Configure Azure RBAC for FHIR
Important
Azure API for FHIR will be retired on September 30, 2026. Follow the migration strategies to transition to Azure Health Data Services FHIR® service by that date. Due to the retirement of Azure API for FHIR, new deployments won't be allowed beginning April 1, 2025. Azure Health Data Services FHIR service is the evolved version of Azure API for FHIR that enables customers to manage FHIR, DICOM, and MedTech services with integrations into other Azure services.
In this article, you learn how to use Azure role-based access control (Azure RBAC) to assign access to the Azure API for FHIR® data plane. Azure RBAC is the preferred methods for assigning data plane access when data plane users are managed in the Microsoft Entra tenant associated with your Azure subscription. If you're using an external Microsoft Entra tenant, refer to the local RBAC assignment reference.
Confirm Azure RBAC mode
To use Azure RBAC, your Azure API for FHIR must be configured to use your Azure subscription tenant for data plane, and there should be no assigned identity object IDs. You can verify your settings by inspecting the Authentication of your Azure API for FHIR:
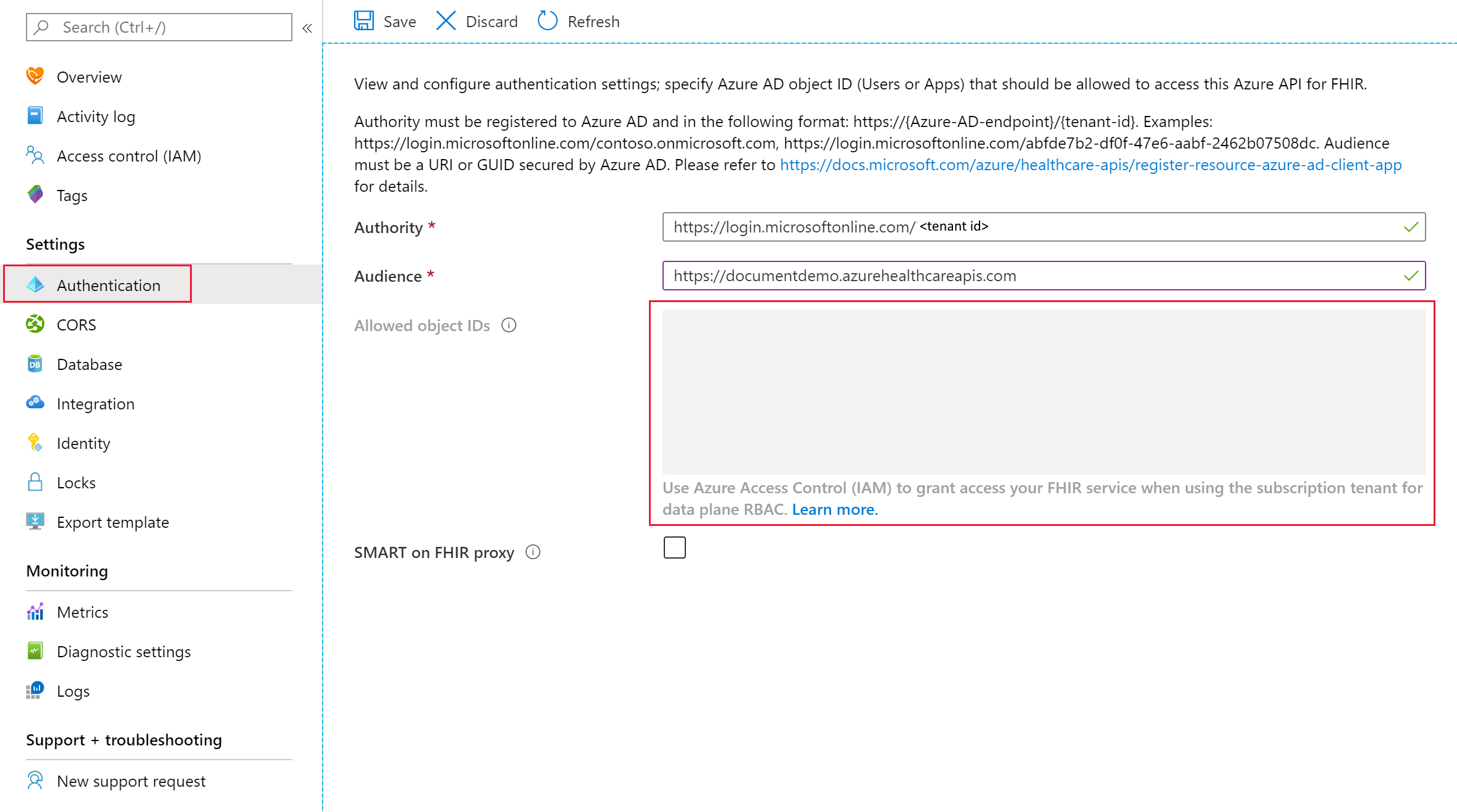
The Authority should be set to the Microsoft Entra tenant associated with your subscription and there should be no GUIDs in the box labeled Allowed object IDs. Notice the box is disabled and a label indicates that Azure RBAC should be used to assign data plane roles.
Assign roles
To grant users, service principals, or groups access to the FHIR data plane, select Access control (IAM), then select Role assignments and select + Add.
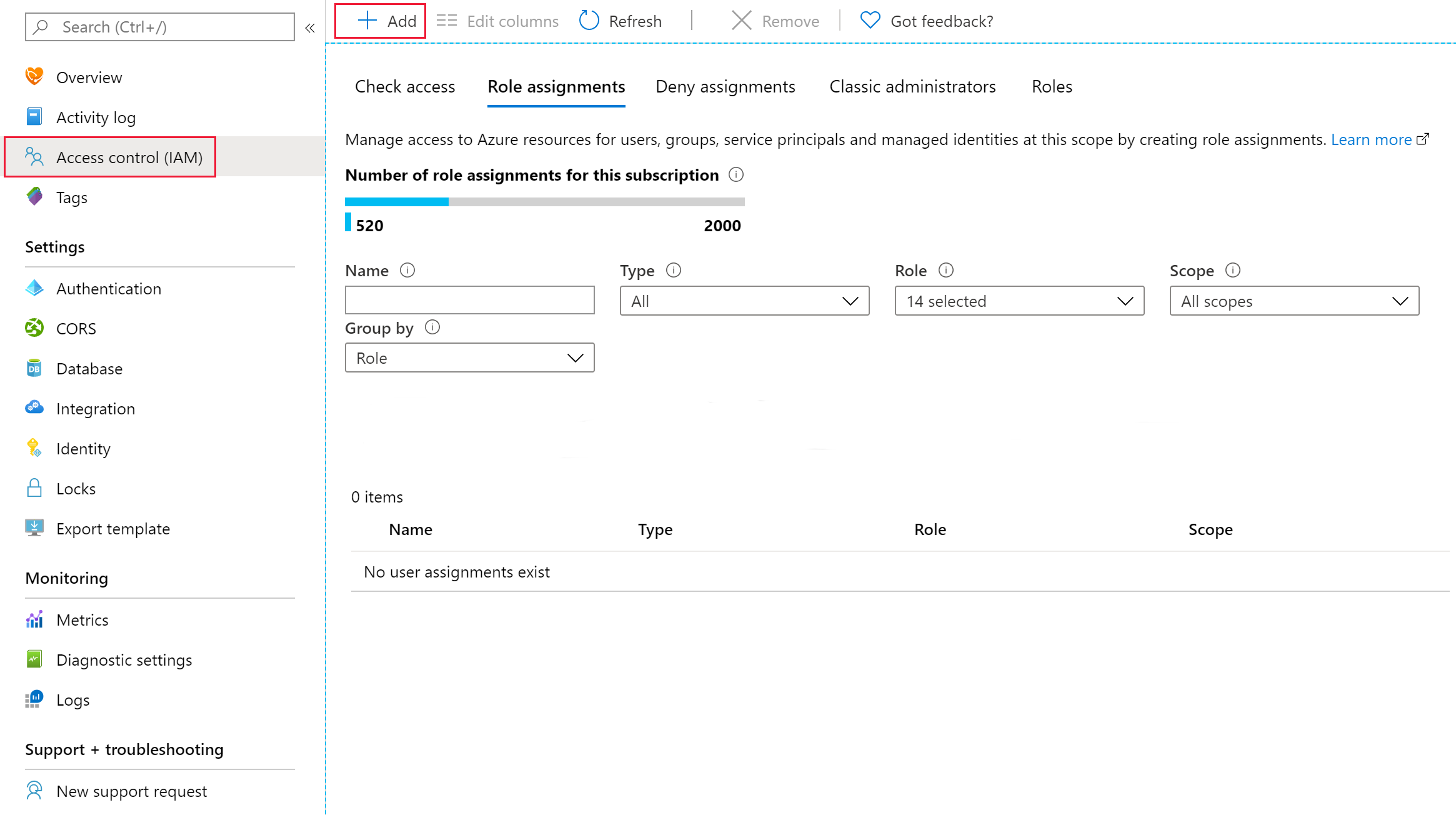
In the Role selection, search for one of the built-in roles for the FHIR data plane.

You can choose from among the following.
- FHIR Data Reader: Can read (and search) FHIR data
- FHIR Data Writer: Can read, write, and soft delete FHIR data
- FHIR Data Exporter: Can read and export (
$exportoperator) data - FHIR Data Contributor: Can perform all data plane operations
In the Select box, search for a user, service principal, or group that you wish to assign the role to.
Note
Make sure that the client application registration is completed. See details on application registration If OAuth 2.0 authorization code grant type is used, grant the same FHIR application role to the user. If OAuth 2.0 client credentials grant type is used, this step is not required.
Caching behavior
The Azure API for FHIR caches decisions for up to 5 minutes. If you grant a user access to the FHIR server by adding them to the list of allowed object IDs, or you remove them from the list, you should expect it to take up to five minutes for changes in permissions to propagate.
Next steps
In this article, you learned how to assign Azure roles for the FHIR data plane. For information about Azure API for FHIR configuration settings, see
Note
FHIR® is a registered trademark of HL7 and is used with the permission of HL7.