Not
Åtkomst till den här sidan kräver auktorisering. Du kan prova att logga in eller ändra kataloger.
Åtkomst till den här sidan kräver auktorisering. Du kan prova att ändra kataloger.
Följande dokumentation innehåller information om hur du inaktiverar och aktiverar vissa TLS/SSL-protokoll och chiffersviter som Active Directory Federation Services (AD FS) använder.
TLS/SSL, Schannel och chiffersviter i AD FS
TLS-protokollet (Transport Layer Security) tillhandahåller krypterad säker kommunikation över nätverket. SSL-protokollet (Secure Sockets Layer) krypterar känsliga datautbyten som överförs mellan en webbserver och en webbläsare som liknar TLS. Active Directory Federation Services (AD FS) använder dessa protokoll för kommunikation. I dag finns det flera versioner av dessa protokoll.
Security Channel (Schannel) är en SSP (Security Support Provider) som implementerar standardautentiseringsprotokollen SSL, TLS och DTLS internet. SSPI (Security Support Provider Interface) är ett API som används av Windows-system för att utföra säkerhetsrelaterade funktioner, inklusive autentisering. SSPI fungerar som ett gemensamt gränssnitt för flera SSP:er, inklusive Schannel SSP.
En chiffersvit är en uppsättning kryptografiska algoritmer. Schannel SSP-implementeringen av TLS/SSL-protokollen använder algoritmer från en chiffersvit för att skapa nycklar och kryptera information. En chiffersvit anger en algoritm för var och en av följande uppgifter:
- Nyckelutbyte
- Masskryptering
- Meddelandeautentisering
AD FS använder Schannel.dll för att utföra sina säkra kommunikationsinteraktioner. För närvarande stöder AD FS alla protokoll och chiffersviter som Schannel.dll stöder.
Hantera TLS/SSL-protokoll och chiffersviter
Important
Det här avsnittet innehåller steg som beskriver hur du ändrar registret. Allvarliga problem kan dock uppstå om du ändrar registret felaktigt. Därför bör du se till att du följer dessa steg noggrant.
Tänk på att en ändring av standardsäkerhetsinställningarna för SCHANNEL kan bryta eller förhindra kommunikation mellan vissa klienter och servrar. Detta inträffar om säker kommunikation krävs och de inte har något protokoll att förhandla kommunikation med.
Om du tillämpar dessa ändringar måste de tillämpas på alla dina AD FS-servrar i servergruppen. När du har tillämpat ändringarna krävs en omstart.
I dagens tid blir härdning av servrar och borttagning av äldre eller svaga chiffersviter en viktig prioritet för många organisationer. Programvarupaket är tillgängliga som testar dina servrar och ger detaljerad information om dessa protokoll och sviter. För att förbli kompatibla eller uppnå säkra klassificeringar har det blivit ett måste att ta bort eller inaktivera svagare protokoll eller chiffersviter. Resten av det här dokumentet innehåller vägledning om hur du aktiverar eller inaktiverar vissa protokoll och chiffersviter.
Följande registernycklar finns på samma plats: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols. Använd Registereditorn eller PowerShell för att aktivera eller inaktivera dessa protokoll och chiffersviter.
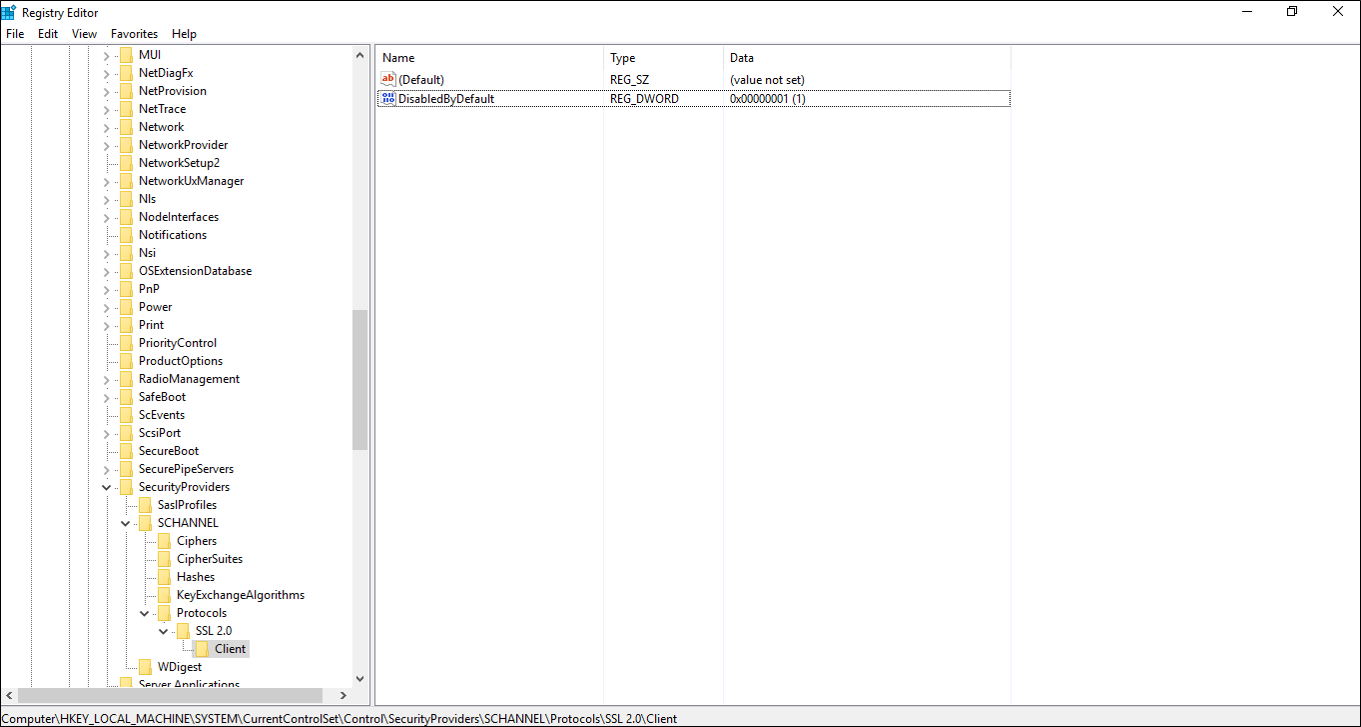
Aktivera och inaktivera SSL 3.0
Använd följande registernycklar och deras värden för att aktivera och inaktivera SSL 3.0.
Aktivera SSL 3.0
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server | Enabled | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server | DisabledByDefault | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client | Enabled | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client | DisabledByDefault | 00000000 |
Inaktivera SSL 3.0
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server | Enabled | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server | DisabledByDefault | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client | Enabled | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client | DisabledByDefault | 00000001 |
Använda PowerShell för att inaktivera SSL 3.0
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'SSL 3.0 has been disabled.'
Aktivera och inaktivera TLS 1.0
Använd följande registernycklar och deras värden för att aktivera och inaktivera TLS 1.0.
Important
Inaktivering av TLS 1.0 bryter förtroenderelationen mellan WAP och AD FS. Om du inaktiverar TLS 1.0 bör du aktivera stark autentisering för dina program. Mer information finns i Aktivera stark autentisering för .NET-program
Aktivera TLS 1.0
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server | Enabled | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server | DisabledByDefault | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client | Enabled | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client | DisabledByDefault | 00000000 |
Inaktivera TLS 1.0
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server | Enabled"=00000000 | |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server | DisabledByDefault | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client | Enabled | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client | DisabledByDefault | 00000001 |
Använda PowerShell för att inaktivera TLS 1.0
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.0 has been disabled.'
Aktivera och inaktivera TLS 1.1
Använd följande registernycklar och deras värden för att aktivera och inaktivera TLS 1.1.
Aktivera TLS 1.1
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server | Enabled | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server | DisabledByDefault | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client | Enabled | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client | DisabledByDefault | 00000000 |
Inaktivera TLS 1.1
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server | Enabled | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server | DisabledByDefault | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client | Enabled | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client | DisabledByDefault | 00000001 |
Använda PowerShell för att inaktivera TLS 1.1
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.1 has been disabled.'
Inaktivera TLS 1.2
TLS 1.2 är aktiverat som standard från och med Windows Server 2012. Du kan använda följande registernycklar och deras värden för att inaktivera TLS 1.2.
Warning
Det rekommenderas inte att inaktivera TLS 1.2 eftersom det kan störa funktionaliteten för andra komponenter på servern som förlitar sig på det här protokollet. Till exempel kräver tjänster som Microsoft Azure AD Connect (Azure AD Sync) TLS 1.2 för att fungera korrekt. Om du inaktiverar det kan det leda till tjänstfel eller försämrad funktionalitet.
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server | Enabled | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server | DisabledByDefault | 00000001 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client | Enabled | 00000000 |
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client | DisabledByDefault | 00000001 |
Använda PowerShell för att inaktivera TLS 1.2
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.2 has been disabled.'
Aktivera eller inaktivera hashar, chiffer och chiffersviter
Kontroll av chiffer, hashvärden och nyckelutbytesalgoritmer, förutom nyckelstorlek, via registret stöds inte. Hashar, chiffer och nyckelutbytesalgoritmer styrs via PowerShell, MDM eller Chiffersvitordning.
En fullständig lista över chiffersviter som stöds finns i Chiffersviter i TLS/SSL (Schannel SSP). Den här artikeln innehåller en tabell med sviter som är aktiverade som standard och visar vilka sviter som stöds men inte är aktiverade som standard. Information om hur du prioriterar chiffersviterna finns i Prioritera Schannel Chiffersviter.
Aktivera stark autentisering för .NET-program
.NET Framework 3.5/4.0/4.5.x-programmen kan växla standardprotokollet till TLS 1.2 genom att aktivera Registernyckeln SchUseStrongCrypto. Dessa registernycklar tvingar .NET-program att använda TLS 1.2.
Important
För AD FS på Windows Server 2016 och Windows Server 2012 R2 måste du använda .NET Framework 4.0/4.5.x-nyckeln: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319
För .NET Framework 3.5 använder du följande registernyckel:
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727 | SchUseStrongCrypto | 00000001 |
För .NET Framework 4.0/4.5.x använder du följande registernyckel:
| Path | Värdenamn | Värdedata |
|---|---|---|
| HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 | SchUseStrongCrypto | 00000001 |
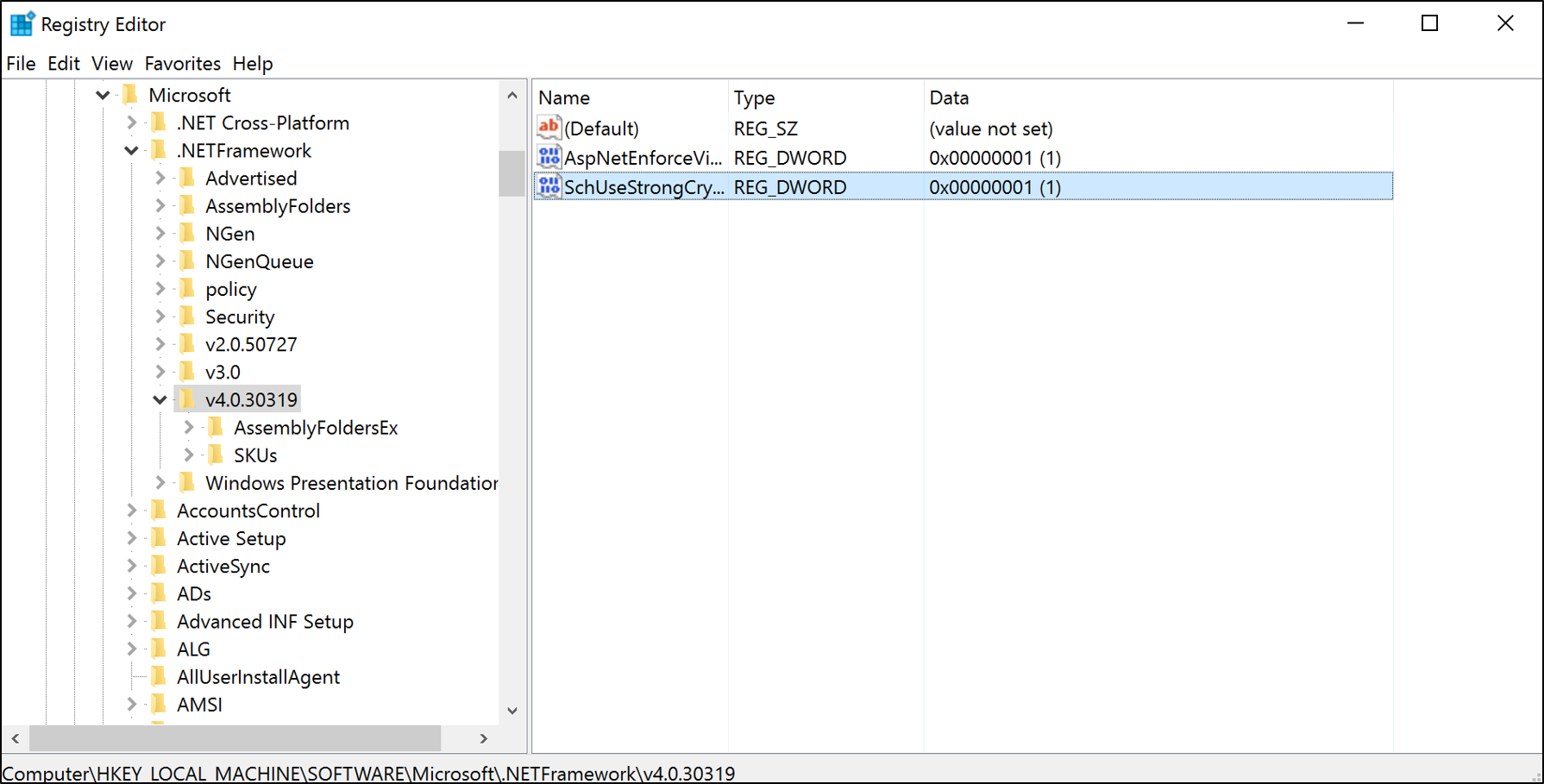
New-ItemProperty -path 'HKLM:\SOFTWARE\Microsoft\.NetFramework\v4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null