What authentication and verification methods are available in Microsoft Entra ID?
Microsoft recommends passwordless authentication methods such as Windows Hello, Passkeys (FIDO2), and the Microsoft Authenticator app because they provide the most secure sign-in experience. Although a user can sign-in using other common methods such as a username and password, passwords should be replaced with more secure authentication methods.
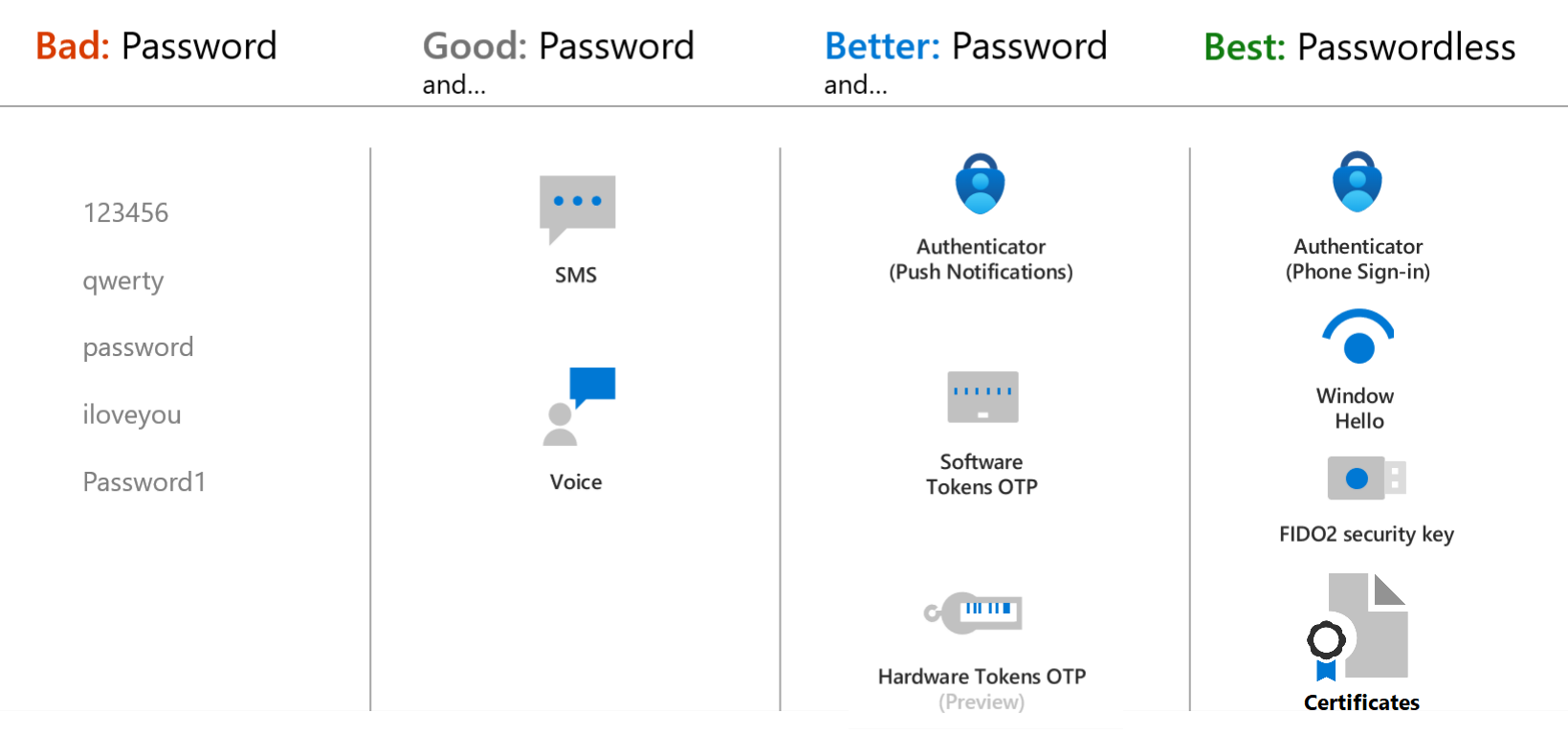
Microsoft Entra multifactor authentication adds additional security over only using a password when a user signs in. The user can be prompted for additional forms of authentication, such as to respond to a push notification, enter a code from a software or hardware token, or respond to a text message or phone call.
To simplify the user on-boarding experience and register for both MFA and self-service password reset (SSPR), we recommend you enable combined security information registration. For resiliency, we recommend that you require users to register multiple authentication methods. When one method isn't available for a user during sign-in or SSPR, they can choose to authenticate with another method. For more information, see Create a resilient access control management strategy in Microsoft Entra ID.
Here's a video we created to help you choose the best authentication method to keep your organization safe.
Authentication method strength and security
When you deploy features like Microsoft Entra multifactor authentication in your organization, review the available authentication methods. Choose the methods that meet or exceed your requirements in terms of security, usability, and availability. Where possible, use authentication methods with the highest level of security.
The following table outlines the security considerations for the available authentication methods. Availability is an indication of the user being able to use the authentication method, not of the service availability in Microsoft Entra ID:
| Authentication method | Security | Usability | Availability |
|---|---|---|---|
| Windows Hello for Business | High | High | High |
| Microsoft Authenticator | High | High | High |
| Authenticator Lite | High | High | High |
| Passkey (FIDO2) | High | High | High |
| Certificate-based authentication | High | High | High |
| OATH hardware tokens (preview) | Medium | Medium | High |
| OATH software tokens | Medium | Medium | High |
| Temporary Access Pass (TAP) | Medium | High | High |
| SMS | Medium | High | Medium |
| Voice | Medium | Medium | Medium |
| Password | Low | High | High |
For the latest information on security, check out our blog posts:
- It's time to hang up on phone transports for authentication
- Authentication vulnerabilities and attack vectors
Tip
For flexibility and usability, we recommend that you use the Microsoft Authenticator app. This authentication method provides the best user experience and multiple modes, such as passwordless, MFA push notifications, and OATH codes.
How each authentication method works
Some authentication methods can be used as the primary factor when you sign in to an application or device, such as using a FIDO2 security key or a password. Other authentication methods are only available as a secondary factor when you use Microsoft Entra multifactor authentication or SSPR.
The following table outlines when an authentication method can be used during a sign-in event:
| Method | Primary authentication | Secondary authentication |
|---|---|---|
| Windows Hello for Business | Yes | MFA* |
| Microsoft Authenticator (Push) | No | MFA and SSPR |
| Microsoft Authenticator (Passwordless) | Yes | No* |
| Authenticator Lite | No | MFA |
| Passkey (FIDO2) | Yes | MFA |
| Certificate-based authentication | Yes | MFA |
| OATH hardware tokens (preview) | No | MFA and SSPR |
| OATH software tokens | No | MFA and SSPR |
| Temporary Access Pass (TAP) | Yes | MFA |
| SMS | Yes | MFA and SSPR |
| Voice call | No | MFA and SSPR |
| Password | Yes | No |
* Windows Hello for Business, by itself, does not serve as a step-up MFA credential. For example, an MFA Challenge from Sign-in Frequency or SAML Request containing forceAuthn=true. Windows Hello for Business can serve as a step-up MFA credential by being used in FIDO2 authentication. This requires users to be registered for FIDO2 authentication to work successfully.
* Passwordless sign-in can be used for secondary authentication only if certificate-based authentication (CBA) is used for primary authentication. For more information, see Microsoft Entra certificate-based authentication technical deep dive.
All of these authentication methods can be configured in the Microsoft Entra admin center, and increasingly using the Microsoft Graph REST API.
To learn more about how each authentication method works, see the following separate conceptual articles:
- Windows Hello for Business
- Microsoft Authenticator app
- Passkey (FIDO2)
- Certificate-based authentication
- OATH hardware tokens (preview)
- OATH software tokens
- Temporary Access Pass (TAP)
- SMS sign-in and verification
- Voice call verification
- Password
Note
In Microsoft Entra ID, a password is often one of the primary authentication methods. You can't disable the password authentication method. If you use a password as the primary authentication factor, increase the security of sign-in events using Microsoft Entra multifactor authentication.
The following additional verification methods can be used in certain scenarios:
- App passwords - used for old applications that don't support modern authentication and can be configured for per-user Microsoft Entra multifactor authentication.
- Security questions - only used for SSPR
- Email address - only used for SSPR
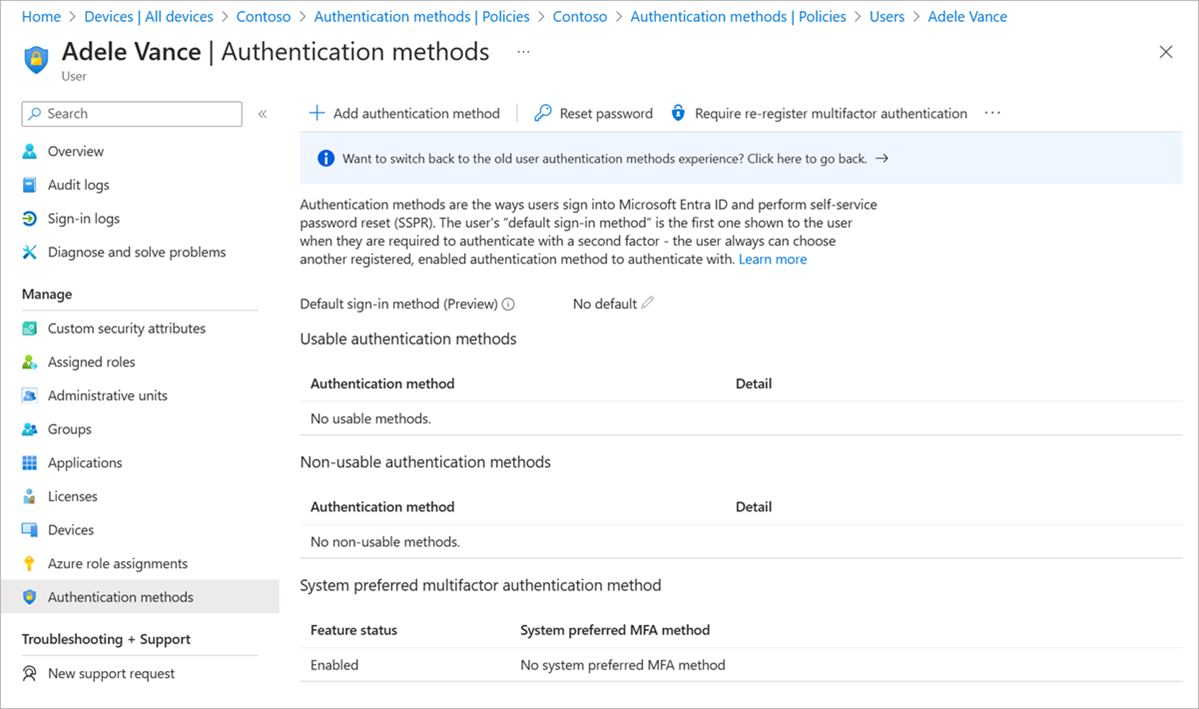
Usable and non-usable methods
Administrators can view user authentication methods in the Microsoft Entra admin center. Usable methods are listed first, followed by non-usable methods.
Each authentication method can become non-usable for different reasons. For example, a Temporary Access Pass may expire, or FIDO2 security key may fail attestation. The portal will be updated to provide the reason for why the method is non-usable.
Authentication methods that are no longer available due to "Require re-register multifactor authentication" are also displayed here.
Next steps
To get started, see the tutorial for self-service password reset (SSPR) and Microsoft Entra multifactor authentication.
To learn more about SSPR concepts, see How Microsoft Entra self-service password reset works.
To learn more about MFA concepts, see How Microsoft Entra multifactor authentication works.
Learn more about configuring authentication methods using the Microsoft Graph REST API.
To review what authentication methods are in use, see Microsoft Entra multifactor authentication authentication method analysis with PowerShell.
Povratne informacije
Kmalu na voljo: V letu 2024 bomo ukinili storitev Težave v storitvi GitHub kot mehanizem za povratne informacije za vsebino in jo zamenjali z novim sistemom za povratne informacije. Za več informacij si oglejte: https://aka.ms/ContentUserFeedback.
Pošlji in prikaži povratne informacije za