platí pro: SQL Server 2022 (16.x)
SQL Server 2022 (16.x)
V tomto článku si ukážeme, jak nastavit správce Microsoft Entra, aby povolil ověřování pomocí Microsoft Entra ID (dříve Azure Active Directory) pro SQL Server pomocí webu Azure Portal a rozhraní API, jako jsou:
- PowerShell
- Nástroj Azure CLI
- Šablona ARM
Budeme také procházet aktualizované funkce, abychom na webu Azure Portal nastavili správce Microsoft Entra pro SQL Server, který by umožňoval automatické vytváření certifikátů a registraci aplikací. Dříve nastavení ověřování Microsoft Entra pro SQL Server vyžadovalo ruční nastavení správce Microsoft Entra pomocí certifikátu Azure a registrace aplikace.
Poznámka:
I když je Microsoft Entra ID novým názvem pro Azure Active Directory (Azure AD), aby nedošlo k narušení stávajících prostředí, Azure AD stále zůstává v některých pevně zakódovaných prvcích, jako jsou pole uživatelského rozhraní, zprostředkovatelé připojení, chybové kódy a příkazy cmdlet. V tomto článku jsou tyto dva názvy zaměnitelné.
Požadavky
Příprava před nastavením správce Microsoft Entra
Následující oprávnění jsou nezbytná k nastavení správce Microsoft Entra na SQL Serveru – Azure Arc a key vaultu prostředků.
Postupujte podle pokynů a ujistěte se, že je SQL Server připojený ke službě Azure Arc. Uživatel, který nastavuje správce Microsoft Entra pro prostředek SQL Server – Azure Arc, by měl mít roli Přispěvatele serveru.
- Přejděte na web Azure Portal.
- Vyberte SQL Server – Azure Arca vyberte instanci pro váš hostitelský SQL Server.
- Vyberte Řízení přístupu (IAM) .
- Vyberte Přidat>Přidat přiřazení role a přidejte roli přispěvatele k uživateli, který nastavuje správce Microsoft Entra.
Pokud ještě nemáte Azure Key Vault, vytvořte ho. Uživatel, který nastavuje správce Microsoft Entra, by měl mít roli přispěvatele pro Azure Key Vault. Přidání role uživateli ve službě Azure Key Vault:
- Přejděte na web Azure Portal.
- Přejděte do prostředku trezoru klíčů.
- Vyberte Řízení přístupu (IAM).
- Vyberte Přidat>Přidat přiřazení role a přidejte roli přispěvatele k uživateli, který nastavuje správce Microsoft Entra.
Nastavení zásad přístupu pro hostitele SQL Serveru
Na webu Azure Portal přejděte do vaší instance služby Azure Key Vault a vyberte zásady přístupu.
Vyberte Přidat zásady přístupu.
Pro oprávnění ke klíčipoužijte Podepisování.
U tajných oprávněnívyberte Získat a Seznam.
Pro oprávnění k certifikátuvyberte Získat a Seznam.
Vyberte Další.
Na stránce Principal vyhledejte název instance Azure Arc, což je název hostitelského počítače SQL Serveru.
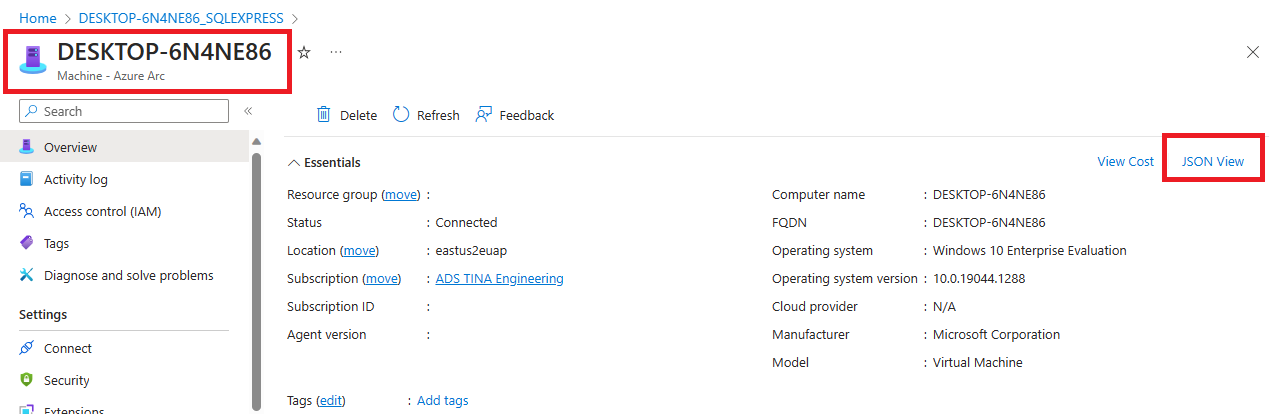
Stránku Aplikace (volitelné) přeskočte tak, že dvakrát zvolíte možnost Další nebo vyberete Zkontrolovat a vytvořit.
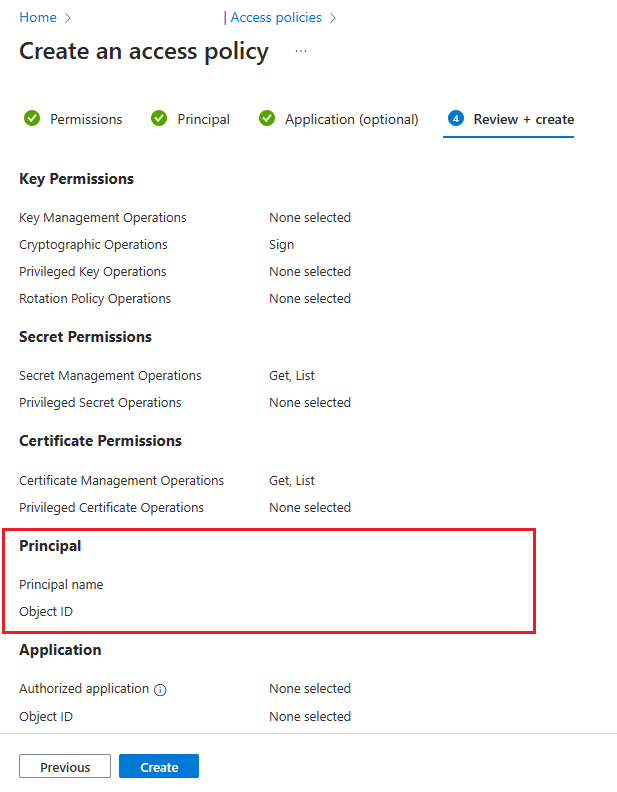
Ověřte, že "ID objektu" objektu zabezpečení odpovídá ID objektu zabezpečení spravované identity přiřazené k instanci.
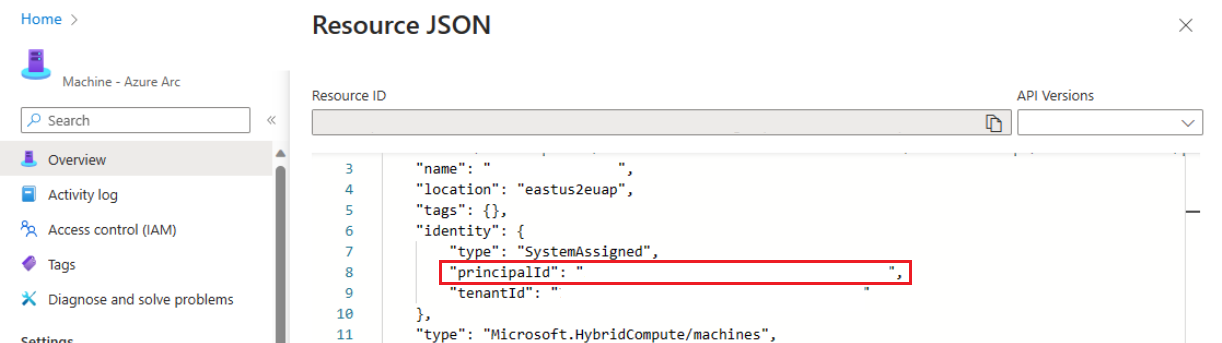
Přejděte na stránku zdroje a vyberte zobrazení JSON v pravém horním rohu sekce Základy na stránce Přehled, abyste to potvrdili. Pod částí identity najdete principalId.
Vyberte Vytvořit.
Abyste měli jistotu, že se oprávnění použijí, musíte vybrat Vytvořit. Pokud chcete zajistit, aby byla oprávnění uložená, aktualizujte okno prohlížeče a zkontrolujte, jestli je řádek vaší instance Azure Arc stále k dispozici.
Nastavení zásad přístupu pro uživatele Microsoft Entra
- Na webu Azure Portal přejděte do vaší instance služby Azure Key Vault a vyberte zásady přístupu.
- Vyberte Přidat zásady přístupu.
- Pro oprávnění ke klíčivyberte Získat, Vypsata Vytvořit.
- Pro tajná oprávněnívyberte Získat, Vypsata Nastavit.
- Pro oprávnění k certifikátuvyberte Získat, Vypsata Vytvořit.
- Pro vyberte hlavní objekt, přidáním uživatele Microsoft Entra, kterého chcete použít pro připojení k SQL Serveru.
- Vyberte Přidat a pak vyberte Uložit.
Nastavení správce Microsoft Entra pro SQL Server
Nová rozhraní API a funkce portálu umožňují uživatelům nastavit správce Microsoft Entra pro SQL Server, aniž by museli samostatně vytvářet certifikát Azure a aplikaci Microsoft Entra. Vyberte kartu, abyste se dozvěděli, jak nastavit správce Microsoft Entra pro váš SQL Server připojený k Azure Arc s automatickým vytvářením certifikátů a aplikací.
Pomocí webu Azure Portal můžete nastavit správce Microsoft Entra, vytvořit certifikát služby Azure Key Vault a aplikaci Microsoft Entra ve stejném procesu. To je nezbytné k použití ověřování Microsoft Entra s SQL Serverem.
Nastavení správce Microsoft Entra pomocí webu Azure Portal
Přejděte na portál Azurea vyberte SQL Server – Azure Arc. Vyberte instanci vašeho hostitele SQL Serveru.
Zkontrolujte stav svého prostředku SQL Server – Azure Arc a zjistěte, jestli je připojený, přechodem do nabídky Vlastnosti . Další informace najdete v tématu Ověření prostředků SQL Serveru s podporou arc.
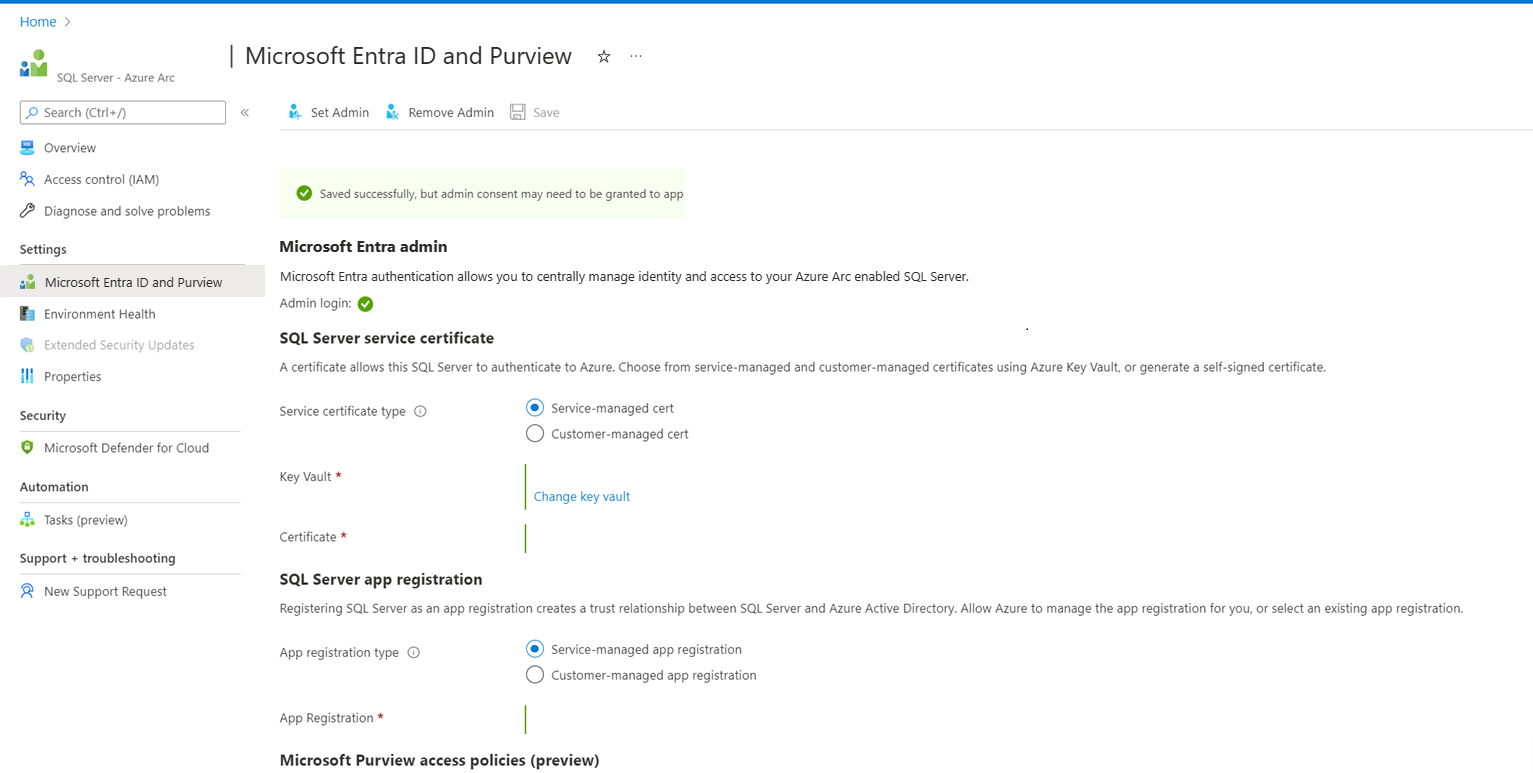
V nabídce prostředků vyberte Microsoft Entra ID a Purview v části Nastavení .
Výběrem možnosti Nastavit správce otevřete podokno Microsoft Entra ID a zvolte účet, který se přidá jako přihlášení správce k SQL Serveru.
Vyberte certifikát spravovaný službou.
Vyberte Změnit trezoru klíčů a vyberte existující prostředek služby Azure Key Vault.
Vyberte registrace aplikace spravované službou.
Zvolte Uložit. Tím se odešle požadavek na agenta serveru Arc, který nakonfiguruje ověřování Microsoft Entra pro danou instanci SQL Serveru. Dokončení operace může trvat několik minut; počkejte, dokud se proces uložení nepotvrdí s Saved successfully, než se pokusíte přihlásit k Microsoft Entra.
Registrace aplikace spravované službou za vás provede následující:
- Vytvoří v trezoru klíčů certifikát s názvem ve formátu
<hostname>-<instanceName><uniqueNumber>.
- Vytvoří aplikaci Microsoft Entra s názvem, jako je
<hostname>-<instanceName><uniqueNumber>, a přiřadí k této aplikaci potřebná oprávnění. Další informace najdete v tématu Oprávnění žádosti o grant
- Přiřadí k aplikaci nový certifikát ve službě Azure Key Vault.
- Uloží tato nastavení do služby Azure Arc.
Poznámka:
Certifikáty vytvořené pro Microsoft Entra se automaticky neotáčí. Zákazníci se můžou rozhodnout, že pro nastavení správce Microsoft Entra poskytnou vlastní certifikát a aplikaci. Další informace naleznete v tématu Kurz: Nastavení ověřování Microsoft Entra pro SQL Server.
Následující skript Azure CLI nastaví správce Microsoft Entra, vytvoří certifikát služby Azure Key Vault a vytvoří aplikaci Microsoft Entra. Existuje další část, která poskytuje ukázkový skript pro nastavení správce Microsoft Entra, pokud certifikát a aplikace již existují.
Poznámka:
Certifikáty vytvořené pro instalaci Microsoft Entra nejsou automaticky otočeny.
K instalaci modulu Az.ConnectedMachine použijte az extension add --name ConnectedMachine. Pokud chcete zkontrolovat, která verze Azure CLI je nainstalovaná, použijte az version.
Pro skript Azure CLI se používají následující vstupní parametry:
-
<applicationName> – název aplikace, který se vytvoří
-
<certSubjectName> – název certifikátu, který se vytvoří
-
<keyVaultName> – název vašeho trezoru klíčů Tento trezor klíčů musí být vytvořen před spuštěním skriptu.
-
<machineName> – název počítače hostitele SQL Serveru
-
<resourceGroupName> – název skupiny prostředků, která obsahuje vaši instanci SQL Serveru – Azure Arc
-
<adminAccountName> – účet správce Microsoft Entra, který chcete nastavit pro SQL Server
-
<instanceName> – Volitelný parametr pro pojmenované instance SQL Serveru. Tento parametr použijte, pokud máte pojmenovanou instanci. Pokud tento parametr vynecháte, použije se výchozí název MSSQLSERVER.
-
<tenantId> – volitelný parametr pro ID tenanta. ID tenanta najdete tak, že přejdete na webu Azure Portala přejdete na prostředek Microsoft Entra ID. V podokně Přehled byste měli vidět svůj ID tenanta. Pokud tento parametr vynecháte, použije se jako parametr výchozí ID tenanta.
-
<subscriptionId> – volitelný parametr pro ID předplatného. ID vašeho předplatného najdete na webu Azure Portal. Pokud tento parametr vynecháte, použije se výchozí ID předplatného.
Pokud chcete použít níže uvedený skript Azure CLI, uložte skript jako soubor .ps1 a spusťte následující příkaz:
./aadAzCliSetup.ps1 -applicationName "<applicationName>" -certSubjectName "<certSubjectName>" -keyVaultName "<keyVaultName>" -machineName "<machineName>" -resourceGroupName "<resourceGroupName>" -adminAccountName "<adminAccountName>" -instanceName "<instanceName>" -tenantId "<tenantId>" -subscriptionId "<subscriptionId>"
Azure CLI skript
Poznámka:
V případě SQL Serveru na hostitelských počítačích s Linuxem nahraďte WindowsAgent.SqlServerLinuxAgent.SqlServer ve skriptu.
# AZ CLI and AZ CLI's connected machine extension must be installed before running this script
param (
[Parameter(mandatory=$true)] $applicationName,
[Parameter(mandatory=$true)] $certSubjectName,
[Parameter(mandatory=$true)] $keyVaultName,
[Parameter(mandatory=$true)] $machineName,
[Parameter(mandatory=$true)] $resourceGroupName,
[Parameter(mandatory=$true)] $adminAccountName,
$instanceName,
$tenantId,
$subscriptionId
)
# Constants
#
$NUMRETRIES = 60
# Helper functions
#
function ConvertFrom-StringArray {
param (
[string[]] $stringArray
)
if (!$stringArray)
{
return $null
}
else
{
return ConvertFrom-JSON ($stringArray -join "`n")
}
}
# Check parameters
#
if ([string]::IsNullOrEmpty($instanceName))
{
Write-Host "Warning: SQL Instance name (-instanceName) not provided. Default of MSSQLSERVER will be used"
$instanceName = "MSSQLSERVER"
}
$tenantIdArgument = ""
if ([string]::IsNullOrEmpty($tenantId))
{
Write-Host "Warning: Tenant ID (-tenantId) not supplied to the script, so default tenant is being used"
}
else
{
$tenantIdArgument = "-TenantId '" + $tenantId + "'"
}
$subscriptionIdArgument = ""
if ([string]::IsNullOrEmpty($subscriptionId))
{
Write-Host "Warning: Subscription ID (-subscriptionId) not supplied to the script, so default subscription is being used"
}
else
{
$subscriptionIdArgument = "-SubscriptionId '" + $subscriptionId + "'"
}
# Login and select subscription
#
$login = az login --tenant $tenantId --use-device-code
if (!$login)
{
Write-Error "Login to Azure AD failed. Exiting."
exit 1
}
if ($subscriptionId)
{
az account set -s $subscriptionId
}
$accountInfo = ConvertFrom-StringArray (az account show)
if (!$accountInfo)
{
Write-Error "Cannot query logged in Azure AD account. Check that 'az login' and 'az account set' succeeded"
exit 1
}
if ($subscriptionId)
{
if ($subscriptionId.ToLower() -ne $accountInfo.id.ToLower())
{
Write-Error "Could not select the desired subscription"
exit 1
}
}
else
{
$subscriptionId = $accountInfo.id
}
# Check AKV path exists
#
$keyVault = ConvertFrom-StringArray (az keyvault show --name $keyVaultName)
if (!$keyVault)
{
Write-Error "Azure key vault '$keyVaultName' does not exist"
exit 1
}
# Check certificate doesn't exist
#
$cert = ConvertFrom-StringArray (az keyvault certificate show --name $certSubjectName --vault-name $keyVaultName 2>$null)
if ($cert)
{
Write-Error "Certificate '$certSubjectName' already exists in key vault '$keyVaultName'"
exit 1
}
# Check app registration doesn't exist
#
$applications = ConvertFrom-StringArray (az ad app list --display-name $applicationName --only-show-errors)
if ($applications.length -gt 0)
{
Write-Error "App registration with name '$applicationName' already exists"
exit 1
}
# Check Arc SQL instance is valid
#
$extension = ConvertFrom-StringArray (az connectedmachine extension show --machine-name $machineName --name "WindowsAgent.SqlServer" --resource-group $resourceGroupName)
if (!$extension)
{
Write-Error "SQL Server Arc Server not found for machine '$machineName' in resource group '$resourceGroupName'"
exit 1
}
$arcServicePrincipals = ConvertFrom-StringArray(az ad sp list --display-name $machineName --only-show-errors)
if (!$arcServicePrincipals -or $arcServicePrincipals.length -eq 0)
{
Write-Error "Could not find a service principal account with the name '$machineName'"
exit 1
}
else
{
$principalFound = $false
for ($i = 0; $i -lt $arcServicePrincipals.length; $i++)
{
if ($arcServicePrincipals[$i].displayName.toLower() -eq $machineName.toLower()) {
if ($principalFound) {
Write-Error "Could not find exactly one service principal account with the name '$machineName'"
exit 1
}
$arcServicePrincipal = $arcServicePrincipals[$i]
$principalFound = $true
}
}
if (!$principalFound) {
Write-Error "Could not find a service principal account with the name '$machineName'"
exit 1
}
}
# Check if admin account exists
#
$adminAccount = ConvertFrom-StringArray (az ad user show --id $adminAccountName --only-show-errors 2>$null)
$adminAccountType = 0
if (!$adminAccount)
{
$adminAccounts = ConvertFrom-StringArray (az ad user list --filter "mail eq '$adminAccountName'" --only-show-errors 2>$null)
if ($adminAccounts -and $adminAccounts.length -gt 0)
{
if ($adminAccounts.length -eq 1)
{
$adminAccount = $adminAccounts[0]
}
else
{
Write-Error "Multiple Azure AD accounts found with identifier '$adminAccountName'"
exit 1
}
}
else
{
$adminAccount = ConvertFrom-StringArray (az ad group show --group $adminAccountName --only-show-errors 2>$null)
if (!$adminAccount)
{
$adminAccounts = ConvertFrom-StringArray (az ad app list --display-name $adminAccountName --only-show-errors 2>$null)
if ($adminAccounts -and $adminAccounts.length -gt 0)
{
if ($adminAccounts.length -eq 1)
{
$adminAccount = $adminAccounts[0]
}
else
{
Write-Error "Multiple Azure AD applications found with identifier '$adminAccountName'"
exit 1
}
}
else
{
Write-Error "Admin account not found"
exit 1
}
}
else
{
$adminAccountType = 1
}
}
}
if ($adminAccount)
{
$adminAccountSid = $adminAccount.id
}
else
{
Write-Error "Admin account not found"
exit 1
}
# Create certificate in AKV
#
$keyVaultPolicy = ConvertFrom-StringArray (az keyvault certificate get-default-policy)
if (!$keyVaultPolicy)
{
Write-Error "Could not get default key vault policy"
exit 1
}
$keyVaultPolicy.x509CertificateProperties.subject = "CN=" + $certSubjectName
$policyString = (ConvertTo-JSON -Depth 8 $keyVaultPolicy).replace("`r`n", "")
$escapedPolicyString = $policyString.replace("`"", "\`"")
$cert = ConvertFrom-StringArray (az keyvault certificate create --vault-name $keyVaultName --name $certSubjectName --policy $escapedPolicyString)
if (!$cert)
{
Write-Error "Failed to create certificate '$certSubjectName'"
exit 1
}
# Wait until cert is created?
#
$cert = ConvertFrom-StringArray (az keyvault certificate show --vault-name $keyVaultName --name $certSubjectName)
for (($i = 0); $i -lt $NUMRETRIES -and (!$cert -or !$cert.attributes.enabled); $i++)
{
$cert = ConvertFrom-StringArray (az keyvault certificate show --vault-name $keyVaultName --name $certSubjectName)
if (!$cert -or !$cert.attributes.enabled)
{
Start-Sleep -Seconds 5
}
}
# Allow Arc to access AKV
#
$newPerms = ConvertFrom-StringArray (az keyvault set-policy --name $keyVaultName --secret-permissions get list --certificate-permissions get list --object-id $arcServicePrincipal.id)
if (!$newPerms)
{
Write-Host "Warning: Unable to add permissions to key vault '$keyVaultName' for Arc's service principal's identity '$($arcServicePrincipal.id)'. Arc may not be able to configure Azure AD authentication"
}
# Create an Azure AD application
#
$application = ConvertFrom-StringArray (az ad app create --display-name $applicationName --only-show-errors)
if (!$application)
{
Write-Error "Unable to create the app registration '$applicationName'"
exit 1
}
# Set perms on app registration
#
az ad app permission add --id $application.id --api 00000003-0000-0000-c000-000000000000 --api-permissions c79f8feb-a9db-4090-85f9-90d820caa0eb=Scope --only-show-errors # Delegated Application.Read.All
az ad app permission add --id $application.id --api 00000003-0000-0000-c000-000000000000 --api-permissions 0e263e50-5827-48a4-b97c-d940288653c7=Scope --only-show-errors # Delegated Directory.AccessAsUser.All
az ad app permission add --id $application.id --api 00000003-0000-0000-c000-000000000000 --api-permissions 7ab1d382-f21e-4acd-a863-ba3e13f7da61=Role --only-show-errors # Application Directory.Read.All
az ad app permission add --id $application.id --api 00000003-0000-0000-c000-000000000000 --api-permissions 5f8c59db-677d-491f-a6b8-5f174b11ec1d=Scope --only-show-errors # Delegated Group.Read.All
az ad app permission add --id $application.id --api 00000003-0000-0000-c000-000000000000 --api-permissions a154be20-db9c-4678-8ab7-66f6cc099a59=Scope --only-show-errors # Delegated User.Read.All
# Upload cert to Azure AD
#
$certUploadRes = ConvertFrom-StringArray (az ad app credential reset --id $application.id --cert $certSubjectName --keyvault $keyVaultName --append --only-show-errors)
if (!$certUploadRes)
{
Write-Error "Failed to set certificate '$certSubjectName' as a credential for app registration '$applicationName'"
exit 1
}
# Remove the version from the secret ID if present
#
$secretId = $cert.sid
if ($secretId -Match "(https:\/\/[^\/]+\/secrets\/[^\/]+)(\/.*){0,1}$") {
if ($Matches[1]) {
$secretId = $Matches[1]
}
}
# Create the settings object to write to the Azure extension for SQL Server
#
$instanceSettings = @{
instanceName = $instanceName
adminLoginName = $adminAccountName
adminLoginSid = $adminAccountSid
azureCertSecretId = $secretId
azureCertUri = $cert.id
azureKeyVaultResourceUID = $keyVault.id
managedCertSetting = "CUSTOMER MANAGED CERT"
managedAppSetting = "CUSTOMER MANAGED APP"
appRegistrationName = $application.displayName
appRegistrationSid = $application.appId
tenantId = $tenantId
aadCertSubjectName = $certSubjectName
adminLoginType = $adminAccountType
}
$extension = ConvertFrom-StringArray (az connectedmachine extension show --machine-name $machineName --name "WindowsAgent.SqlServer" --resource-group $resourceGroupName)
if ($extension.properties.Settings.AzureAD)
{
$aadSettings = $extension.properties.Settings.AzureAD
$instanceFound = $false
$instanceNameLower = $instanceName.ToLower()
$instanceIndex = 0
for (($i = 0); $i -lt $aadSettings.Length; $i++)
{
if ($aadSettings[$i].instanceName.ToLower() -eq $instanceNameLower)
{
$instanceIndex = $i
$instanceFound = $true
break
}
}
if ($instanceFound)
{
$aadSettings[$instanceIndex] = $instanceSettings
}
else
{
$aadSettings += $instanceSettings
}
$extension.properties.Settings.AzureAD = $aadSettings
}
else
{
$aadSettings = , $instanceSettings
$extension.properties.Settings | Add-Member -Name 'AzureAD' -Value $aadSettings -MemberType NoteProperty
}
$settingsString = (ConvertTo-Json $extension.properties.Settings).replace("`"", "\`"").replace("`r`n", "")
# Push settings to Arc
#
Write-Host "Writing Azure AD setting to Azure extension for SQL Server. This may take several minutes..."
$updateRes = az connectedmachine extension update --machine-name $machineName --name "WindowsAgent.SqlServer" --resource-group $resourceGroupName --settings $settingsString
if (!$updateRes)
{
Write-Error "Failed to update Azure extension for SQL Server with Azure AD settings"
exit 1
}
Write-Output "Success"
Spuštění skriptu může trvat několik minut. Po dokončení procesu se zobrazí zpráva podobná této:
Name Location ProvisioningState
---- -------- -----------------
WindowsAgent.SqlServer westus2 Succeeded
Success
Nastavení správce Microsoft Entra s existujícím certifikátem a aplikací pomocí Azure CLI
Pokud už máte existující certifikát služby Azure Key Vault a aplikaci Azure, kterou chcete použít k nastavení správce Microsoft Entra, můžete použít následující skript rozhraní příkazového řádku:
# Set up Microsoft Entra admin for user's existing key vault, certificate, and application
# Requires input parameters indicated below
# Connect statement
AZ Login
#Input parameters
$subscriptionId="<subscriptionId>"
$tenantId="<tenantId>"
$machineName="<machineName>" # hostname
$instanceName="<instanceName>" # SQL Server is define as `machine_name\instance_name`
$resourceGroupName="<resourceGroupName>"
$keyVaultName="<keyVaultName>"
$certSubjectName="<certSubjectName>" # Your existing certificate name
$applicationName="<applicationName>" # Your existing application name
$adminAccountName="<adminAccountName>"
$adminAccountSid="<adminID>" # Use object ID for the Azure AD user and group, or client ID for the Azure AD application
$adminAccountType= 0 # 0 – for Azure AD user and application, 1 for Azure AD group
# Helper function
#
function ConvertFrom-StringArray {
param (
[string[]] $stringArray
)
if (!$stringArray)
{
return $null
}
else
{
return ConvertFrom-JSON ($stringArray -join "`n")
}
}
$keyVault = ConvertFrom-StringArray (az keyvault show --name $keyVaultName)
if (!$keyVault)
{
Write-Error "Azure key vault '$keyVaultName' does not exist"
exit 1
}
$cert = ConvertFrom-StringArray (az keyvault certificate show --name $certSubjectName --vault-name $keyVaultName 2>$null)
if (!$cert)
{
Write-Error "Supplied certificate $certSubjectName was not found for this key vault. Please specify an existing certificate"
exit 1
}
$secretId = $cert.sid
if ($secretId -Match "(https:\/\/[^\/]+\/secrets\/[^\/]+)(\/.*){0,1}$") {
if ($Matches[1]) {
$secretId = $Matches[1]
}
}
$application = ConvertFrom-StringArray (az ad app list --display-name $applicationName --only-show-errors)
if (!$application)
{
Write-Error "Supplied application was not found in the subscription. Please specify an existing application"
exit 1
}
# Create the settings object to write to the Arc extension
#
$instanceSettings = @{
instanceName = $instanceName
adminLoginName = $adminAccountName
adminLoginSid = $adminAccountSid
azureCertSecretId = $secretId
azureCertUri = $cert.id
azureKeyVaultResourceUID = $keyVault.id
managedCertSetting = "CUSTOMER MANAGED CERT"
managedAppSetting = "CUSTOMER MANAGED APP"
appRegistrationName = $application.displayName
appRegistrationSid = $application.appId
tenantId = $tenantId
aadCertSubjectName = $certSubjectName
adminLoginType = $adminAccountType
}
$extension = ConvertFrom-StringArray (az connectedmachine extension show --machine-name $machineName --name "WindowsAgent.SqlServer" --resource-group $resourceGroupName)
if ($extension.properties.Settings.AzureAD)
{
$aadSettings = $extension.properties.Settings.AzureAD
$instanceFound = $false
$instanceNameLower = $instanceName.ToLower()
$instanceIndex = 0
for (($i = 0); $i -lt $aadSettings.Length; $i++)
{
if ($aadSettings[$i].instanceName.ToLower() -eq $instanceNameLower)
{
$instanceIndex = $i
$instanceFound = $true
break
}
}
if ($instanceFound)
{
$aadSettings[$instanceIndex] = $instanceSettings
}
else
{
$aadSettings += $instanceSettings
}
$extension.properties.Settings.AzureAD = $aadSettings
}
else
{
$aadSettings = , $instanceSettings
$extension.properties.Settings | Add-Member -Name 'AzureAD' -Value $aadSettings -MemberType NoteProperty
}
$settingsString = (ConvertTo-Json $extension.properties.Settings).replace("`"", "\`"").replace("`r`n", "")
# Push settings to Arc
#
Write-Host "Writing Azure AD setting to SQL Server Arc Extension. This may take several minutes..."
$updateRes = az connectedmachine extension update --machine-name $machineName --name "WindowsAgent.SqlServer" --resource-group $resourceGroupName --settings $settingsString
if (!$updateRes)
{
Write-Error "Failed to update SQL Arc Extension with Azure AD settings"
exit 1
}
Write-Output "Success"
Následující skript PowerShellu nastaví správce Microsoft Entra, vytvoří certifikát služby Azure Key Vault a vytvoří aplikaci Microsoft Entra. Existuje další část, která poskytuje ukázkový skript pro nastavení správce Microsoft Entra, pokud certifikát a aplikace již existují.
Poznámka:
Certifikáty vytvořené pro instalaci Microsoft Entra nejsou automaticky otočeny.
Pro účely tohoto kurzu jsou vyžadovány následující moduly. Nainstalujte nejnovější verze modulů nebo novějších než uvedená verze níže:
- Az.Accounts 3.37.0
- Az.ConnectedMachine 0.5.0
- Az.KeyVault 4.5.0
- Az.Resources 6.0.0
Pro skript PowerShellu se používají následující vstupní parametry:
-
<applicationName> – název aplikace, který se vytvoří
-
<certSubjectName> – název certifikátu, který se vytvoří
-
<keyVaultName> – název vašeho trezoru klíčů Tento trezor klíčů musí být vytvořen před spuštěním skriptu.
-
<machineName> – název počítače hostitele SQL Serveru
-
<resourceGroupName> – název skupiny prostředků, která obsahuje vaši instanci SQL Serveru – Azure Arc
-
<adminAccountName> – účet správce Microsoft Entra, který chcete nastavit pro SQL Server
-
<instanceName> – Volitelný parametr pro pojmenované instance SQL Serveru. Tento parametr použijte, pokud máte pojmenovanou instanci. Pokud tento parametr vynecháte, použije se výchozí název MSSQLSERVER.
-
<tenantId> – volitelný parametr pro ID tenanta. ID tenanta najdete tak, že přejdete na webu Azure Portala přejdete na prostředek Microsoft Entra ID. V podokně Přehled byste měli vidět svůj ID tenanta. Pokud tento parametr vynecháte, použije se jako parametr výchozí ID tenanta.
-
<subscriptionId> – volitelný parametr pro ID předplatného. ID vašeho předplatného najdete na webu Azure Portal. Pokud tento parametr vynecháte, použije se výchozí ID předplatného.
Pokud chcete použít níže uvedený skript PowerShellu, uložte ho jako soubor .ps1 a spusťte následující příkaz:
./aadPowerShellsetup.ps1 -applicationName "<applicationName>" -certSubjectName "<certSubjectName>" -keyVaultName "<keyVaultName>" -machineName "<machineName>" -resourceGroupName "<resourceGroupName>" -adminAccountName "<adminAccountName>" -instanceName "<instanceName>" -tenantId "<tenantId>" -subscriptionId "<subscriptionId>"
Skript pro PowerShell
V případě SQL Serveru na hostitelských počítačích s Linuxem nahraďte WindowsAgent.SqlServerLinuxAgent.SqlServer ve skriptu.
param (
[Parameter(mandatory=$true)] $applicationName,
[Parameter(mandatory=$true)] $certSubjectName,
[Parameter(mandatory=$true)] $keyVaultName,
[Parameter(mandatory=$true)] $machineName,
[Parameter(mandatory=$true)] $resourceGroupName,
[Parameter(mandatory=$true)] $adminAccountName,
$instanceName,
$tenantId,
$subscriptionId
)
Import-Module Az.Accounts
Import-Module Az.ConnectedMachine
Import-Module Az.KeyVault
Import-Module Az.Resources
# Constants
#
$NUMRETRIES = 60
# Check parameters
#
if ([string]::IsNullOrEmpty($instanceName))
{
Write-Host "Warning: SQL Instance name (-instanceName) not provided. Default of MSSQLSERVER will be used"
$instanceName = "MSSQLSERVER"
}
$tenantIdArgument = ""
if ([string]::IsNullOrEmpty($tenantId))
{
Write-Host "Warning: Tenant ID (-tenantId) not supplied to the script, so default tenant is being used"
}
else
{
$tenantIdArgument = "-TenantId '" + $tenantId + "'"
}
$subscriptionIdArgument = ""
if ([string]::IsNullOrEmpty($subscriptionId))
{
Write-Host "Warning: Subscription ID (-subscriptionId) not supplied to the script, so default subscription is being used"
}
else
{
$subscriptionIdArgument = "-SubscriptionId '" + $subscriptionId + "'"
}
# Login
#
try
{
$loginRes = Invoke-Expression -Command ("Connect-AzAccount " + $tenantIdArgument + " " + $subscriptionIdArgument + " -ErrorAction stop -UseDeviceAuthentication")
}
catch
{
Write-Error $_
Write-Error "Failed to login to Azure. Script can not continue"
exit 1
}
# Get subscription ID
#
if ([string]::IsNullOrEmpty($subscriptionId))
{
$context = Get-AzContext
if ($context)
{
if ($context.Name -Match "[^(]+\(([^)]{36})\)")
{
if ($Matches[1])
{
$subscriptionId = $Matches[1]
}
}
}
}
if ([string]::IsNullOrEmpty($subscriptionId))
{
Write-Error "Failed to find default subscription"
exit 1
}
# Check AKV path exists
#
$keyVault = Get-AzKeyVault -VaultName $keyVaultName
if (!$keyVault)
{
Write-Error "Supplied key vault was not found in the subscription. Please specify an existing key vault"
exit 1
}
# Check certificate doesn't exist
#
$cert = Get-AzKeyVaultCertificate -VaultName $keyVaultName -Name $certSubjectName
if ($cert)
{
Write-Error "Certificate $certSubjectName already exists"
exit 1
}
# Check app registration doesn't exist
#
$application = Get-AzADApplication -DisplayName $applicationName
if ($application)
{
Write-Error "Application $applicationName already exists"
exit 1
}
# Check Arc SQL instance is valid
#
$arcInstance = Get-AzConnectedMachineExtension -SubscriptionId $subscriptionId -MachineName $machineName -ResourceGroupName $resourceGroupName -Name "WindowsAgent.SqlServer"
if (!$arcInstance)
{
Write-Error "Could not find a SQL Server Arc instance in subscription '$subscriptionId' and resource group '$resourceGroupName' with name '$machineName'"
exit 1
}
# Check if admin account exists
#
$adminAccount = Get-AzADUser -UserPrincipalName $adminAccountName
$adminAccountType = 0
if (!$adminAccount)
{
# Check for guest user
#
$adminAccount = Get-AzADUser -Mail $adminAccountName
if (!$adminAccount)
{
$adminAccount = Get-AzADGroup -DisplayName $adminAccountName
if (!$adminAccount)
{
$adminAccount = Get-AzADServicePrincipal -DisplayName $adminAccountName
}
else
{
$adminAccountType = 1
}
}
}
if ($adminAccount)
{
if ($adminAccount.Length -gt 1)
{
Write-Error "Multiple accounts with found with name $adminAccountName"
exit 1
}
$adminAccountSid = $adminAccount.Id
}
else
{
Write-Error "Could not find an account with name $adminAccountName"
exit 1
}
# Create certificate in AKV
#
$Policy = New-AzKeyVaultCertificatePolicy -SecretContentType "application/x-pkcs12" -SubjectName "CN=$certSubjectName" -IssuerName "Self" -ValidityInMonths 12 -ReuseKeyOnRenewal
try
{
$addCertRes = Add-AzKeyVaultCertificate -VaultName $keyVaultName -Name $certSubjectName -CertificatePolicy $Policy -ErrorAction stop
}
catch
{
Write-Error $_
Write-Error "Certificate $certSubjectName could not be created"
exit 1
}
for (($i = 0); $i -lt $NUMRETRIES -and (!$cert -or !$cert.enabled); $i++)
{
$cert = Get-AzKeyVaultCertificate -VaultName $keyVaultName -Name $certSubjectName
if (!$cert -or !$cert.enabled)
{
Start-Sleep -Seconds 5
}
}
if (!$cert)
{
Write-Error "Certificate $certSubjectName could not be created"
exit 1
}
# Allow Arc to access AKV
#
$arcServicePrincipal = Get-AzADServicePrincipal -DisplayName $machineName
if ($arcServicePrincipal -and ![string]::IsNullOrEmpty($arcServicePrincipal.Id))
{
try
{
Set-AzKeyVaultAccessPolicy -VaultName $keyVaultName -ObjectId $arcServicePrincipal.Id -PermissionsToSecrets Get,List -PermissionsToCertificates Get,List
}
catch
{
Write-Error $_
Write-Host "Warning: Could not find the identity of the Azure extension for SQL Server and thus, could not add permissions for the Arc process to read from AKV. Ensure the Arc identity has the required permissions to read from AKV."
}
}
else
{
Write-Host "Warning: Could not find the identity of the Azure extension for SQL Server and thus, could not add permissions for the Arc process to read from AKV. Ensure the Arc identity has the required permissions to read from AKV."
}
# Create an Azure AD application
#
$application = New-AzADApplication -DisplayName $applicationName
if (!$application)
{
Write-Error "Application could not be created"
exit 1
}
# Set perms on app registration
#
Add-AzADAppPermission -ObjectId $application.Id -ApiId 00000003-0000-0000-c000-000000000000 -PermissionId c79f8feb-a9db-4090-85f9-90d820caa0eb # Delegated Application.Read.All
Add-AzADAppPermission -ObjectId $application.Id -ApiId 00000003-0000-0000-c000-000000000000 -PermissionId 0e263e50-5827-48a4-b97c-d940288653c7 # Delegated Directory.AccessAsUser.All
Add-AzADAppPermission -ObjectId $application.Id -ApiId 00000003-0000-0000-c000-000000000000 -PermissionId 7ab1d382-f21e-4acd-a863-ba3e13f7da61 -Type Role # Application Directory.Read.All
Add-AzADAppPermission -ObjectId $application.Id -ApiId 00000003-0000-0000-c000-000000000000 -PermissionId 5f8c59db-677d-491f-a6b8-5f174b11ec1d # Delegated Group.Read.All
Add-AzADAppPermission -ObjectId $application.Id -ApiId 00000003-0000-0000-c000-000000000000 -PermissionId a154be20-db9c-4678-8ab7-66f6cc099a59 # Delegated User.Read.All
# Upload cert to Azure AD
#
try
{
$base64Cert = [System.Convert]::ToBase64String($cert.Certificate.GetRawCertData())
New-AzADAppCredential -ApplicationObject $application -CertValue $base64Cert -EndDate $cert.Certificate.NotAfter -StartDate $cert.Certificate.NotBefore -ErrorAction stop
}
catch
{
Write-Error $_
Write-Error "Failed to add certificate to app registration"
exit 1
}
# Remove the version from the secret ID if present
#
$secretId = $cert.SecretId
if ($secretId -Match "(https:\/\/[^\/]+\/secrets\/[^\/]+)(\/.*){0,1}$") {
if ($Matches[1]) {
$secretId = $Matches[1]
}
}
# Create the settings object to write to the Azure extension for SQL Server
#
$instanceSettings = @{
instanceName = $instanceName
adminLoginName = $adminAccountName
adminLoginSid = $adminAccountSid
azureCertSecretId = $secretId.replace(":443", "")
azureCertUri = $cert.Id.replace(":443", "")
azureKeyVaultResourceUID = $keyVault.ResourceId
managedCertSetting = "CUSTOMER MANAGED CERT"
managedAppSetting = "CUSTOMER MANAGED APP"
appRegistrationName = $application.DisplayName
appRegistrationSid = $application.AppId
tenantId = $tenantId
aadCertSubjectName = $certSubjectName
adminLoginType = $adminAccountType
}
$arcInstance = Get-AzConnectedMachineExtension -SubscriptionId $subscriptionId -MachineName $machineName -ResourceGroupName $resourceGroupName -Name "WindowsAgent.SqlServer"
if ($arcInstance.Setting.AdditionalProperties.AzureAD)
{
$aadSettings = $arcInstance.Setting.AdditionalProperties.AzureAD
$instanceFound = $false
$instanceNameLower = $instanceName.ToLower()
$instanceIndex = 0
for (($i = 0); $i -lt $aadSettings.Length; $i++)
{
if ($aadSettings[$i].instanceName.ToLower() -eq $instanceNameLower)
{
$instanceIndex = $i
$instanceFound = $true
break
}
}
if ($instanceFound)
{
$aadSettings[$instanceIndex] = $instanceSettings
}
else
{
$aadSettings += $instanceSettings
}
}
else
{
$aadSettings = , $instanceSettings
}
Write-Host "Writing Microsoft Entra setting to SQL Server Arc Extension. This may take several minutes..."
# Push settings to Arc
#
try
{
#set the Entra ID / AzureAD setting in the hash table
$SettingsToConfigure = @{
AzureAD = $aadSettings
}
#add any non-AzureAD key value pairs back to the hashtable
$keys = $arcInstance.Setting.Keys | where-object {$_ -notin ("AzureAD")}
foreach ($key in $keys) {
$SettingsToConfigure.$key = $arcInstance.Setting["$key"]
}
#Issue the update of the updated settings
Update-AzConnectedMachineExtension `
-MachineName $machineName `
-Name "WindowsAgent.SqlServer" `
-ResourceGroupName $resourceGroupName `
-Setting $SettingsToConfigure
}
catch
{
Write-Error $_
Write-Error "Failed to write settings to Arc host"
exit 1
}
Write-Output "Success"
Nastavení správce Microsoft Entra s existujícím certifikátem a aplikací pomocí PowerShellu
Pokud už máte existující certifikát služby Azure Key Vault a aplikaci Azure, kterou chcete použít k nastavení správce Microsoft Entra, můžete použít následující skript PowerShellu:
# Connect statement
Connect-AzAccount
#Input parameters
$subscriptionId="<subscriptionId>"
$tenantId="<tenantId>"
$machineName="<machineName>" # hostname
$instanceName="<instanceName>" # SQL Server is define as `machine_name\instance_name`
$resourceGroupName="<resourceGroupName>"
$keyVaultName="<keyVaultName>"
$certSubjectName="<certSubjectName>" # Your existing certificate name
$applicationName="<applicationName>" # Your existing application name
$adminAccountName="<adminAccountName>"
$adminAccountSid="<adminID>" # Use object ID for the Microsoft Entra user and group, or client ID for the Microsoft Entra application
$adminAccountType= 0 # 0 – for Microsoft Entra user and application, 1 for Microsoft Entra group
$keyVault = Get-AzKeyVault -VaultName $keyVaultName
if (!$keyVault)
{
Write-Error "Supplied key vault was not found in the subscription. Please specify an existing key vault"
exit 1
}
$cert = Get-AzKeyVaultCertificate -VaultName $keyVaultName -Name $certSubjectName
if (!$cert)
{
Write-Error "Supplied certificate $certSubjectName was not found for this key vault. Please specify an existing certificate"
exit 1
}
$secretId = $cert.SecretId
if ($secretId -Match "(https:\/\/[^\/]+\/secrets\/[^\/]+)(\/.*){0,1}$") {
if ($Matches[1]) {
$secretId = $Matches[1]
}
}
$application = Get-AzADApplication -DisplayName $applicationName
if (!$application)
{
Write-Error "Supplied application was not found in the subscription. Please specify an existing application"
exit 1
}
# Create the settings object to write to the Arc extension
#
$instanceSettings = @{
instanceName = $instanceName
adminLoginName = $adminAccountName
adminLoginSid = $adminAccountSid
azureCertSecretId = $secretId.replace(":443", "")
azureCertUri = $cert.Id.replace(":443", "")
azureKeyVaultResourceUID = $keyVault.ResourceId
managedCertSetting = "CUSTOMER MANAGED CERT"
managedAppSetting = "CUSTOMER MANAGED APP"
appRegistrationName = $application.DisplayName
appRegistrationSid = $application.AppId
tenantId = $tenantId
aadCertSubjectName = $certSubjectName
adminLoginType = $adminAccountType
}
$arcInstance = Get-AzConnectedMachineExtension -SubscriptionId $subscriptionId -MachineName $machineName -ResourceGroupName $resourceGroupName -Name "WindowsAgent.SqlServer"
if ($arcInstance.Setting.AdditionalProperties.AzureAD)
{
$aadSettings = $arcInstance.Setting.AdditionalProperties.AzureAD
$instanceFound = $false
$instanceNameLower = $instanceName.ToLower()
$instanceIndex = 0
for (($i = 0); $i -lt $aadSettings.Length; $i++)
{
if ($aadSettings[$i].instanceName.ToLower() -eq $instanceNameLower)
{
$instanceIndex = $i
$instanceFound = $true
break
}
}
if ($instanceFound)
{
$aadSettings[$instanceIndex] = $instanceSettings
}
else
{
$aadSettings += $instanceSettings
}
}
else
{
$aadSettings = , $instanceSettings
}
Write-Host "Writing Microsoft Entra setting to SQL Server Arc Extension. This may take several minutes..."
# Push settings to Arc
#
try
{
#set the Entra ID / AzureAD setting in the hash table
$SettingsToConfigure = @{
AzureAD = $aadSettings
}
#add any non-AzureAD key value pairs back to the hashtable
$keys = $arcInstance.Setting.Keys | where-object {$_ -notin ("AzureAD")}
foreach ($key in $keys) {
$SettingsToConfigure.$key = $arcInstance.Setting["$key"]
}
#Issue the update of the updated settings
Update-AzConnectedMachineExtension `
-MachineName $machineName `
-Name "WindowsAgent.SqlServer" `
-ResourceGroupName $resourceGroupName `
-Setting $SettingsToConfigure
}
catch
{
Write-Error $_
Write-Error "Failed to write settings to Arc host"
exit 1
}
Write-Output "Success"
Následující šablona ARM nastaví správce Microsoft Entra pomocí existujícího certifikátu služby Azure Key Vault a aplikace Microsoft Entra.
Pro šablonu ARM se používají následující vstupní parametry:
-
<machineName> – název počítače hostitele SQL Serveru
-
<Location> – umístění SQL Serveru – skupina prostředků azure Arc, například West USnebo Central US
-
<tenantId> – ID tenanta najdete tak, že přejdete na Azure Portal, a přejděte k prostředku Microsoft Entra ID.
V podokně Přehled by se mělo zobrazit ID tenanta.
-
<instanceName> – název instance SQL Serveru. Výchozí název instance SYSTÉMU SQL Server je MSSQLSERVER
-
<certSubjectName> – název certifikátu, který jste vytvořili
-
<subscriptionId> – ID předplatného. ID vašeho předplatného najdete na webu Azure Portal.
-
<resourceGroupName> – název skupiny prostředků, která obsahuje váš trezor klíčů. Úplnou hodnotu azureKeyVaultResourceUID najdete tak, že přejdete do Key Vault, vyberete Vlastnosti a zkopírujete Resource ID
-
<keyVaultName> – název vašeho trezoru klíčů
-
<certIdentifier> – identifikátor certifikátu pro certifikát služby Azure Key Vault. Pokud chcete získat identifikátor certifikátu , přejděte k prostředku trezoru klíčů a v části Nastavení vyberte certifikáty . Vyberte aktuální verzi certifikátu , který jste vytvořili, a zkopírujte hodnotu identifikátoru certifikátu . Další informace najdete v tématu Přidání certifikátu do služby Key Vault
-
<certSecret> – identifikátor tajného klíče vašeho certifikátu a najdete ho ve stejné nabídce jako identifikátor certifikátu
-
<applicationName> – název vaší vytvořené aplikace Microsoft Entra
-
<appID> – ID aplikace (klient) vaší aplikace Microsoft Entra najdete v nabídce Přehled aplikace.
-
<adminAccountName> – účet správce Microsoft Entra, který chcete nastavit pro SQL Server
-
<adminID> – ID objektu uživatele nebo skupiny Microsoft Entra nebo ID aplikace (klient) aplikace, pokud používáte jinou aplikaci jako účet správce Microsoft Entra. Další informace najdete v tématu Kurz: Vytvoření uživatelů Microsoft Entra pomocí aplikací Microsoft Entra
-
<adminType> – použití 0 pro uživatele a aplikace Microsoft Entra a 1 pro skupiny Microsoft Entra
Použijte vlastní nasazení v Azure portálu a vytvořte vlastní šablonu v editoru. Nakonec uložte konfiguraci, jakmile vložíte příklad.
Poznámka:
V případě SQL Serveru na hostitelských počítačích s Linuxem nahraďte WindowsAgent.SqlServerLinuxAgent.SqlServer ve skriptu.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {},
"resources": [
{
"type": "Microsoft.HybridCompute/machines/extensions",
"apiVersion": "2022-03-10",
"name": "<machineName>/WindowsAgent.SqlServer",
"location": "<Location>",
"properties": {
"publisher": "Microsoft.AzureData",
"type": "WindowsAgent.SqlServer",
"settings": {
"AzureAD": [
{
"tenantId": "<tenantId>",
"instanceName": "<instanceName>",
"managedCertSetting": "CUSTOMER MANAGED CERT",
"aadCertSubjectName": "<certSubjectName>",
"azureKeyVaultResourceUID": "/subscriptions/<subscriptionId>/resourceGroups/<resourceGroupName>/providers/Microsoft.KeyVault/vaults/<keyVaultName>",
"azureCertUri": "<certIdentifier>",
"azureCertSecretId": "<certSecret>",
"managedAppSetting": "CUSTOMER MANAGED APP",
"appRegistrationName": "<applicationName>",
"appRegistrationSid": "<appID>",
"adminLoginName": "<adminAccountName>",
"adminLoginSid" : "<adminID>",
"adminLoginType": 0
}
]
}
}
}
]
}
Udělení souhlasu správce pro aplikaci
Jakmile je správce Microsoft Entra nastavený, můžete se pomocí přihlašovacích údajů správce Microsoft Entra připojit k SQL Serveru. Jakékoli další databázové aktivity zahrnující vytváření nových přihlášení Microsoft Entra a uživatelů se však nezdaří, dokud nebude souhlas správce udělen aplikaci Microsoft Entra.
Poznámka:
K udělení souhlasu správce pro aplikaci je potřeba, aby účet, který uděluje souhlas, měl roli správce privilegovaných rolí Microsoft Entra ID. Tyto role jsou nezbytné k udělení souhlasu správce pro aplikaci, ale není nutné nastavit správce Microsoft Entra.
Na webu Azure Portalvyberte ID Microsoft Entra>registrace aplikacía vyberte nově vytvořenou aplikaci. Aplikace by měla mít název, například <hostname>-<instanceName><uniqueNumber>.
Vyberte nabídku oprávnění rozhraní API .
Vyberte Udělit souhlas správce.

Bez udělení souhlasu správce s aplikací způsobí vytvoření přihlášení Microsoft Entra nebo uživatele na SQL Serveru následující chybu:
Msg 37455, Level 16, State 1, Line 2
Server identity does not have permissions to access MS Graph.
Použití ověřování Microsoft Entra pro připojení k SQL Serveru
Ověřování Microsoft Entra je teď nastavené pro SQL Server, který je připojený ke službě Azure Arc. Postupujte podle částí po nastavení správce Microsoft Entra v článku, Kurz: Nastavení ověřování Microsoft Entra pro SQL Server pro připojení k SQL Serveru pomocí ověřování Microsoft Entra.
Viz také
SQL Server 2022 (16.x)




