Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
By using administrative units in Microsoft Entra ID, you can restrict administrative permissions to specific parts of your Microsoft Entra organization. You can create, delete, and edit administrative units in Microsoft Entra. In Microsoft Entra, you manage the users or groups that are members of the administrative unit. This feature lets you subdivide your organization into smaller units and assign specific administrators to manage only the members within those units. Microsoft Purview role groups enable you to assign admins to specific administrative units. Microsoft Purview solutions that support administrative units restrict visibility and management permissions to the members of the unit.
For example, use administrative units to delegate permissions to administrators for each geographic region in a large multinational organization, or for grouping administrator access by department within your organization. You can create region or department-specific policies or view user activity as a result of those policies and administrative unit assignment. You can also use administrative units as an initial scope for a policy, where the selection of users eligible for the policy depends on membership in administrative units.
If you're using adaptive scopes for compliance policies, see How adaptive scopes work with Microsoft Entra administrative units.
Administrative units support in Microsoft Purview
The following Microsoft Purview compliance solutions support administrative units:
The configuration for administrative units automatically flows down to the following features:
- Alerts:
- DLP alerts are visible only to users in assigned administrative units.
- Activity explorer:
- Activity events are visible only to users in assigned administrative units.
- Adaptive scopes:
- Restricted administrators can select, create, edit, and view adaptive scopes only for users in those administrators' assigned administrative units.
- When a restricted administrator configures a policy that uses adaptive scopes, the administrator can select only adaptive scopes that are assigned to their administrative units.
- Audit log:
- Communication Compliance:
- Policy lookup and configuration: Restricted administrators can create or manage policies only for users assigned to their administrative units.
- Alerts and policy matches: Restricted administrators can investigate user activities only for users within their assigned administrative units.
- Data lifecycle management and records management:
- Policy lookup: Restricted administrators see policies only from users within their assigned administrative units.
- Disposition review and verification: Restricted administrators can add reviewers only from within their assigned administrative units, and see disposition reviews and items disposed only from users within their assigned administrative units.
- Insider Risk Management:
- Policy lookup and configuration: Restricted administrators can create or manage policies only for users assigned to their administrative units.
- User activities: Restricted administrators can start scoring activities or investigate user activities only for users within their assigned administrative units.
- Alerts and cases: Restricted administrators can view and investigate alerts and cases only for users within their assigned administrative units.
Note
Although DLP and Insider Risk Management both surface alerts in Microsoft Defender XDR, Microsoft Defender XDR only supports administrative units for DLP. Microsoft Defender XDR supports up to 100 administrative units.
Permissions for administrative units
To assign a role group member to an administrative unit, admins must be assigned the Role management role. For more information about Microsoft Purview role groups and roles, see Role groups in Microsoft Purview.
You can assign role group members to administrative units within the following built-in role groups:
- Communication Compliance
- Communication Compliance Admins
- Communication Compliance Analysts
- Communication Compliance Investigators
- Compliance Administrator
- Compliance Data Administrators
- Global Reader
- Information Protection
- Information Protection Admins
- Information Protection Analyst
- Information Protection Investigators
- Information Protection Readers
- Insider Risk Management
- Insider Risk Management Admins
- Insider Risk Management Analysts
- Insider Risk Management Approvers
- Insider Risk Management Investigators
- Insider Risk Management Session Approvers
- Organization Management
- Records Management
- Security Administrator
- Security Operator
- Security Reader
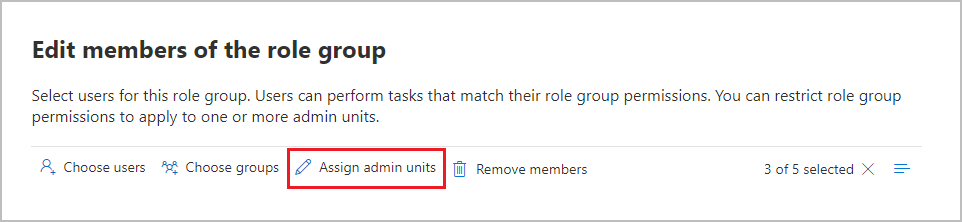
When you assign role groups, you can select individual members or groups, and then select the Assign admin units option to select administrative units that you define in Microsoft Entra ID:
Important
Assign admin units is always available when you create custom role groups. You can assign administrative units for any custom role group.
These administrators, referred to as restricted administrators, can select one or more of their assigned administrative units to automatically define the initial scope of policies that they create or edit. If administrators don't have administrative units assigned (unrestricted administrators), they can assign policies to the entire directory without being required to select individual administrative units.
Important
After you assign administrative units to members of the role groups, these restricted administrators can't see and edit existing policies. However, there's no operational change to these policies and they remain visible and can be edited by unrestricted administrators.
Restricted administrators also can't see historical data by using features that support administrative units, such as activity explorer and alerts. They remain visible to unrestricted administrators. Going forward, restricted administrators can see this related data for their assigned administrative units only.
Prerequisites for administrative units
Before configuring administrative units for Microsoft Purview compliance solutions, make sure your organization and users meet the following subscription and licensing requirements:
Microsoft Purview licensing:
- Microsoft 365 E5/A5/G5
- Microsoft 365 E5/A5/G5/F5 Compliance or F5 Security & Compliance
- Microsoft 365 E5/A5/G5/F5 Information Protection & Governance
- Microsoft 365 E5/A5/F5 Insider Risk Management
Configure and use administrative units
Complete the following steps to configure and use administrative units with Microsoft Purview compliance solutions:
Create administrative units to restrict the scope of role permissions in Microsoft Entra ID.
Add users and distribution groups to administrative units.
Important
Members of Dynamic Distribution Groups don't automatically become members of an administrative unit.
If you create geographic region or department-based administrative units, configure administrative units with dynamic membership rules.
Note
You can't add groups to an administrative unit that uses dynamic membership rules. If needed, create two administrative units, one for users and one for groups.
Use any of the role groups from the Microsoft Purview compliance solutions that support administrative units to assign administrative units to members.
When these restricted administrators create or edit policies that support administrative units, they can select administrative units so that only the users in those administrative units are eligible for the policy:
- Unrestricted administrators don't have to select administrative units as part of the policy configuration. They can keep the default of the entire directory or select one or more administrative units.
- Restricted administrators must select one or more administrative units as part of the policy configuration.
Later in the policy configuration, administrators who select administrative units must include or exclude (if supported) individual users and groups from the administrative units that they previously selected for the policy.
For information about administrative units that is specific to each supported solution, see the following sections:
- For audit: Scoping access to audit logs using administrative units
- For communication compliance: Consider administrative units if you want to scope user permissions to a region or department
- For data lifecycle management: Support for administrative units
- For DLP: Administrative Unit restricted policies
- For insider risk management: Consider administrative units if you want to scope user permissions to a region or department
- For records management: Support for administrative units
- For sensitivity labeling: Support for administrative units
Administrative units support for SharePoint sites
Microsoft Purview now supports adding SharePoint sites to administrative units. This feature enables you to tailor visibility and management control of Microsoft Purview administrators within the Microsoft Purview portal. This support is only available for Microsoft Information Protection auto-labeling policies and Microsoft Data Loss Prevention policies that support application to SharePoint sites.
Note
You manage administrative unit creation, deletion, and Microsoft Entra resource membership from Microsoft Entra ID. Any administrative unit you create appears in the listing for Microsoft Purview.
It can take up to five days for a query to fully populate. Changes aren't immediate. Wait until the query fully populates before you associate a policy with an administrative unit.
Configure administrative units for SharePoint sites
Follow these steps to configure and use administrative units. These steps guide you through administrative unit creation, how to associate resources to that administrative unit, and how to assign Microsoft Purview compliance role group members to administrative units. Once you create administrative units, use the following steps to associate SharePoint sites to the administrative unit.
Microsoft Purview customers entitled to this feature can now access Administrative units under the Roles and scopes in Microsoft Purview portal settings. Within Administrative units, select an administrative unit and edit it to associate SharePoint sites to the administrative unit.
To complete the following steps to configure SharePoint sites within administrative units for use in Microsoft Purview, you must have the admin unit extension manager role assigned. An administrator with role management rights in Microsoft Purview assigns this role, either by using a built-in role group with this role or by using a custom role group.
- Go to the Microsoft Purview portal.
- Select settings and select Roles and scopes.
- Select Administrative units.
- Select an existing administrative unit from the list.
- Select Edit.
- Create a query to associate SharePoint sites with the administrative unit.
- Use any of the role groups from the Microsoft Purview compliance solutions that support administrative units to assign administrative units to members.
Queries to associate SharePoint sites with administrative units support site properties for Site URL, Site name, and RefinableString00-RefinableString99. These queries apply both to SharePoint sites and OneDrive accounts, with the exception of shared channel SharePoint sites. The property names for sites are based on SharePoint site managed properties. For more information about associating custom properties to managed properties (RefinableString00-RefinableString99), see Using Custom SharePoint Site Properties to Apply Microsoft 365 Retention with Adaptive Policy Scopes.
Test your query
To test your query by using SharePoint search, complete the following steps:
- With an account assigned the SharePoint admin role, go to
https://<your_tenant>.sharepoint.com/search. - Use the search bar to enter the query shown in the query summary for your SharePoint sites in the administrative unit.
- Verify that the search results match the expected site URLs for your administrative unit. If they don't, check your query and the URLs with the relevant administrator for SharePoint.
When restricted administrators create or edit policies that support administrative units, they can select administrative units so that only the SharePoint sites, users, or groups in those administrative units are eligible for the policy:
- Unrestricted administrators don't have to select administrative units as part of the policy configuration. They can keep the default of the entire directory or select one or more administrative units.
- Restricted administrators must select one or more administrative units as part of the policy configuration.
Administrators selecting administrative units can't include or exclude individual SharePoint sites. SharePoint sites support application to all sites associated with the administrative unit.
Important
To remove associated sites from an administrative unit, edit a SharePoint query for an administrative unit to result in no site memberships. To clear site membership, make the query result in no sites.
View administrative unit SharePoint site membership details in Purview
After creating a SharePoint query for an administrative unit in Microsoft Purview, you can view the site members of the administrative unit. You can only view user and group membership of an administrative unit from the Microsoft Entra ID portal.
Complete the following steps to access the member details page to see SharePoint site members of an administrative unit in Microsoft Purview:
- Go to the Microsoft Purview portal at purview.microsoft.com.
- Select settings and select Roles and scopes.
- Select Administrative units.
- Select an existing administrative unit from the list.
- Select Member Details.
- View the list of SharePoint site members.
- Check the State column in the list, which shows Added for sites added to the administrative unit or Removed if the site was previously in the administrative unit but is removed once it's no longer a match for the SharePoint query.
- Use the Export function to download a list of the displayed sites to a CSV file.
Note
It might take up to five days for the member details list to update added or removed sites.
For information about administrative units and the SharePoint site in Microsoft Purview solutions, see:
- DLP: Administrative Unit restricted policies
- Sensitivity labels: Support for administrative units