Events
Apr 9, 3 PM - Apr 10, 12 PM
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
In this article, you learn how to review permissions granted to applications in your Microsoft Entra tenant. You might need to review permissions when you detect a malicious application, or one that has more permissions than is necessary. You learn how to revoke permissions granted to the application using Microsoft Graph API and existing versions of PowerShell.
The steps in this article apply to all applications that were added to your Microsoft Entra tenant via user or admin consent. For more information on consenting to applications, see User and admin consent.
To review permissions granted to applications, you need:
You can access the Microsoft Entra admin center to view the permissions granted to an app. You can revoke permissions granted by admins for your entire organization, and you can get contextual PowerShell scripts to perform other actions.
For information on how to restore revoked or deleted permissions, see Restore permissions granted to applications.
To review an application's permissions granted for the entire organization or to a specific user or group:
Note
You can't revoke permissions in the User consent tab using the portal. You can revoke these permissions using Microsoft Graph API calls or PowerShell cmdlets. Go to the PowerShell and Microsoft Graph tabs of this article for more information.
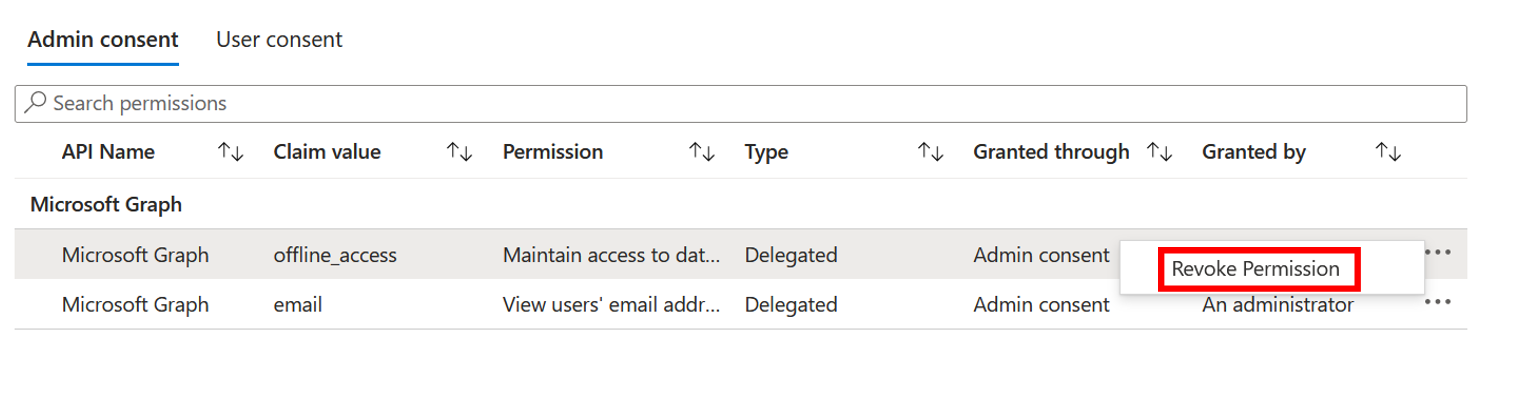
To revoke permissions in the Admin consent tab:
Use the following Microsoft Entra PowerShell script to revoke all permissions granted to an application. You need to sign in as at least a Cloud Application Administrator.
Connect-Entra -scopes "Application.ReadWrite.All", "DelegatedPermissionGrant.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
# Get Service Principal using objectId
$app_name = "<app-displayName>"
$sp = Get-EntraServicePrincipal -Filter "displayName eq '$app_name'"
# Get all delegated permissions for the service principal
$spOAuth2PermissionsGrants = Get-EntraOAuth2PermissionGrant -All | Where-Object { $_.clientId -eq $sp.ObjectId }
# Remove all delegated permissions granted to the service principal
$spOAuth2PermissionsGrants | ForEach-Object {
Remove-EntraOAuth2PermissionGrant -ObjectId $_.ObjectId
}
# Get all application permissions for the service principal
$spApplicationPermissions = Get-EntraServicePrincipalAppRoleAssignment -ObjectId $sp.ObjectId -All | Where-Object { $_.PrincipalType -eq "ServicePrincipal" }
# Remove all application permissions
$spApplicationPermissions | ForEach-Object {
Remove-EntraServicePrincipalAppRoleAssignment -ObjectId $_.PrincipalId -AppRoleAssignmentId $_.objectId
}
Remove appRoleAssignments for users or groups to the application using the following scripts.
connect-entra -scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
#Retrieve the service principal object ID.
$app_name = "<Your App's display name>"
$sp = Get-EntraServicePrincipal -Filter "displayName eq '$app_name'"
$sp.ObjectId
# Get Microsoft Entra App role assignments using objectId of the Service Principal
$assignments = Get-EntraServicePrincipalAppRoleAssignedTo -ObjectId $sp.ObjectId -All $true
# Remove all users and groups assigned to the application
$assignments | ForEach-Object {
if ($_.PrincipalType -eq "User") {
Remove-EntraUserAppRoleAssignment -ObjectId $_.PrincipalId -AppRoleAssignmentId $_.ObjectId
} elseif ($_.PrincipalType -eq "Group") {
Remove-EntraGroupAppRoleAssignment -ObjectId $_.PrincipalId -AppRoleAssignmentId $_.ObjectId
}
}
Use the following Microsoft Graph PowerShell script to revoke all permissions granted to an application. You need to sign in as at least a Cloud Application Administrator.
Connect-MgGraph -Scopes "Application.ReadWrite.All", "Directory.ReadWrite.All", "DelegatedPermissionGrant.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
# Get Service Principal using objectId
$sp = Get-MgServicePrincipal -ServicePrincipalID "<ServicePrincipal objectID>"
Example: Get-MgServicePrincipal -ServicePrincipalId 'aaaaaaaa-bbbb-cccc-1111-222222222222'
# Get all delegated permissions for the service principal
$spOAuth2PermissionsGrants= Get-MgOauth2PermissionGrant -All| Where-Object { $_.clientId -eq $sp.Id }
# Remove all delegated permissions
$spOauth2PermissionsGrants |ForEach-Object {
Remove-MgOauth2PermissionGrant -OAuth2PermissionGrantId $_.Id
}
# Get all application permissions for the service principal
$spApplicationPermissions = Get-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $Sp.Id -All | Where-Object { $_.PrincipalType -eq "ServicePrincipal" }
# Remove all application permissions
$spApplicationPermissions | ForEach-Object {
Remove-MgServicePrincipalAppRoleAssignedTo -ServicePrincipalId $Sp.Id -AppRoleAssignmentId $_.Id
}
Remove appRoleAssignments for users or groups to the application using the following scripts.
Connect-MgGraph -Scopes "Application.ReadWrite.All", "Directory.ReadWrite.All", "AppRoleAssignment.ReadWrite.All"
# Get Service Principal using objectId
$sp = Get-MgServicePrincipal -ServicePrincipalID "<ServicePrincipal objectID>"
Example: Get-MgServicePrincipal -ServicePrincipalId 'aaaaaaaa-bbbb-cccc-1111-222222222222'
# Get Microsoft Entra App role assignments using objectID of the Service Principal
$spApplicationPermissions = Get-MgServicePrincipalAppRoleAssignedTo -ServicePrincipalID $sp.Id -All | Where-Object { $_.PrincipalType -eq "ServicePrincipal" }
# Revoke refresh token for all users assigned to the application
$spApplicationPermissions | ForEach-Object {
Remove-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $_.PrincipalId -AppRoleAssignmentId $_.Id
}
To review permissions, Sign in to Graph Explorer as at least a Cloud Application Administrator.
You need to consent to the following permissions:
Application.ReadWrite.All, Directory.ReadWrite.All, DelegatedPermissionGrant.ReadWrite.All, AppRoleAssignment.ReadWrite.All.
Run the following queries to review delegated permissions granted to an application.
Get service principal using the object ID.
GET https://graph.microsoft.com/v1.0/servicePrincipals/{id}
Example:
GET https://graph.microsoft.com/v1.0/servicePrincipals/00001111-aaaa-2222-bbbb-3333cccc4444
Get all delegated permissions for the service principal
GET https://graph.microsoft.com/v1.0/servicePrincipals/{id}/oauth2PermissionGrants
Remove delegated permissions using oAuth2PermissionGrants ID.
DELETE https://graph.microsoft.com/v1.0/oAuth2PermissionGrants/{id}
Run the following queries to review application permissions granted to an application.
Get all application permissions for the service principal
GET https://graph.microsoft.com/v1.0/servicePrincipals/{servicePrincipal-id}/appRoleAssignments
Remove application permissions using appRoleAssignment ID
DELETE https://graph.microsoft.com/v1.0/servicePrincipals/{resource-servicePrincipal-id}/appRoleAssignedTo/{appRoleAssignment-id}
Run the following queries to remove appRoleAssignments of users or groups to the application.
Get Service Principal using objectID.
GET https://graph.microsoft.com/v1.0/servicePrincipals/{id}
Example:
GET https://graph.microsoft.com/v1.0/servicePrincipals/aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb
Get Microsoft Entra App role assignments using objectID of the Service Principal.
GET https://graph.microsoft.com/v1.0/servicePrincipals/{servicePrincipal-id}/appRoleAssignedTo
Revoke refresh token for users and groups assigned to the application using appRoleAssignment ID.
DELETE https://graph.microsoft.com/v1.0/servicePrincipals/{servicePrincipal-id}/appRoleAssignedTo/{appRoleAssignment-id}
Note
Revoking the current granted permission doesn't stop users from re-consenting to the application's requested permissions. You need to stop the application from requesting the permissions through dynamic consent. If you want to block users from consenting altogether, read Configure how users consent to applications.
Delegated and application permissions aren't the only ways to grant applications and users access to protected resources. Admins should be aware of other authorization systems that might grant access to sensitive information. Examples of various authorization systems at Microsoft include Microsoft Entra built-in roles, Exchange RBAC, and Teams resource-specific consent.
Events
Apr 9, 3 PM - Apr 10, 12 PM
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowTraining
Module
Manage Microsoft Entra application access - Training
This module focuses on effectively managing identities and enhancing security in Microsoft Enterprise Identity, ensuring that users, groups, and external identities are protected against security threats and unauthorized access.
Certification
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Documentation
Grant tenant-wide admin consent to an application - Microsoft Entra ID
Learn how to grant tenant-wide consent to an application so that end-users aren't prompted for consent when signing in to an application.
Grant consent on behalf of a single user - Microsoft Entra ID
Learn how to grant consent on behalf of a single user when the user consent is disabled or restricted.
Configure how users consent to applications - Microsoft Entra ID
Learn how to manage how and when users can consent to applications that request access to your organization's data.