How Defender for Cloud Apps helps protect your Microsoft 365 environment
As a major productivity suite providing cloud file storage, collaboration, BI, and CRM tools, Microsoft 365 enables your users to share their documents across your organization and partners in a streamlined and efficient way. Using Microsoft 365 may expose your sensitive data not only internally, but also to external collaborators, or even worse make it publicly available via a shared link. Such incidents might occur due to malicious actor, or by an unaware employee. Microsoft 365 also provides a large third-party app eco-system to help boost productivity. Using these apps can expose your organization to the risk of malicious apps or use of apps with excessive permissions.
Connecting Microsoft 365 to Defender for Cloud Apps gives you improved insights into your users' activities, provides threat detection using machine learning based anomaly detections, information protection detections (such as detecting external information sharing), enables automated remediation controls, and detects threats from enabled third-party apps in your organization.
Defender for Cloud Apps integrates directly with Microsoft 365's audit logs and provides protection for all supported services. For a list of supported services, see Microsoft 365 services that support auditing.
Use this app connector to access SaaS Security Posture Management (SSPM) features, via security controls reflected in Microsoft Secure Score. Learn more.
File scanning improvements for Microsoft 365
Defender for Cloud Apps has added new file scanning improvements for SharePoint and OneDrive:
Faster near-real-time scanning speed for files in SharePoint and OneDrive.
Better identification for a file's access level in SharePoint: file access level in SharePoint will be marked by default as Internal, and not as Private (since every file in SharePoint is accessible by the site owner, and not only by the file owner).
Note
This change could impact your file policies (if a file policy is looking for Internal or Private files in SharePoint).
Main threats
- Compromised accounts and insider threats
- Data leakage
- Insufficient security awareness
- Malicious third-party apps
- Malware
- Phishing
- Ransomware
- Unmanaged bring your own device (BYOD)
How Defender for Cloud Apps helps to protect your environment
- Detect cloud threats, compromised accounts, and malicious insiders
- Discover, classify, label, and protect regulated and sensitive data stored in the cloud
- Discover and manage OAuth apps that have access to your environment
- Enforce DLP and compliance policies for data stored in the cloud
- Limit exposure of shared data and enforce collaboration policies
- Use the audit trail of activities for forensic investigations
Control Microsoft 365 with built-in policies and policy templates
You can use the following built-in policy templates to detect and notify you about potential threats:
| Type | Name |
|---|---|
| Built-in anomaly detection policy | Activity from anonymous IP addresses Activity from infrequent country Activity from suspicious IP addresses Impossible travel Activity performed by terminated user (requires Microsoft Entra ID as IdP) Malware detection Multiple failed login attempts Ransomware detection Suspicious email deletion activity (Preview) Suspicious inbox forwarding Unusual file deletion activities Unusual file share activities Unusual multiple file download activities |
| Activity policy template | Logon from a risky IP address Mass download by a single user Potential ransomware activity Access level change (Teams) External user added (Teams) Mass deletion (Teams) |
| File policy template | Detect a file shared with an unauthorized domain Detect a file shared with personal email addresses Detect files with PII/PCI/PHI |
| OAuth app anomaly detection policy | Misleading OAuth app name Misleading publisher name for an OAuth app Malicious OAuth app consent |
For more information about creating policies, see Create a policy.
Automate governance controls
In addition to monitoring for potential threats, you can apply and automate the following Microsoft 365 governance actions to remediate detected threats:
| Type | Action |
|---|---|
| Data governance | OneDrive: - Inherit parent folder permissions - Make file/folder private - Put file/folder in admin quarantine - Put file/folder in user quarantine - Trash file/folder - Remove a specific collaborator - Remove external collaborators on file/folder - Apply Microsoft Purview Information Protection sensitivity label - Remove Microsoft Purview Information Protection sensitivity label SharePoint: - Inherit parent folder permissions - Make file/folder private - Put file/folder in admin quarantine - Put file/folder in user quarantine - Put file/folder in user quarantine and add owner permissions - Trash file/folder - Remove external collaborators on file/folder - Remove a specific collaborator - Apply Microsoft Purview Information Protection sensitivity label - Remove Microsoft Purview Information Protection sensitivity label |
| User governance | - Notify user on alert (via Microsoft Entra ID) - Require user to sign in again (via Microsoft Entra ID) - Suspend user (via Microsoft Entra ID) |
| OAuth app governance | - Revoke OAuth app permission |
For more information about remediating threats from apps, see Governing connected apps.
Protect Microsoft 365 in real time
Review our best practices for securing and collaborating with external users and blocking and protecting the download of sensitive data to unmanaged or risky devices.
Defender for Cloud Apps integration with Microsoft 365
Defender for Cloud Apps supports the legacy Microsoft 365 Dedicated Platform as well as the latest offerings of Microsoft 365 services, commonly referred as the vNext release family of Microsoft 365.
In some cases, a vNext service release differs slightly at the administrative and management levels from the standard Microsoft 365 offering.
Audit logging
Defender for Cloud Apps integrates directly with Microsoft 365's audit logs and receives all audited events from all supported services. For a list of supported services, see Microsoft 365 services that support auditing.
Exchange administrator audit logging, which is enabled by default in Microsoft 365, logs an event in the Microsoft 365 audit log when an administrator (or a user who has been assigned administrative privileges) makes a change in your Exchange Online organization. Changes made using the Exchange admin center or by running a cmdlet in Windows PowerShell are logged in the Exchange admin audit log. For more detailed information about admin audit logging in Exchange, see Administrator audit logging.
Events from Exchange, Power BI, and Teams will only appear after activities from those services are detected in the portal.
Multi-geo deployments are only supported for OneDrive
Microsoft Entra integration
If your Microsoft Entra ID is set to automatically sync with the users in your Active Directory on-premises environment the settings in the on-premises environment override the Microsoft Entra settings and use of the Suspend user governance action is reverted.
For Microsoft Entra sign-in activities, Defender for Cloud Apps only surfaces interactive sign-in activities and sign-in activities from legacy protocols such as ActiveSync. Non-interactive sign-in activities may be viewed in the Microsoft Entra audit log.
If Office apps are enabled, groups that are part of Microsoft 365 are also imported to Defender for Cloud Apps from the specific Office apps, for example, if SharePoint is enabled, Microsoft 365 groups are imported as SharePoint groups as well.
Quarantine support
In SharePoint and OneDrive, Defender for Cloud Apps supports user quarantine only for files in Shared Documents libraries (SharePoint Online) and files in the Documents library (OneDrive for Business).
In SharePoint, Defender for Cloud Apps supports quarantine tasks only for files with Shared Documents in path in English.
Connect Microsoft 365 to Microsoft Defender for Cloud Apps
This section provides instructions for connecting Microsoft Defender for Cloud Apps to your existing Microsoft 365 account using the app connector API. This connection gives you visibility into and control over Microsoft 365 use. For information about how Defender for Cloud Apps protects Microsoft 365, see Protect Microsoft 365.
Use this app connector to access SaaS Security Posture Management (SSPM) features, via security controls reflected in Microsoft Secure Score. Learn more.
Prerequisites:
You must have at least one assigned Microsoft 365 license to connect Microsoft 365 to Defender for Cloud Apps.
To enable monitoring of Microsoft 365 activities in Defender for Cloud Apps, you are required to enable auditing in Microsoft Purview.
Exchange Mailbox audit logging must be turned on for each user mailbox before user activity in Exchange Online is logged, see Exchange Mailbox activities.
You must enable auditing in Power BI to get the logs from there. Once auditing is enabled, Defender for Cloud Apps starts getting the logs (with a delay of 24-72 hours).
You must enable auditing in Dynamics 365 to get the logs from there. Once auditing is enabled, Defender for Cloud Apps starts getting the logs (with a delay of 24-72 hours).
To connect Microsoft 365 to Defender for Cloud Apps:
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors.
In the App connectors page, select +Connect an app, and then select Microsoft 365.
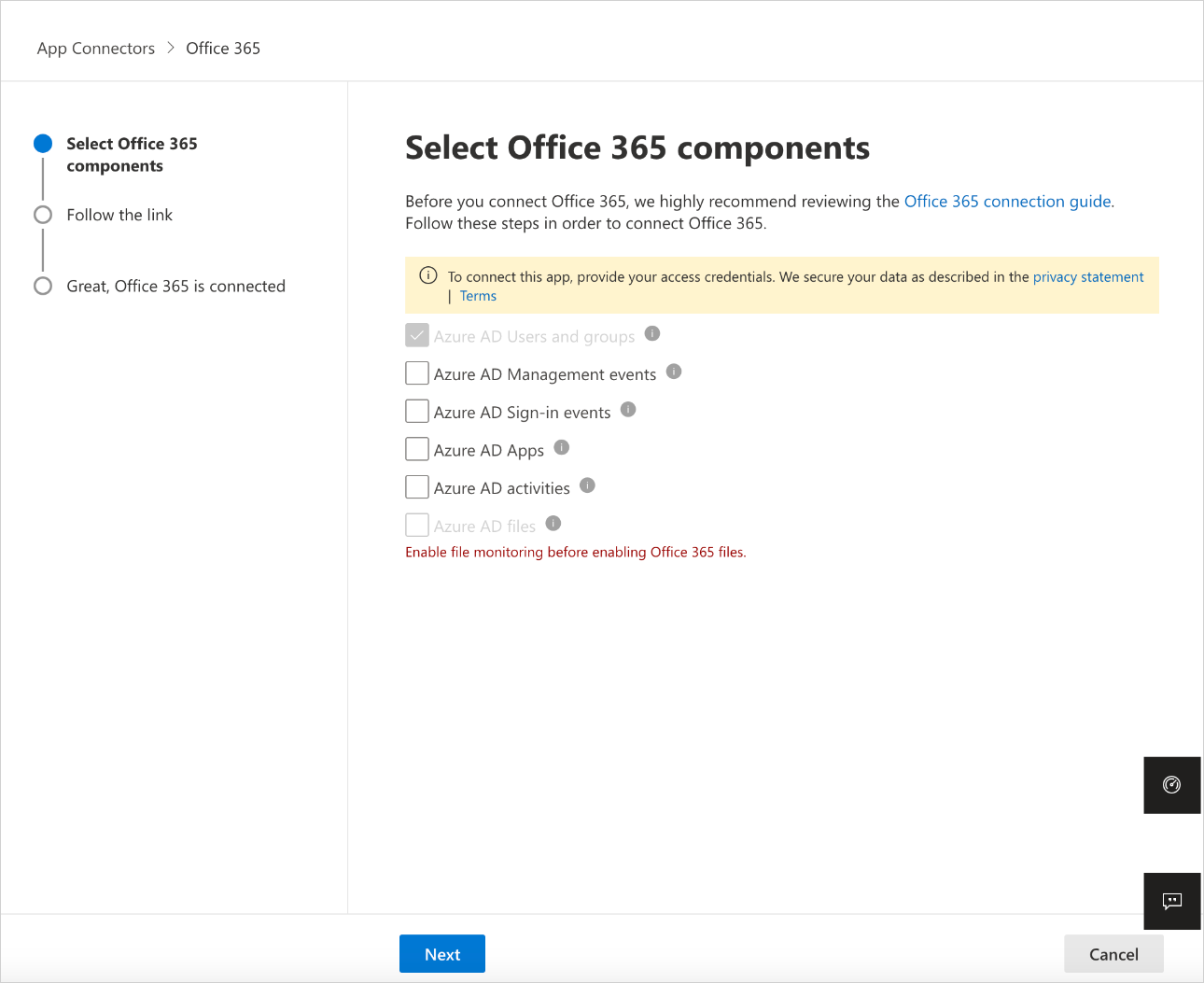
In the Select Microsoft 365 components page, select the options you require, and then select Connect.
Note
- For best protection, we recommend selecting all Microsoft 365 components.
- The Azure AD files component, requires the Azure AD activities component and Defender for Cloud Apps file monitoring (Settings > Cloud Apps > Files > Enable file monitoring).
On the Follow the link page, select Connect Microsoft 365.
After Microsoft 365 is displayed as successfully connected, select Done.
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors. Make sure the status of the connected App Connector is Connected.
SaaS Security Posture Management (SSPM) data is shown in the Microsoft Defender Portal on the Secure Score page. For more information, see Security posture management for SaaS apps.
Note
After connecting Microsoft 365, you will see data from a week back including any third-party applications connected to Microsoft 365 that are pulling APIs. For third-party apps that weren't pulling APIs prior to connection, you see events from the moment you connect Microsoft 365 because Defender for Cloud Apps turns on any APIs that had been off by default.
If you have any problems connecting the app, see Troubleshooting App Connectors.
Next steps
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.