Understand the security architecture
When you understand the security architecture of finance and operations apps, you can more easily customize security to fit the requirements of your business.
In this lesson you will learn about:
- Security architecture
- Role-based security
- Duties
- Privileges
- Permissions
- Authentication
- Authorization
- Auditing
The system architecture of finance and operations apps uses the stack of features within Microsoft Azure. This allows finance and operations apps to operate and communicate with a variety of web enabled devices.
The security model is hierarchical, and each element in the hierarchy represents a different level of detail. Consider the following facts regarding security:
- Finance and operations apps uses role-based security.
- Access is granted only to security roles, not to individual users.
- Users are assigned to roles. A user who is assigned to a security role has access to the set of privileges that is associated with that role.
- A user who isn't assigned to any role has no privileges.
The following diagram provides a high-level overview of the security architecture:
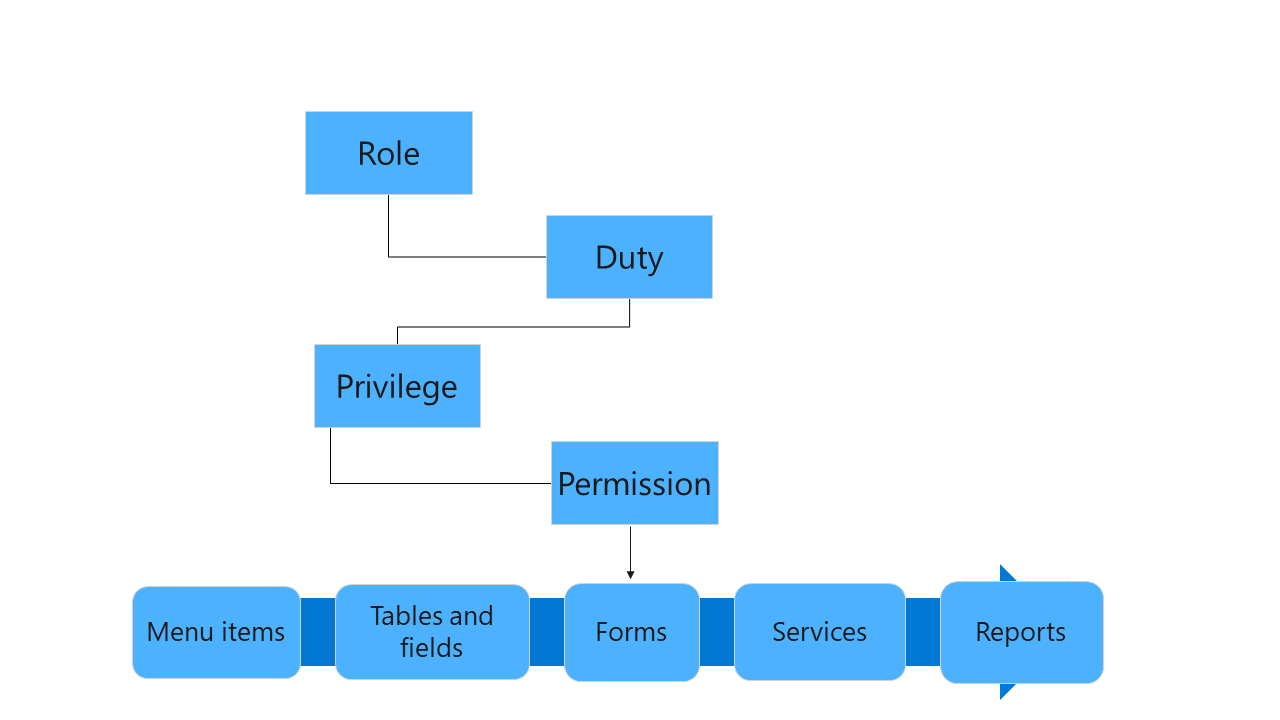
Role-based security
Role-based security is aligned with the structure of the business. Users are assigned to security roles based on their responsibilities in the organization and their participation in business processes. The administrator grants access to the duties that users in a role perform, not to the program elements that users must use.
In role-based security, access is not granted to individual users, only to security roles. Users are assigned to roles. A user who is assigned to a security role has access to the set of privileges that is associated with that role. A user who is not assigned to any role has no privileges.
All users must be assigned to at least one security role to have access to finance and operations apps. The security roles that are assigned to a user determine the duties that the user can perform and the parts of the user interface that the user can view.
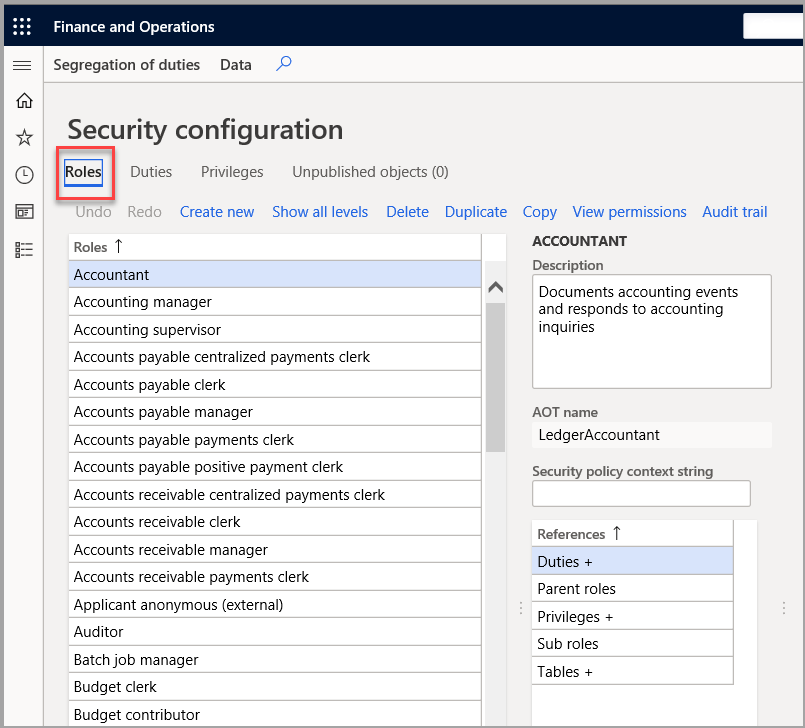
Users are assigned to roles via System administration > Security > Assign users to roles.
Because rules can be set up for automatic role assignment, the administrator does not have to be involved every time that a user's responsibilities change. After security roles and rules have been set up, business managers can control day-to-day user access based on business data.
By default, sample security roles are provided. All functionality in finance and operations apps is associated with at least one of the sample security roles. The administrator can assign users to the sample security roles, modify the sample security roles to fit the needs of the business, or create new security roles. By default, the sample roles are not arranged in a hierarchy.
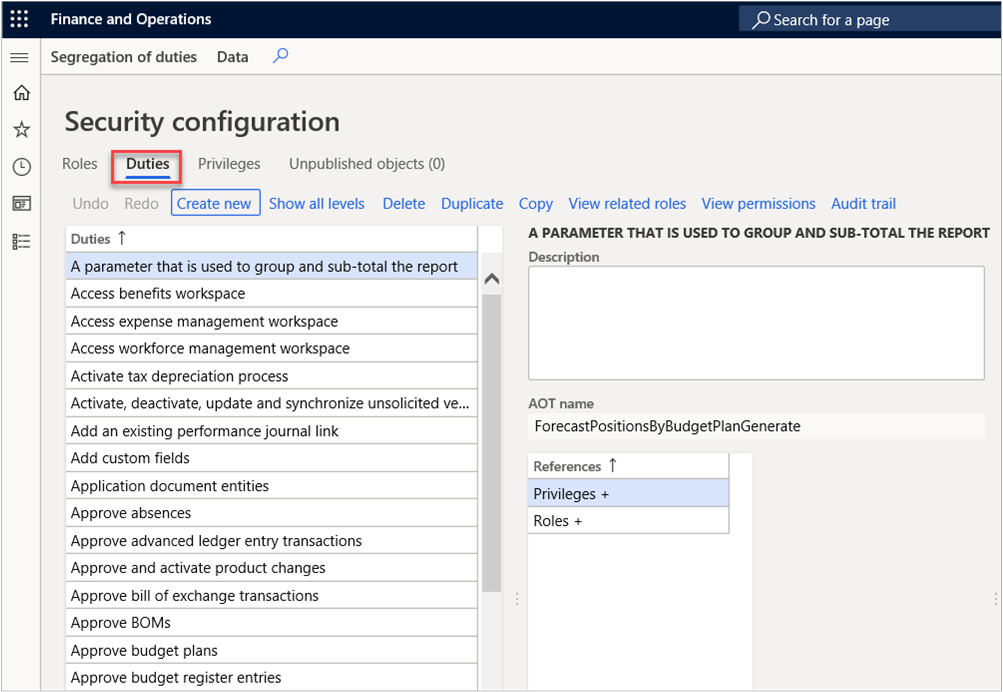
Duties
Duties correspond to parts of a business process. The administrator assigns duties to security roles. A duty can be assigned to more than one role. In finance and operations apps, duties contain privileges. For example, the Maintain bank transactions duty contains the generate deposit slips and cancel payments privileges. Both duties and privileges can be assigned to security roles. However, we recommend that you use duties to grant access to finance and operations apps.
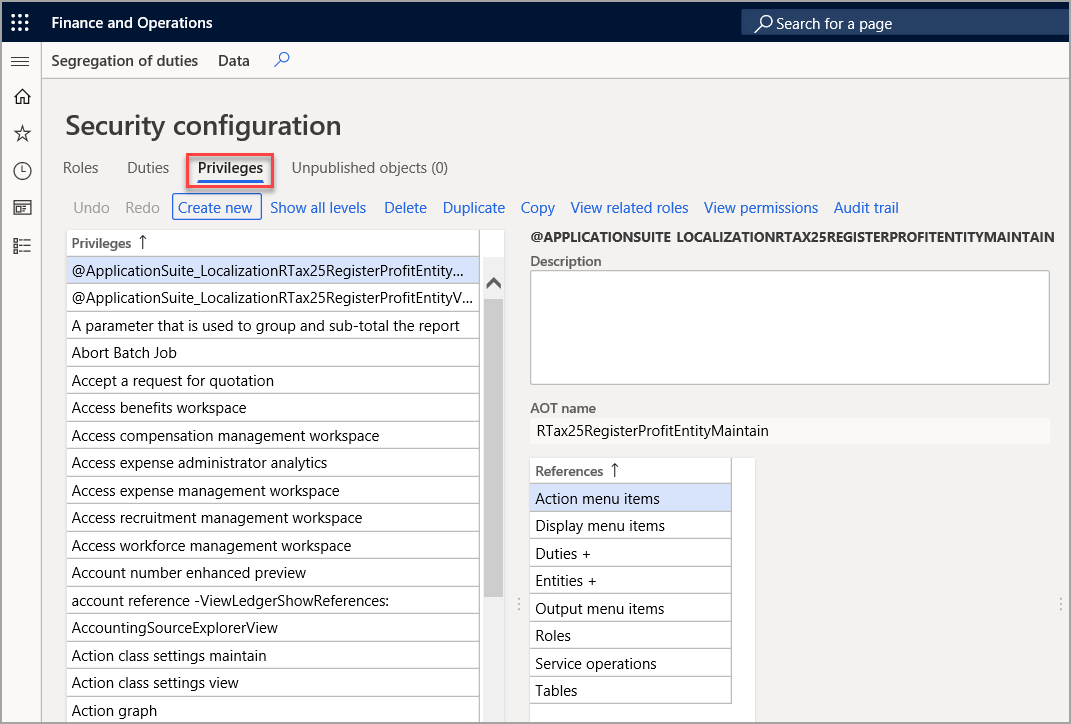
Privileges
Privileges can be assigned directly to roles. However, for easier maintenance, we recommend that you assign only duties to roles. A privilege specifies the level of access that is required to perform a job, solve a problem, or complete an assignment. It also contains permissions to individual application objects, such as user interface elements and tables.
For example, the Cancel payments privilege contains permissions to the menu items, fields, and tables that are required to cancel payments.
By default, privileges are provided for all features in finance and operations apps. The administrator can modify the permissions that are associated with a privilege or create new privileges.
Permissions
Permissions represent access to individual securable objects, such as menu items and tables. Privileges are composed of permissions and represent access to tasks, such as posting a journal and processing credits and collections. Duties are composed of privileges and represent parts of a business process, such as maintaining cash and bank transactions. Both duties and privileges can be assigned to roles to grant access to finance and operations apps.
Each function in finance and operations apps, such as a form or a service, is accessed through an entry point. Menu items, web content items, and service operations are referred to collectively as entry points.
Authentication
Only authenticated users who have user rights in finance and operations apps can establish a connection. finance and operations apps uses Microsoft Entra ID as a primary identity provider. To access the system, users must be provisioned into a finance and operations apps instance and should have a valid Microsoft Entra ID account in an authorized tenant.
Authorization
Authorization is the control of access to the finance and operations apps program. Security permissions are used to control access to individual elements of the program: menus, menu items, action and command buttons, reports, service operations, web URL menu items, web controls, and fields in the finance and operations apps client.
In finance and operations apps, individual security permissions are combined into privileges, and privileges are combined into duties. The administrator grants security roles access to the program by assigning duties and privileges to those roles.
Finance and operations apps uses context-based security to determine access to securable objects. When a privilege is associated with an entry point (such as a menu item or a service operation), a level of access, such as Read or Delete, is specified. The finance and operations apps authorization subsystem detects the access at run time, when that entry point is accessed, and applies the specified level of access to the securable object that the entry point leads to. This functionality helps to ensure that you do not assign more permissions for a user than you need to.
Auditing
Auditing of user sign in and sign-out is now enabled in finance and operations apps. The system logs when a user signs in or out of the application. A sign-out is logged even if the user's session expires or ends.
A system administrator or security administrator can access the audit logs by going to the User log page (System administration > Inquiries > User log).
Additional considerations:
- External Roles form allows administrators to assign security roles to an external part role such as a customer, vendor, prospect, prospective vendor and worker
- Dormant user security accounts allow you to identify idle accounts and find out if the accounts are enabled or disabled
