Manage resource accounts for service numbers
In Microsoft Teams, a resource account is required for each auto attendant or call queue. Resource accounts may also be assigned telephone numbers. This is how you assign phone numbers to auto attendants and call queues allowing callers from outside Teams to reach the auto attendant or call queue.
This article covers how to create resource accounts and ready them for use with auto attendants and call queues.
Before you start the procedures in this article, ensure you've done the following steps:
Note
Resource accounts used for auto attendants and call queues are disabled for sign in and must remain so. Chat and presence are not available for these accounts.
Obtain Microsoft Teams Phone Resource Account licenses
Each resource account requires a license in order to work with auto attendants and call queues, known as a Microsoft Teams Phone Resource Account license. Subscriptions with Teams Phone have access to a zero-cost allocation of Microsoft Teams Phone Resource Account licenses, and if more are needed, extra Microsoft Teams Phone Resource Account licenses can be purchased at a cost. For details on how to obtain these licenses, see Microsoft Teams Phone Resource Account licenses.
We cover how to assign the license to a resource account later in this article.
If you purchased Teams Phone Standard, Teams Phone with Calling Plan, or Teams Shared Devices licenses, you still need to complete the purchasing process for your allocation of Teams Phone Resource Account licenses, but your allotment of licenses will be zero cost at checkout.
To see if you already have Teams Phone Resource Account licenses in your tenant, sign into the Microsoft 365 admin center using an account with Global admin permissions. Then, go to Billing > Your products. If you have Teams Phone Resource Account licenses, they'll appear as Microsoft Teams Phone Resource Account.
- Open the Microsoft 365 admin center and sign in with a user that is a Global admin. This is usually the account you used to sign up for Microsoft 365.
- In the left navigation pane, go to Billing > Purchase services > Add-ons.
- Scroll to find the Microsoft Teams Phone Resource Account license.
- Select the Details button.
- Choose the number of licenses you want to purchase and a billing frequency.
- You need one license for each auto attendant and call queue you plan to set up. We recommend selecting at least five licenses so you can easily set up more auto attendants and call queues in the future without having to purchase more licenses right away.
- Select the Buy button.
- Fill in the purchasing details.
- Confirm your order details, and then select the Place order button.
There's zero cost for your allotment of licenses, but you still need to follow these steps to acquire the licenses.
Obtain phone numbers
Phone numbers are optional for auto attendants and call queues. For any auto attendant or call queue that you want to be reachable directly by a phone number, you must have a resource account with an associated phone number.
Resource accounts can use either toll or toll-free phone numbers. You can request new numbers or port existing numbers from another carrier.
Acceptable phone numbers that can be applied to resource accounts include:
- Calling Plans service numbers: To acquire service numbers with Calling Plans, see Getting service phone numbers.
- Direct Routing numbers: To acquire Direct Routing numbers, see Enable users for Direct Routing.
- Operator Connect numbers: To acquire Operator Connect numbers, see Configure Operator Connect.
Note
Resource accounts with Direct Routing phone numbers with or without extensions are supported. Currently, the Teams admin center only supports assigning Direct Routing phone numbers without extensions. To assign a Direct Routing phone number with an extension to a resource account, use the Teams PowerShell cmdlet Set-CsPhoneNumberAssignment.
To port a number from another carrier, see Transfer phone numbers to Teams.
Create a resource account
You can create a resource account in the Teams admin center.
- Sign into the Teams admin center.
- Expand Voice, and then select Resource accounts.
- Select Add.
- In the Add resource account pane, fill out Display name, Username, and the Resource account type. The resource account type can be either Auto attendant or Call queue, depending how you intend to use this resource account.
- Select Save.
Assign a license
For each resource account, you must assign a Microsoft Teams Phone Resource Account license.
- Sign into the Microsoft 365 admin center.
- Expand Users, then select Active users.
- Select the resource account to which you want to assign a license. The resource account's user pane will appear.
- On the Licenses and Apps tab, under Licenses, select Microsoft Teams Phone Resource Account.
- Select Save changes.
Note
If the resource account requires a phone number, check that the Select location dropdown list in the Licenses and Apps tab matches the intended country code.
Assign a phone number
If you're planning to use the resource account with an auto attendant or call queue that requires a phone number, assign a number to the resource account.
- Sign into the Teams admin center.
- Expand Voice, and then select Resource accounts page.
- Select the resource account to which you want to assign a phone number, and then select Assign/unassign.
- In the Phone number type dropdown, choose the type of number that you want to use.
- In the Assigned phone number box, search for the number you want to use and select Add. Be sure to include the country code (for example, +1 250 555 0012).
- Select Save.
Next steps
Once you complete the resource account setup and assign a phone number if needed, you're ready to use the resource account with an Auto attendant or Call queue.
To learn more, see the following references:
You can edit the resource account Display name and Resource account type using the Edit option. Select Save when you're done.
Change an existing resource account to use a Microsoft Teams Phone Resource Account license
To switch the licenses on your existing resource account from a Teams Phone Standard license to a Microsoft Teams Phone Resource Account license, you'll need to acquire the Microsoft Teams Phone Resource Account license, and then follow the steps in the Microsoft 365 admin center to Move users to a different subscription.
Warning
Always remove a Teams Phone Standard license and assign the Microsoft Teams Phone Resource Account license in the same license activity. If you remove the old license, save the account changes, add the new license, and then save the account settings again, the resource account may no longer function as expected. If this happens, we recommend you create a new resource account for the Microsoft Teams Phone Resource Account license and remove the broken resource account.
Skype For Business Server 2019
For resource accounts homed on Skype For Business Server 2019 that can be used with cloud Call queues and cloud Auto attendants, see Plan Cloud Call queues or Plan Cloud Auto attendants. Hybrid implementations (numbers homed on Direct Routing) are configured using the New-CsHybridApplicationEndpoint cmdlet on an on-premises Skype for Business Server 2019 server.
The application IDs that you need to use while creating the application instances are:
- Auto Attendant: ce933385-9390-45d1-9512-c8d228074e07
- Call Queue: 11cd3e2e-fccb-42ad-ad00-878b93575e07
Note
If you want the Call queue or Auto attendant to be searchable by Skype For Business Server 2019 users, you should create your resource accounts on Skype For Business Server 2019, since online resource accounts are not synced down to Active Directory. When DNS SRV records for sipfederationtls resolve to Skype for Business Server 2019, then resource accounts must be created on Skype For Business Server 2019 using SfB Management shell and synchronized to Microsoft Entra ID.
For hybrid implementations with Skype for Business Server:
Delete a resource account
Make sure you dissociate the telephone number from the resource account before deleting it, to avoid getting your phone number stuck in pending mode.
- Sign into the Teams admin center.
- Expand Voice, and then select Resource accounts page.
- Select the resource account to which you want to assign a phone number, and then select Assign/unassign.
- Select the X on the assigned Auto attendant or Call queue.
- Select the Save button.
After you do that, you can delete the resource account in the Microsoft 365 admin center, under the Users tab.
Hide resource accounts from Teams users
You may want to hide certain resources accounts from Teams users. For example, you may want to prevent Teams users from directly calling a Call queue and bypassing the Auto attendant where the hours of operation are configured.
Information barriers are used to hide the resource accounts. Review the information barriers documentation to understand the possible impacts before proceeding with the steps below.
Required subscriptions and permissions
To access and use information barriers, your organization must have one of the following subscriptions or add-ons:
- Microsoft 365 E5/A5 subscription (paid or trial version).
- Office 365 E5/A5/A3/A1 subscription (paid or trial version).
- Office 365 Advanced Compliance add-on.
- Microsoft 365 E3/A3/A1 subscription + the Microsoft 365 E5/A5 Compliance add-on.
- Microsoft 365 E3/A3/A1 subscription + the Microsoft 365 E5/A5 Insider Risk Management add-on.
Note
If you already have Exchange Online address book policies configured, they must be removed before proceeding with the steps below.
All the steps below are performed by the Tenant Global Administrator.
These instructions assume there are no other information barriers configured.
Teams admin center
- Sign into the Teams admin center.
- In the left-rail menu, expand Teams.
- Select Teams settings.
- Scroll down to Search by name.
- Turn on the toggle, and save the change.
For more information on this option, see Limit who users can see when searching the directory in Teams.
Compliance - Auditing
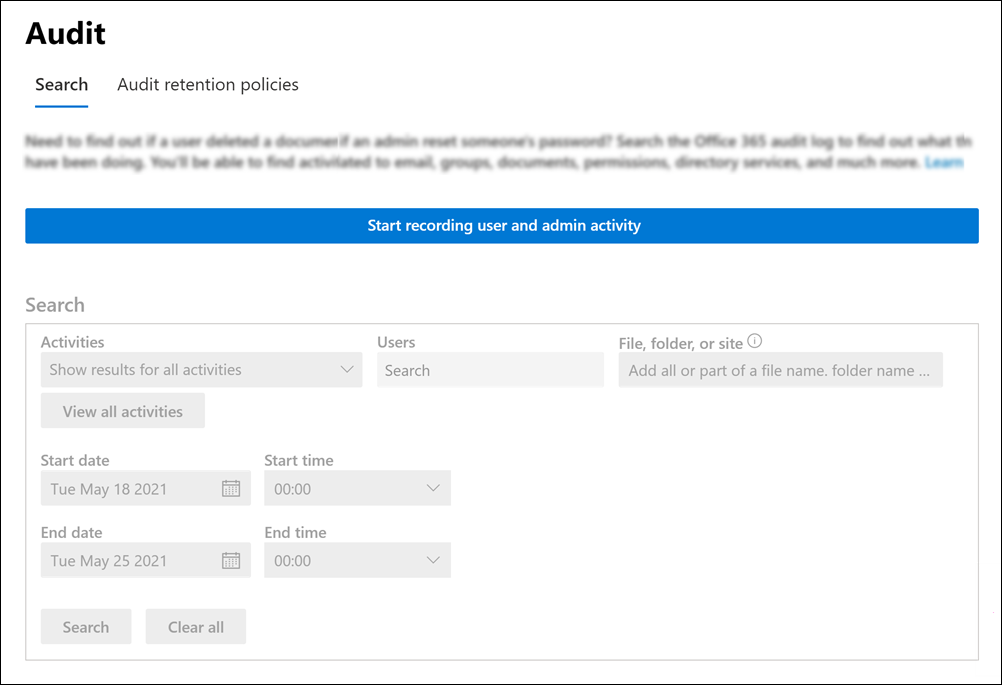
Sign into the Microsoft Purview compliance portal.
In the left navigation pane, select Audit.
If auditing is turned off, the following banner is displayed:
Select the Start recording user and admin activity.
For more information on auditing, see Set up Audit (Standard) in Microsoft 365.
Segmenting Data
The Resource Accounts that shouldn't be called directly need to be segmented and easily identifiable. This can be done by making them members of a particular group or by some unique information in their user profile such as:
- Company
- User principal name
- Location
- Department
- Usage location
- Mail nickname (Alias)
- Physical delivery office name (Office)
- Postal code
- Proxy address (Email Address)
- Street address
- Target address (ExternalEmailAddress)
- Mail (WindowsEmailAddress)
- Description
In the example steps below, the Department field is used.
For more information on segmenting users, see Identify segments.
Microsoft admin center
- Sign into the Microsoft 365 Admin Center.
- In the left navigation pane, select Active Users.
- Select the first Resource Account to block direct calls to.
- Select Manage contact information in the right pane.
- Replace the contents of the
Departmentfield with a unique word or acronym that isn't used as a department name. For example,DNC. - Save changes.
- Repeat for each Resource Account that needs to be blocked from receiving direct calls.
Compliance - Information Barriers
- Sign into the Microsoft Purview compliance portal.
- In the left navigation pane, select Information barriers > Segments.
- Select New segment.
- Enter a name for the segment, and select Next. For example,
Uncallable Resource Accounts. - Select + Add, and then Department.
- Enter the unique word or acronym used in Microsoft admin center step 5 above. For example,
DNC. - Select Next, and then Submit.
- Select New segment.
- Enter a name for the segment, and select Next. For example,
Callable Users. - Select + Add, and then Department.
- Select the Equal drop-down, and select Not equal to.
- Enter the unique word or acronym used in Microsoft admin center step 5 above. For example,
DNC. - Select Next, and then Submit.
- In the left navigation pane, select Information barriers > Policies.
- Select Create policy.
- Enter a name for the policy, and select Next. For example,
Uncallable Resource Accounts. - Select + Choose segment, add the segment created in step 9 above, and select Next. For example,
Callable Users. - Select Blocked from the Communication and collaboration drop-down.
- Select + Choose segment, add the segment created in step 4 above, and select Next. For example,
Uncallable Resource Accounts. - Set the policy to On, select Next, and then Submit.
- Select Create policy.
- Enter a name for the policy, and select Next. For example,
Callable Users. - Select + Choose segment, add the segment created in step 4, and select Next.
- Select Blocked from the Communication and collaboration drop-down.
- Select + Choose segment, add the segment created in step 9 above, and select Next.
- Set the policy to On, select Next, and then Submit.
- In the left navigation pane, select Information barriers > Policy application.
- Select Apply all policies.
Note
It may take 30 minutes or more for the policy to be applied.
Once the status shows completed, go into Teams Client and try to search for the Resource Accounts that were blocked. It may be necessary to clear the Teams cache.
If a Teams user has saved the Resource Account as a contact, they will no longer be able to call it.
Feedback
Kommer snart: Under hela 2024 kommer vi att fasa ut GitHub-problem som feedbackmekanism för innehåll och ersätta det med ett nytt feedbacksystem. Mer information finns i: https://aka.ms/ContentUserFeedback.
Skicka och visa feedback för