Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Effective May 1, 2025, Azure AD B2C will no longer be available to purchase for new customers. Learn more in our FAQ.
With Azure Active Directory B2C (Azure AD B2C) and solutions from software-vendor partners, customers can enable end-user identity verification and proofing for account registration. Identity verification and proofing can check documents, knowledge-based information, and liveness.
Architecture diagram
The following architecture diagram illustrates the verification and proofing flow.
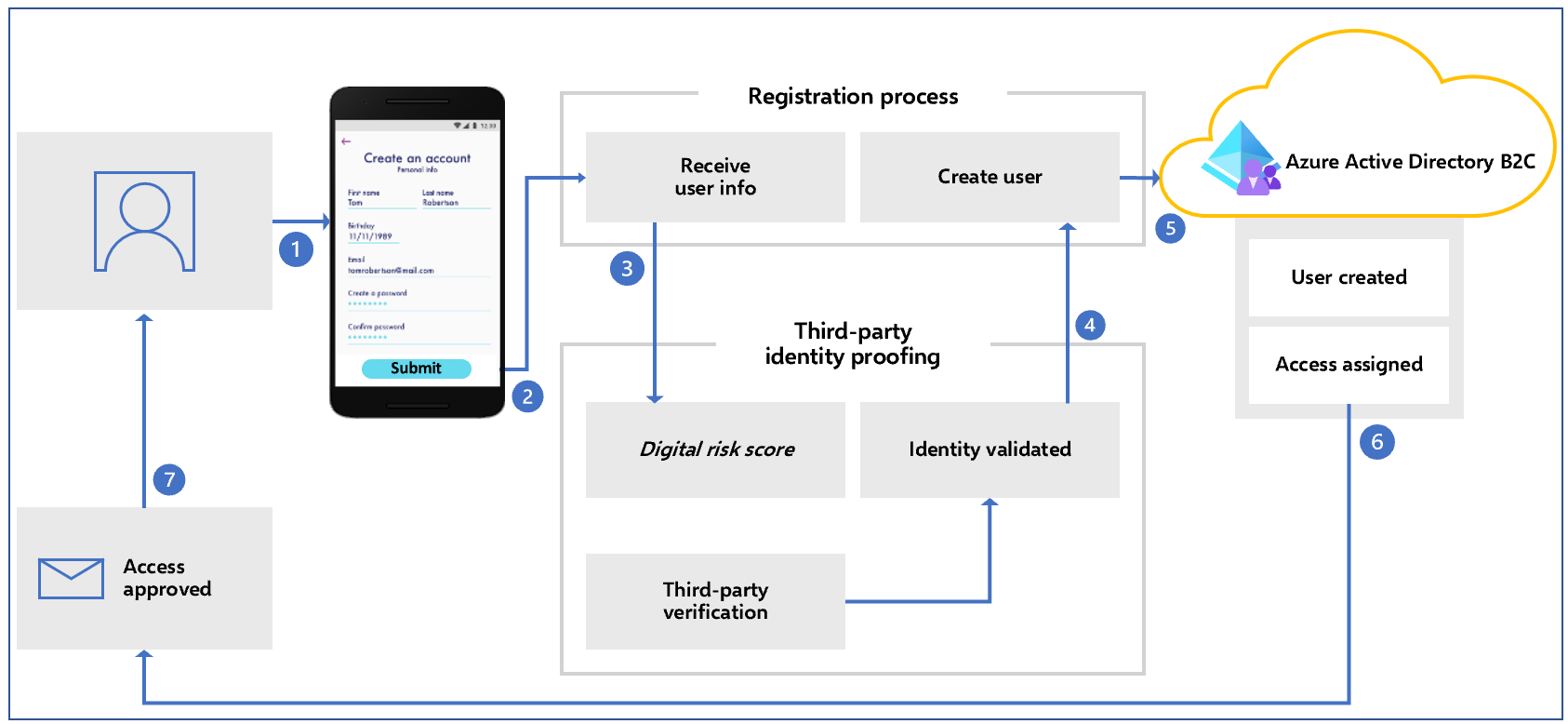
- User begins registration with a device.
- User enters information.
- Digital-risk score is assessed, then third-party identity proofing and identity validation occurs.
- Identity is validated or rejected.
- User attributes are passed to Azure Active Directory B2C.
- If user verification is successful, a user account is created in Azure AD B2C during sign-in.
- Based on the verification result, the user receives an access-approved or -denied message.
Software vendors and integration documentation
Microsoft partners with independent software vendors (ISVs). Use the following table to locate an ISV and related integration documentation.
| ISV logo | ISV link and description | Integration documentation |
|---|---|---|
 |
Deduce: Identity verification and proofing provider that helps stop account takeover and registration fraud. Use it to combat identity fraud and create a trusted user experience. | Configure Azure AD B2C with Deduce to combat identity fraud and create a trusted user experience |
 |
Bluink, Ltd.: eID-Me is an identity verification and decentralized digital identity solution for Canadian citizens. Use it to meet Identity Assurance Level (IAL) 2 and Know Your Customer (KYC) requirements. | Configure eID-Me with Azure AD B2C for identity verification |
 |
Experian Information Solutions, Inc.: Identity verification and proofing provider with solutions that perform risk assessments based on user attributes. | Tutorial: Configure Experian with Azure AD B2C |
 |
IDology, a GBG company: Identity verification and proofing provider with ID verification, fraud prevention, and compliance solutions. | Tutorial for configuring IDology with Azure AD B2C |
 |
Jumio: Identify verification service with products for real-time, automated ID verification. | Tutorial for configuring Jumio with Azure AD B2C |
 |
LexisNexis Risk Solutions Group: Profiling and identity validation provider that verifies user identification and provides risk assessment based on user devices. See, ThreatMetrix. | Tutorial for configuring LexisNexis with Azure AD B2C |
 |
Onfido: Document ID and facial biometrics verification solutions to meet Know Your Customer (KYC) and identity requirements. | Tutorial for configuring Onfido with Azure AD B2C |
Resources
- Azure AD B2C custom policy overview
- Tutorial: Create user flows and custom policies in Azure Active Directory B2C
Next steps
Select and contact a partner from the previous table to get started on solution integration with Azure AD B2C. The partners have similar processes to contact them for a product demo.