Overview of Microsoft Cloud for Financial Services reference architectures
The Microsoft Cloud for Financial Services is constructed upon specialized vertical and core data models, facilitating seamless interoperability and data unification to expedite both insights and business workflows. With this foundational framework in place, a collection of cloud-based, first-party industry starter apps and building blocks empowers enhanced collaboration, automation, and insights. It enabled the streamlining processes, personalizing customer interactions, and elevating the overall customer experience. This comprehensive solution also ensures that robust security, compliance, and interoperability measures are in place to safeguard critical operations.
To gain a thorough grasp of deploying, configuring and extending these vertical solution components and data models, and integrating them as core elements of an all-encompassing solution, reference architectures offer precise guidelines for solution architects and developers to follow. These reference architectures serve as invaluable tools in minimizing the likelihood of errors and omissions throughout the design and development phases, ensuring a more effective and reliable implementation.
Architecture
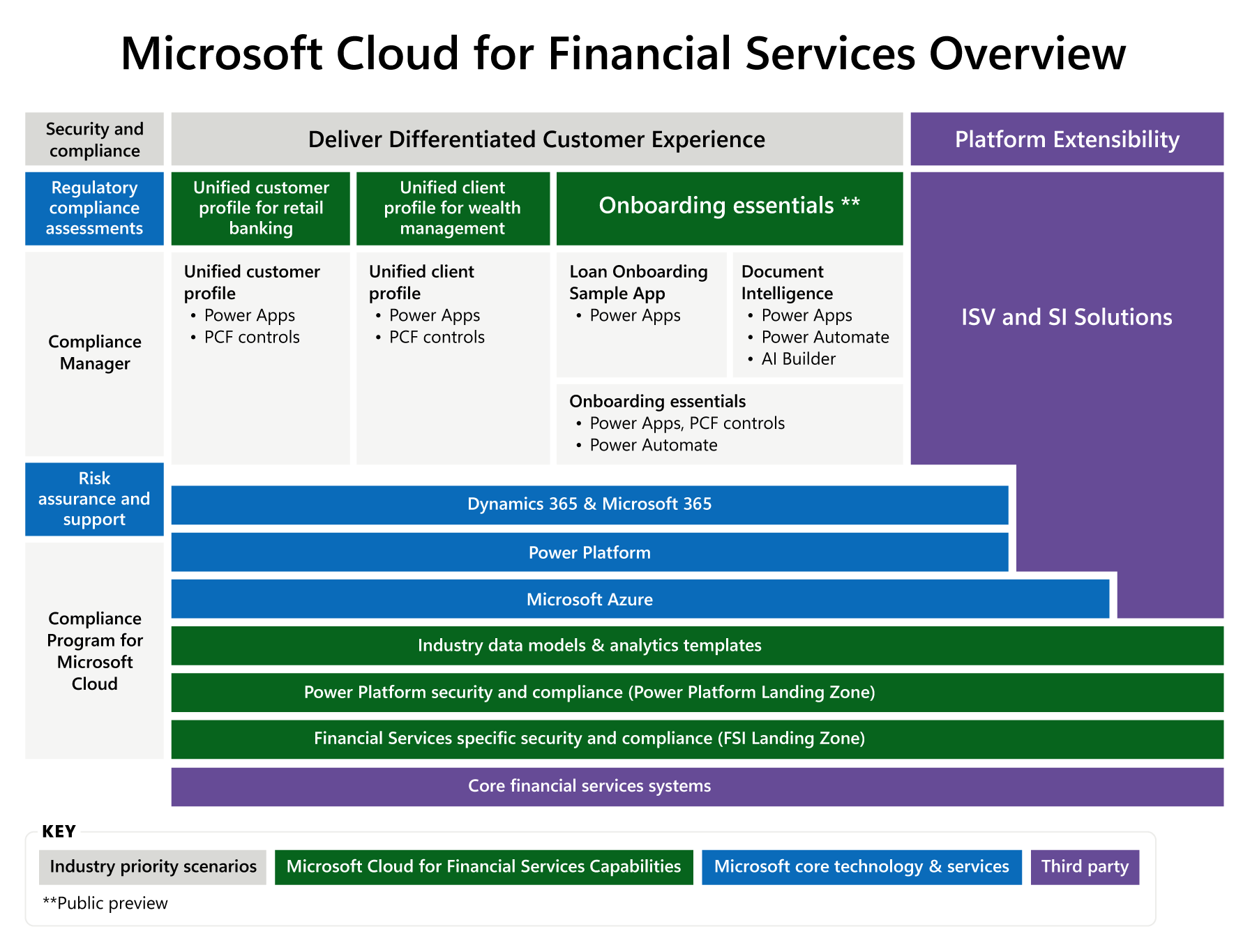
Microsoft Cloud for Financial Services uses a combination of Microsoft products to address the industry's prioritized scenarios that are focused on retail banking and extend the Property & Casualty Insurance (preview) and Small Medium Business (preview) lines of business with data models. The following illustration shows the required and recommended capabilities along with the external extensions that independent software vendors and system integrators drive.
Download a printable PDF of this diagram.
Common Concepts
Security
Authentication
Users authenticate to the PowerApps via Microsoft Entra ID like any other Power Apps application. Microsoft Entra ID performs the authentication methods that are enabled in the tenant and enforces any conditional access policies, such as multifactor authentication for users accessing the application.
Authorization
The Unified customer/client profile uses the role-based security model in Dataverse to authorize users to access data elements. Built-in security roles are available, or you can configure your own to implement the role-based security model. The access level considers the business unit hierarchy that the user is a member of.
First, you need to model and configure your business unit hierarchy. Then you can copy these built-in security roles and apply them to your business units to create your security segmentation. As part of your user management, you assign these security roles to the end user, teams, or business units. For more information about working with Microsoft Entra ID security groups, go to Security concepts in Microsoft Dataverse.
After assigning a proper license for dependent solution components and granting environment access to each user, you'll need to assign extra built-in security roles to users, owner teams or Microsoft Entra ID Group teams to access or operate in the app.
Security Extension
Financial institutions usually have complex security policies, they need to be monitored closely for auditing and compliance needs. Following are some common scenarios that might require an extension:
Entitlement Rules to access customer data
As Unified customer/client profile is built to provide a 360-degree perspective, it needs to access many customer data elements and objects. Financial institutions usually have specific rules to consider before users can access or operate on specific objects like customer data. These rules might include many criteria including the users branch, users role, teams that user is member of, the product category being accessed, line of business, the segment of the customer etc. Solution should apply these rules while user is searching, listing, accessing and operating on customer record.
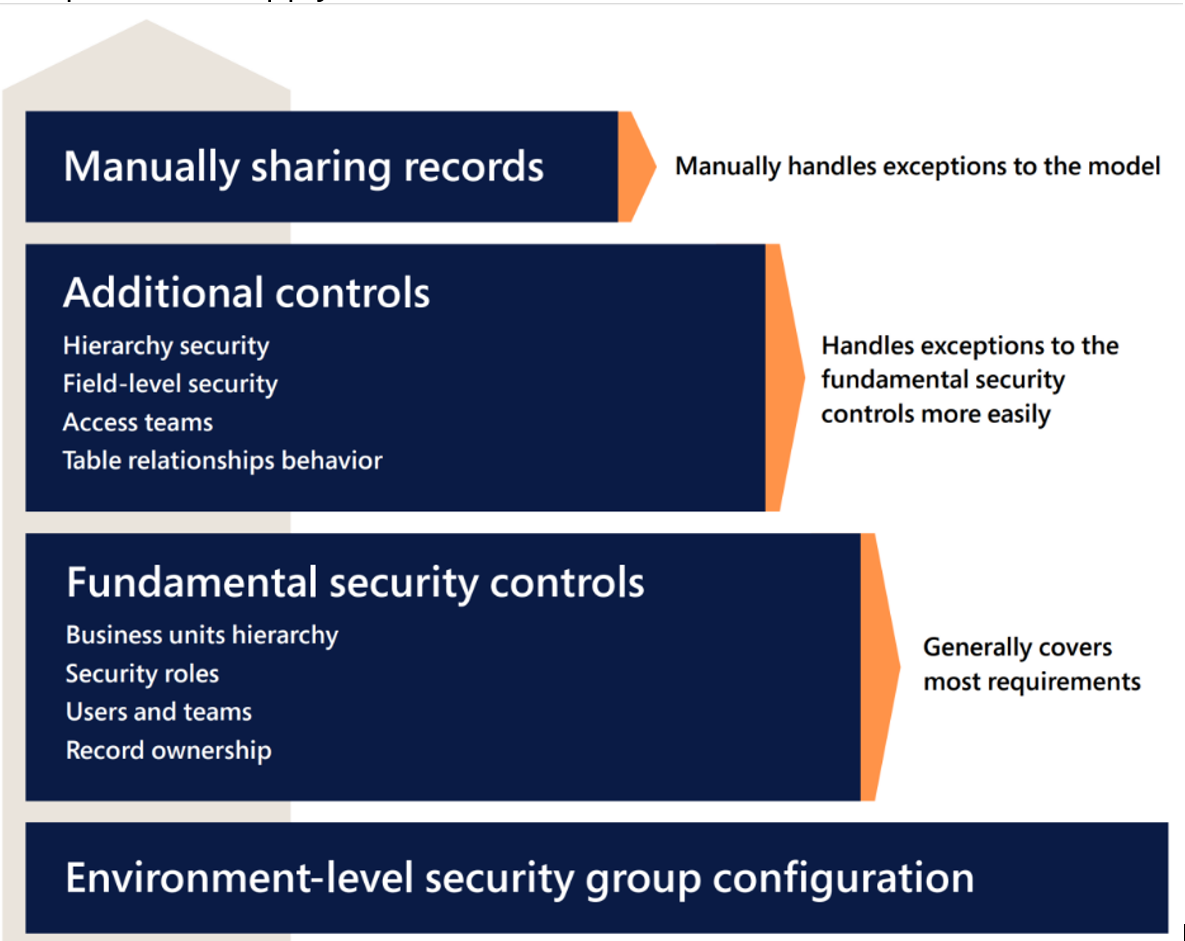
Microsoft Cloud for Financial Services is using the native security capabilities of Dataverse detailed here. Microsoft recommends taking a configure-first approach, as illustrated, to design the security model with these native security components to apply these entitlement rules.
You can follow the security best practices shared in Dynamics 365 implementation guide, and the following practices.
- Dataverse Security is designed with ownership, consider not assigning and sharing records with individual users. Instead, consider assigning and sharing records to teams.
- If there's a system of record that hosts these access rules, consider doing a batch sync process to transform the ownership model to security model in Dataverse.
- To make your security model performance efficient, consider using owned teams over access-teams and eliminate or at least optimize the sharing of records to different teams.
Data Masking and field level security needs
Financial institutions frequently employ extra security measures to protect sensitive data such as Social Security Numbers (SSN), Credit Card details, and occasionally personal information like mobile numbers and email addresses. These security measures often involve restricting access to specific individuals and even masking sensitive information when displayed.
To implement these security requirements, you can create new field level security profiles, which specify read, update, and create permissions for specific fields. These profiles can then be assigned to users or teams, granting them controlled access to sensitive data.
Moreover, if there are more compliance requirements necessitating data masking, you can achieve it by creating a new PowerFX column (preview) or calculated column. This new column generates a masked version of the original data, providing an extra layer of data protection. The previous original column can be secured with field level security and this new data masked column can be added to Unified Customer Profile through quick forms configuration.
Private or restricted connection needs
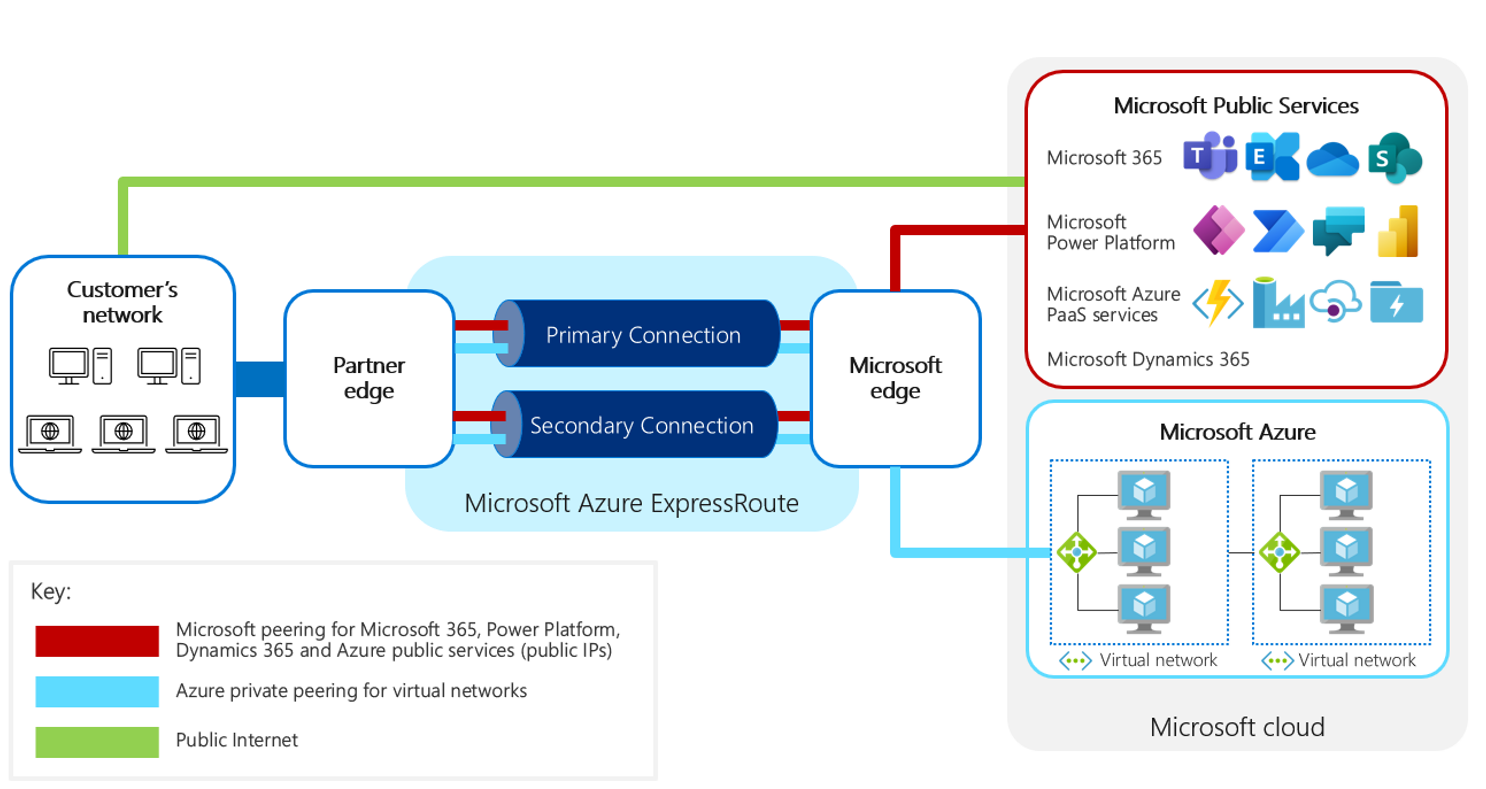
The Unified customer profile and Unified customer profile solutions runs on Power Platform, which operates on a scale-group shared infrastructure architecture.
A scale group hosts multiple customer organizations, each with their own database but with shared service infrastructure. These scale groups are set in pairs for each region the customer has selected. You can set up ExpressRoute to provide a private connection between your on-premises network and the entrance to the cloud service as specified in the following image. However, because the infrastructure is shared, you can’t set up a private connection between Azure and Power Platform.
Financial organizations usually have a strict access policy while systems are accessing customer and financial data. You can consider the following implementation options to address security concerns while Power Platform running on public cloud accessing customer data.
| Technical Options | Description | Consideration | Use When |
|---|---|---|---|
| Enable server to server traffic with new firewall rules | Existing firewalls can be configured to add Power Platform IP Ranges and URLs to allow traffic from Power Platform to API Gateways and VNETs (that have private endpoints to access data sources) | IP Ranges might change and it's important to monitor those changes to reflect them in firewall | Server to server integration needs between Power Platform to Gateways and VNETs. When the connectivity is established, you can use custom connectors, plug-in or webhook and Azure Integration technologies to access to these data sources directly. |
| Use client-based scripting to access API Data | Creating custom PCF controls to access API data. | Devices not using a corporate network can't access the data. It requires customization work and data still needs to be synced for FSI Data Model. | When all devices are domain-joint and using the corporate network while accessing custom PCF Controls in Unified Client Profile. |
| Data replication to FSI Data Model | Async / batch integrations to be developed to extract, transform and load (ETL) data elements to FSI data model | Data lives in the FSI Model as a replica of existing systems. | When there are no real-time integration needs. |
Security automation needs
Security automation is a vital aspect of modern-day organizations, especially when dealing with a multitude of users and complex scenarios. As the user base expands and organizational dynamics evolve, ensuring robust security measures becomes increasingly challenging. From adding new users to handling changes in roles, teams, and business units, to provisioning new environments and identifying system administrators, each scenario demands meticulous attention to safeguard sensitive data and critical systems. In this context, implementing automated security protocols proves indispensable, streamlining processes, mitigating risks, and fortifying the organization’s defenses against potential threats. By embracing security automation, businesses can effectively adapt to dynamic user landscapes and maintain an agile and secure environment that safeguards both valuable assets and user privacy.
Following are some scenarios and how you can approach implementing authorization and automate tasks where possible.
| Scenario | Security Implementation Approach |
|---|---|
| When New personas are introduced in the security model | In Dynamics, a security role with the required functional entitlements represents each persona. Configure a group teams in Dataverse for each persona and assign the security role for the persona. Set up group teams in active directory for the personas and use out-of-the-box integration to manage user membership in the group teams in Dataverse. Eliminate or minimize assignment of security roles to individuals. Change the member’s privilege inheritance parameter of the security roles only to Team privileges so that the records users create with the team as the owner and not individuals. |
| When new environments are provisioned | A new security group should be created for each Dataverse environment to control and limit users to access specific environments. Otherwise, whoever has Dataverse license is created as a user in the environment. |
| New users are added to application or some users need to be removed from the application | Rather than each time adding / removing users to the environment, you can take a nested group approach and add the group teams (that is, relationship-manager-group) as child to the environment security group (ucp-production). With this approach, when users are added to the group team for specific role, they're automatically added to the environment as a user and assigned a role. Similarly, when users are removed from the group team, they're also removed from the environment if they aren't part of any other group teams. |
| When existing users change their title, role or location that might change their persona. | The dynamic membership type in Entra ID uses business rules to manage the group membership dynamically. You can use this dynamic membership type to configure the business rules to define which users are added or removed from the group team created for given persona. As Dataverse now supports dynamic membership type, these new or removed members are automatically synchronized to group teams in Dataverse, and the user gets the latest security role assigned for access. |
| When offboarding users | Same as the previous row. Use dynamic membership type to add active users to groups. Any inactive users are automatically removed. You can use the Lifecycle Workflows for offboarding that can be updated and triggered from Azure portal or Microsoft Graph API. |
| When organization structures change | Not every organization structure change affects the application security. Consider how data ownership changes based on business unit ownership hierarchy and reflect those changes on an environment with the updated business unit configuration. |
| When users change their teams or business unit they're working with | Microsoft recommends using the dynamic membership type and group teams while assigning security roles to teams and also not direct assigning security roles to users. With this security model, user-changing teams don't require any automation to reflect the change as authorization is based on membership to group teams. If a business unit needs to change in the user profile, you can create a Power Automate flow with trigger when a business unit changes in primary systems, and use the SetBusinessSystemUser action to move the user to a different business unit. |
| When users change their position or manager | The hierarchy security model is an extension to the existing security models that use business units, security roles, sharing, and teams. If you configure these elements in the security model, make sure the position and manager information in the user record gets updated. |
Collaboration
The Cloud for Financial Services applications use the native Microsoft Teams integration to collaborate seamlessly with Power Apps / Dynamics 365 team members. The solution utilizes the collaboration and chat features of Microsoft Teams.
Analytics
If you have the requirement to create an overall view of customers using the data in the Microsoft Cloud for Financial Services data models, you can extend the analytics by creating custom Model-Driven App Dashboards and Power BI embedded dashboards. Alternatively, you can add a Power BI report into the model-driven app using Power BI report control (preview).
You can find further detailed guidance on how to extend analytics capabilities within the Analytics Data Estate article.
See also
Next steps
Well-Architected for Microsoft Cloud for Financial Services introduces the following reference architectures: