Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Devices that are configured for IPv6-only traffic are not supported.
Note
To use the proxy correctly, configure these two different proxy settings in Defender for Endpoint:
Depending on the operating system, the proxy to be used for Microsoft Defender for Endpoint can be configured automatically. You can use autodiscovery, an autoconfig file, or a method statically specific to Defender for Endpoint services running on the device.
- For Windows devices, see Configure device proxy and Internet connectivity settings (in this article).
- For Linux devices, see Configure Microsoft Defender for Endpoint on Linux for static proxy discovery.
- For macOS devices, see Microsoft Defender for Endpoint on macOS.
The Defender for Endpoint sensor requires Microsoft Windows HTTP (WinHTTP) to report sensor data and communicate with the Defender for Endpoint service. The embedded Defender for Endpoint sensor runs in system context using the LocalSystem account.
Tip
If you use forward proxies as a gateway to the Internet, you can use network protection to investigate connection events that occur behind forward proxies.
The WinHTTP configuration setting is independent of the Windows Internet (WinINet) browsing proxy settings (see WinINet vs. WinHTTP). It can only discover a proxy server by using the following discovery methods:
Autodiscovery methods:
Transparent proxy
Web Proxy Autodiscovery Protocol (WPAD)
Note
If you're using Transparent proxy or WPAD in your network topology, you don't need special configuration settings.
Manual static proxy configuration:
Registry-based configuration
WinHTTP configured using netsh command: Suitable only for desktops in a stable topology (for example: a desktop in a corporate network behind the same proxy)
Note
Microsoft Defender Antivirus and EDR proxies can be set independently. In the sections that follow, be aware of those distinctions.
Configure the proxy server manually using a registry-based static proxy setting
Configure a registry-based static proxy for Defender for Endpoint detection and response (EDR) sensor to report diagnostic data and communicate with Defender for Endpoint services if a computer isn't permitted to directly connect to the Internet.
Note
Always ensure to apply the latest updates to ensure successful connectivity to Defender for Endpoint services.
The static proxy settings are configurable through group policy (GP), both settings under group policy values should be configured. The group policy is available in Administrative Templates.
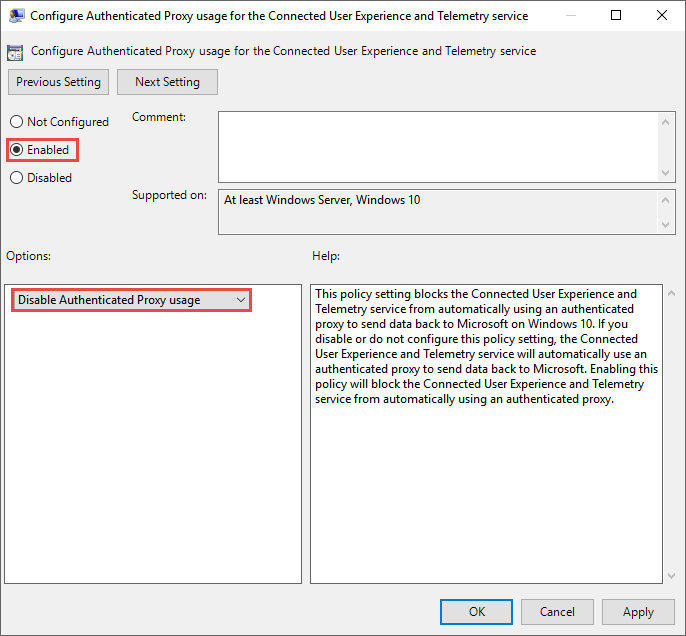
Administrative Templates > Windows Components > Data Collection and Preview Builds > Configure Authenticated Proxy usage for the Connected User Experience and Telemetry Service.
Set it to Enabled and select Disable Authenticated Proxy usage.
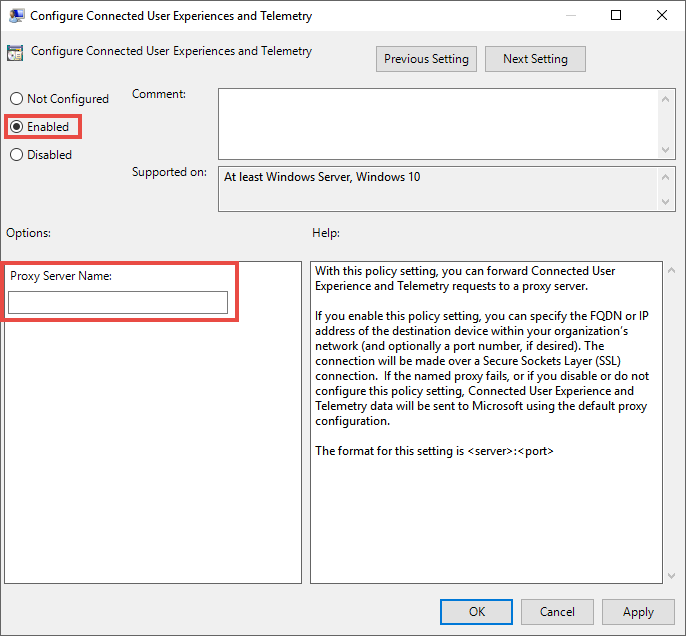
Administrative Templates > Windows Components > Data Collection and Preview Builds > Configure connected user experiences and telemetry:
Enter the proxy information.
| Group Policy | Registry key | Registry entry | Value |
|---|---|---|---|
| Configure authenticated proxy usage for the connected user experience and the telemetry service | HKLM\Software\Policies\Microsoft\Windows\DataCollection |
DisableEnterpriseAuthProxy |
1 (REG_DWORD) |
| Configure connected user experiences and telemetry | HKLM\Software\Policies\Microsoft\Windows\DataCollection |
TelemetryProxyServer |
servername:port or ip:port For example: 10.0.0.6:8080 (REG_SZ) |
Note
If you are using TelemetryProxyServer setting on devices that are otherwise completely offline, meaning the operating system is unable to connect for the online certificate revocation list or Windows Update, then you must add the additional registry setting PreferStaticProxyForHttpRequest with a value of 1.
Parent registry path location for PreferStaticProxyForHttpRequest is HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection.
The following command can be used to insert the registry value in the correct location:
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v PreferStaticProxyForHttpRequest /t REG_DWORD /d 1 /f
The registry value mentioned earlier is applicable only starting with MsSense.exe version 10.8210.* and later, or version 10.8049.* and later.
Configure a static proxy for Microsoft Defender Antivirus
Microsoft Defender Antivirus cloud-delivered protection provides near-instant, automated protection against new and emerging threats. Connectivity is required for custom indicators when Microsoft Defender Antivirus is your active anti-malware solution and EDR in block mode, which provides a fallback option when a non-Microsoft solution didn't perform a block.
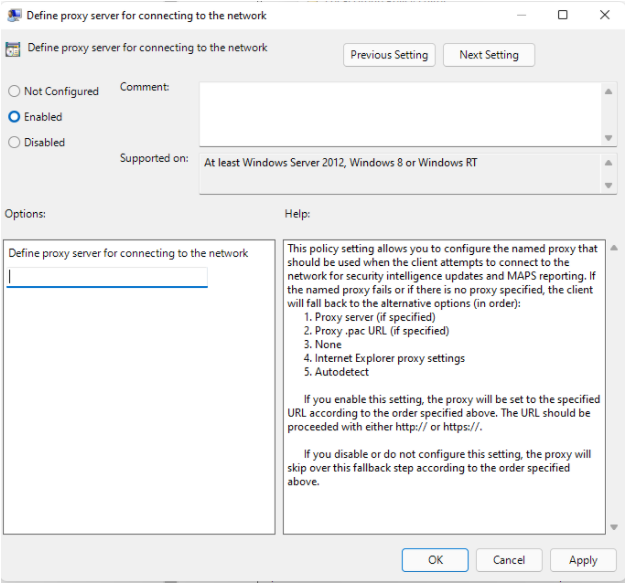
Configure the static proxy using the Group Policy available in Administrative Templates:
Administrative Templates > Windows Components > Microsoft Defender Antivirus > Define proxy server for connecting to the network.
Set it to Enabled and define the proxy server. The URL must have either
http://orhttps://. For supported versions forhttps://, see Manage Microsoft Defender Antivirus updates.Under the registry key
HKLM\Software\Policies\Microsoft\Windows Defender, the policy sets the registry valueProxyServerasREG_SZ.The registry value
ProxyServertakes the following string format:<server name or ip>:<port>For example,
http://10.0.0.6:8080
Note
If you are using static proxy setting on devices that are otherwise completely offline, meaning the operating system is unable to connect for the online certificate revocation list or Windows Update, then it is required to add the additional registry setting SSLOptions with a DWORD value of 2. The parent registry path location for SSLOptions is HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Spynet. For more information about the SSLOptions, see Cloud Protection.
For resiliency purposes and the real-time nature of cloud-delivered protection, Microsoft Defender Antivirus caches the last known working proxy. Ensure your proxy solution does not perform SSL inspection, as that breaks the secure cloud connection.
Microsoft Defender Antivirus doesn't use the static proxy to connect to Windows Update or Microsoft Update for downloading updates. Instead, it uses a system-wide proxy if configured to use Windows Update, or the configured internal update source according to the configured fallback order.
If necessary, you can use Administrative Templates > Windows Components > Microsoft Defender Antivirus > Define proxy auto-config (.pac) for connecting to the network. If you need to set up advanced configurations with multiple proxies, use Administrative Templates > Windows Components > Microsoft Defender Antivirus > Define addresses to bypass proxy server and prevent Microsoft Defender Antivirus from using a proxy server for those destinations.
You can use PowerShell with the Set-MpPreference cmdlet to configure these options:
ProxyBypassProxyPacUrlProxyServer
Configure the proxy server manually using netsh command
Use netsh to configure a system-wide static proxy.
Note
This configuration affects all applications, including Windows services which use WinHTTP with default proxy.
Open an elevated command line:
- Go to Start and type
cmd. - Right-click Command prompt and select Run as administrator.
- Go to Start and type
Enter the following command and press Enter:
netsh winhttp set proxy <proxy>:<port>For example:
netsh winhttp set proxy 10.0.0.6:8080To reset the
winhttpproxy, enter the following command and press Enter:netsh winhttp reset proxy
See Netsh Command Syntax, Contexts, and Formatting to learn more.
Windows devices running the previous MMA-based solution
For devices running Windows 7, Windows 8.1, Windows Server 2008 R2, and servers that aren't upgraded to Unified Agent and use the Microsoft Monitoring Agent (also known as Log Analytics Agent) to connect to the Defender for Endpoint service, you can either use a system-wide proxy setting, or configure the agent to connect through a proxy or a log analytics gateway.
- Configure the agent to use a proxy: Proxy configuration
- Set up Azure Log Analytics (formerly known as OMS Gateway) to act as proxy or hub: Azure Log Analytics Agent
Onboard previous versions of Windows
Next step
STEP 3: Verify client connectivity to Microsoft Defender for Endpoint service URLs
Related articles
- Disconnected environments, proxies, and Microsoft Defender for Endpoint
- Use Group Policy settings to configure and manage Microsoft Defender Antivirus
- Onboard client devices running Windows or macOS
- Troubleshoot Microsoft Defender for Endpoint onboarding issues
- Onboard devices without Internet access to Microsoft Defender for Endpoint
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.