Manage exclusions for Microsoft Defender for Endpoint and Microsoft Defender Antivirus
Applies to:
- Microsoft Defender Antivirus
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
Platforms
- Windows
Note
As a Microsoft MVP, Fabian Bader contributed to and provided material feedback for this article.
Microsoft Defender for Endpoint includes a wide range of capabilities to prevent, detect, investigate, and respond to advanced cyberthreats. These capabilities include Next-generation protection (which includes Microsoft Defender Antivirus). As with any endpoint protection or antivirus solution, sometimes files, folders, or processes that aren't actually a threat can be detected as malicious by Defender for Endpoint or Microsoft Defender Antivirus. These entities can be blocked or sent to quarantine, even though they're not really a threat.
You can take certain actions to prevent false positives and similar issues from occurring. These actions include:
This article explains how these actions work, and describes the various types of exclusions that can be defined for Defender for Endpoint and Microsoft Defender Antivirus.
Caution
Defining exclusions reduces the level of protection offered by Defender for Endpoint and Microsoft Defender Antivirus. Use exclusions as a last resort, and make sure to define only the exclusions that are necessary. Make sure to review your exclusions periodically, and remove the ones you no longer need. See Important points about exclusions and Common mistakes to avoid.
Submissions, suppressions, and exclusions
When you're dealing with false positives, or known entities that are generating alerts, you don't necessarily need to add an exclusion. Sometimes classifying and suppressing an alert is enough. We recommend submitting false positives (and false negatives) to Microsoft for analysis as well. The following table describes some scenarios and what steps to take with respect to file submissions, alert suppressions, and exclusions.
| Scenario | Steps to consider |
|---|---|
| False positive: An entity, such as a file or a process, was detected and identified as malicious, even though the entity isn't a threat. | 1. Review and classify alerts that were generated as a result of the detected entity. 2. Suppress an alert for a known entity. 3. Review remediation actions that were taken for the detected entity. 4. Submit the false positive to Microsoft for analysis. 5. Define an exclusion for the entity (only if necessary). |
| Performance issues such as one of the following issues: - A system is having high CPU usage or other performance issues. - A system is having memory leak issues. - An app is slow to load on devices. - An app is slow to open a file on devices. |
1. Collect diagnostic data for Microsoft Defender Antivirus. 2. If you're using a non-Microsoft antivirus solution, check with the vendor for any needed exclusions. 3. Analyze the Microsoft Protection Log to see the estimated performance impact. 4. Define an exclusion for Microsoft Defender Antivirus (if necessary). 5. Create an indicator for Defender for Endpoint (only if necessary). |
| Compatibility issues with non-Microsoft antivirus products. Example: Defender for Endpoint relies on security intelligence updates for devices, whether they're running Microsoft Defender Antivirus or a non-Microsoft antivirus solution. |
1. If you're using a non-Microsoft antivirus product as your primary antivirus/antimalware solution, set Microsoft Defender Antivirus to passive mode. 2. If you're switching from a non-Microsoft antivirus/antimalware solution to Defender for Endpoint, see Make the switch to Defender for Endpoint. This guidance includes: - Exclusions you might need to define for the non-Microsoft antivirus/antimalware solution; - Exclusions you might need to define for Microsoft Defender Antivirus; and - Troubleshooting information (just in case something goes wrong while migrating). |
Important
An "allow" indicator is the strongest type of exclusion you can define in Defender for Endpoint. Make sure to use indicators sparingly (only when necessary), and review all exclusions periodically.
Submitting files for analysis
If you have a file that you think is wrongly detected as malware (a false positive), or a file that you suspect might be malware even though it wasn't detected (a false negative), you can submit the file to Microsoft for analysis. Your submission is scanned immediately, and will then be reviewed by Microsoft security analysts. You're able to check the status of your submission on the submission history page.
Submitting files for analysis helps reduce false positives and false negatives for all customers. To learn more, see the following articles:
- Submit files for analysis (available to all customers)
- Submit files using the new unified submissions portal in Defender for Endpoint (available to customers who have Defender for Endpoint Plan 2 or Microsoft Defender XDR)
Suppressing alerts
If you're getting alerts in the Microsoft Defender portal for tools or processes that you know aren't actually a threat, you can suppress those alerts. To suppress an alert, you create a suppression rule, and specify what actions to take for that on other, identical alerts. You can create suppression rules for a specific alert on a single device, or for all alerts that have the same title across your organization.
To learn more, see the following articles:
- Suppress alerts
- Introducing the new alert suppression experience (for Defender for Endpoint)
Exclusions and indicators
Sometimes, the term exclusions is used to refer to exceptions that apply across Defender for Endpoint and Microsoft Defender Antivirus. A more accurate way to describe these exceptions is as follows:
- Indicators for Defender for Endpoint; (which apply across Defender for Endpoint and Microsoft Defender Antivirus); and
- Exclusions for Microsoft Defender Antivirus.
The following table summarizes exclusion types that can be defined for Defender for Endpoint and Microsoft Defender Antivirus.
Tip
- Defender for Endpoint Plan 1 is available as a standalone plan, and is included in Microsoft 365 E3.
- Defender for Endpoint Plan 2 is available as a standalone plan, and is included in Microsoft 365 E5.
- If you have Microsoft 365 E3 or E5, make sure to set up your Defender for Endpoint capabilities.
| Product/service | Exclusion types |
|---|---|
| Microsoft Defender Antivirus Defender for Endpoint Plan 1 or Plan 2 |
- Automatic exclusions (for active roles on Windows Server 2016 and later) - Built-in exclusions (for operating system files in Windows) - Custom exclusions, such as process-based exclusions, folder location-based exclusions, file extension exclusions, or contextual file and folder exclusions - Custom remediation actions based on threat severity or for specific threats The standalone versions of Defender for Endpoint Plan 1 and Plan 2 don't include server licenses. To onboard servers, you need another license, such as Microsoft Defender for Endpoint for Servers or Microsoft Defender for Servers Plan 1 or 2. To learn more, see Defender for Endpoint onboarding Windows Server. If you're a small or medium-sized business using Microsoft Defender for Business, you can get Microsoft Defender for Business servers. |
| Defender for Endpoint Plan 1 or Plan 2 | - Indicators for files, certificates, or IP addresses, URLs/domains - Attack surface reduction exclusions - Controlled folder access exclusions |
| Defender for Endpoint Plan 2 | Automation folder exclusions (for automated investigation and remediation) |
The following sections describe these exclusions in more detail:
- Microsoft Defender Antivirus exclusions
- Defender for Endpoint indicators
- Attack surface reduction exclusions
- Controlled folder access exclusions
- Automation folder exclusions (for automated investigation and remediation)
Microsoft Defender Antivirus exclusions
Microsoft Defender Antivirus exclusions can apply to antivirus scans and/or to real-time protection. These exclusions include:
- Automatic exclusions (for server roles on Windows Server 2016 and later)
- Built-in exclusions (for operating system files in all versions of Windows)
- Custom exclusions (for files and folders that you specify, if necessary)
- Custom remediation actions (to determine what happens with detected threats)
Automatic exclusions
Automatic exclusions (also referred to as automatic server role exclusions) include exclusions for server roles and features in Windows Server. These exclusions aren't scanned by real-time protection but are still subject to quick, full, or on-demand antivirus scans.
Examples include:
- File Replication Service (FRS)
- Hyper-V
- SYSVOL
- Active Directory
- DNS Server
- Print Server
- Web Server
- Windows Server Update Services
- ...and more.
Note
Automatic exclusions for server roles aren't supported on Windows Server 2012 R2. For servers running Windows Server 2012 R2 with the Active Directory Domain Services (AD DS) server role installed, exclusions for domain controllers must be specified manually. See Active Directory exclusions.
For more information, see Automatic server role exclusions.
Built-in exclusions
Built-in exclusions include certain operating system files that are excluded by Microsoft Defender Antivirus on all versions of Windows (including Windows 10, Windows 11, and Windows Server).
Examples include:
%windir%\SoftwareDistribution\Datastore\*\Datastore.edb%allusersprofile%\NTUser.pol- Windows Update files
- Windows Security files
- ... and more.
The list of built-in exclusions in Windows is kept up to date as the threat landscape changes. To learn more about these exclusions, see Microsoft Defender Antivirus exclusions on Windows Server: Built-in exclusions.
Custom exclusions
Custom exclusions include files and folders that you specify. Exclusions for files, folders, and processes will be skipped by scheduled scans, on-demand scans, and real-time protection. Exclusions for process-opened files won't be scanned by real-time protection but are still subject to quick, full, or on-demand antivirus scans.
Custom remediation actions
When Microsoft Defender Antivirus detects a potential threat while running a scan, it attempts to remediate or remove the detected threat. You can define custom remediation actions to configure how Microsoft Defender Antivirus should address certain threats, whether a restore point should be created before remediating, and when threats should be removed. Configure remediation actions for Microsoft Defender Antivirus detections.
Defender for Endpoint indicators
You can define indicators with specific actions for entities, such as files, IP addresses, URLs/domains, and certificates. In Defender for Endpoint, indicators are referred to as Indicators of Compromise (IoCs), and less often, as custom indicators. When you define your indicators, you can specify one of the following actions:
Allow – Defender for Endpoint won't block files, IP addresses, URLs/domains, or certificates that have Allow indicators. (Use this action with caution.)
Audit – Files, IP addresses, and URLs/domains with Audit indicators are monitored, and when they're accessed by users, informational alerts are generated in the Microsoft Defender portal.
Block and Remediate – Files or certificates with Block and Remediate indicators are blocked and quarantined when detected.
Block Execution – IP addresses and URLs/domains with Block Execution indicators are blocked. Users can't access those locations.
Warn – IP addresses and URLs/domains with Warn indicators cause a warning message to be displayed when a user attempts to access those locations. Users can choose to bypass the warning and proceed to the IP address or URL/domain.
Important
You can have up to 15,000 indicators in your tenant.
The following table summarizes IoC types and available actions:
| Indicator type | Available actions |
|---|---|
| Files | - Allow - Audit - Warn - Block execution - Block and remediate |
| IP addresses and URLs/domains | - Allow - Audit - Warn - Block execution |
| Certificates | - Allow - Block and remediate |
Tip
See the following resources to learn more about indicators:
Attack surface reduction exclusions
Attack surface reduction rules (also known as ASR rules) target certain software behaviors, such as:
- Launching executable files and scripts that attempt to download or run files
- Running scripts that seem to be obfuscated or otherwise suspicious
- Performing behaviors that apps don't usually initiate during normal day-to-day work
Sometimes, legitimate applications exhibit software behaviors that could be blocked by attack surface reduction rules. If that's occurring in your organization, you can define exclusions for certain files and folders. Such exclusions are applied to all attack surface reduction rules. See Enable attack surface reduction rules.
Also note that while most ASR rules exclusions are independent from Microsoft Defender Antivirus exclusions, some ASR rules do honor some Microsoft Defender Antivirus exclusions. See Attack surface reduction rules reference - Microsoft Defender Antivirus exclusions and ASR rules.
Controlled folder access exclusions
Controlled folder access monitors apps for activities that are detected as malicious and protects the contents of certain (protected) folders on Windows devices. Controlled folder access allows only trusted apps to access protected folders, such as common system folders (including boot sectors) and other folders that you specify. You can allow certain apps or signed executables to access protected folders by defining exclusions. See Customize controlled folder access.
Automation folder exclusions
Automation folder exclusions apply to automated investigation and remediation in Defender for Endpoint, which is designed to examine alerts and take immediate action to resolve detected breaches. As alerts are triggered, and an automated investigation runs, a verdict (Malicious, Suspicious, or No threats found) is reached for each piece of evidence investigated. Depending on the automation level and other security settings, remediation actions can occur automatically or only upon approval by your security operations team.
You can specify folders, file extensions in a specific directory, and file names to be excluded from automated investigation and remediation capabilities. Such automation folder exclusions apply to all devices onboarded to Defender for Endpoint. These exclusions are still subject to antivirus scans. See Manage automation folder exclusions.
How exclusions and indicators are evaluated
Most organizations have several different types of exclusions and indicators to determine whether users should be able to access and use a file or process. Exclusions and indicators are processed in a particular order so that policy conflicts are handled systematically.
The following image summarizes how exclusions and indicators are handled across Defender for Endpoint and Microsoft Defender Antivirus:
Here's how it works:
If a detected file/process isn't allowed by Windows Defender Application Control and AppLocker, it's blocked. Otherwise, it proceeds to Microsoft Defender Antivirus.
If the detected file/process isn't part of an exclusion for Microsoft Defender Antivirus, it's blocked. Otherwise, Defender for Endpoint checks for a custom indicator for the file/process.
If the detected file/process has a Block or Warn indicator, that action is taken. Otherwise, the file/process is allowed, and proceeds to evaluation by attack surface reduction rules, controlled folder access, and SmartScreen protection.
If the detected file/process isn't blocked by attack surface reduction rules, controlled folder access, or SmartScreen protection, it proceeds to Microsoft Defender Antivirus.
If the detected file/process isn't allowed by Microsoft Defender Antivirus, it's checked for an action based on its threat ID.
How policy conflicts are handled
In cases where Defender for Endpoint indicators conflict, here's what to expect:
If there are conflicting file indicators, the indicator that uses the most secure hash is applied. For example, SHA256 takes precedence over SHA-1, which takes precedence over MD5.
If there are conflicting URL indicators, the more strict indicator is used. For Microsoft Defender SmartScreen, an indicator that uses the longest URL path is applied. For example,
www.dom.ain/admin/takes precedence overwww.dom.ain. (Network protection applies to domains, rather than subpages within a domain.)If there are similar indicators for a file or process that have different actions, the indicator that is scoped to a specific device group takes precedence over an indicator that targets all devices.
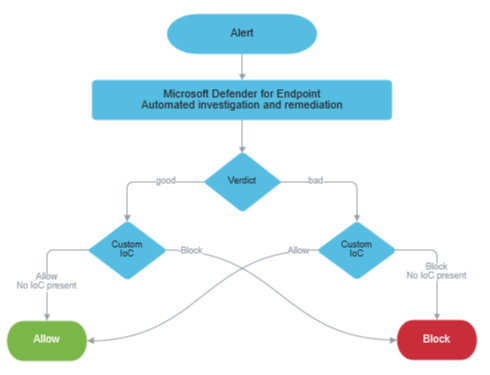
How automated investigation and remediation works with indicators
Automated investigation and remediation capabilities in Defender for Endpoint first determine a verdict for each piece of evidence, and then take an action depending on Defender for Endpoint indicators. Thus, a file/process could get a verdict of "good" (which means no threats were found) and still be blocked if there's an indicator with that action. Similarly, an entity could get a verdict of "bad" (which means it's determined to be malicious) and still be allowed if there's an indicator with that action.
The following diagram shows how automated investigation and remediation works with indicators:
Other server workloads and exclusions
If your organization is using other server workloads, such as Exchange Server, SharePoint Server, or SQL Server, be aware that only built-in server roles (that could be prerequisites for software you install later) on Windows Server are excluded by automatic exclusions feature (and only when using their default installation location). You'll likely need to define antivirus exclusions for these other workloads, or for all workloads if you disable automatic exclusions.
Here are some examples of technical documentation to identify and implement the exclusions you need:
- Running antivirus software on Exchange Server
- Folders to exclude from antivirus scans on SharePoint Server
- Choosing antivirus software for SQL Server
Depending on what you're using, you might need to refer to the documentation for that server workload.
Tip
Performance tip Due to a variety of factors, Microsoft Defender Antivirus, like other antivirus software, can cause performance issues on endpoint devices. In some cases, you might need to tune the performance of Microsoft Defender Antivirus to alleviate those performance issues. Microsoft's Performance analyzer is a PowerShell command-line tool that helps determine which files, file paths, processes, and file extensions might be causing performance issues; some examples are:
- Top paths that impact scan time
- Top files that impact scan time
- Top processes that impact scan time
- Top file extensions that impact scan time
- Combinations, such as:
- top files per extension
- top paths per extension
- top processes per path
- top scans per file
- top scans per file per process
You can use the information gathered using Performance analyzer to better assess performance issues and apply remediation actions. See: Performance analyzer for Microsoft Defender Antivirus.
See also
- Important points about exclusions
- Common mistakes to avoid when defining exclusions
- Blog post: The Hitchhiker's Guide to Microsoft Defender for Endpoint exclusions
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for