How Defender for Cloud Apps helps protect your ServiceNow environment
As a major CRM cloud provider, ServiceNow incorporates large amounts of sensitive information about customers, internal processes, incidents, and reports inside your organization. Being a business-critical app, ServiceNow is accessed and used by people inside your organization and by others outside of it (such as partners and contractors) for various purposes. In many cases, a large proportion of your users accessing ServiceNow have low awareness of security and might put your sensitive information at risk by unintentionally sharing it. In other instances, malicious actors may gain access to your most sensitive customer-related assets.
Connecting ServiceNow to Defender for Cloud Apps gives you improved insights into your users' activities, provides threat detection using machine learning based anomaly detections, and information protection detections such as identifying when sensitive customer information is uploaded to the ServiceNow cloud.
Use this app connector to access SaaS Security Posture Management (SSPM) features, via security controls reflected in Microsoft Secure Score. Learn more.
Main threats
- Compromised accounts and insider threats
- Data leakage
- Insufficient security awareness
- Unmanaged bring your own device (BYOD)
How Defender for Cloud Apps helps to protect your environment
- Detect cloud threats, compromised accounts, and malicious insiders
- Discover, classify, label, and protect regulated and sensitive data stored in the cloud
- Enforce DLP and compliance policies for data stored in the cloud
- Limit exposure of shared data and enforce collaboration policies
- Use the audit trail of activities for forensic investigations
SaaS security posture management
Connect ServiceNow to automatically get security recommendations for ServiceNow in Microsoft Secure Score.
In Secure Score, select Recommended actions and filter by Product = ServiceNow. For example, recommendations for ServiceNow include:
- Enable MFA
- Activate the explicit role plugin
- Enable high security plugin
- Enable script request authorization
For more information, see:
Control ServiceNow with built-in policies and policy templates
You can use the following built-in policy templates to detect and notify you about potential threats:
| Type | Name |
|---|---|
| Built-in anomaly detection policy | Activity from anonymous IP addresses Activity from infrequent country |
| Activity from suspicious IP addresses Impossible travel Activity performed by terminated user (requires Microsoft Entra ID as IdP) Multiple failed login attempts Ransomware detection Unusual multiple file download activities |
|
| Activity policy template | Logon from a risky IP address Mass download by a single user |
| File policy template | Detect a file shared with an unauthorized domain Detect a file shared with personal email addresses Detect files with PII/PCI/PHI |
For more information about creating policies, see Create a policy.
Automate governance controls
In addition to monitoring for potential threats, you can apply and automate the following ServiceNow governance actions to remediate detected threats:
| Type | Action |
|---|---|
| User governance | - Notify user on alert (via Microsoft Entra ID) - Require user to sign in again (via Microsoft Entra ID) - Suspend user (via Microsoft Entra ID) |
For more information about remediating threats from apps, see Governing connected apps.
Protect ServiceNow in real time
Review our best practices for securing and collaborating with external users and blocking and protecting the download of sensitive data to unmanaged or risky devices.
Connect ServiceNow to Microsoft Defender for Cloud Apps
This article provides instructions for connecting Microsoft Defender for Cloud Apps to your existing ServiceNow account using the app connector API. This connection gives you visibility into and control over ServiceNow use. For information about how Defender for Cloud Apps protects ServiceNow, see Protect ServiceNow.
Use this app connector to access SaaS Security Posture Management (SSPM) features, via security controls reflected in Microsoft Secure Score. Learn more.
Prerequisites
Defender for Cloud Apps supports the following ServiceNow versions:
- Eureka
- Fiji
- Geneva
- Helsinki
- Istanbul
- Jakarta
- Kingston
- London
- Utah
- Madrid
- New York
- Orlando
- Paris
- Quebec
- Rome
- San Diego
- Tokyo
- Vancouver
- Washington
- Xanadu
In order to connect ServiceNow with Defender for Cloud Apps, you must have the Admin role and make sure the ServiceNow instance supports API access.
For more information, see the ServiceNow product documentation.
Tip
We recommend deploying ServiceNow using OAuth app tokens, available for Fuji and later releases. For more information, see the relevant ServiceNow documentation.
For earlier releases, a legacy connection mode is available based on user/password. The username/password provided are only used for API token generation and are not saved after the initial connection process.
How to connect ServiceNow to Defender for Cloud Apps using OAuth
Sign in with an Admin account to your ServiceNow account.
Note
The username/password provided are only used for API token generation and are not saved after the initial connection process.
In the Filter navigator search bar, type OAuth and select Application Registry.
In the Application Registries menu bar, select New to create a new OAuth profile.
Under What kind of OAuth application?, select Create an OAuth API endpoint for external clients.
Under Application Registries New record fill in the following fields:
Name field, name the new OAuth profile, for example, CloudAppSecurity.
The Client ID is generated automatically. Copy this ID, you need to paste it into Defender for Cloud Apps to complete connection.
In the Client Secret field, enter a string. If left empty, a random Secret is generated automatically. Copy and save it for later.
Increase the Access Token Lifespan to at least 3,600.
Select Submit.
Update the lifespan of the refresh token:
On the ServiceNow pane, search for System OAuth, and then select Application Registry.
Select the name of the OAuth that was defined, and change Refresh Token Lifespan to 7,776,000 seconds (90 days).
Select Update.
Establish an internal procedure to ensure that the connection remains alive. A couple of days before the expected expiration of the refresh token lifespan. Revoke to the old refresh token. We don't recommend keeping old keys for security reasons.
On the ServiceNow pane, search for System OAuth, and then select Manage Tokens.
Select the old token from the list according to the OAuth name and expiration date.
Select Revoke Access > Revoke.
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors.
In the App connectors page, select +Connect an app, and then ServiceNow.
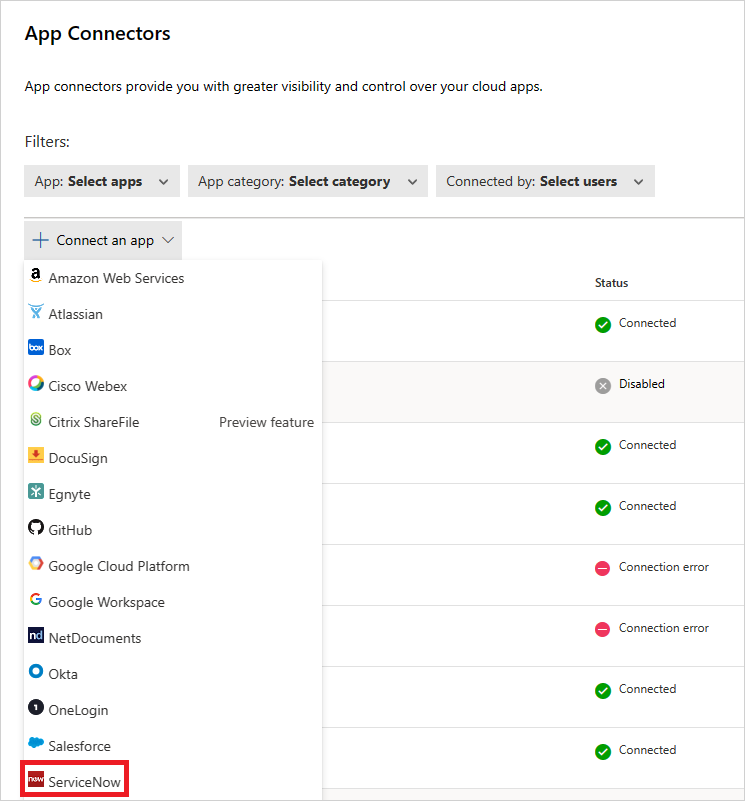
In the next window, give the connection a name and select Next.
In the Enter details page, select Connect using OAuth token (recommended). Select Next.
In the Basic Details page, add your ServiceNow user ID, password, and instance URL in the appropriate boxes. Select Next.
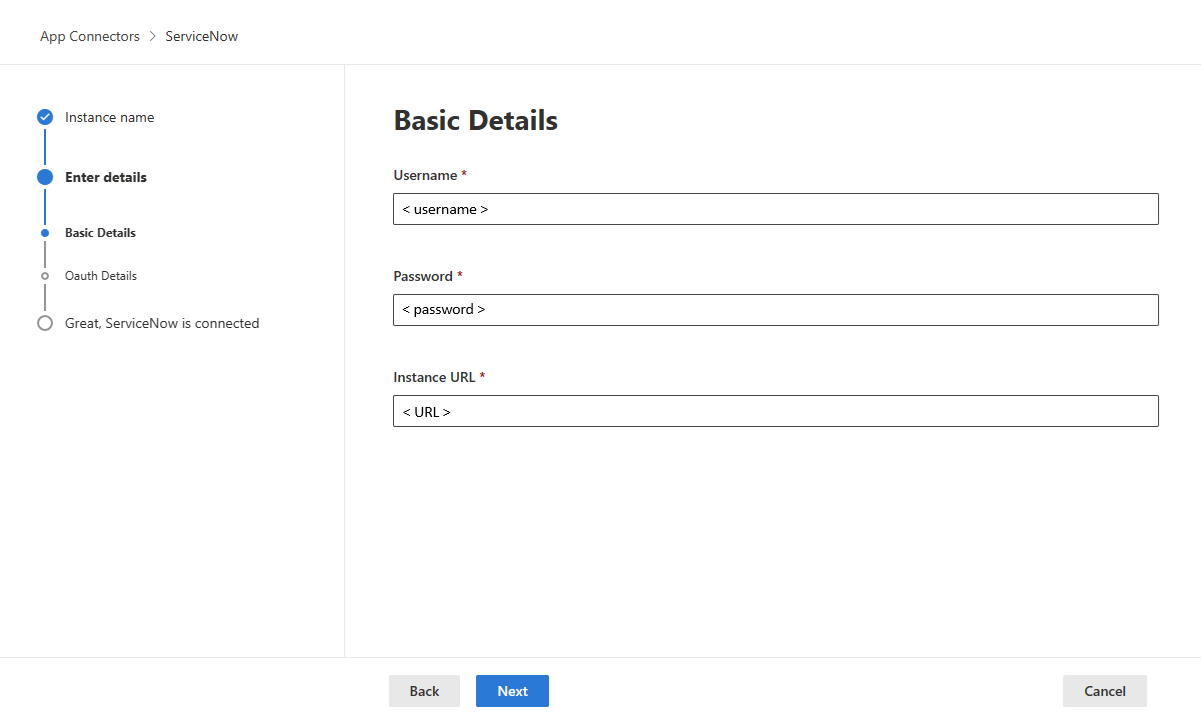
To find your ServiceNow User ID, in the ServiceNow portal, go to Users and then locate your name in the table.
In the OAuth Details page, enter your Client ID and Client Secret. Select Next.
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors. Make sure the status of the connected App Connector is Connected.
After connecting ServiceNow, you'll receive events for 1 hour prior to connection.
Legacy ServiceNow connection
To connect ServiceNow with Defender for Cloud Apps, you must have admin-level permissions and make sure the ServiceNow instance supports API access.
Sign in with an Admin account to your ServiceNow account.
Create a new service account for Defender for Cloud Apps and attach the Admin role to the newly created account.
Make sure the REST API plug-in is turned on.
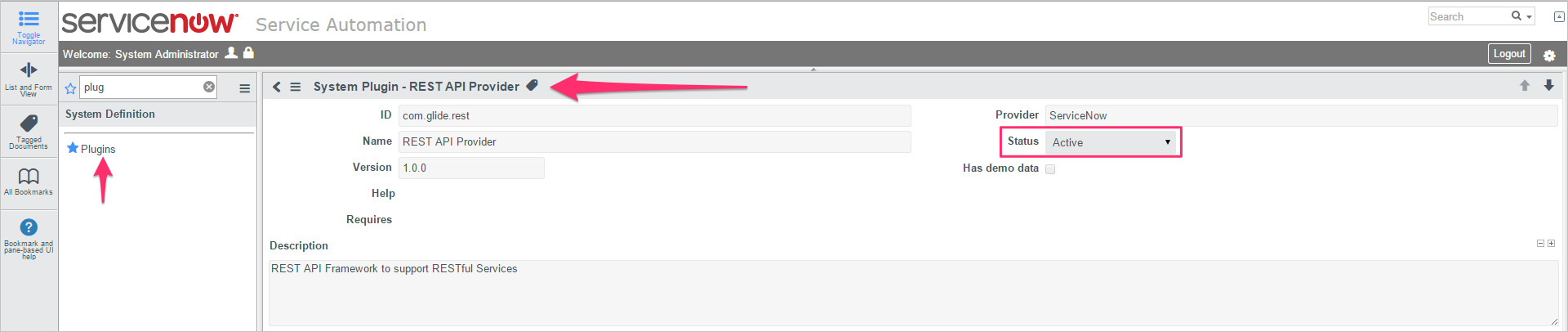
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors.
In the App connectors page, select +Connect an app, and then ServiceNow.

In the next window, give the connection a name and select Next.
In the Enter details page, select Connect using username and password only. Select Next.
In the Basic Details page, add your ServiceNow user ID, password, and instance URL in the appropriate boxes. Select Next.
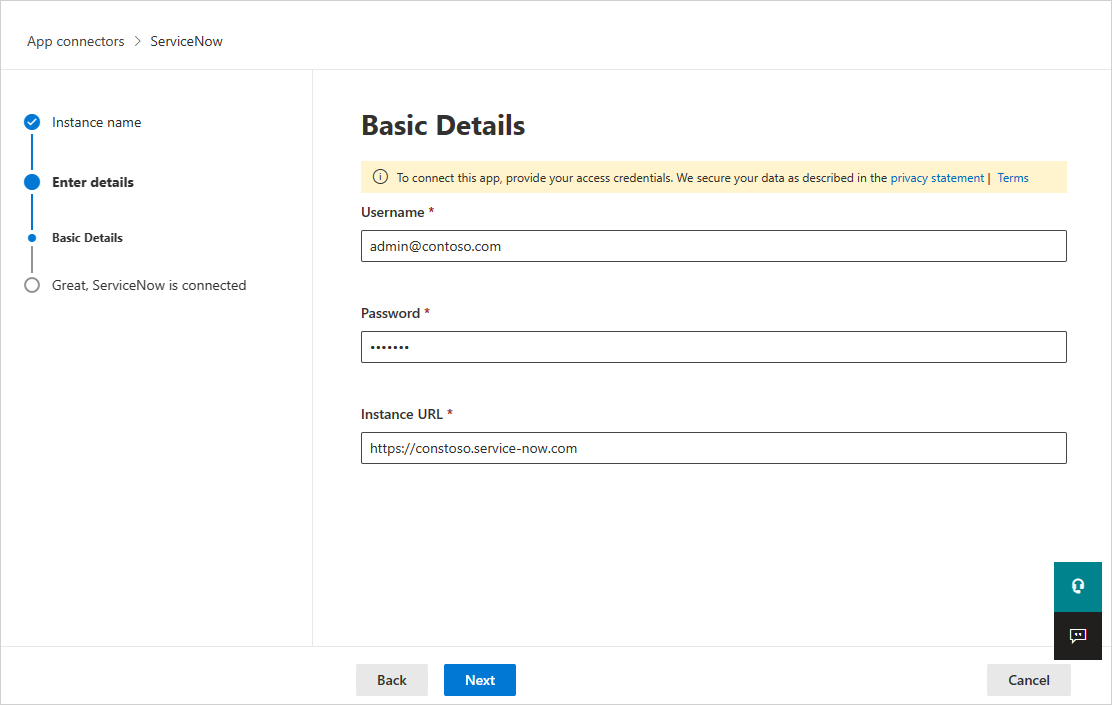
Select Connect.
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors. Make sure the status of the connected App Connector is Connected. After connecting ServiceNow, you'll receive events for one hour prior to connection.
If you have any problems connecting the app, see Troubleshooting App Connectors.
Next steps
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.