Introduction
The first step in implementing the Zero Trust strategy is to verify and secure identities. In the Zero Trust journey, identities control and administer access to critical data and resources. This strategy challenges the assumption of everything being safe within a defined network perimeter. No user, device, or application is trusted until verified.
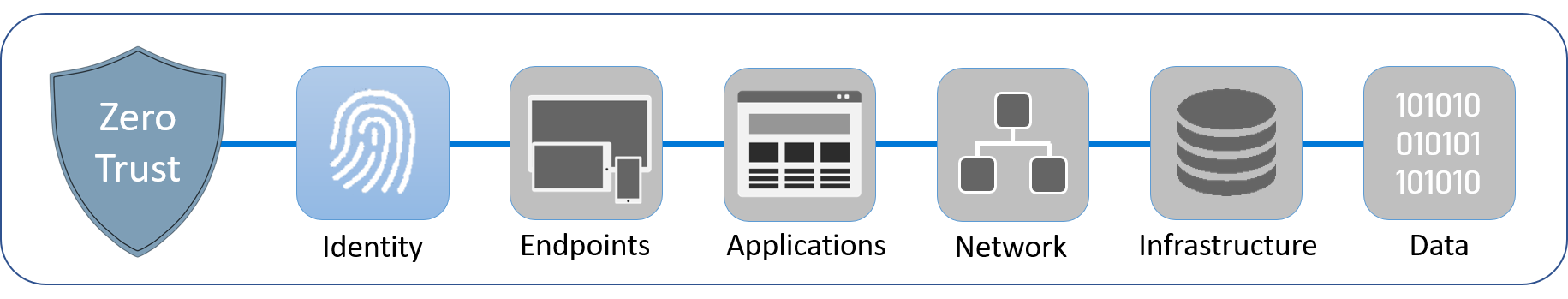
In this module, you'll learn about identity, the first of six components of Zero Trust. You'll understand the Zero Trust approach to identity and access management, and how critical it is for security and regulatory compliance. You must keep in mind the key principles of Zero Trust — verify explicitly, apply least privilege access, and always assume breach.