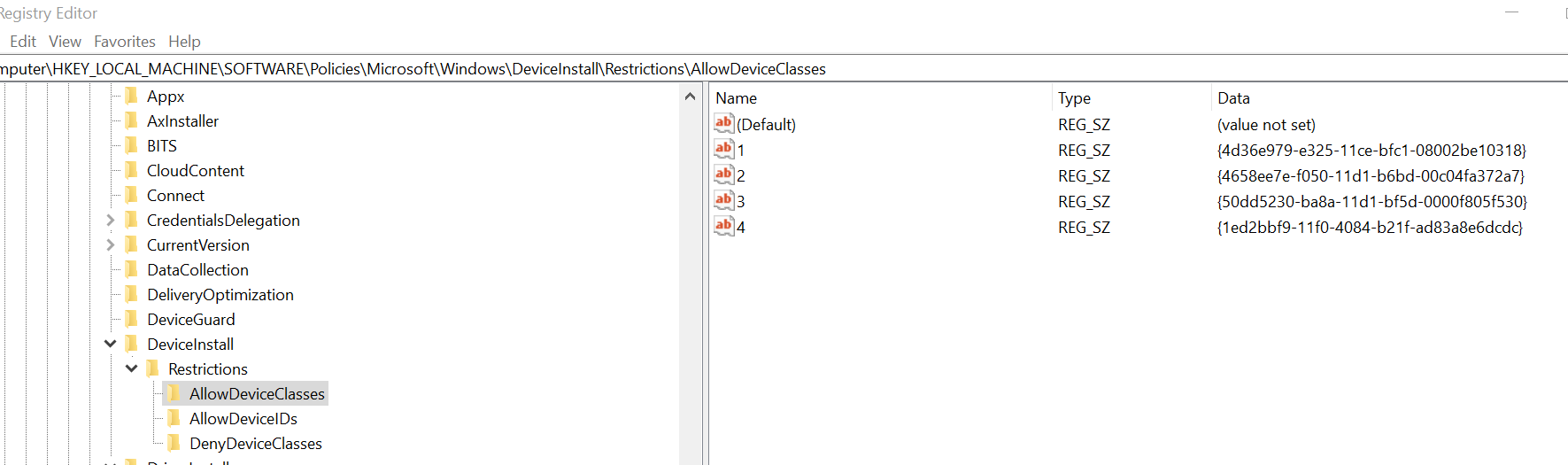
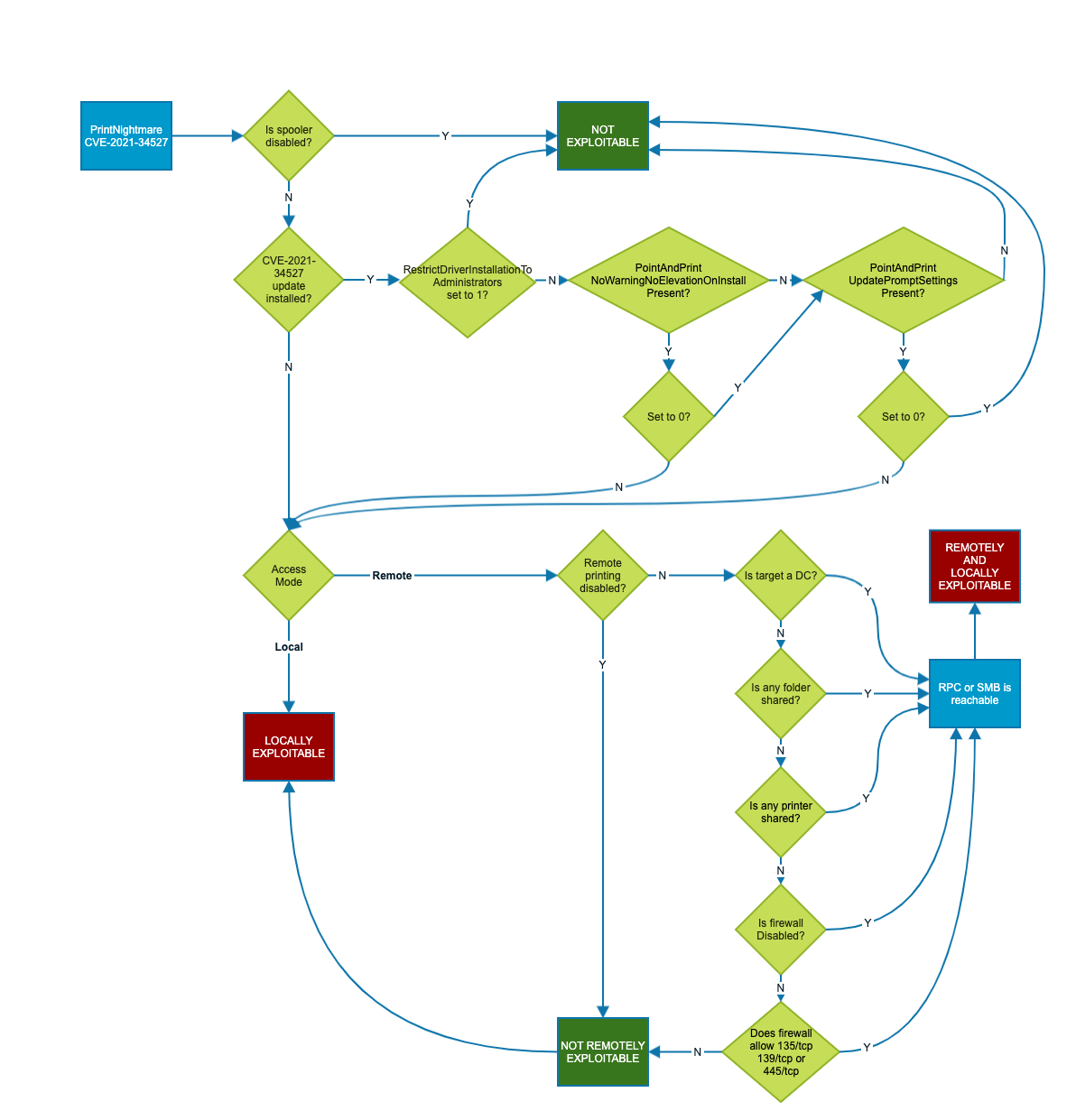
Those CU are real mess....
Since months now we are strungling by uninstall all CU for servers since the 21-07 because each time it breaks printing on rds / print servers.
We tried all solutions with the point and print restrictions, registry keys, it doesnt work, the only solution for us is to uninstall the cumulative updates for servers.
But the problem is that nexts CUs applies the same things, so for now we had to stop CU since July, which is not secured at all for long time.
When the CU are installed, the problems are :
- The printers are not anymore deployed with GPO
- We cant manage printers anymore, bugs while adding/removing printers
- Sometimes printers are deployed duplicated like this : PRINT1 and PRINT1.domain.local with nothing inside.
- Beside GPO failing, we cant add printer manually fromt print server. error when installing
We have those issues randomly on severals clients sites, the only solution that works is to uninstall the CU on the print server and the TS.
We have an IT assets management tool, so we are able to prevent installation of specific updates such as the CUs, but we cant continue like this.
Printers are up to date with very last drivers, but it doesnt help at all.
I'm sorry to bother but the point and print restriction gpo solution doesnt work also.
Does anyone knows another way to be protected, updated and PRINTERS WORKS normally ?