Tutorial: Migrate Okta sign-on policies to Microsoft Entra Conditional Access
In this tutorial, learn to migrate an organization from global or application-level sign-on policies in Okta Conditional Access in Microsoft Entra ID. Conditional Access policies secure user access in Microsoft Entra ID and connected applications.
Learn more: What is Conditional Access?
This tutorial assumes you have:
- Office 365 tenant federated to Okta for sign-in and multifactor authentication
- Microsoft Entra Connect server, or Microsoft Entra Connect cloud provisioning agents configured for user provisioning to Microsoft Entra ID
Prerequisites
See the following two sections for licensing and credentials prerequisites.
Licensing
There are licensing requirements if you switch from Okta sign-on to Conditional Access. The process requires a Microsoft Entra ID P1 license to enable registration for Microsoft Entra multifactor authentication.
Learn more: Assign or remove licenses in the Microsoft Entra admin center
Enterprise Administrator credentials
To configure the service connection point (SCP) record, ensure you have Enterprise Administrator credentials in the on-premises forest.
Evaluate Okta sign-on policies for transition
Locate and evaluate Okta sign-on policies to determine what will be transitioned to Microsoft Entra ID.
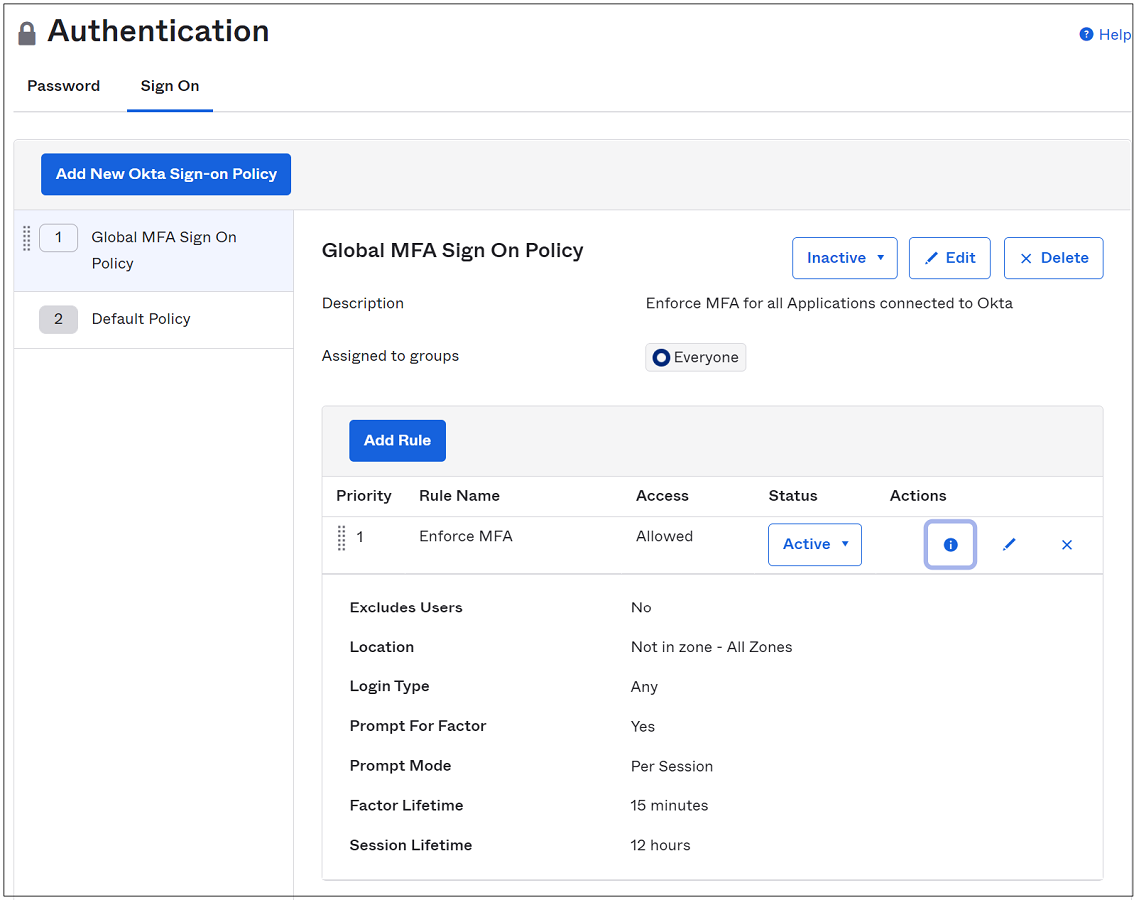
In Okta go to Security > Authentication > Sign On.
Go to Applications.
From the submenu, select Applications
From the Active apps list, select the Microsoft Office 365 connected instance.
Select Sign On.
Scroll to the bottom of the page.
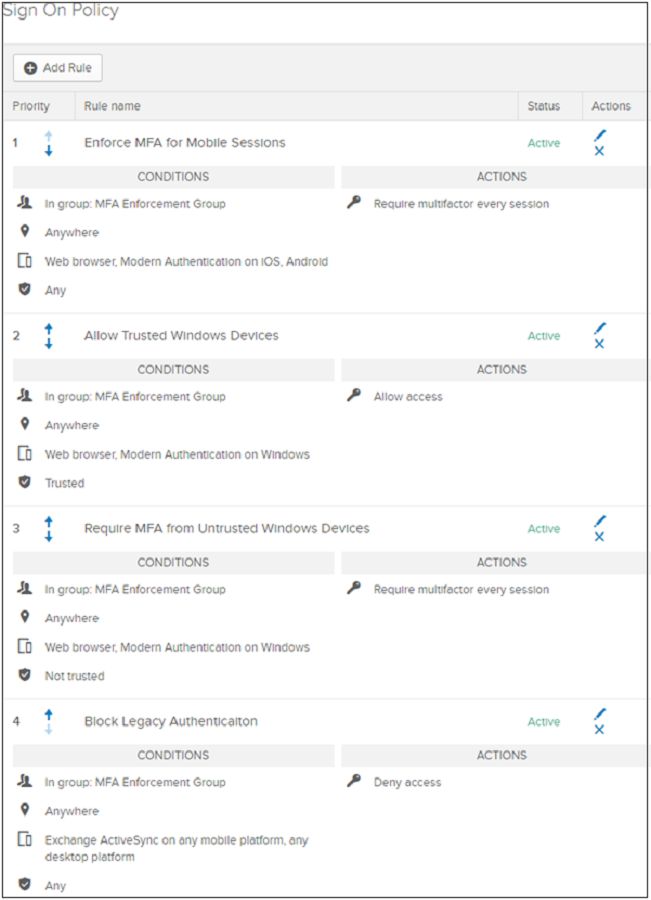
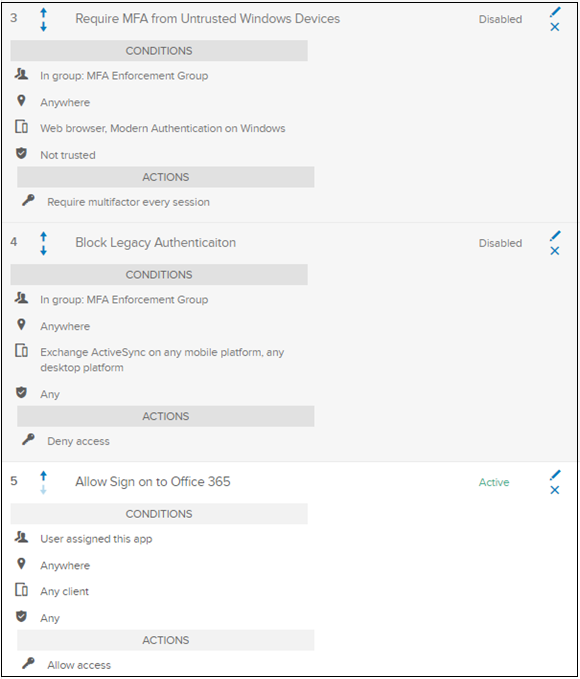
The Microsoft Office 365 application sign-on policy has four rules:
- Enforce MFA for mobile sessions - requires MFA from modern authentication or browser sessions on iOS or Android
- Allow trusted Windows devices - prevents unnecessary verification or factor prompts for trusted Okta devices
- Require MFA from untrusted Windows devices - requires MFA from modern authentication or browser sessions on untrusted Windows devices
- Block legacy authentication - prevents legacy authentication clients from connecting to the service
The following screenshot is conditions and actions for the four rules, on the Sign On Policy screen.
Configure Conditional Access policies
Configure Conditional Access policies to match Okta conditions. However, in some scenarios, you might need more setup:
- Okta network locations to named locations in Microsoft Entra ID
- Okta device trust to device-based Conditional Access (two options to evaluate user devices):
- See the following section, Microsoft Entra hybrid join configuration to synchronize Windows devices, such as Windows 10, Windows Server 2016 and 2019, to Microsoft Entra ID
- See the following section, Configure device compliance
- See, Use Microsoft Entra hybrid join, a feature in Microsoft Entra Connect server that synchronizes Windows devices, such as Windows 10, Windows Server 2016, and Windows Server 2019, to Microsoft Entra ID
- See, Enroll the device in Microsoft Intune and assign a compliance policy
Microsoft Entra hybrid join configuration
To enable Microsoft Entra hybrid join on your Microsoft Entra Connect server, run the configuration wizard. After configuration, enroll devices.
Note
Microsoft Entra hybrid join isn't supported with the Microsoft Entra Connect cloud provisioning agents.
On the SCP configuration page, select the Authentication Service dropdown.
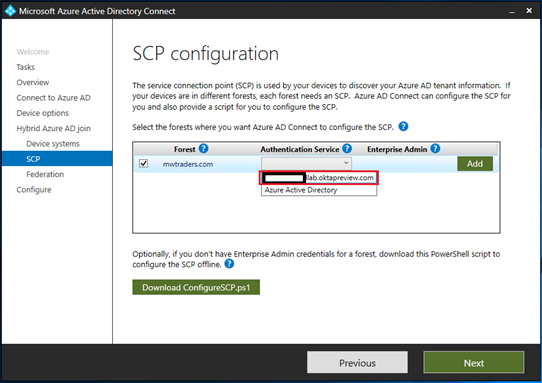
Select an Okta federation provider URL.
Select Add.
Enter your on-premises Enterprise Administrator credentials
Select Next.
Tip
If you blocked legacy authentication on Windows clients in the global or app-level sign-on policy, make a rule that enables the Microsoft Entra hybrid join process to finish. Allow the legacy authentication stack for Windows clients.
To enable custom client strings on app policies, contact the Okta Help Center.
Configure device compliance
Microsoft Entra hybrid join is a replacement for Okta device trust on Windows. Conditional Access policies recognize compliance for devices enrolled in Microsoft Intune.
Device compliance policy
- Use compliance policies to set rules for devices you manage with Intune
- Create a compliance policy in Microsoft Intune
Windows 10/11, iOS, iPadOS, and Android enrollment
If you deployed Microsoft Entra hybrid join, you can deploy another group policy to complete auto-enrollment of these devices in Intune.
- Enrollment in Microsoft Intune
- Quickstart: Set up automatic enrollment for Windows 10/11 devices
- Enroll Android devices
- Enroll iOS/iPadOS devices in Intune
Configure Microsoft Entra multifactor authentication tenant settings
Before you convert to Conditional Access, confirm the base MFA tenant settings for your organization.
Sign in to the Microsoft Entra admin center as a Hybrid Identity Administrator.
Browse to Identity > Users > All users.
Select Per-user MFA on the top menu of the Users pane.
The legacy Microsoft Entra multifactor authentication portal appears. Or select Microsoft Entra multifactor authentication portal.
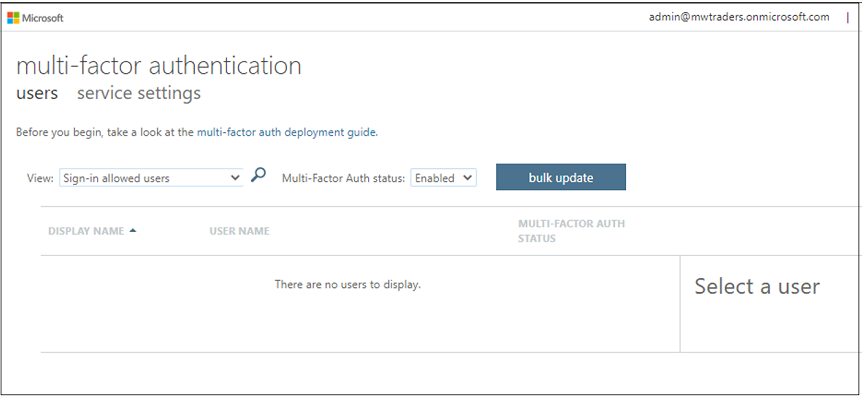
Confirm there are no users enabled for legacy MFA: On the Multifactor authentication menu, on Multifactor authentication status, select Enabled and Enforced. If the tenant has users in the following views, disable them in the legacy menu.
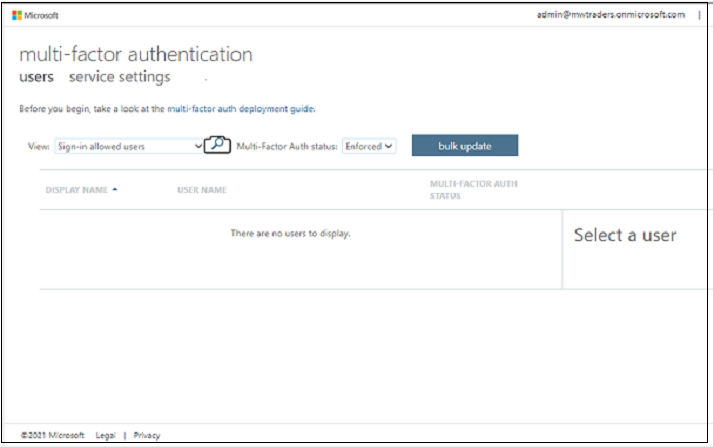
Ensure the Enforced field is empty.
Select the Service settings option.
Change the App passwords selection to Do not allow users to create app passwords to sign in to non-browser apps.
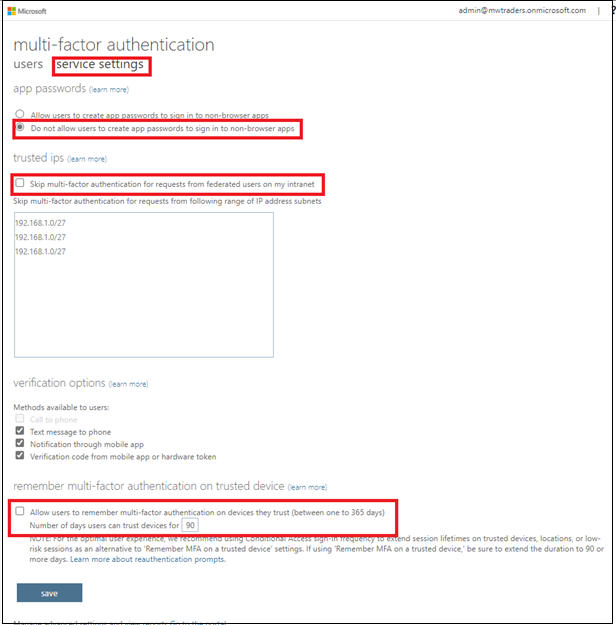
Clear the checkboxes for Skip multifactor authentication for requests from federated users on my intranet and Allow users to remember multifactor authentication on devices they trust (between one to 365 days).
Select Save.
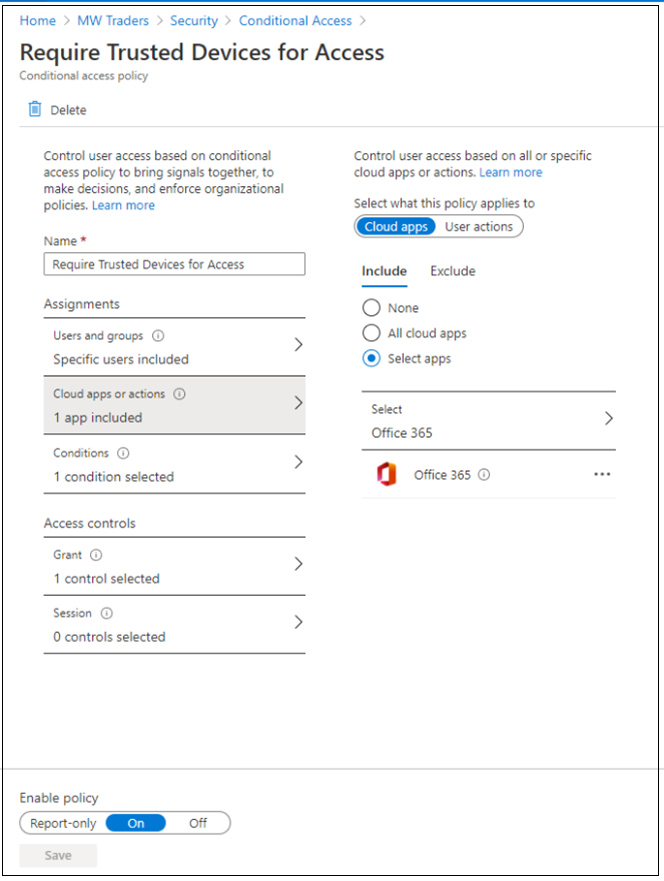
Build a Conditional Access policy
To configure Conditional Access policies, see Best practices for deploying and designing Conditional Access.
After you configure the prerequisites and established base settings, you can build Conditional Access policy. Policy can be targeted to an application, a test group of users, or both.
Before you get started:
Sign in to the Microsoft Entra admin center.
Browse to Identity.
To learn how to create a policy in Microsoft Entra ID. See, Common Conditional Access policy: Require MFA for all users.
Create a device trust-based Conditional Access rule.
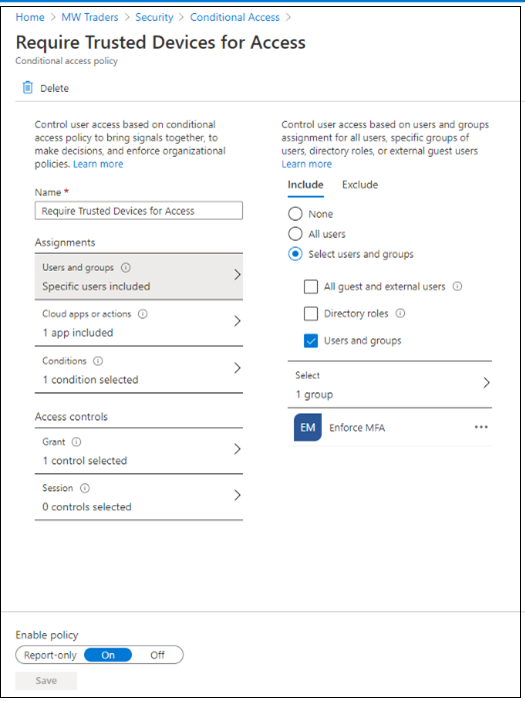
After you configure the location-based policy and device trust policy, Block legacy authentication with Microsoft Entra ID with Conditional Access.
With these three Conditional Access policies, the original Okta sign-on policies experience is replicated in Microsoft Entra ID.
Enroll pilot members in MFA
Users register for MFA methods.
For individual registration, users go to Microsoft Sign-in pane.
To manage registration, users go to Microsoft My Sign-Ins | Security Info.
Learn more: Enable combined security information registration in Microsoft Entra ID.
Note
If users registered, they're redirected to the My Security page, after they satisfy MFA.
Enable Conditional Access policies
To test, change the created policies to Enabled test user login.
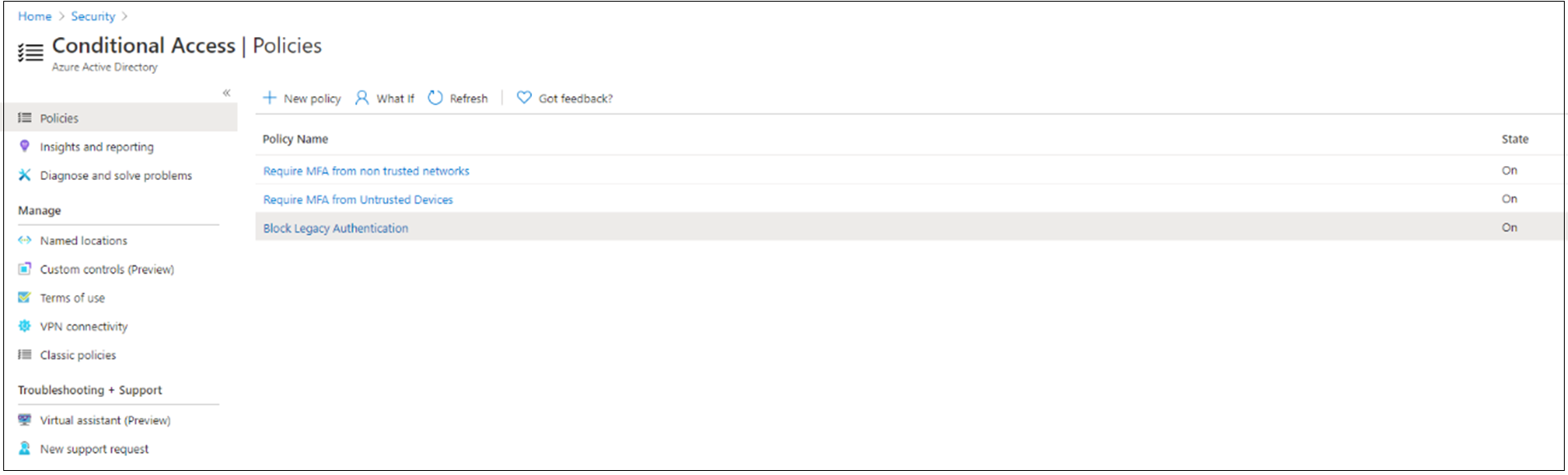
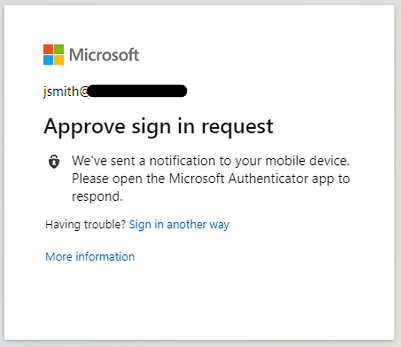
On the Office 365 Sign-In pane, the test user John Smith is prompted to sign in with Okta MFA and Microsoft Entra multifactor authentication.
Complete the MFA verification through Okta.
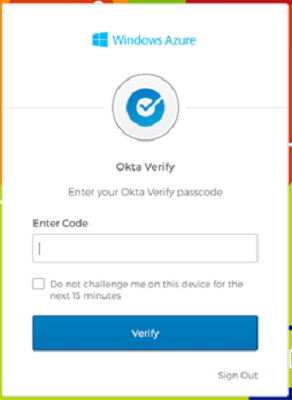
The user is prompted for Conditional Access.
Ensure the policies are configured to be triggered for MFA.
Add organization members to Conditional Access policies
After you conduct testing on pilot members, add the remaining organization members to Conditional Access policies, after registration.
To avoid double-prompting between Microsoft Entra multifactor authentication and Okta MFA, opt out from Okta MFA: modify sign-on policies.
Go to the Okta admin console
Select Security > Authentication
Go to Sign-on Policy.
Note
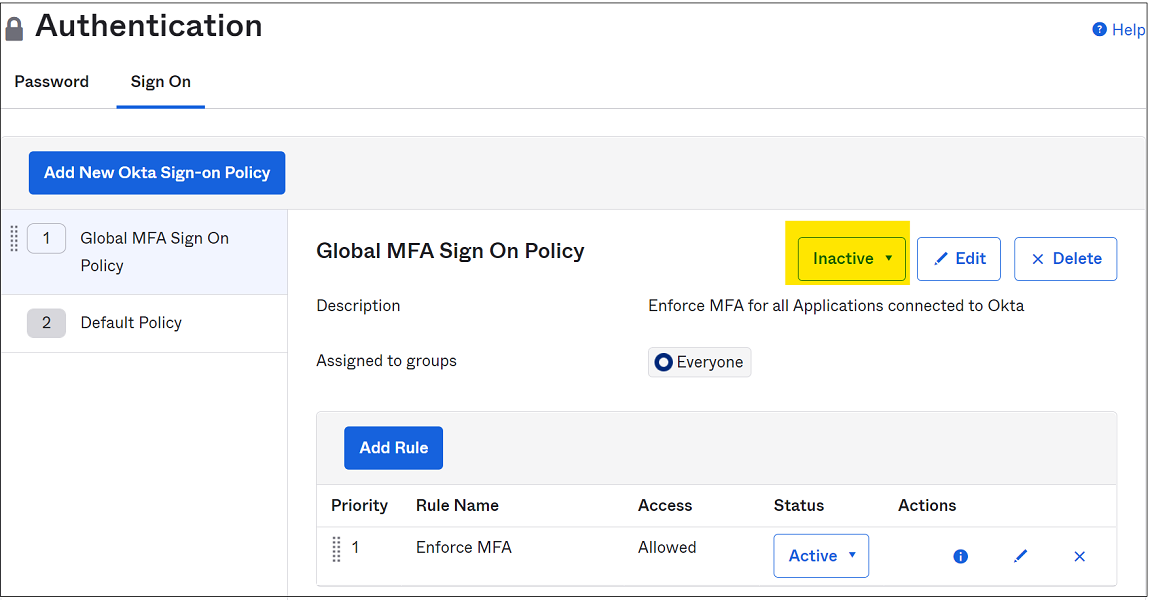
Set global policies to Inactive if all applications from Okta are protected by application sign-on policies.
Set the Enforce MFA policy to Inactive. You can assign the policy to a new group that doesn't include the Microsoft Entra users.
On the application-level sign-on policy pane, select the Disable Rule option.
Select Inactive. You can assign the policy to a new group that doesn't include the Microsoft Entra users.
Ensure there's at least one application-level sign-on policy enabled for the application that allows access without MFA.
Users are prompted for Conditional Access the next time they sign in.