Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Note
Community interest groups have now moved from Yammer to Microsoft Viva Engage. To join a Viva Engage community and take part in the latest discussions, fill out the Request access to Finance and Operations Viva Engage Community form and choose the community you want to join.
This article describes how to access development instances, configure local development virtual machines (VMs), and find important configurations settings for developers and administrators.
Note
- Microsoft Support may provide limited troubleshooting on Tier 1 development environments.
- In certain circumstances, a fresh deploy of a Tier 1 environment may be requested by Microsoft Support to resolve an issue.
- Development environments shouldn't contain business critical data and are considered disposable.
- These environments aren't intended for performance testing.
- Depending on your workload, you may need to choose or adjust the Azure SKU for the selected VM.
- Only 120 environments are support per tenant. We recommend that you limit the number of cloud-hosted environments under a specific tenant to allow enough capacity to be able to deploy sandbox and production environments.
- For cloud-hosted environments older than 6 months, it's advisable to review the supported software list on the Microsoft Dynamics 365 Finance + Operations supported software page.
Definitions
| Term | Definition |
|---|---|
| End user | A user who accesses an instance through the web client. The end user must have Microsoft Microsoft Entra credentials to access an instance and must be provisioned/added as a user of that instance. |
| Developer | A user who develops code through the Microsoft Visual Studio environment. A developer requires Remote Desktop access to development environment (VM). The developer account must be an administrator on the VM. |
Deploy cloud development environments
To deploy a cloud development environment in your Lifecycle Services project:
Create a connection between an Lifecycle Services project and your Azure subscription. You need your Azure subscription ID and authorize the use of the subscription.
Select + under Environments to deploy.
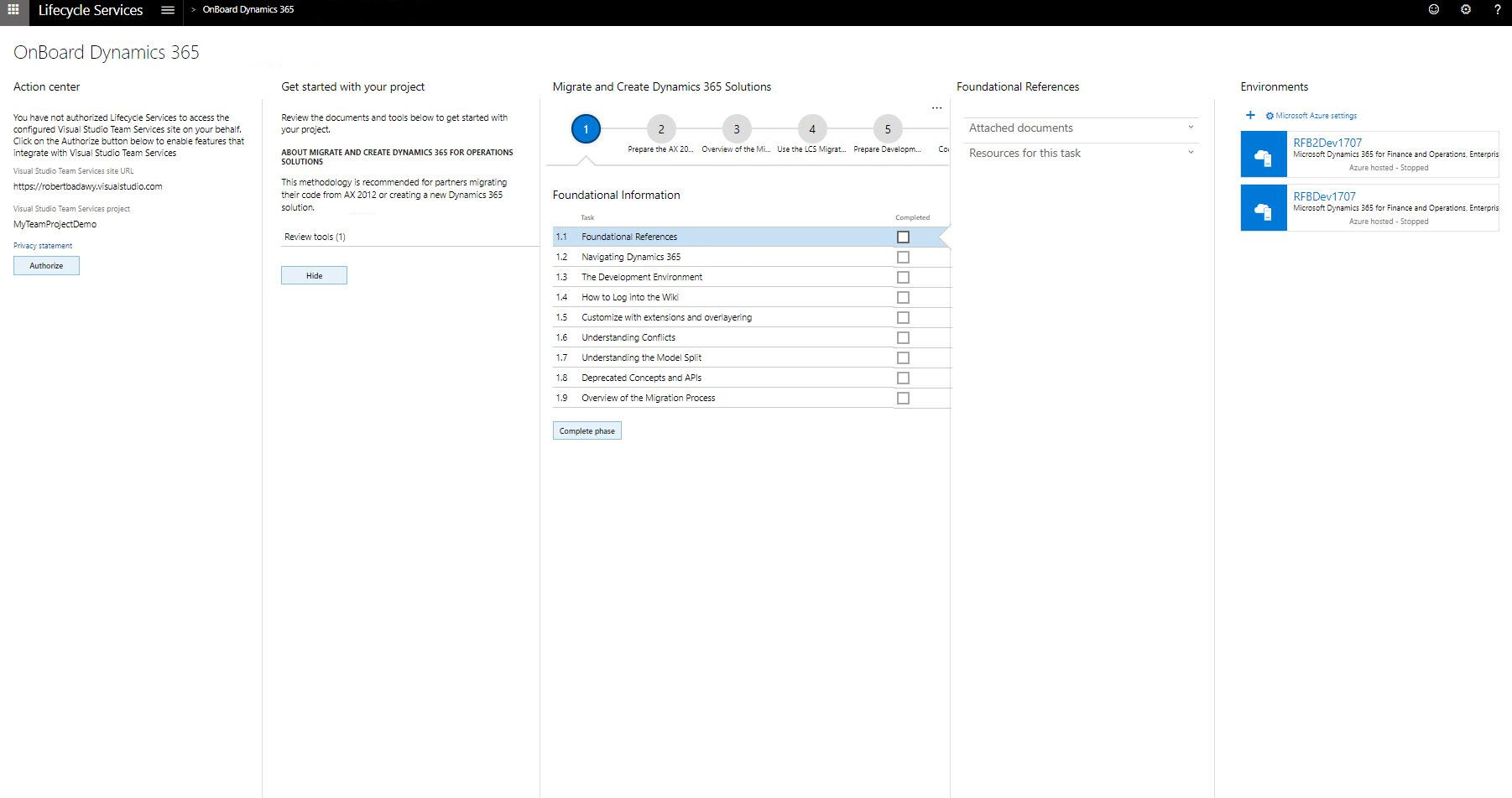
Select an application and platform version.
Select an environment topology. For more information, see Sign up for preview subscriptions.
If you chose a cloud-hosted environment, select which Azure connector you want to use. Then select Deploy.
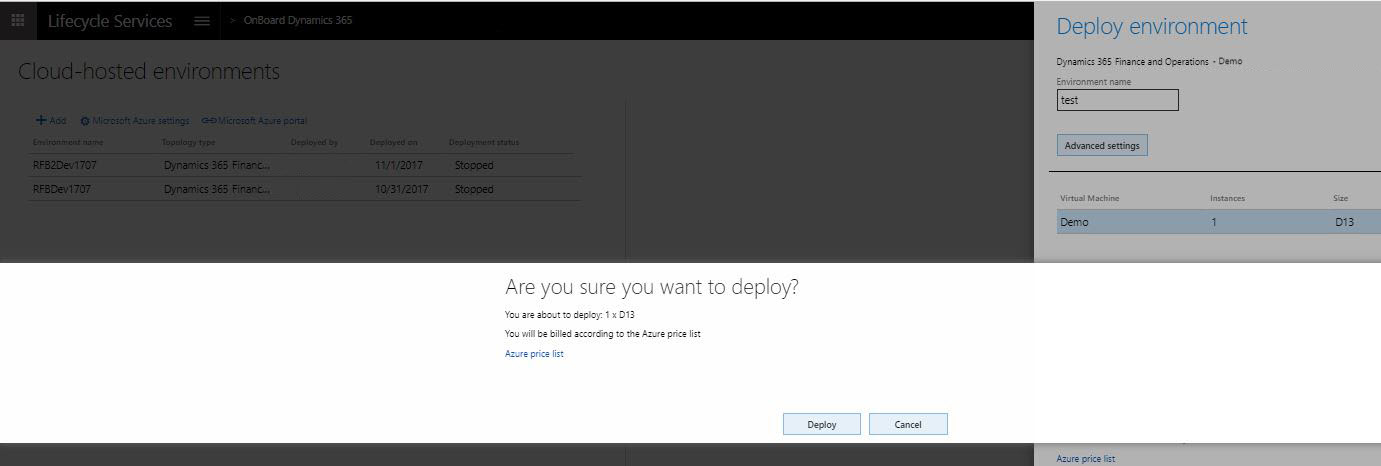

Cloud environment that is provisioned through Lifecycle Services
Note
Copilot and AI agents aren't supported in developer environments that were deployed through Lifecycle Services.
When a cloud environment is provisioned through Lifecycle Services:
- The user who requests the cloud environment is provisioned as the administrator in that environment.
- User accounts are provisioned on the development VM to allow access to the environment using Remote Desktop, these credentials are accessible on the environment page in Lifecycle Services.
Access an instance through a URL
The system can be accessed by end users. The administrator can add users to this system by using the Users page in the instance. These users don't have to be users in Lifecycle Services. You obtain the base URL for the cloud environment from your Lifecycle Services project site.
- Go to your Lifecycle Services project navigation menu, and select Cloud-hosted environments.
- In the environment list section, select the deployed environment.
- When the environment page opens, you can access the application by clicking Login > Log on to finance and operations in the upper-right corner.
- Use valid end user credentials to sign in to the application. If the current Lifecycle Services user is the user who originally deployed the environment, that user is probably a valid end user and the administrator of the application.
- In your browser, make a note of the base URL after you sign in. For example, the base URL might be
https://dynamicsAx7aosContoso.cloud.dynamics.com.
Access the cloud instance through Remote Desktop
Cloud environments can be accessed both as an end user and as a developer. The developer gets access to the system through Remote Desktop credentials. The Remote Desktop credentials are obtained from the environment page on the Lifecycle Services project site (see the illustration earlier in this article).
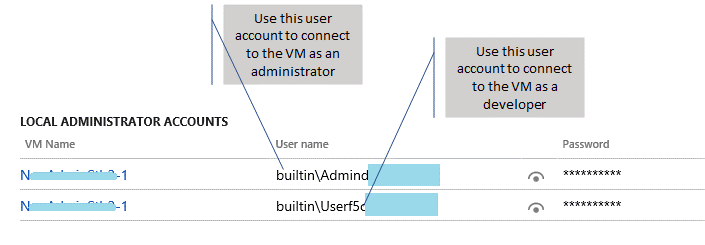
For environments deployed before Platform update 12:
- Click the VM name.
- Use the local administrator user name and password that are shown to connect to the cloud VM through Remote Desktop. You can reveal the password by selecting the show password icon.
For any environments deployed on or after Platform update 12, there are distinct accounts, a developer account, and an admin account.
After you sign in to the environment through Remote Desktop, if you want to access the local application from the browser, use the same base URL that you use to access the application from a remote computer. The previous section explains how to obtain this base URL from Lifecycle Services.
Delete cloud-hosted developer environments
When you're done with the developer environment, or in some cases where troubleshooting an infrastructure issue is too time consuming, you can always delete the environment from Lifecycle Services and create a new one later. To delete a cloud-hosted environment from Lifecycle Services, use the following steps:
- Go to your Lifecycle Services project navigation menu, and select Cloud-hosted environments.
- Highlight the environment that you want to remove and select Deallocate, which power down the machine in your Azure subscription.
- After the deallocation is successful, the environment is in a Deallocated state. You may now use the Delete button to start the deletion process.
You can't delete a cloud-hosted environment if the virtual network (VNET) that was created with it is also being used by other cloud-hosted environments. This scenario isn't common, but in some cases customers want all their developer environments to reuse an existing VNET so that they can share files more easily between them. If you implemented this scenario, you must delete the other environments before you delete the base environment that created the original VNET.
If the delete operation fails, check to see if one of the following issues may have occurred:
- The Azure connector management certificate has expired.
- The Azure subscription has been moved to a different tenant than where it was originally.
- The Azure subscription has been disabled.
- There are Azure policies in your subscription that prevent you from deleting one or more resources in your environment's resource group.
If Lifecycle Services wasn't able to successfully complete the delete operation, the operation is marked as Incomplete. Use the Delete Lifecycle Services metadata button to clean up this environment's metadata from the Lifecycle Services backend systems.
Note
This operation will not try to delete the resources in the Azure subscription. It is the customer's responsibility to manually remove the environment's resource group if it still exists.
You can easily identify the environment’s resource group in the Azure subscription, as it has the same name as the environment in Lifecycle Services.
VM that is running locally
A virtual hard disk (VHD) is made available for download from Lifecycle Services, so that you can set it up on a local machine. This system is intended to be accessed by a developer and is a preconfigured one-box development environment of finance and operations apps. The VHD is available in the Shared Asset library of Lifecycle Services under the asset type Downloadable VHD.
- Go to the Lifecycle Services main page and select Shared asset library or go to Shared Asset Library.
- Select the asset type Downloadable VHD.
- Find the VHD you're looking for based on the desired finance and operations version. The VHD is divided into multiple file parts that you need to download. For example, the asset files that start with "VHD - 10.0.5" are the different files you need in order to install version 10.0.5.
- Download all files (parts) associated with the desired VHD to a local folder.
- After the download is complete, run the executable file that you downloaded, accept the software license agreement, and choose a file path to extract the VHD to. These steps create a local VHD file that you can use to run a local virtual machine.
Configure the VHD for Commerce
Follow the steps in this section if you're also configuring for Commerce.
To use the downloadable VHD for POS customizations, you must also follow this step.
- On the host computer, enable Nested VM support. For more information, see Run Hyper-V in a Virtual Machine with Nested Virtualization.
Running the virtual machine locally
Follow these steps to run the VM from Hyper-V Manager.
To start the VM, select Start.
To open the VM in a window, select Connect.
Select the Ctrl+Alt+Delete button on the toolbar. The VM receives most keyboard commands, but Ctrl+Alt+Delete isn't one of them. Therefore, you must use the button or a menu command.
Sign in to the VM by using the following credentials:
- User name: localadmin
- Password: pass@word1
Tip
You can resize the VM window by changing the screen resolution. Right-click the desktop on the VM, and then click Screen resolution. Select a resolution that works well for your display.
Provision the administrator user. For more information, see the next section.
Start the Batch Manager Service. This step is required if you're running batch jobs or workflows.
- Open a Command Prompt window as an administrator.
- Type net start DynamicsAxBatch, and then press Enter.
You can also start the service from the Services window.
Apply updates as needed.
Commerce configuration
For POS customizations, you must also follow these steps on the guest VM.
- Download and install Microsoft Emulator for Windows 10 Mobile Anniversary Update.
- Start the Hyper-V host service. For more information, see Hyper-V: The Hyper-V Virtual Machine Management service must be running. If errors occur during startup, you can also try to uninstall and reinstall the Hyper-V role on the guest VM.
Provision the administrator user
For developer access, you must be an administrator on the instance. For environments that are provisioned through Lifecycle Services, we encourage you to deploy with the correct user. For more information, see Frequently asked questions. To provision your own credentials as an administrator on a local VM, run the Admin user provisioning tool. On the local VM, a link is provided on the desktop.
- Run the admin user provisioning tool as an administrator (right-click the icon, and then click Run as administrator).
- Enter your email address, and then select Submit.
Note
The Admin user provisioning tool isn't supported in environments that are provisioned through Lifecycle Services. It should be used only on local VMs.
Note
For local VMs that use the virtual hard drive (VHD) that was released for versions 10.0.24 and later, the instructions in Set up the downloadable VHD for first use should be used instead.
Commerce configuration
Follow the steps in this section if you're also configuring for Commerce.
Base URL of the local application
After the user is provisioned as an administrator, that user can access the instance on the computer by navigating to the following base URL: https://usnconeboxax1aos.cloud.onebox.dynamics.com. If you're using version control and plan to connect multiple development VMs to the same Azure DevOps project, rename your local VM. For instructions, see Rename a local development (VHD) environment.
Commerce configuration
The URL of the POS app is https://usnconeboxax1pos.cloud.onebox.dynamics.com/.
The URL of the Cloud POS app is https://usnconeboxax1pos.cloud.onebox.dynamics.com. After you complete the configuration steps, this VM is provisioned with your Microsoft Entra tenant. Your Microsoft Entra admin account is mapped to a cashier worker account in demo data. You can use this cashier account to easily activate a POS device in this environment.
- Cashier user ID: 000160
- Cashier password: 123
- Cashier LE: USRT
- Cashier store: Houston
Location of packages, source code, and other AOS configurations
On a VM, you can find most of the application configuration by opening the web.config file of AOSWebApplication.
Start IIS.
Go to Sites > AOSWebApplication.
Right-click, and then click Explore to open File Explorer.
Open the web.config file in Notepad or another text editor. The following keys are of interest to many developers and administrators:
- Aos.MetadataDirectory – This key points to the location of the packages folder that contains platform and application binaries, and also source code. (Source code is available only in development environments.) Typical values are: c:\packages, c:\AosServicePackagesLocalDirectory, and J:AosServicePackagesLocalDirectory.
- DataAccess.Database – This key holds the name of the database.
- Aos.AppRoot – This key points to the root folder of the Application Object Server (AOS) web application.
Commerce configuration
The software development kit (SDK) is available at C:\RetailSDK. For more information about how to use and customize applications, see the following topics:
Remove preexisting encrypted data from headquarters
If while configuring the shared hardware station on a VHD image you see the following "NoCertificateFoundException" error in the Event Viewer, the Commerce configuration for the VHD environment may require the manual removal of the merchant properties from the deployed environment.
No certificate found for id <id value presented>...
In AOS of your VHD environment, if preloaded values are set in the SECUREMERCHANTPROPERTIES or CONNECTIONSTRING attributes, those values should be cleared from the following tables:
SELECT SECUREMERCHANTPROPERTIES FROM dbo.RETAILHARDWAREPROFILE -- hardware profile form
SELECT SECUREMERCHANTPROPERTIES FROM dbo.RETAILCHANNELPAYMENTCONNECTORLINE -- online stores form
SELECT SECUREMERCHANTPROPERTIES FROM dbo.CREDITCARDACCOUNTSETUP -- payment service form
SELECT CONNECTIONSTRING FROM dbo.RETAILCONNDATABASEPROFILE -- payment service connection string for CDX
If preloaded values are found, set the attribute values to empty with scripts similar to the following examples.
Warning
The example UPDATE scripts provided below are illustrative for newly provisioned environments experiencing the certificate issue described above. You should only update values for the intended table or rows to avoid disruptive or destructive data updates. More selectors may be required if updating specific rows for the tables being updated.
UPDATE dbo.RETAILHARDWAREPROFILE SET SECUREMERCHANTPROPERTIES=";)
UPDATE dbo.RETAILCHANNELPAYMENTCONNECTORLINE SET SECUREMERCHANTPROPERTIES=";)
UPDATE dbo.CREDITCARDACCOUNTSETUP SET SECUREMERCHANTPROPERTIES=";)
UPDATE dbo.RETAILCONNDATABASEPROFILE SET CONNECTIONSTRING=";
Once cleared, use the forms in headquarters to set up your payment gateway merchant details in the hardware profile, online store channel, or the payments service forms appropriate for the environment. For the setup instructions required for your payment options, see the appropriate article:
Redeploy or restart the runtime on the VM
To restart the local runtime and redeploy all the packages, follow these steps:
- Open File Explorer, and go to C:\CustomerServiceUnit.
- Right-click AOSDeploy.cmd, and then click Run as administrator.
This process might take a while. The process is completed when the cmd.exe window closes. If you just want to restart AOS (without redeploying the runtime), run iisreset from an administrator Command Prompt window, or restart AOSWebApplication from IIS.
Frequently asked questions
Can we join cloud-hosted environments to our Microsoft Entra domain as it is currently deployed in a workgroup?
These environments are self-contained and haven't been tested, nor are they supported when joined to an Microsoft Entra domain when deployed via Azure.
Is there a way to hide the local account passwords in Lifecycle Services?
This is only possible if you lower a user's security role in the project to Project team member role, and it isn't possible to hide the local account passwords for the Environment manager, or Project owner roles.
Are cloud-hosted environments supported with Azure Bastion?
These environments haven't been tested, nor are they supported with Azure Bastion.
Environment is in a failed state with the error message, "Updated Microsoft Entra ID Tenant is missing reply URL configuration". How do I resolve this issue?
This message indicates that a Tier 1/customer-managed environment is configured with an Azure AD tenant different from the one used at the time of deployment. There are different options available to help resolve this issue:
- (Recommended) Delete the environment and redeploy with the tenant in which the environment will be used.
- Revert the settings to the tenant configuration used at the time of deployment.
- Follow the instructions in How can I fix my existing environment when my environment is in a failed state or if I am getting sign-in errors? to update the reply URL in the target tenant.
As a partner/ISV, how can I facilitate cloud-hosted deployments for customers that I work with?
A Tier 1/customer-managed environment should be deployed under the customer's Microsoft Entra tenant, to ensure that all the configuration and integrations are correctly provisioned for any given environment. The tenant and environment association is determined based on the user who deployed the environment.
To facilitate cloud-hosted deployments, we recommend that partners follow this step to create customer-specific, cloud-hosted environments. In this way, they'll ensure that the deployment is registered under the correct tenant.
- Deploy the environment via a user from the tenant that the environment will be used with. The Admin user provisioning tool shouldn't be used to change the tenant for a Tier 1/customer-managed/cloud-hosted environment.
Note
The Microsoft Entra tenant that is associated with the Azure subscription doesn't play any role in environment configuration. The Azure subscription and the corresponding connector configuration are used only to deploy Azure resources.
I have run the Admin user provisioning tool on my development environment, and now I receive the following sign-in error: "Error: Microsoft EntraSTS50011: The reply URL specified in the request doesn't match the reply URLs configured for the application."
As was stated earlier, it's important that finance and operations environments be deployed under the correct Microsoft Entra tenant. For Tier 1/customer-managed environments that are deployed via LCS, changes to the Microsoft Entra tenant settings aren't supported after deployment.
How can I fix my existing environment when my environment is in a failed state or I am getting sign-in errors?
If you have environments where the Admin user provisioning tool was previously used to update the tenant settings, we recommend that you delete those environments and then redeploy them under the correct Microsoft Entra tenant.
If an existing environment can't be deleted and redeployed, its URL must be added to the configured Microsoft Entra tenant. The following commands can be run by the tenant admin.
Note
Since these URLs are being added manually, the clean-up of these URLs also has to be done manually when the environment is deleted.
If not already on your machine you need to install the Microsoft.Graph PowerShell module.
Install-Module Microsoft.GraphRetrieve the following values from the web.config file.
$Microsoft EntraTenant = <Value of Aad.TenantDomainGUID from web.config> $EnvironmentUrl = <Value of Infrastructure.HostUrl from web.config> # For example, if value is spn:fd663e81-110e-4c18-8995-ddf534bcf5e1 then take only fd663e81-110e-4c18-8995-ddf534bcf5e1 $Microsoft EntraRealm = <Value of Aad.Realm from web.config without spn: prefix. >Run the following commands via the tenant admin account for the Microsoft Entra tenant in the web.config file.
# Using tenant admin account under this tenant login via Microsoft Graph PowerShell cmdlet. Connect-MgGraph -TenantId $Microsoft EntraTenant -Scopes "Application.ReadWrite.All" # Get Service Principal details $SP = Get-MgServicePrincipal -Filter "AppId eq '$Microsoft EntraRealm'" # Add Reply URLs [System.Collections.ArrayList]$ReplyUrls = $SP.ReplyUrls $ReplyUrls.Add("$EnvironmentUrl") $ReplyUrls.Add("$EnvironmentUrl/oauth") #Set/Update Reply URL Update-MgServicePrincipal -ServicePrincipalId $SP.Id -ReplyUrls $ReplyUrls # Log out Disconnect-MgGraph
I've fixed my environment, but it's still in a failed state. How do I resolve this issue?
Restart your environment from Lifecycle Services by first performing Stop and then Start operations against your environment. If the environment configuration is found to be correct, then the environment URL is restored automatically within 2 hours of the Start operation.
When the Admin user provisioning tool is run on my local development environment, I get the error "The value's length for key 'password' exceeds its limit of '128'."
If you're using the virtual hard drive (VHD) that was released for versions 10.0.24 and later, the Generate Self-Signed Certificates tool needs to be run before the Admin user provisioning tool. For more information, see Set up the downloadable VHD for first use.