Introduction
Data protection is at the heart of a Zero Trust framework. Inadequately protected data can harm your users and the organization as a whole. Your organization must take appropriate measures to know its data, protect its data, and ensure that it's in a position to prevent data loss. These three aspects can be addressed in any order, but they all have to be achieved for effective data protection.
We're now at data in the Zero Trust journey. With a Zero Trust strategy, your organization can help ensure that its data is protected, regardless of its type, or whether it's in use, moving, or in long-term storage.
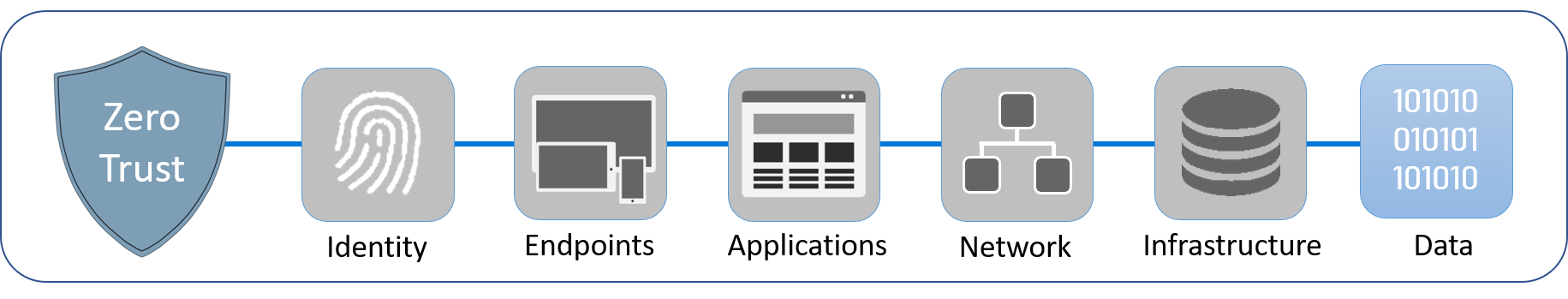
Remember that Zero Trust requires you to follow three security principles:
- Verify explicitly
- Use least privilege access
- Assume breach
To protect your organization and users, these principles need to be applied to all data. Here, you'll learn how to protect your data using a Zero Trust strategy.