Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article lists recent features added for Microsoft Sentinel, and new features in related services that provide an enhanced user experience in Microsoft Sentinel. For new features related to unified security operations in the Defender portal, see the What's new for unified security operations?
The listed features were released in the last six months. For information about earlier features delivered, see our Tech Community blogs.
Note
For information about feature availability in US Government clouds, see the Microsoft Sentinel tables in Cloud feature availability for US Government customers.
July 2025
- For new customers only: Automatic onboarding and redirection to the Microsoft Defender portal
- No limit on the number of workspaces you can onboard to the Defender portal
- Microsoft Sentinel in the Azure portal to be retired July 2026
For new customers only: Automatic onboarding and redirection to the Microsoft Defender portal
For this update, new Microsoft Sentinel customers are customers who are onboarding the first workspace in their tenant to Microsoft Sentinel on or after July 1, 2025.
Starting July 1, 2025, such new customers who have the permissions of a subscription Owner or a User access administrator, and are also not Azure Lighthouse-delegated users, have their workspaces automatically onboarded to the Defender portal together with onboarding to Microsoft Sentinel. Users of such workspaces, who also aren't Azure Lighthouse-delegated users, see links in Microsoft Sentinel in the Azure portal that redirect them to the Defender portal. Such users use Microsoft Sentinel in the Defender portal only.

New customers who don't have relevant permissions aren't automatically onboarded to the Defender portal, but they do still see redirection links in the Azure portal, together with prompts to have a user with relevant permissions manually onboard the workspace to the Defender portal.
This change streamlines the onboarding process and ensures that new customers can immediately take advantage of unified security operations capabilities without the extra step of manually onboarding their workspaces.
For more information, see:
- Onboard Microsoft Sentinel
- Microsoft Sentinel in the Microsoft Defender portal
- Changes for new customers starting July 2025
No limit on the number of workspaces you can onboard to the Defender portal
There is no longer any limit to the number of workspaces you can onboard to the Defender portal.
Limitations still apply to the number of workspaces you can include in a Log Analytics query, and in the number of workspaces you can or should include in a scheduled analytics rule.
For more information, see:
- Connect Microsoft Sentinel to the Microsoft Defender portal
- Multiple Microsoft Sentinel workspaces in the Defender portal
- Extend Microsoft Sentinel across workspaces and tenants
Microsoft Sentinel in the Azure portal to be retired July 2026
Microsoft Sentinel is generally available in the Microsoft Defender portal, including for customers without Microsoft Defender XDR or an E5 license. This means that you can use Microsoft Sentinel in the Defender portal even if you aren't using other Microsoft Defender services.
Starting in July 2026, Microsoft Sentinel will be supported in the Defender portal only, and any remaining customers using the Azure portal will be automatically redirected.
If you're currently using Microsoft Sentinel in the Azure portal, we recommend that you start planning your transition to the Defender portal now to ensure a smooth transition and take full advantage of the unified security operations experience offered by Microsoft Defender.
For more information, see:
- Microsoft Sentinel in the Microsoft Defender portal
- Transition your Microsoft Sentinel environment to the Defender portal
- Planning your move to Microsoft Defender portal for all Microsoft Sentinel customers (blog)
June 2025
- Microsoft Sentinel Codeless Connector Platform (CCP) renamed to Codeless Connector Framework (CCF)
- Consolidated Microsoft Sentinel data connector reference
- Summary rule templates now in public preview
Codeless Connector Platform (CCP) renamed to Codeless Connector Framework (CCF)
The Microsoft Sentinel Codeless Connector Platform (CCP) has been renamed to Codeless Connector Framework (CCF). The new name reflects the platform's evolution and avoids confusion with other platform-oriented services, while still providing the same ease of use and flexibility that users have come to expect.
For more information, see Create a codeless connector for Microsoft Sentinel.
Consolidated Microsoft Sentinel data connector reference
We've consolidated the connector reference documentation, merging the separate connector articles into a single, comprehensive reference table.
You can find the new connector reference at Microsoft Sentinel data connectors. For more information, see Create a codeless connector and Unlock the potential of Microsoft Sentinel’s Codeless Connector Framework and do more with Microsoft Sentinel faster.
Summary rule templates now in public preview
You can now use summary rule templates to deploy pre-built summary rules tailored to common security scenarios. These templates help you aggregate and analyze large datasets efficiently, don't require deep expertise, reduce setup time, and ensure best practices. For more information, see Aggregate Microsoft Sentinel data with summary rules (Preview).
May 2025
- All Microsoft Sentinel use cases generally available in the Defender portal
- Unified IdentityInfo table
- Additions to SOC optimization support (Preview)
All Microsoft Sentinel use cases generally available in the Defender portal
All Microsoft Sentinel use cases that are in general availability, including multitenant and multi-workspace capabilities and support for all government and commercial clouds, are now also supported for general availability in the Defender portal.
We recommend that you onboard your workspaces to the Defender portal to take advantage of unified security operations. For more information, see:
For more information, see:
- The Best of Microsoft Sentinel - now in Microsoft Defender (blog)
- Microsoft Sentinel in the Microsoft Defender portal
- Transition your Microsoft Sentinel environment to the Defender portal
Unified IdentityInfo table
Customers of Microsoft Sentinel in the Defender portal who have enabled UEBA can now take advantage of a new version of the IdentityInfo table, located in the Defender portal's Advanced hunting section, that includes the largest possible set of fields common to both the Defender and Azure portals. This unified table helps enrich your security investigations across the entire Defender portal.
For more information, see IdentityInfo table.
Additions to SOC optimization support (Preview)
SOC optimization support for:
- AI MITRE ATT&CK tagging recommendations (Preview): Uses artificial intelligence to suggest tagging security detections with MITRE ATT&CK tactics and techniques.
- Risk-based recommendations (Preview): Recommends implementing controls to address coverage gaps linked to use cases that may result in business risks or financial losses, including operational, financial, reputational, compliance, and legal risks.
For more information, see SOC optimization reference.
April 2025
- Microsoft Sentinel solution for Microsoft Business Apps generally available in the Azure portal
- Security Copilot generates incident summaries in Microsoft Sentinel in the Azure portal (Preview)
- Multi workspace and multitenant support for Microsoft Sentinel in the Defender portal (Preview)
- Microsoft Sentinel now ingests all STIX objects and indicators into new threat intelligence tables (Preview)
- SOC optimization support for unused columns (Preview)
Microsoft Sentinel solution for Microsoft Business Apps generally available in the Azure portal
The Microsoft Sentinel solution for Microsoft Business Apps is now generally available in the Azure portal.
Security Copilot generates incident summaries in Microsoft Sentinel in the Azure portal (Preview)
Microsoft Sentinel in the Azure portal now features (in Preview) incident summaries generated by Security Copilot, bringing it in line with the Defender portal. These summaries give your security analysts the up-front information they need to quickly understand, triage, and start investigating developing incidents.
For more information, see Summarize Microsoft Sentinel incidents with Security Copilot.
Multi workspace and multitenant support for Microsoft Sentinel in the Defender portal (Preview)
For preview, in the Defender portal, connect to one primary workspace and multiple secondary workspaces for Microsoft Sentinel. If you onboard Microsoft Sentinel with Defender XDR, a primary workspace's alerts are correlated with Defender XDR data. So incidents include alerts from Microsoft Sentinel's primary workspace and Defender XDR. All other onboarded workspaces are considered secondary workspaces. Incidents are created based on the workspace’s data and won't include Defender XDR data.
- If you plan to use Microsoft Sentinel in the Defender portal without Defender XDR, you can manage multiple workspaces. But, the primary workspace doesn't include Defender XDR data and you won't have access to Defender XDR capabilities.
- If you're working with multiple tenants and multiple workspaces per tenant, you can also use Microsoft Defender multitenant management to view incidents and alerts, and to hunt for data in Advanced hunting, across both multiple workspaces and tenants.
For more information, see the following articles:
- Multiple Microsoft Sentinel workspaces in the Defender portal
- Connect Microsoft Sentinel to the Microsoft Defender portal
- Microsoft Defender multitenant management
- View and manage incidents and alerts in Microsoft Defender multitenant management
- Advanced hunting in Microsoft Defender multitenant management
Microsoft Sentinel now ingests all STIX objects and indicators into new threat intelligence tables (Preview)
Microsoft Sentinel now ingests STIX objects and indicators into the new threat intelligence tables, ThreatIntelIndicators and ThreatIntelObjects. The new tables support the new STIX 2.1 schema, which lets you ingest and query various threat intelligence objects, including identity, attack-pattern, threat-actor, and relationship.
Microsoft Sentinel will ingest all threat intelligence into the new ThreatIntelIndicators and ThreatIntelObjects tables, while continuing to ingest the same data into the legacy ThreatIntelligenceIndicator table until July 31, 2025.
Be sure to update your custom queries, analytics and detection rules, workbooks, and automation to use the new tables by July 31, 2025. After this date, Microsoft Sentinel will stop ingesting data to the legacy ThreatIntelligenceIndicator table. We're updating all out-of-the-box threat intelligence solutions in Content hub to leverage the new tables.
For more information, see the following articles:
- Threat intelligence in Microsoft Sentinel
- Work with STIX objects and indicators to enhance threat intelligence and threat hunting in Microsoft Sentinel (Preview)
SOC optimization support for unused columns (Preview)
To optimize your cost/security value ratio, SOC optimization surfaces hardly used data connectors or tables. SOC optimization now surfaces unused columns in your tables. For more information, see SOC optimization reference of recommendations.
March 2025
Agentless connection to SAP now in public preview
The Microsoft Sentinel agentless data connector for SAP and related security content is now included, as public preview, in the solution for SAP applications. This update also includes the following enhancements for the agentless data connector:
- Enhanced instructions in the portal for deploying and configuring the data connector. External documentation is updated to rely on the instructions in the portal.
- More data ingested, such as Change Docs logs and User Master data.
- Optional parameters to Customize data connector behavior (optional).
- A new tool to verify system prerequisites and compatibility, recommended both before deploying and when troubleshooting.
For more information, see:
- Microsoft Sentinel solution for SAP applications: Deployment overview
- Microsoft Sentinel solution for SAP applications - functions reference
- Troubleshooting your Microsoft Sentinel solution for SAP applications deployment
January 2025
- Optimize threat intelligence feeds with ingestion rules
- Matching analytics rule now generally available (GA)
- Threat intelligence management interface updated
- Unlock advanced hunting with new STIX objects by opting in to new threat intelligence tables
- Threat intelligence upload API now supports more STIX objects
- Microsoft Defender Threat Intelligence data connectors now generally available (GA)
- Bicep file support for repositories (Preview)
- SOC optimization updates for unified coverage management
- View granular solution content in the Microsoft Sentinel content hub
Optimize threat intelligence feeds with ingestion rules
Optimize threat intelligence feeds by filtering and enhancing objects before they're delivered to your workspace. Ingestion rules update threat intel object attributes, or filter objects out all together. Check out the blog announcement here!
For more information, see Understand threat intelligence ingestion rules.
Matching analytics rule now generally available (GA)
Microsoft provides access to its premium threat intelligence through the Defender Threat Intelligence analytics rule which is now generally available (GA). For more information on how to take advantage of this rule, which generates high-fidelity alerts and incidents, see Use matching analytics to detect threats.
Threat intelligence management interface has moved
Threat intelligence for Microsoft Sentinel in the Defender portal has changed! We've renamed the page Intel management and moved it with other threat intelligence workflows. There's no change for customers using Microsoft Sentinel in the Azure experience.

Enhancements to threat intelligence capabilities are available for customers using both Microsoft Sentinel experiences. The management interface streamlines the creation and curation of threat intel with these key features:
- Define relationships as you create new STIX objects.
- Curate existing threat intelligence with the new relationship builder.
- Create multiple objects quickly by copying common metadata from a new or existing TI object using a duplication feature.
- Use advanced search to sort and filter your threat intelligence objects without even writing a Log Analytics query.
For more information, see the following articles:
- New STIX objects in Microsoft Sentinel
- Understand threat intelligence
- Uncover adversaries with threat intelligence in the Defender portal
Unlock advanced hunting with new STIX objects by opting in to new threat intelligence tables
Tables supporting the new STIX object schema aren't available publicly. In order to query threat intelligence for STIX objects with KQL and unlock the hunting model that uses them, request to opt in with this form. Ingest your threat intelligence into the new tables, ThreatIntelIndicators and ThreatIntelObjects alongside with or instead of the current table, ThreatIntelligenceIndicator, with this opt-in process.
For more information, see the blog announcement New STIX objects in Microsoft Sentinel.
Threat intelligence upload API now supports more STIX objects
Make the most of your threat intelligence platforms when you connect them to Microsoft Sentinel with the upload API. Now you can ingest more objects than just indicators, reflecting the varied threat intelligence available. The upload API supports the following STIX objects:
indicatorattack-patternidentitythreat-actorrelationship
For more information, see the following articles:
- Connect your threat intelligence platform with the upload API (Preview)
- Import threat intelligence to Microsoft Sentinel with the upload API (Preview)
- New STIX objects in Microsoft Sentinel
Microsoft Defender Threat Intelligence data connectors now generally available (GA)
Both premium and standard Microsoft Defender Threat Intelligence data connectors are now generally available (GA) in content hub. For more information, see the following articles:
- Explore Defender Threat Intelligence licenses
- Enable the Microsoft Defender Threat Intelligence data connector
Bicep file support for repositories (Preview)
Use Bicep files alongside or as a replacement of ARM JSON templates in Microsoft Sentinel repositories. Bicep provides an intuitive way to create templates of Azure resources and Microsoft Sentinel content items. Not only is it easier to develop new content items, Bicep makes reviewing and updating content easier for anyone that's a part of the continuous integration and delivery of your Microsoft Sentinel content.
For more information, see Plan your repository content.
SOC optimization updates for unified coverage management
In workspaces onboarded to the Defender portal, SOC optimizations now support both SIEM and XDR data, with detection coverage from across Microsoft Defender services.
In the Defender portal, the SOC optimizations and MITRE ATT&CK pages also now provide extra functionality for threat-based coverage optimizations to help you understand the impact of the recommendations on your environment and help you prioritize which to implement first.
Enhancements include:
| Area | Details |
|---|---|
| SOC optimizations Overview page | - A High, Medium, or Low score for your current detection coverage. This sort of scoring can help you decide which recommendations to prioritize at a glance. - An indication of the number of active Microsoft Defender products (services) out of all available products. This helps you understand whether there's a whole product that you're missing in your environment. |
| Optimization details side pane, shown when you drill down to a specific optimization |
- Detailed coverage analysis, including the number of user-defined detections, response actions, and products you have active. - Detailed spider charts that show your coverage across different threat categories, for both user-defined and out-of-the-box detections. - An option to jump to the specific threat scenario in the MITRE ATT&CK page instead of viewing MITRE ATT&CK coverage only in the side pane. - An option to View full threat scenario to drill down to even further details about the security products and detections available to provide security coverage in your environment. |
| MITRE ATT&CK page | - A new toggle to view coverage by threat scenario. If you've jumped to the MITRE ATT&CK page from either a recommendation details side pane or from the View full threat scenario page, the MITRE ATT&CK page is pre-filtered for your threat scenario. - The technique details pane, shown on the side when you select a specific MITRE ATT&CK technique, now shows the number of active detections out of all available detections for that technique. |
For more information, see Optimize your security operations and Understand security coverage by the MITRE ATT&CK framework.
View granular solution content in the Microsoft Sentinel content hub
Now you can view the individual content available in a specific solution directly from the Content hub, even before you've installed the solution. This new visibility helps you understand the content available to you, and more easily identify, plan, and install the specific solutions you need.
Expand each solution in the Content hub to view included security content. For example:
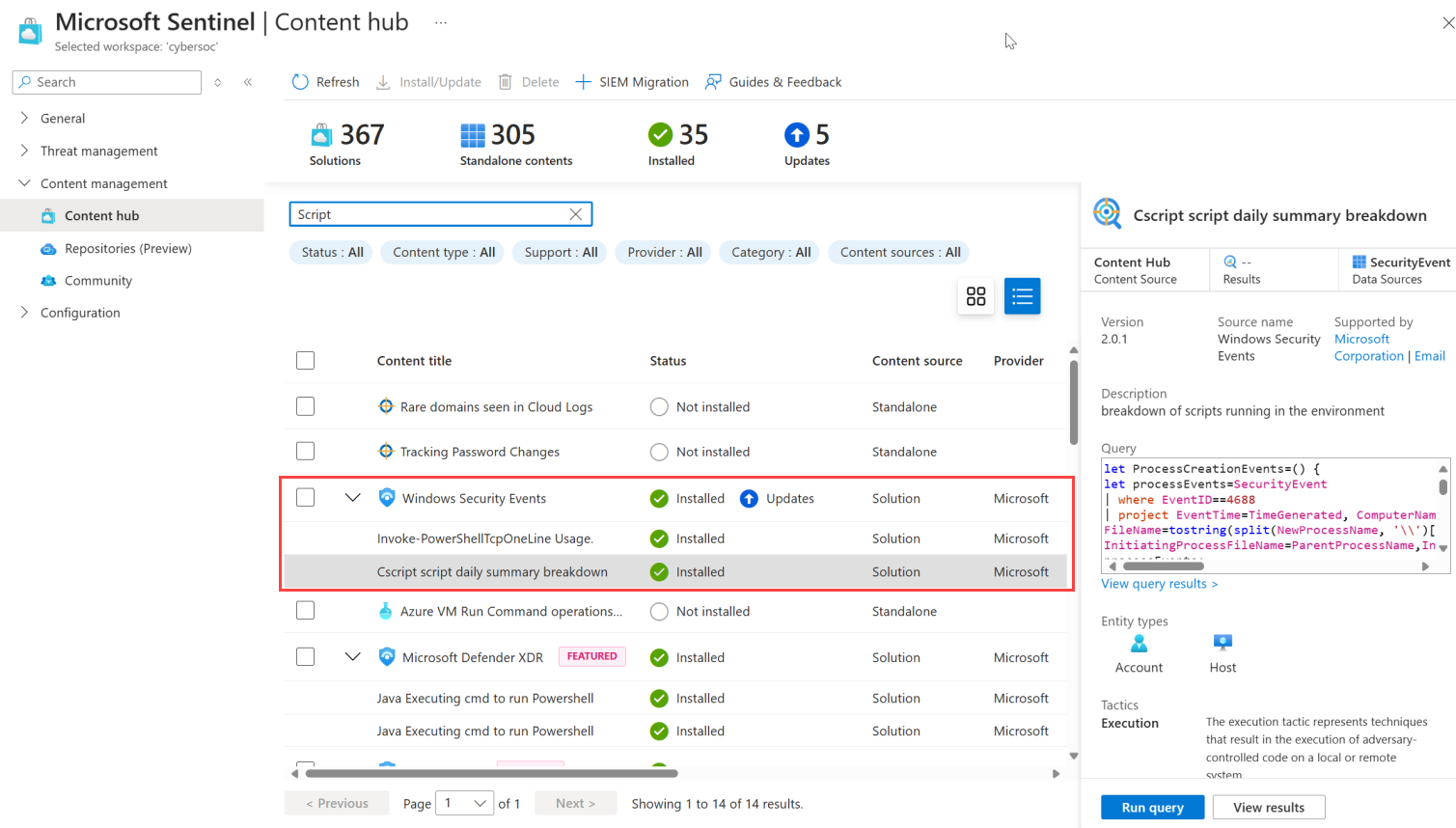
The granular solution content updates also include a generative AI-based search engine that helps you run more robust searches, diving deep into the solution content and returning results for similar terms.
For more information, see Discover content.