After 2 days trying to find a solution and changing every imaginable Windows 10 setting, we purchased a printer with ethernet connection (a Brother laser printer in our case) and the problem was solved in a few minutes, that was the best thing I did this year. I understand this may not help larger companies with a complex infrastructure but smaller companies should not waste time uninstalling packages or changing settings.
Print server and Print Nightmare update
Hi All,
I'm having issues with some Print Servers after running Windows Updates and installed
2021-08 Cumulative Update for Windows Server 2019 for x64-based Systems (KB5005030)
After the update installation I'm getting the error "Connect to printer Windows cannot connect to the printer. Operation failed with error 0x0000011b" and the printer fails to install.
Is there any workaround to keep Print Severs up and running?
I cannot permanently remove the August update, because the Print Nightmare update will come again in Sept Cummulative Update.
I also tried to revert the configurations using:
* “Allow Print Spooler to accept client connections” policy
* HKEY_LOCAL_MACHINE \Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint.
Nothing worked. I will appreciate any advice.
Thanks,
Manuel
Windows Server Printing
-
Ruhan Rheeder 6 Reputation points
2021-08-18T15:05:19.897+00:00 This problem caused allot of pain in our environment 600 users couldn't print.
This was our fix and it works immediately:
Create a GPO in the computer configuration:
NoWarningNoElevationOnInstall = 1
UpdatePromptSettings = 1
RestrictDriverInstallationToAdministrators - 0This solved our issue.
Regards
-
Mark K 71 Reputation points
2021-08-18T15:41:01.437+00:00 The RestrictDriverInstallationToAdministrators - 0 is what is fixing the issue for you, but that opens the way for the PrintNightmare vulnerability to still be exploited. It is a solution to get people working again, but this is something that Microsoft needs to fix in a better fashion somehow, such as having GPO installed printers still work.
-
 James Iversen 36 Reputation points
James Iversen 36 Reputation points2021-08-24T23:50:49.157+00:00 I've got a good one Microsoft may not actually be devising a fix for this but...
Got the above error with a twist. We don't use PointandPrint... All our (I say "all" when things are running smoothly) printers are published using GPO's to targeted computers, not users. Every computer is named in such a way we can identify groups of computers based on location, department and OS. When a new computer is joined to the domain, the computer is added to several groups. One of the groups they are added to are used for multiple policies. The policies are designed to publish as few as one to as many as a dozen printers to that computer. So there's no user interaction when installing a printer. RestrictDriverInstallationToAdministrators - 0 is being used on a case by case basis for people who absolutely must print to keep our business running. Corporate is going to be some pissed with the AD guy because he can't get printers to deploy any more. Not a fun place to be. Never have I seen something like this before. Oh, there's been inconveniences but never a total blockage. I spun up a new 2019 server and started building V4 ONLY queues with still no joy. This is the crap suicides are made of. -
F17576 1 Reputation point
2021-09-03T08:28:24.507+00:00 If you deploy the printer via GPO to the machine rather than the user, it works as the machine installs the driver with SYSTEM rights.
-
The_Russeller_1 6 Reputation points
2021-09-15T11:50:17.887+00:00 Interesting question this one as it seems this PrintNightMare patch has caused an even bigger nightmare...
I've also implemented the GPO to restrict the point and print down to a specified list of print server and am seeing somewhat inconsistent results with the behaviour of this - adding the printers print queue seems to be possible sometimes but others not, when adding/ installing the drivers for a shared printer from the print server directly no issues this can continue without the UAC prompt.
My troubleshooting has led to me adding the print queue class (1ed2bbf9-11f0-4084-b21f-ad83a8e6dcdc) into the GPO option to enable specified device classes to be installed seems to work really well - I am now able to install the print queue drivers without any issues.
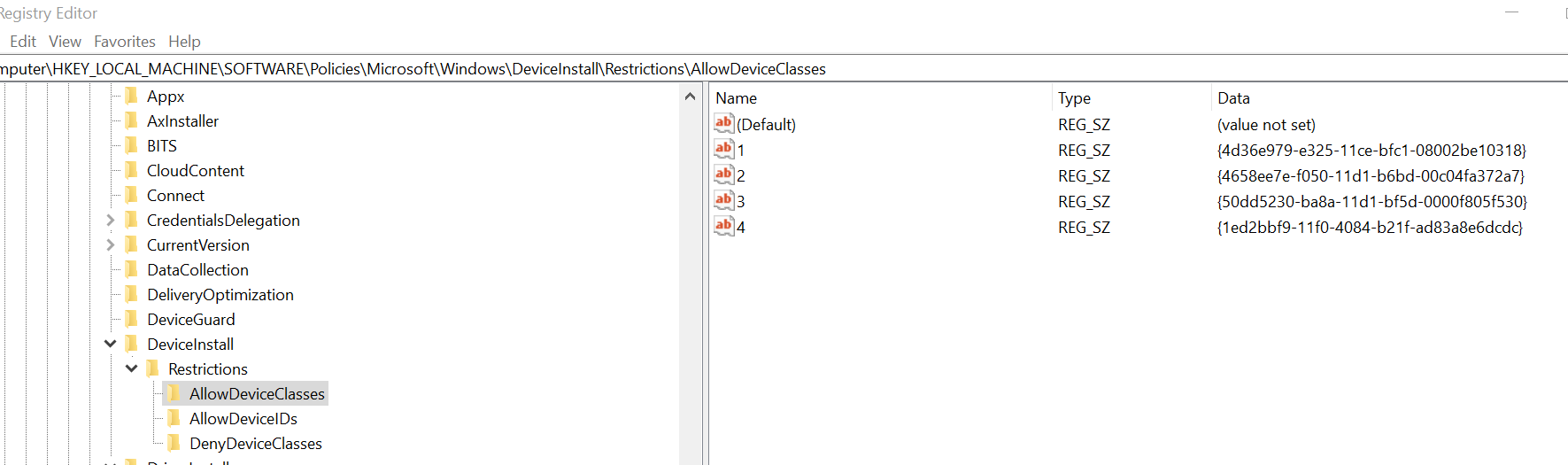
-
Mike Price 71 Reputation points
2021-09-15T21:00:20.583+00:00 This just hit us this morning too. 9/15/2021. No one can print to the network printers.
I removed KB5005613 from our server and rebooted the server and that fixed it. Had to do that at all 8 of our branch offices too.
Microsoft updates seem to be more like hackers. Not professional. -
RAGIL ARUM 26 Reputation points
2021-09-16T02:34:16.293+00:00 Today, 16 September 2021, I got the same problem, cannot print to printer on the server. Fortunately, I read this article and then I can assume what was happen to me, is caused by BAD Windows update. Then, I check Updates history, and find one update installed on 15 September 2021 (Security updates KB5005565). So, I uninstall it, and reboot. And, YES, the printer works normally, ... God Bless Us.. Alhamdulillah, Amiin
-
Rytis Pau 1 Reputation point
2021-09-16T05:02:15.253+00:00 It is also hepled me too! Thnaks!
-
CashCity Joondalup 11 Reputation points
2021-09-16T06:13:44.83+00:00 I Can CONFIRM we had the same Problem and nothing would work , even our Tec couldn't figure it out so i got on this Forum and YES The Above answer Solved our Prob , Deleted the Security updates KB5005565 and restarted and bingo , Printer can connect again..
Thanks
-
Javier Polo Cozar 31 Reputation points
2021-09-16T09:31:57.723+00:00 We had same problem, just affecting to Windows 7 computers. After uninstalling 15/09/2021 updates
(KB5005613, KB5005627 y KB5005563) and a long reboot, computers were able to print again. -
Informatique HLP 11 Reputation points
2021-09-16T12:19:57.577+00:00 We did the same thing, on our PRINTER Server, and it works.
-
Chris Clementi 1 Reputation point
2021-09-16T13:09:36.283+00:00 Doing the same thing on my print server now.
-
cgrun 1 Reputation point
2021-09-16T14:14:33.51+00:00 Hi,
Same here, forced to uninstall the monthly KB on Windows 2019 in order to permit to Windows 7 users to continue to print... Very long reboot after the uninstall, but users can print now... How correct this ?
-
Thomas Jaisson 11 Reputation points
2021-09-16T14:38:08.457+00:00 Hi from France
Same thing here.
I just wanted to mention that on our 2012 server the update I had to remove was KB5005623
W7 clients are now able to print again. -
imvoidingwarranties 1 Reputation point
2021-09-16T16:52:06.057+00:00 Push the printer drivers for your devices to your users using SCCM. Make sure when you extract the drivers from your print servers that you use an Administrator account. Once the users have the printer drivers they will no longer be prompted for an elevated user. I realize that the package is going to be large. If you use x86 and x64 bit driver packages it will increase the package size, but for some of us in large enterprises old applications and equipment still utilize these. Remember, the GPO states that if the DRIVER is new or updated you will be prompted. It doesn't prompt because you are installing a new device. If you already have the driver it will not prompt you for an elevated account.
-
Baronduke 11 Reputation points
2021-09-16T16:55:32.9+00:00 thank you for help . in my case it was necessary to restart the second server which was on 2016. Windows should not launch a security update for our security.
-
Eric Treater 1 Reputation point
2021-09-16T19:17:16.62+00:00 got us today, and I had already put the RestrictDriverInstallationToAdministrators - 0 key into place previously. It hit us when KB5005613 got installed on our print servers. Still testing, but I believe uninstalling 5613 fixed it.
-
Surge 16 Reputation points
2021-09-16T21:00:58.207+00:00 Uninstalling KB5005565 may work but this is a cumulative update. i may be wrong but you still have the PrinterNightmare issue. Just trading off risk/problem.
-
Surge 16 Reputation points
2021-09-16T21:06:12.867+00:00 Some of the KBs you removed are cumulative. Printing may have been restored but so was the PrintNightmare problem and other vulnerabilities.
-
Surge 16 Reputation points
2021-09-16T21:07:33.017+00:00 We deploy per machine and still see problems.
-
Michael McDonald 1 Reputation point
2021-09-16T22:04:46.937+00:00 Same problem here on server 2012 r2, except the next day the update just reinstalled. Wish Microsoft would hurry up and fix this plagued update.
-
David Jerrams 6 Reputation points
2021-09-17T13:49:11.637+00:00 Hi,
All 4 of my windows 10 computer have this error -
38330931 6 Reputation points
2021-09-17T14:13:46.303+00:00 Same issue. Removed that update, and all devices were able to print after the server was rebooted.
-
DrT 26 Reputation points
2021-09-17T17:47:38.417+00:00 What do you think is better, to have the inability to print within your organization, or continue to have PrintNightmare vulnerability? It's not a trade-off at all. Businesses need to print to continue their operations. Obviously Microsoft needs to fix the problem properly. You need to uninstall September 2021 cumulative update on all print servers to get them working again.
-
DrT 26 Reputation points
2021-09-17T17:49:38.907+00:00 Just what MarkK said, this was a known workaround to the problems caused by the 'fixes' for PrintNightmare, but doesn't resolve PrintNightmare. Once this issue is actually resolved, you need to consider removing that GPO as it will override the actual fix (if it's ever available).
-
Dr. Aries Singularity 1 Reputation point
2021-09-18T15:57:36.283+00:00 I started getting calls from clients over the last 4-6 weeks about a "shared" printer suddenly could not be accessed. The networks are typically small 10-15 PCs in a non-AD environment in veterinarian clinics.
The printer status column shows "driver needs update". You click to update and it fails - Cannot Connect to Printer. If I remove the shared printer and try to connect to it again, the Cannot Connect message comes up again.
After many hours of trying everything under the sun, I added the user account/password (for every user needing to access the printer) to the PC where the "shared" printer is actually installed (USB). I could then immediately connect.
I haven't had any problems with Ethernet connected network printers - just the shared printers (i.e. DYMO label) attached to a PC.
I think the problems everyone are having is related to whatever security update Microsoft recently put out there. Would sure be nice to see an error message that gave some useful information instead of 0X000001B or whatever.
Nuff Said!
-
Andy Baptist 1 Reputation point
2021-09-20T10:00:57.967+00:00 When rolling back the dodgy update is it on the server machine, the client PCs or both?
-
SenhorDolas 1,171 Reputation points
2021-09-20T14:15:41.53+00:00 Hi Everyone,
Is the September patches affecting already mapped printers or newly mapped?
My Print server is 2016 and clients are W10.
We have a Win 10 UAT groups and the update KB5005565 installed fine and no users complained.
However I am not sure if this is affecting newly mapped printers? As in user connect to print server and select the printer and the drivers come down?
Thanks M -
Rayden Germosen 1 Reputation point
2021-09-20T18:12:26.353+00:00 Just apply all the windows updates. specially H20. after that check there are no more updates. issue will be fixed. The work around is to add the printer locally (manually).
-
Connie Richardson 1 Reputation point
2021-09-20T19:25:13.707+00:00 I I have all Widows 10 computers and and a Windows 2012 R2 Printserver.
I I unistalled update 5005613 from the printer Server and all printers started printing on Wed September 16th 2021. The next morning bright and early the calls started coming in that peoples printers would not print again. So I Looked that the print server update and It had reinstalled itself. I uninstalled it and they all started printing again. Today is Monday, September 20th and I have had to uninstall it everyday. It did not affect all my network printers, just some of them. I am hoping for a fix on Tuesday ( with fingers crossed) but I have also deleted some of the affected printers and reinstalled them with an adiministrator rights and the IP address. I will retrun tomorror and let you know if it helped. -
Sandy 1 Reputation point
2021-09-20T19:34:51.213+00:00 None of the reg hacks worked for me. Bringing the problematic computer UptoDate with windows worked like a charm.
Regards,
-
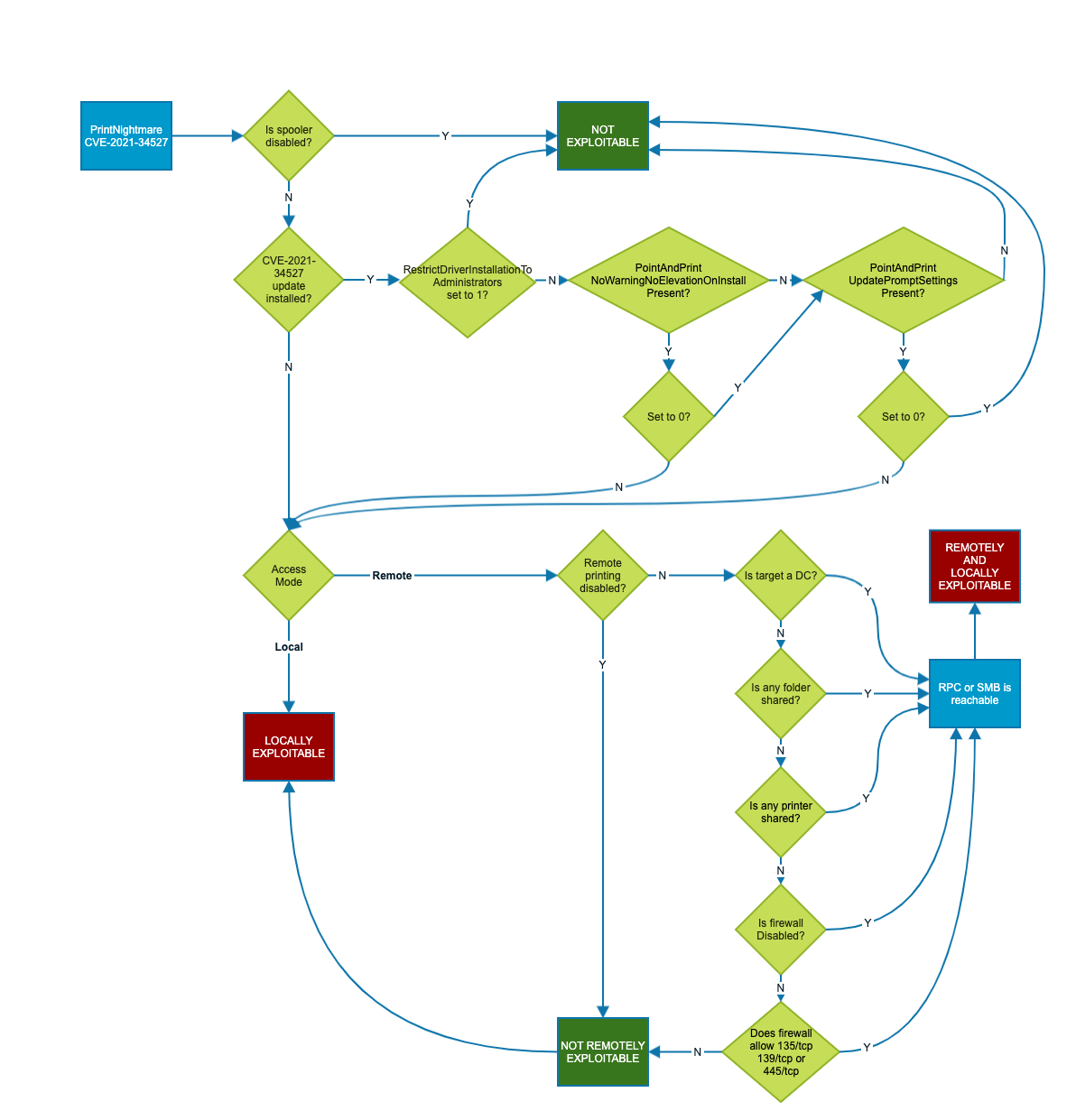
 ahunt 161 Reputation points
ahunt 161 Reputation points2021-09-20T19:40:21.817+00:00 The correct way to fix this may lie in following this flowchart to ensure that remote exploitation of PrintNightmare is not possible while allowing Point and Print
I will update this later with any progress I find in this. If you can, please do not set RestrictDriverInstallationToAdministrators to 0 as this will make you vulnerable.-thank you
-
BlakeWAmy 11 Reputation points
2021-09-20T19:45:49.877+00:00 Awesome, I am building up a guide for my org and will use this.
From what I see most people are getting servers updated then reporting the clients can't print. So they uninstall the servers updates and volia. I'm not fully sure of the clients being unable to print if the server is updated already as well. But the aforementioned issue appears to be the main culprit. This Sept update made an enforcement change on the Jan updates for the Auth protocol of the Print Spooler to the Server/Client relationship. So the value is being set from the default of 0 as non enforcement to 1 with the Sept updates. I haven't run into this problem directly but was following this thread due to the Admin install prompt issue which is unrelated to the Sept updates issue. The unfortunate situation here is Microsoft has poorly communicated the Print Nightmare fixes. But they have slowly updated their primary Point and Point document to detail the needed changes. They have yet to deal with the V3 GPO issue, although mentioned now doing a manual compare of the users driver files. Alas. I set the Auth protocol to 0 through GPO and updated my server. Then installed the latest updates on a client and server. No issues printing. I tested on a non updated client and no issues printing as well. This is due to me changing the enforcement level for the Auth change. I suspect when I change the Auth level back to 1 as Enforced per Microsoft then those client machines won't print because they are not up to date.
Soooooo confusing. Your flow chart is very helpful!
-
BlakeWAmy 11 Reputation points
2021-09-20T19:48:30.44+00:00 One more note, I would say you should add the RPC changes to this as well.
And
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1678
This is what I primarily mention above and what seems to have triggered an influx of complaints.
-
 ahunt 161 Reputation points
ahunt 161 Reputation points2021-09-20T19:49:34.93+00:00 Credit goes to Will Dormann twitter @wdormann for this flow chart, I'm just sharing it here.
-
Abdou Elmoslemany 1 Reputation point
2021-09-21T08:10:19.247+00:00 I have tray almost all of the solutions in this topic and no thing works with me,
I have try to remove updates, registry records and even 3rd party solutions and others option
tI notice then this not only one update, it seams that it is more than one update from 8-2021 until now on windows server and windows 10
so i have install all updates and after September 14, 2021—KB5005565 installed on windows 10 then try again the registry value of "RestrictDriverInstallationToAdministrators" and set it to 0 and and surprise ... it's works .. it's works
this topic is very helpful to me, thanks for it's author
https://www.anthonyfontanez.com/index.php/2021/08/12/printnightmare-point-and-print/
-
Sean Andrews 1 Reputation point
2021-09-22T01:36:30.503+00:00 After workstations are fully patched, is it safe to turn on remote printing to shared printers again?
Remove HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\RegisterSpoolerRemoteRpcEndPoint = 2Thank you for the help,
Sean
-
 Kazim 66 Reputation points
Kazim 66 Reputation points2021-09-22T13:30:10.723+00:00 Currently experiencing this same issue 09/22/2021. Where a Windows Server 2012 R2 Standard can't add/connect to shared printers. "Connect to Printer Windows cannot connect to the printer. Operation failed with error 0x0000011b"
I don't have any of these KB updates mentioned installed, so basically, I can’t use the uninstallation method which seems to be working for everyone. How do I go about fixing this issue if I don’t have these KB installed already?
NB: There are pending updates which include KB5005613
-
steviefaux 181 Reputation points
2021-09-22T13:57:19+00:00 Just removed those 3 on our server and now all working.
-
Mech 6 Reputation points
2021-09-22T16:12:47.727+00:00 I don't have any of these updates installed on my Server 2019 either tried all suggestions so far nothing
-
Justin 1 Reputation point
2021-09-22T20:53:24.98+00:00 Same here. Don't have any of these updates on the server. The fixes listed help with some PCs, but not all. Uninstalling updates on the PCs seems to work, but is a pain.
-
 Kazim 66 Reputation points
Kazim 66 Reputation points2021-09-22T21:17:07.553+00:00 Finally got it working!! Ensure that you uninstall those KB Updates on the client computers not just on the server; well in your case you don’t have those updates on your server so ensure that non-windows server operating systems do not have those updates installed.
-
Alex Pine 1 Reputation point
2021-09-23T00:05:35.007+00:00 I was able to resolve the issue by removing 5005568 from the print server
-
 Kazim 66 Reputation points
Kazim 66 Reputation points2021-09-23T18:00:20.437+00:00 Ensure that you remove those updates on your Windows 8.1/10 machines as well. This seems to have worked for me.
-
Daniel Estrada 1 Reputation point
2021-09-24T16:55:59.267+00:00 this is only affecting Print servers and Network printres correct? no other server to client printing?
-
Mech 6 Reputation points
2021-09-24T18:01:05.463+00:00 That is correct.
-
Mi4c 21 Reputation points
2021-09-24T18:26:51.98+00:00 IIf you really want really answers for this issue:
https://support.microsoft.com/en-us/topic/kb5004442-manage-changes-for-windows-dcom-server-security-feature-bypass-cve-2021-26414-f1400b52-c141-43d2-941e-37ed901c769cAfter the later link enforcement with septermber updates all MAC-, Linux- and windows-clients printing ability was disabled.
When client tries to communicate unsufficient authentication method the server responsed access denied with unproper error message.
There might be a firewall configurations to prevent proper communications in environments where only 445/TCP is enabled, some organizations doesn't like to approve unintended high ports communications with TCP nor UDP.
MS has now triggered something that no-one was prepared to deal with and haven't shared enought documentation how to properly configure these services to communicate how they want them to communicate.When only 445/TCP open, it is not enough ?
Should we open the high ports, is there any answer? which TCP or UDP to establish the correct communication?
IIn documentations of printing services there is ability to configure your print server to communicate only with 445/TCP, but this breaks now with the newest security update...
So you should enable high ports 49152-49158 tcp ???
Do we need to enable those documented udp ports also with 445 only enabled servers? that have the registry tweak to support non udp communications? -
 ahunt 161 Reputation points
ahunt 161 Reputation points2021-09-24T18:43:33.673+00:00 I especially like the part about "If you find issues during testing, you must contact the vendor for the affected client or server software for an update or workaround before early 2022."
yeah just push these issues out to the manufacturers, that sounds like a good idea....
I have had issues here with Brother printers, however they are not as severe. Some application calls seem to work while others fail. Our issues appear to be related to our Azure Active Directory in some way, but I haven't gathered any evidence for this yet. I believe it is a permissions issue, as I've experienced no problems with administrator accounts.
-
Jeff Wilson 6 Reputation points
2021-09-27T06:13:13.757+00:00 My 2k8R2 RDS servers could not connect to my 2k12 Std Print server. I removed KB5005623 from my 2k12 printer server and things came back on line.
2021-09 Security Monthly Quality Rollup for Windows Server 2012 for x64-based Systems (KB5005623)
Installation date: 2021-09-26 13:46
Installation status: Succeeded
Update type: Important
A security issue has been identified in a Microsoft software product that could affect your system. You can help protect your system by installing this update from Microsoft. For a complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article. After you install this update, you may have to restart your system.
More information:
https://support.microsoft.com/help/5005623Help and Support:
https://support.microsoft.com/help/5005623 -
DanHoffa 46 Reputation points
2021-09-27T16:30:13.483+00:00 I am experiencing a similar issue but it has to do with Deployment of Printers from GPO. If a user had already gotten their prints from GPO they are present and work. If users need printers to load from GPO they will not. When we run gpupdate /force we get this "Windows failed to apply the Deployed Printer Connections settings. Deployed Printer Connections settings might have its own log file. Please click on the "More information" link."
All other GPOs are processing and working properly.
Since I list all printers in the Directory. I can still install the printers manually from the Printer Servers through "Add Printer" and they install without issue even for none admin users.
Microsoft has really made a mess with this recent security update. Did they every test this with GPO deployment of printers before dumping it out there?
Anyone else seeing this behavior? Has anyone fixed this behavior?
-
John Paul Kendall 16 Reputation points
2021-09-28T14:04:33.193+00:00 Good point, however availability is part of the security triangle. Hopefully M$ will issue a new KB that patches the vulnerability as well as lets users print.
-
Musat, Eddy 1 Reputation point
2021-10-01T15:50:03.757+00:00 Best way around it that I found is to install the printer manually using a local port. No registry changes needed, and doesn't bypass any security patches put in place by Microsoft. Created a video on it: https://youtu.be/QwnOh69dlM8
-
Turps3000 1 Reputation point
2021-10-23T13:25:30.22+00:00 So, after following this message board and following most of what has been done before. E.g preloading drivers, placing DLLs in C:\Windows\System32\spool\drivers\x64\3, or some other changes, only half worked or was inconsistent. I came up with the approach below. I am aware that this will allow the vulnerability, but it will restrict it to a single or chosen print servers, which you can monitor with any desired VS/Network tools. Also make sure that DC have printer server spooler turned off (which you should be doing anyway) and the printer server is NOT facing the outside/externally (which to me would be nuts!) then this way will work for you….
This approach will do the following,
Allow a certain print server to install to non admins. All other print servers or other machines are not allowed to add drivers via non admin accounts.Allow you to carry on using GPO while you move to a better process like uni print.
No extra settings need to be added or reloaded via Intune/SCCM
Create the following rekey’s in GPP via Computer – Preferences – Windows settings – Registry – DO NOT USE A POLICY for some of the settings EVEN though they are located in the point and print template…..as this will not apply correctly. ALSO MAKE SURE THAT YOU ALSO APPLY IN ORDER AS MENTIONED BELOW 1-9. It’s very important the “RestrictDriverInstallationToAdministrators” is last to be applied. Also just apply it to your Machine OUs and you don’t have to change your existing printer policy.
-
Ffuhller 36 Reputation points
2021-11-17T20:32:37.687+00:00 I'm having the exact same issue but I have NONE of those updates nor on my server or my Win10 workstations. Anybody found a workaround that won't involve uninstalling updates? Server is 2016.
-
Ffuhller 36 Reputation points
2021-11-17T20:32:49.447+00:00 I'm having the exact same issue but I have NONE of those updates nor on my server or my Win10 workstations. Anybody found a workaround that won't involve uninstalling updates? Server is 2016.
-
 Alan Morris 1,156 Reputation points
Alan Morris 1,156 Reputation points2021-11-17T20:52:19.557+00:00 Hi @Ffuhller ,
The updates are cumulative in most cases. The numbers change from mont to month. For instance, October updates will include the binaries changed in July, then August, then September. The update that originally caused other failures was later updayed that caused different failures.
If you have not had a Windows update since June, then this would be some other issue. Check the file dates for localspl.dll and win32spl.dll in c:\windows\system32. If they have a date after July 3 of 2021, then you have been updated which is causing the problem. -
Julien.L Thesis 6 Reputation points
2021-12-13T10:25:31.373+00:00 Those CU are real mess....
Since months now we are strungling by uninstall all CU for servers since the 21-07 because each time it breaks printing on rds / print servers.
We tried all solutions with the point and print restrictions, registry keys, it doesnt work, the only solution for us is to uninstall the cumulative updates for servers.
But the problem is that nexts CUs applies the same things, so for now we had to stop CU since July, which is not secured at all for long time.When the CU are installed, the problems are :
- The printers are not anymore deployed with GPO
- We cant manage printers anymore, bugs while adding/removing printers
- Sometimes printers are deployed duplicated like this : PRINT1 and PRINT1.domain.local with nothing inside.
- Beside GPO failing, we cant add printer manually fromt print server. error when installing
We have those issues randomly on severals clients sites, the only solution that works is to uninstall the CU on the print server and the TS.
We have an IT assets management tool, so we are able to prevent installation of specific updates such as the CUs, but we cant continue like this.Printers are up to date with very last drivers, but it doesnt help at all.
I'm sorry to bother but the point and print restriction gpo solution doesnt work also.
Does anyone knows another way to be protected, updated and PRINTERS WORKS normally ?
-
ahmad seayfan 1 Reputation point
2022-06-16T09:35:15.323+00:00 Is this update happening today/anytime
Sign in to comment
54 answers
Sort by: Most helpful
-
Marcio Azevedo 1 Reputation point
2021-10-14T20:24:47.757+00:00 -
Allinace Z 16 Reputation points
2021-10-15T09:46:26.287+00:00 Shared printers did not work again with new update KB5006670 on Win10 21H1
sucks-
Ruan Sardinha 1 Reputation point
2021-11-04T18:56:20.31+00:00 Com essa atualização, não é mais preciso alterar o registro do Windows e consequentemente, tornar a maquina vulnerável. (Não tenho certeza se a maquina permanece vulnerável)
Para voltar a imprimir, basta logar como adm e reiniciar o serviço Spooler de Impressão. Minha maquina Win10 esta com a atualização 21H1
Sign in to comment -
-
MarlboroMan 1 Reputation point
2021-10-15T14:44:38.5+00:00 I am wondering if the new cumulative update for October just pushed out will mess up shared network printers hosted on a print server. I have held off on applying the updates for it.
-
Chris Clementi 1 Reputation point
2021-10-15T14:49:09.797+00:00 If you skipped last months update and didn't apply any of the work arounds. It will stop the network printing just like the last one did.
-
MarlboroMan 1 Reputation point
2021-10-15T14:59:38.617+00:00 What work arounds? Last month when the CU was applied to our Server 2016 print server. It stopped shared network printer from working. The solution in this thread was to uninstall it and reboot. Then the print server worked and all network shared printer resumed working again. We do not publish printers via GPO. We do use a Server 2016 as a network print server.
-
bwilkerson217 21 Reputation points
2021-10-15T15:13:42.483+00:00 There was information about registry changes as work arounds. I posted such a registry change I found on another site that worked for my environment. It is just a few posts above all this.
Here is that information again:
Registry subkey
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print
Value
RpcAuthnLevelPrivacyEnabled
Data type
REG_DWORD
Data
1: Enables Enforcement mode. Before you enable Enforcement mode for server-side, make sure all client devices have installed the Windows update released on January 12, 2021 or a later Windows update. This fix increases the authorization level for printer IRemoteWinspool RPC interface and adds a new policy and registry value on the server-side to enforce the client to use the new authorization level if Enforcement mode is applied. If the client device does not have the January 12, 2021 security update or a later Windows update applied, the printing experience will be broken when the client connects to the server through the IRemoteWinspool interface.
0: Not recommended. Disables the increase authentication level for printer IRemoteWinspool, and your devices are not protected.
-
MarlboroMan 1 Reputation point
2021-10-15T15:18:33.91+00:00 Thanks.
Which value did you use 1 or 0?
-
MarlboroMan 1 Reputation point
2021-10-15T15:19:59.523+00:00 Is this registry entry needed on the Server 2016 running as a print server and what value did you use for the work around 1 or 0?
-
bwilkerson217 21 Reputation points
2021-10-15T15:21:21.96+00:00 0
This will disable the security.
-
MarlboroMan 1 Reputation point
2021-10-15T15:25:42.307+00:00 Thank you!
-
bwilkerson217 21 Reputation points
2021-10-15T16:13:10.193+00:00 Good luck. I am hoping more information will come out on how organizations that use print servers and often have older printers that will never meet these new security requirements can have a solution on how to properly deploy printers and comply with the Microsoft Security settings
-
MarlboroMan 1 Reputation point
2021-10-15T16:17:59.327+00:00 Thanks! We do not have really old printers. Some were new Konica's but in the print server no issues printing with the CU installed. The issue was the clients connecting to the print server as others mentioned. What a cluster this has been.
I will hold off a few weeks and see what others have gone thru before I make the workaround and install the current October CU.
-
MarlboroMan 1 Reputation point
2021-10-16T02:15:52.727+00:00 I just looked in our print server Windows Server 1016 and the top value in the registry is not found. Did you have to create the value: RpcAuthnLevelPrivacyEnabled ?
-
bwilkerson217 21 Reputation points
2021-10-16T02:19:37.907+00:00 Yes You have to create the registry key.
-
MarlboroMan 1 Reputation point
2021-10-16T02:22:05.137+00:00 Thanks for the reply.
Sign in to comment -
-
Ruan Sardinha 1 Reputation point
2021-11-04T18:58:22.787+00:00 Senhores,
Acredito que o problema relacionado a correção da vulnerabilidade foi corrigido no pacote de atualização 21H1, não é mais preciso alterar o registro do Windows e consequentemente, tornar a maquina vulnerável. Para voltar a imprimir, basta logar com uma conta administrador e reiniciar o serviço Spooler de Impressão.
-
Turps3000 1 Reputation point
2021-10-23T13:27:07.627+00:00 So, after following this message board and following most of what has been done before. E.g preloading drivers, placing DLLs in C:\Windows\System32\spool\drivers\x64\3, or some other changes, only half worked or was inconsistent. I came up with the approach below. I am aware that this will allow the vulnerability, but it will restrict it to a single or chosen print servers, which you can monitor with any desired VS/Network tools. Also make sure that DC have printer server spooler turned off (which you should be doing anyway) and the printer server is NOT facing the outside/externally (which to me would be nuts!) then this way will work for you….
This approach will do the following,
Allow a certain print server to install to non admins. All other print servers or other machines are not allowed to add drivers via non admin accounts.Allow you to carry on using GPO while you move to a better process like uni print.
No extra settings need to be added or reloaded via Intune/SCCM
Create the following rekey’s in GPP via Computer – Preferences – Windows settings – Registry – DO NOT USE A POLICY for some of the settings EVEN though they are located in the point and print template…..as this will not apply correctly. ALSO MAKE SURE THAT YOU ALSO APPLY IN ORDER AS MENTIONED BELOW 1-9. It’s very important the “RestrictDriverInstallationToAdministrators” is last to be applied. Also just apply it to your Machine OUs and you don’t have to change your existing printer policy.
Hive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – Restricted
Value Type – REG_DWORD
Value data - 1Hive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – TrustedServers
Value Type – REG_DWORD
Value data – 1Hive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – ServerList
Value Type – REG_SZ
Value data – YOURPRINTSERVERNAME01@keyman .COM; YOURPRINTSERVERNAME02@keyman .COMHive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – InForest
Value Type – REG_DWORD
Value data – 1Hive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – NoWarningNoElevationOnInstall
Value Type – REG_DWORD
Value data – 1Hive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – UpdatePromptSettings
Value Type – REG_DWORD
Value data – 1Hive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – PackagePointAndPrintServerList
Value Type – REG_DWORD
Value data – 1Hive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PackagePointAndPrint\ListofServers
Value name – YOURPRINTSERVERNAME01; YOURPRINTSERVERNAME02
Value Type – REG_SZ
Value data – YOURPRINTSERVERNAME01@keyman .COM; YOURPRINTSERVERNAME02@keyman .COMHive - HKEY_LOCAL_MACHINE
Key path - SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Value name – RestrictDriverInstallationToAdministrators
Value Type – REG_DWORD
Value data – 0