Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The most widely adopted industry standard for the transmission of threat intelligence is a combination of the STIX data format and the TAXII protocol. If your organization receives threat indicators from solutions that support the current STIX/TAXII version (2.0 or 2.1), you can use the Threat Intelligence - TAXII data connector to bring your threat indicators into Microsoft Sentinel. This connector enables a built-in TAXII client in Microsoft Sentinel to import threat intelligence from TAXII 2.x servers.
To import STIX-formatted threat indicators to Microsoft Sentinel from a TAXII server, you must get the TAXII server API root and collection ID. Then you enable the Threat Intelligence - TAXII data connector in Microsoft Sentinel.
Learn more about threat intelligence in Microsoft Sentinel, and specifically about the TAXII threat intelligence feeds that you can integrate with Microsoft Sentinel.
Note
For information about feature availability in US Government clouds, see the Microsoft Sentinel tables in Cloud feature availability for US Government customers.
For more information, see Connect your threat intelligence platform (TIP) to Microsoft Sentinel.
Important
Microsoft Sentinel is generally available in the Microsoft Defender portal, including for customers without Microsoft Defender XDR or an E5 license.
Starting in July 2026, all customers using Microsoft Sentinel in the Azure portal will be redirected to the Defender portal and will use Microsoft Sentinel in the Defender portal only. Starting in July 2025, many new customers are automatically onboarded and redirected to the Defender portal.
If you're still using Microsoft Sentinel in the Azure portal, we recommend that you start planning your transition to the Defender portal to ensure a smooth transition and take full advantage of the unified security operations experience offered by Microsoft Defender. For more information, see It’s Time to Move: Retiring Microsoft Sentinel’s Azure portal for greater security.
Prerequisites
- To install, update, and delete standalone content or solutions in the Content hub, you need the Microsoft Sentinel Contributor role at the resource group level.
- You must have read and write permissions to the Microsoft Sentinel workspace to store your threat indicators.
- You must have a TAXII 2.0 or TAXII 2.1 API root URI and collection ID.
Get the TAXII server API root and collection ID
TAXII 2.x servers advertise API roots, which are URLs that host collections of threat intelligence. You can usually find the API root and the collection ID in the documentation pages of the threat intelligence provider that hosts the TAXII server.
Note
In some cases, the provider only advertises a URL called a discovery endpoint. You can use the cURL utility to browse the discovery endpoint and request the API root.
Install the Threat Intelligence solution in Microsoft Sentinel
To import threat indicators into Microsoft Sentinel from a TAXII server, follow these steps:
For Microsoft Sentinel in the Azure portal, under Content management, select Content hub.
For Microsoft Sentinel in the Defender portal, select Microsoft Sentinel > Content management > Content hub.
Find and select the Threat Intelligence solution.
Select the
 Install/Update button.
Install/Update button.
For more information about how to manage the solution components, see Discover and deploy out-of-the-box content.
Enable the Threat Intelligence - TAXII data connector
To configure the TAXII data connector, select the Data connectors menu.
Find and select the Threat Intelligence - TAXII data connector, and then select Open connector page.
Enter a name for this TAXII server collection in the Friendly name text box. Fill in the text boxes for API root URL, Collection ID, Username (if necessary), and Password (if necessary). Choose the group of indicators and the polling frequency you want. Select Add.
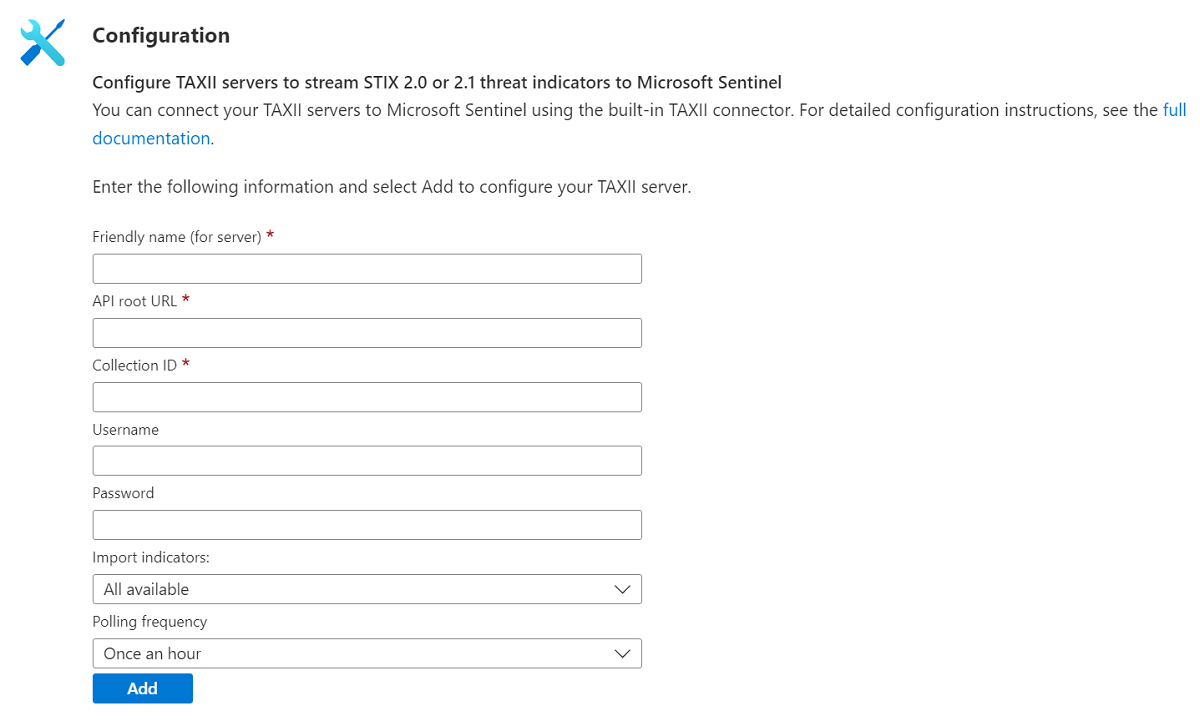
You should receive confirmation that a connection to the TAXII server was established successfully. Repeat the last step as many times as you want to connect to multiple collections from one or more TAXII servers.
Within a few minutes, threat indicators should begin flowing into this Microsoft Sentinel workspace. Find the new indicators on the Threat intelligence pane. You can access it from the Microsoft Sentinel menu.
IP allowlisting for the Microsoft Sentinel TAXII client
Some TAXII servers, like FS-ISAC, have a requirement to keep the IP addresses of the Microsoft Sentinel TAXII client on the allowlist. Most TAXII servers don't have this requirement.
When relevant, the following IP addresses are the addresses to include in your allowlist:
- 20.193.17.32
- 20.197.219.106
- 20.48.128.36
- 20.199.186.58
- 40.80.86.109
- 52.158.170.36
- 20.52.212.85
- 52.251.70.29
- 20.74.12.78
- 20.194.150.139
- 20.194.17.254
- 51.13.75.153
- 102.133.139.160
- 20.197.113.87
- 40.123.207.43
- 51.11.168.197
- 20.71.8.176
- 40.64.106.65
Related content
In this article, you learned how to connect Microsoft Sentinel to threat intelligence feeds by using the TAXII protocol. To learn more about Microsoft Sentinel, see the following articles:
- Learn how to get visibility into your data and potential threats.
- Get started detecting threats with Microsoft Sentinel.
