Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In the Teams admin center, we provide a few dedicated pages and UIs to manage your apps. You manage apps for your organization in the Manage apps page in the Teams admin center portal. Use the URL https://admin.teams.microsoft.com/policies/manage-apps to view and govern apps that are available in your organization's app catalog. Evaluate apps before allowing them, find support information, and manage availability of apps across your org on a per-user or per-app basis. Starting from April 2025, your tenant is automatically migrated to app centric management.
The Teams admin center now includes Apps to consider allowing tile on the Manage apps page. This tile displays counts of Microsoft 365 certified and publisher-attested apps, helping admins quickly identify trusted apps. Select a count to filter the app list and simplify app management.
A new Security and compliance tab on each app’s details page displays its certification status, publisher attestation, and key security attributes etc. For more information, see App compliance program for security, data handling, and privacy.
To use Teams admin center, you must have a Teams Administrator role. Some admins with a higher privilege role can accomplish app governance tasks but we recommend using the lower privilege role where possible. For details, see Teams administrator roles and Microsoft 365 administrator roles.
App developers extend Microsoft 365 Copilot by creating copilot agents, for example, Microsoft Teams message extension or a Power Platform connector. These copilot agents increase user productivity across daily tasks and workflows. Admins manage copilot agents in the Integrated apps page of the Microsoft 365 admin center.
Note
You can only view and manage apps that are deployed in the same release channel as your tenant is. For example, if your tenant is in the general release channel then you can't manage apps that are deployed in the private or public preview channels. This isn't an issue for apps that are released to the general release channel.
App management use cases and the available interfaces
The options to accomplish most of app management use cases are available in Teams admin center. In addition, some options are available in other portals or different pages in the Teams admin center.
App management tasks that are supported in admin center are tabulated as follows:
| App management use cases | Link to the interface | Documentation |
|---|---|---|
| Control which apps are available to users in your organization by allowing and blocking apps. You can also upload and approve custom apps. After managing apps on this page, you can use app permission and app setup policies to configure what apps are available for specific users in your organization's app store. | Manage apps in Teams admin center | Current article |
| Specific users and groups that you select can access the app. Supported group types include Security groups, Microsoft 365 groups, Dynamic user membership groups, Nested groups, and Distribution lists. Guest users can't access the app, even if they’re assigned to it. | TAC-Dashboard | Access Control for Apps |
| You can customize the Teams app store with your organization's logo, custom background, or color. | Customize store | Customize your organization's app store |
| The Teams app usage report provides information about which apps in use, active users, and other app usage information. | Usage reports | Teams app usage report |
| Your users can add apps when they host meetings or chats with guests. They can also use apps shared by guests when they join meetings or chats hosted externally. The data policies of the hosting user's organization, and the data sharing practices of any third-party apps shared by that user's organization, are applied. | External access | App behavior depending on types of users |
| With guest access, you can provide access to applications and other Teams functionality to people outside your organization, while maintaining control over your corporate data. | Guest access | Guest access in Teams |
| Teams update policies are used to manage Teams and Office preview users who can see prerelease or preview features in the Teams app. | Teams update policies | Teams public preview |
Export app catalog as CSV
As an admin, you can export the entire app catalog of your org from the Teams admin center. It can help you to coordinate with admin and security teams to evaluate apps, verify app availability, verify app status, and more.


Allow or block apps
As an admin, you control access to all types of apps that are used across your organization. Know the different Types of Apps, which you can access. Teams provides granular controls to configure access for each app and for each user. To allow an app or a Copilot agent, you must do all of the following settings. To block an app, use any one of the following settings:
| Method | Scope | Use case |
|---|---|---|
| Org-wide app settings | Org-level | Use this setting to allow use of relevant apps in your org. |
| app centric management | User-level | Let all users or let specific users use an app. |
You can allow or block specific apps or Copilot agents on either the Manage apps page or in the app details page. If your organization isn't migrated to unified app management, allow or block the app or Copilot agent in Teams admin center and under the Integrated apps page in Microsoft 365 admin center. If your organization is migrated to unified app management, allow or block the app or Copilot agent in Teams admin center or under the Integrated apps page in Microsoft 365 admin center. See Unified agent and app management to understand how you can unify agents, apps availability across both the admin centers.
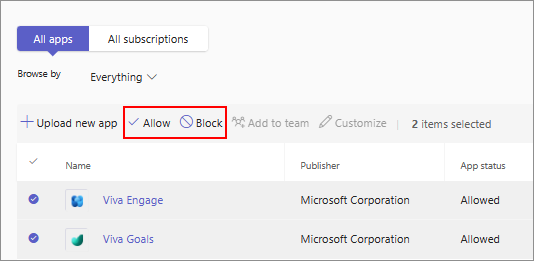
The Manage apps page displays all the available apps and the current org-level app status. To allow or block an app in TAC, follow these steps:
Sign in to the Teams admin center and access Teams apps > Manage apps.
Select the app on the Manage apps page and select Allow or Block option.
Alternately, click on the app name to open its app details page. Change status between Allowed and Blocked.
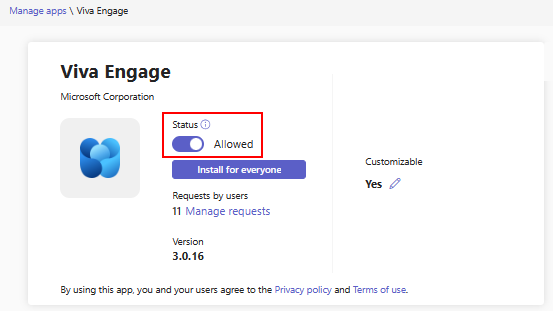
Use app assignment through app centric management to define user access for apps. The previous App permission policies is deprecated.
When a developer publishes an app to the Teams store, some apps may need an admin to configure the app. Before an admin allows such an app, it shows as Blocked by publisher in the admin center. Before you allow it for users, follow the publisher's guidance to configure the app.
To block all third-party apps, open the Org-wide app settings on the Manage apps page and disallow the use of third-party apps. With app centric assignment you can also block apps created by Microsoft.
Note
From within the Teams client, your users can request you to allow the apps that aren't available for them. You receive notifications and can allow the app. For details, see view and manage user requests.
- If your organization is migrated to unified app management, you can allow apps and Copilot agents in Teams admin center or under the Integrated apps page in Microsoft 365 admin center. For more information, see Unified agent and app management.
Note
Until your tenant is migrated to unified app management, ensure that the settings in both admin centers, such as blocked apps or org-wide app settings, remain synchronized. This measure prevents unexpected disruptions or issues with app functionality.
Manage org-wide app settings
Use org-wide app settings to control whether users with an F license get the tailored frontline app experience. Check if users can install third-party apps, or upload custom apps in your organization.
On Manage apps page, under the Actions menu, select Org-wide app settings. You can then configure the settings you want in the pane.

Under Tailored apps, turn off or turn on Show tailored apps. When this setting is on, users with an F license get the tailored frontline app experience. This experience pins the most relevant apps in Teams for frontline workers. To learn more, see Tailor Teams apps for your frontline workers. This feature is available for F licenses.
Under Microsoft apps, a single control automatically enables users to install and use any available apps by default.
Under Third-party apps, a single control manages the bulk availability of both the new and existing third-party apps.
Under Custom apps, turn off or turn on Let users install and use available apps by default option. This setting controls whether users can install and use the custom apps that you make available to them. To learn more about custom apps, see how to manage custom apps.
Select Save. The settings take effect after a few hours.
Admin center settings might allow your users to collaborate with users from other organizations. To understand how apps work with external users in meetings, see Teams apps for external attendees.
Install apps or let users install apps and uninstall apps
IT admins can install Teams apps for some or all users in their organization. Developers might create some Teams apps to work on Outlook and Microsoft 365 Apps (formerly office.com). You can easily preinstall the apps on all the supported hosts. Alternately, you can let users install apps on their own. A few supported apps can also be auto installed if a user uses it outside teams. For details, see how to preinstall apps.
Manage org-wide app settings for Microsoft 365 Government
In a Microsoft 365 Government - GCC, GCCH and DoD deployment of Teams, all third-party apps are blocked by default. In GCC, you see the following note about managing third-party apps on the app permission policies page in the Microsoft Teams admin center.
Manage apps in 21Vianet and air-gapped cloud environments
In Microsoft 365 operated by 21Vianet and air-gapped cloud environments, you get an overview of the apps on the Teams apps > Manage apps page.
To view more details of an app, select an app's name to access the app details page. You can allow or block the app for your users.
Support information for apps
You might have queries about admin settings or configuration, user flows and app features, app troubleshooting, and more. You receive support information about apps from the following two different sources:
We don't provide direct customer support for Teams apps but we provide the following safeguards, health checks, and certification methods for apps:
- We proactively check Teams apps for issues and inform the developer to update their app. Scenarios covered are related to app health, functional issues reported by users to Microsoft, security issues, and so on. For details, see Microsoft enforcement actions for published apps.
- For Publisher Attested and Microsoft 365 certified apps, Microsoft offers security and compliance information. If app developers consent, Microsoft provides admins with the option to download the detailed evidence submitted by developers during the certification audits for apps or copilot agents.
- Testing of all apps as part of its app validation program to ensure that all apps work as advertised. If apps don't work as suggested in the app listing, then we contact app developers to request either an update to the app. If app developers don't make the requested updates after a few reminders, we proactively remove the apps from Teams.
- Certification to apps using Microsoft 365 app compliance program ensures that apps are compliant with the industry-standard frameworks.
Developer provided app information, support, and documentation
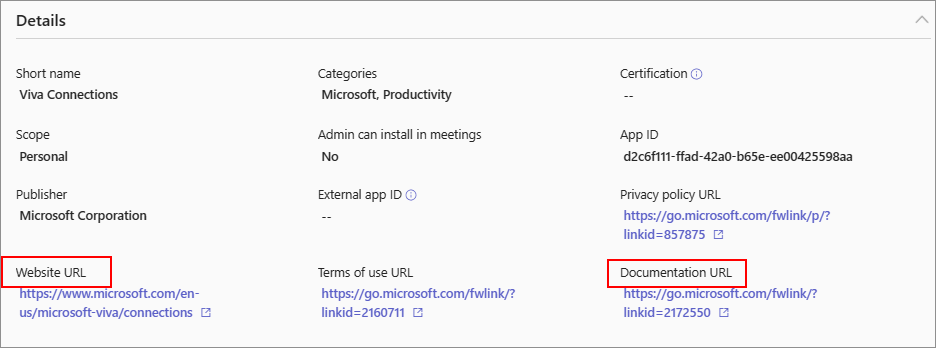
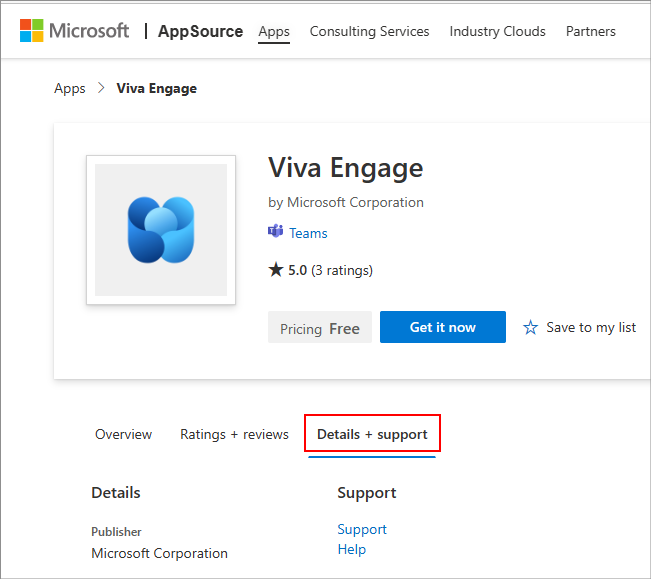
App developers provide customer support, updates to the apps, security and compliance information, bug fixes, and so on. The app security and compliance information are available in the admin center in app details page. App developers publish app updates, bug fixes, and vulnerability fixes as per their business requirements, issue severity, and service agreements. For direct support requests and inquiry about app updates, contact the app developer at their website address available at the following two places:
App details page of the app in Manage apps page in Teams admin center.
Details + support tab of the app's AppSource page.
Privacy and data access considerations: In the terms of use and privacy policy of any app, the app developer discloses what data their app uses and how it handles the data. This information is available on app developer's website and you can access the URLs in the app details page in Teams admin center. Many app developers choose to undergo the Microsoft 365 app compliance program. The program checks and audits an app against controls that are derived from leading industry-standard frameworks. The detailed information about each such app is available at Teams Apps Security and Compliance.
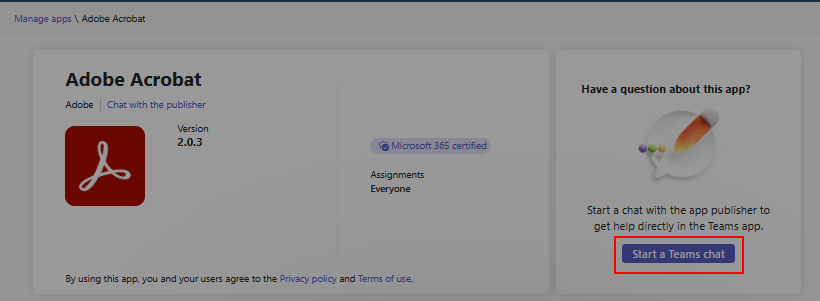
App developers can provide their contact information that you can use to chat with them. It helps you quickly evaluate an app and get the needed information from the app developers before you adopt and roll out an app. Examples include compliance information, certifications, data handling practices, pricing details for paid apps, and setup instructions. You can start a chat with app developers by selecting Start a Teams chat but only if the app developer provided their contact information. We recommend that you don't share personal and sensitive information in the chat.