <attribute> -LookupForests <forest domain>
AlternateLoginID is de LDAP-naam van het kenmerk dat u wilt gebruiken voor aanmelding.
LookupForests is de lijst met forest-DNS waartoe uw gebruikers behoren.
Als u de functie voor alternatieve aanmeldings-id's wilt inschakelen, moet u zowel de -AlternateLoginID- als de -LookupForests-parameters configureren met een geldige, niet-nietige waarde.
In het volgende voorbeeld schakelt u alternatieve functionaliteit voor aanmeldings-id's in, zodat uw gebruikers met accounts in contoso.com en fabrikam.com forests zich kunnen aanmelden bij ad FS-toepassingen met hun kenmerk 'mail'.
Set-AdfsClaimsProviderTrust -TargetIdentifier "AD AUTHORITY" -AlternateLoginID mail -LookupForests contoso.com,fabrikam.com
- Als u deze functie wilt uitschakelen, stelt u de waarde voor beide parameters in op null.
Set-AdfsClaimsProviderTrust -TargetIdentifier "AD AUTHORITY" -AlternateLoginID $NULL -LookupForests $NULL
Hybride moderne verificatie met alternatieve id
Belangrijk
Het volgende is alleen getest op AD FS en niet op id-providers van derden.
Exchange en Skype voor Bedrijven
Als u een alternatieve aanmeldings-id gebruikt met Exchange en Skype voor Bedrijven, is de gebruikerservaring afhankelijk van of u HMA gebruikt.
Notitie
Voor de beste eindgebruikerservaring raadt Microsoft aan hybride moderne verificatie te gebruiken.
Voor meer informatie, zie Overzicht van hybride moderne verificatie
Vereisten voor Exchange en Skype voor Bedrijven
Hier volgen de vereisten vooraf voor het bereiken van SSO met een alternatieve ID.
- Exchange Online moet moderne verificatie zijn ingeschakeld.
- Skype voor Bedrijven (SFB) Online moet moderne verificatie hebben ingeschakeld.
- Exchange on-premises moet moderne verificatie hebben ingeschakeld. Exchange 2013 CU19 of Exchange 2016 CU18 en hoger is vereist op alle Exchange-servers. Geen Exchange 2010 in de omgeving.
- Skype voor Bedrijven on-premises moet moderne verificatie hebben ingeschakeld.
- U moet Exchange- en Skype-clients gebruiken waarvoor moderne verificatie is ingeschakeld. Op alle servers moet SFB Server 2015 CU5 worden uitgevoerd.
- Skype voor Bedrijven-clients die moderne verificatie kunnen gebruiken
- iOS, Android, Windows Phone
- SFB 2016 (MA is standaard INGESCHAKELD, maar zorg ervoor dat deze niet is uitgeschakeld.)
- SFB 2013 (MA is standaard uitgeschakeld, dus zorg ervoor dat MA is ingeschakeld.)
- SFB Mac-bureaublad
- Exchange-clients die moderne verificatie kunnen gebruiken en ondersteuning bieden voor AltID-regkeys
- Alleen Office Pro Plus 2016
Ondersteunde Office-versie
Uw directory configureren voor eenmalige aanmelding met alternatieve id
Het gebruik van alternatieve id kan extra prompts voor verificatie veroorzaken als deze aanvullende configuraties niet zijn voltooid. Raadpleeg het artikel voor mogelijke gevolgen voor de gebruikerservaring met alternatieve id.
Met de volgende aanvullende configuratie wordt de gebruikerservaring aanzienlijk verbeterd en kunt u bijna nul vragen om verificatie voor alternatieve id-gebruikers in uw organisatie bereiken.
Stap 1: Bijwerken naar vereiste Office-versie
Office-versie 1712 (build no 8827.2148) en hoger hebben de verificatielogica bijgewerkt om het scenario alternatieve id af te handelen. Als u gebruik wilt maken van de nieuwe logica, moeten de clientcomputers worden bijgewerkt naar Office versie 1712 (build nr. 8827.2148) en hoger.
Stap 2: Bijwerken naar vereiste Windows-versie
Windows-versie 1709 en hoger hebben de authenticatielogica bijgewerkt om het Alternatieve ID-scenario af te handelen. Als u gebruik wilt maken van de nieuwe logica, moeten de clientcomputers worden bijgewerkt naar Windows versie 1709 en hoger.
Stap 3: register configureren voor betrokken gebruikers met behulp van groepsbeleid
De Office-toepassingen zijn afhankelijk van informatie die door de adreslijstbeheerder wordt verstrekt om de Alternatieve ID-omgeving te identificeren. De volgende registersleutels moeten worden geconfigureerd om Office-toepassingen te helpen bij het verifiëren van de gebruiker met alternatieve id zonder extra prompts weer te geven.
| Regkey om toe te voegen | Regkey-gegevensnaam, -type en -waarde | Vensters 7/8 | Windows 10 | Beschrijving |
|---|---|---|---|---|
| HKEY_CURRENT_USER\Software\Microsoft\AuthN | DomainHint REG_SZ contoso.com |
Verplicht | Verplicht | De waarde van deze registersleutel is een geverifieerde aangepaste domeinnaam in de tenant van de organisatie. Contoso corp kan bijvoorbeeld een waarde van Contoso.com in deze regkey opgeven als Contoso.com een van de geverifieerde aangepaste domeinnamen in de tenant Contoso.onmicrosoft.com is. |
| HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Identity | EnableAlternateIdSupport REG_DWORD 1 |
Vereist voor Outlook 2016 ProPlus | Vereist voor Outlook 2016 ProPlus | De waarde van deze regkey kan 1/0 zijn om aan te geven aan de Outlook-toepassing of deze de verbeterde verificatielogica voor alternatieve id's moet inschakelen. |
| HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\contoso.com\sts |
*
REG_DWORD 1 |
Verplicht | Verplicht | Deze regkey kan worden gebruikt om de STS in te stellen als een vertrouwde zone in de internetinstellingen. Bij de standaard AD FS-implementatie wordt aanbevolen om de AD FS-naamruimte toe te voegen aan de zone Lokaal intranet voor Internet Explorer. |
Nieuwe verificatiestroom na aanvullende configuratie
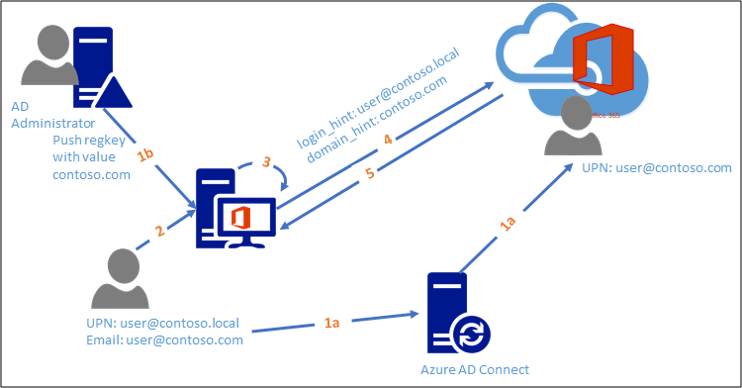
- a: Gebruiker wordt ingericht in Microsoft Entra ID met een alternatieve ID
b: Adreslijstbeheerder stuurt vereiste registersleutelinstellingen naar betrokken clientcomputers - Gebruiker verifieert zich op de lokale computer en opent een Office-toepassing
- Office-toepassing gebruikt de lokale sessiereferenties
- Office-applicatie authenticeert bij Microsoft Entra ID met behulp van de domeinhint die door de beheerder wordt verzonden en lokale inloggegevens.
- Microsoft Entra ID verifieert de gebruiker door te leiden naar de juiste federatierealm en een token uit te geven
Toepassingen en gebruikerservaring na de aanvullende configuratie
Niet-Exchange- en Skype voor Bedrijven-clients
| Cliënt | Ondersteuningsverklaring | Opmerkingen |
|---|---|---|
| Microsoft Teams | Ondersteund | |
| OneDrive voor Bedrijven | Ondersteund - registersleutel aan clientzijde aanbevolen | Als alternatieve id is geconfigureerd, ziet u dat de on-premises UPN vooraf is ingevuld in het verificatieveld. Dit moet worden gewijzigd in de alternatieve identiteit die wordt gebruikt. U wordt aangeraden de registersleutel aan de clientzijde te gebruiken die in dit artikel wordt vermeld: Office 2013 en Lync 2013 vragen regelmatig om referenties voor SharePoint Online, OneDrive en Lync Online. |
| Mobiele OneDrive voor Bedrijven-client | Ondersteund | |
| Activeringspagina van Office 365 Pro Plus | Ondersteund - registersleutel aan clientzijde aanbevolen | Als alternatieve id is geconfigureerd, ziet u dat de on-premises UPN vooraf is ingevuld in het verificatieveld. Dit moet worden gewijzigd in de alternatieve identiteit die wordt gebruikt. U wordt aangeraden de registersleutel aan de clientzijde te gebruiken die in dit artikel wordt vermeld: Office 2013 en Lync 2013 vragen regelmatig om referenties voor SharePoint Online, OneDrive en Lync Online. |
Exchange- en Skype voor Bedrijven-clients
| Cliënt | Ondersteuningsverklaring - met HMA | Ondersteuningsverklaring - zonder HMA |
|---|---|---|
| Vooruitzicht | Ondersteund, geen extra prompts | Ondersteund met moderne verificatie voor Exchange Online: Ondersteund met reguliere verificatie voor Exchange Online: Ondersteund met de volgende opmerkingen: |
| Hybride openbare mappen | Ondersteund, geen extra prompts. | Met moderne verificatie voor Exchange Online: ondersteund met reguliere verificatie voor Exchange Online: niet ondersteund |
| Kruislings overdracht tussen locaties | Zie Exchange configureren ter ondersteuning van gedelegeerde postvakmachtigingen in een hybride implementatie | Zie Exchange configureren ter ondersteuning van gedelegeerde postvakmachtigingen in een hybride implementatie |
| Toegang tot archiefpostvak (postvak on-premises - archief in de cloud) | Ondersteund, geen extra prompts | Ondersteund: gebruikers krijgen een extra prompt voor referenties bij het openen van het archief, ze moeten hun alternatieve id opgeven wanneer hierom wordt gevraagd. |
| Webtoegang tot Outlook | Ondersteund | Ondersteund |
| Outlook Mobile Apps voor Android, IOS en Windows Phone | Ondersteund | Ondersteund |
| Skype voor Bedrijven/Lync | Ondersteund, zonder extra prompts | Ondersteund (behalve zoals vermeld), maar er is een potentieel voor verwarring van gebruikers. Op mobiele clients wordt alternatieve id alleen ondersteund als SIP-adres = e-mailadres = Alternatieve id. Gebruikers moeten zich mogelijk twee keer aanmelden bij de Skype voor Bedrijven-bureaubladclient, eerst met de on-premises UPN en vervolgens met de alternatieve id. (Houd er rekening mee dat het 'aanmeldingsadres' eigenlijk het SIP-adres is dat mogelijk niet hetzelfde is als de gebruikersnaam, maar vaak wel). Wanneer de gebruiker voor het eerst om een gebruikersnaam wordt gevraagd, moet de gebruiker de UPN invoeren, zelfs als deze onjuist vooraf is ingevuld met het alternatieve id- of SIP-adres. Nadat de gebruiker op aanmelding met de UPN heeft geklikt, wordt de prompt gebruikersnaam opnieuw weergegeven, deze keer vooraf ingevuld met de UPN. Deze keer moet de gebruiker deze vervangen door de alternatieve id en op Aanmelden klikken om het aanmeldingsproces te voltooien. Op mobiele clients moeten gebruikers de on-premises gebruikers-id invoeren op de geavanceerde pagina, met behulp van de indeling SAM-stijl (domein\gebruikersnaam), niet de UPN-indeling. Als Skype voor Bedrijven of Lync na een geslaagde aanmelding 'Exchange heeft uw inloggegevens nodig', moet u de inloggegevens opgeven die geldig zijn voor de locatie van het postvak. Als het postvak zich in de cloud bevindt, moet u de alternatieve id opgeven. Als het postvak binnen de organisatie is, moet u de locale UPN opgeven. |
Aanvullende details en overwegingen
Microsoft Entra ID biedt verschillende functies met betrekking tot 'Alternatieve aanmeldings-id'
- Het artikel beschrijft de AD FS Alternatieve configuratiefunctie voor aanmeldings-id voor omgevingen met een federatieve1 identiteitsinfrastructuur.
- De Configuratie van Microsoft Entra Connect Sync waarmee wordt gedefinieerd welk on-premises kenmerk wordt gebruikt als Microsoft Entra-gebruikersnaam (userPrincipalName) voor federatieve1 OF beheerde2 identiteitsinfrastructuuromgevingen, die gedeeltelijk in dit artikel worden behandeld.
- De functie aanmelden bij Microsoft Entra ID met e-mail als alternatieve aanmeldings-ID voor beheerde2 identiteitsinfrastructuuromgevingen.
De alternatieve aanmeldings-id-functie die in dit artikel wordt beschreven, is beschikbaar voor federatieve1 identiteitsinfrastructuuromgevingen. Dit wordt niet ondersteund in de volgende scenario's:
- Een AlternateLoginID-kenmerk met niet-routeerbare domeinen (bijvoorbeeld Contoso.local) die niet kunnen worden geverifieerd door Microsoft Entra-id.
- Beheerde omgevingen waarop AD FS niet is geïmplementeerd. Raadpleeg de documentatie van Microsoft Entra Connect Sync of de documentatie over aanmelden bij Microsoft Entra ID met een e-mail als alternatieve aanmeldings-id. Als u besluit om de Microsoft Entra Connect Sync-configuratie in een omgeving met beheerde 2-identiteitsinfrastructuur aan te passen, zijn de toepassingen en gebruikerservaring na de aanvullende configuratiesectie van dit artikel mogelijk nog steeds van toepassing, terwijl de specifieke AD FS-configuratie niet meer van toepassing is omdat ad FS niet meer wordt geïmplementeerd in een beheerde2-identiteitsinfrastructuuromgeving.
Wanneer deze functie is ingeschakeld, is de alternatieve functie voor aanmeldings-id alleen beschikbaar voor verificatie via gebruikersnaam/wachtwoord in alle protocollen voor gebruikersnaam/wachtwoordverificatie die worden ondersteund door AD FS (SAML-P, WS-Fed, WS-Trust en OAuth).
Wanneer Windows Integrated Authentication (WIA) wordt uitgevoerd (bijvoorbeeld wanneer gebruikers vanaf intranet toegang proberen te krijgen tot een bedrijfstoepassing op een computer die lid is van een domein en AD FS-beheerder het verificatiebeleid heeft geconfigureerd voor het gebruik van WIA voor intranet), wordt UPN gebruikt voor verificatie. Als u claimregels voor de vertrouwende partijen hebt geconfigureerd voor de functie alternatieve aanmeldings-id, moet u ervoor zorgen dat deze regels nog steeds geldig zijn in het WIA-geval.
Als deze functie is ingeschakeld, moet voor de alternatieve aanmeldings-id-functie ten minste één globale catalogusserver bereikbaar zijn vanaf de AD FS-server voor elk forest met gebruikersaccounts dat DOOR AD FS wordt ondersteund. Als het niet mogelijk is om een globale catalogusserver in het gebruikersaccount-forest te bereiken, leidt dit ertoe dat AD FS terugvalt op het gebruik van de UPN. Standaard zijn alle domeincontrollers globale catalogusservers.
Wanneer dit is ingeschakeld, als de AD FS-server meer dan één gebruikersobject met dezelfde alternatieve aanmeldings-id-waarde vindt die is opgegeven in alle geconfigureerde gebruikersaccountforests, mislukt de aanmelding.
Wanneer alternatieve aanmeldings-id-functie is ingeschakeld, probeert AD FS de eindgebruiker eerst te verifiëren met alternatieve aanmeldings-id en vervolgens terug te vallen om UPN te gebruiken als het geen account kan vinden dat kan worden geïdentificeerd door de alternatieve aanmeldings-id. Zorg ervoor dat er geen conflicten zijn tussen de alternatieve aanmeldings-id en de UPN als u de UPN-aanmelding nog steeds wilt ondersteunen. Als u bijvoorbeeld het e-mailkenmerk instelt met de UPN van de andere gebruiker, kan de andere gebruiker zich niet aanmelden met zijn UPN.
Als een van de forests die door de beheerder is geconfigureerd niet beschikbaar is, blijft AD FS de gebruikersaccount met alternatieve aanmeldings-id opzoeken in andere forests die zijn geconfigureerd. Als de AD FS-server een uniek gebruikersobject vindt in de forests die het heeft doorzocht, meldt een gebruiker zich succesvol aan.
U kunt ook de AD FS-aanmeldingspagina aanpassen om eindgebruikers een hint te geven over de alternatieve aanmeldings-id. U kunt dit doen door de aangepaste beschrijving van de aanmeldingspagina toe te voegen (zie De aanmeldingspagina's van AD FS aanpassen of door de tekenreeks Aanmelden met organisatieaccount aan te passen boven het gebruikersnaamveld (zie Geavanceerde aanpassing van AD FS-aanmeldingspagina's voor meer informatie.
Het nieuwe claimtype dat de alternatieve aanmeldings-id-waarde bevat, is http:schemas.microsoft.com/ws/2013/11/alternateloginid
1 Een omgeving met federatieve identiteitsinfrastructuur vertegenwoordigt een omgeving met een id-provider, zoals AD FS of andere IDP van derden.
2 Een infrastructuuromgeving voor beheerde identiteit vertegenwoordigt een omgeving met Microsoft Entra-id als de id-provider die is geïmplementeerd met wachtwoord-hashsynchronisatie (PHS) of passthrough-verificatie (PTA).
Gebeurtenissen en prestatiemeters
De volgende prestatiemeteritems zijn toegevoegd om de prestaties van AD FS-servers te meten wanneer alternatieve aanmeldings-id is ingeschakeld:
Alternatieve aanmeldings-id-verificaties: het aantal verificaties dat wordt uitgevoerd met behulp van een alternatieve aanmeldings-id
Alternatieve aanmeldings-id-verificaties per seconde: het aantal verificaties dat wordt uitgevoerd met behulp van een alternatieve aanmeldings-id per seconde
Gemiddelde zoeklatentie voor alternatieve aanmeldings-id: gemiddelde zoeklatentie in de forests die een beheerder heeft geconfigureerd voor alternatieve aanmeldings-id
Hier volgen verschillende foutcases en de bijbehorende impact op de aanmeldingservaring van een gebruiker met gebeurtenissen die zijn vastgelegd door AD FS:
| Foutgevallen | Impact op aanmeldingservaring | Gebeurtenis |
|---|---|---|
| Kan geen waarde ophalen voor SAMAccountName voor het gebruikersobject | Mislukte aanmelding | Gebeurtenis-id 364 met uitzonderingsbericht MSIS8012: Kan samAccountName niet vinden voor de gebruiker: '{0}'. |
| Het kenmerk CanonicalName is niet toegankelijk | Mislukte aanmelding | Gebeurtenis-id 364 met uitzonderingsbericht MSIS8013: CanonicalName: '{0}' van de gebruiker:'{1}' is in een ongeldig formaat. |
| Er zijn meerdere gebruikersobjecten gevonden in één forest | Mislukte aanmelding | Gebeurtenis-ID 364 met het uitzonderingsbericht MSIS8015: Er zijn meerdere gebruikersaccounts gevonden met de identiteit '{0}' in forest '{1}' met de identiteiten: {2} |
| Meerdere gebruikersobjecten worden gevonden in meerdere forests | Mislukte aanmelding | Gebeurtenis-id 364 met uitzonderingsbericht MSIS8014: meerdere gebruikersaccounts gevonden met identiteit '{0}' in forests: {1} |