Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
![]()
Endpoints are devices that access an organization's resources and applications. Modern workplaces include various devices that request access from both inside and outside the corporate network.
Zero Trust solutions for endpoints are about verifying the security of the devices that access work data, including the applications that are running on the devices. Partners can integrate with Microsoft's endpoint solutions to verify device and app security, enforce least privilege policies, and prepare in advance for breaches.
This guidance is for software providers and technology partners who want to enhance their endpoint security solutions by integrating with Microsoft products.
Zero Trust integration for Endpoints guide
This integration guide includes instructions for integrating with the following products:
- Microsoft Defender for Endpoint, which helps enterprise networks prevent, detect, investigate, and respond to advanced threats.
- Microsoft Intune, which provides protection and security for the devices that employees use and the applications that run on those devices.
- Microsoft Defender for IoT, which provides security across your operational technology (OT) networks.
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. It uses a combination of endpoint behavioral sensors, cloud security analytics, and threat intelligence.
Defender for Endpoint supports non-Microsoft applications to help enhance the detection, investigation, and threat intelligence capabilities of the platform. In addition, partners can extend their existing security offerings on top of the open framework and a rich and complete set of APIs to build extensions and integrations with Defender for Endpoint.
The Microsoft Defender for Endpoint partner opportunities and scenarios page describes several categories of integrations that are supported. In addition, other ideas for integration scenarios can include:
- Streamlining threat remediation: Microsoft Defender for Endpoint can take immediate or operator-assisted responses to address alerts. Partners can use the endpoint response actions such as machine isolation, file quarantine to block IoC across the managed endpoint.
- Combine network access control with device security: Risk or exposure scores can be used to implement and enforce policies for network and application access.
To become a Defender for Endpoint solution partner, you need to follow and complete the steps found at Become a Microsoft Defender for Endpoint partner.
Microsoft Intune
Microsoft Intune, which includes the Microsoft Intune service and Microsoft Configuration Manager, provides protection and security for the devices that employees use and the applications that run on those devices. Intune includes device compliance policies that ensure employees are accessing applications and data from devices that meet company security policies. It also includes application protection policies which provide application-based security controls for both fully managed and employee-owned devices.
To integrate with Microsoft Intune, ISVs use Microsoft Graph and the Microsoft Intune application management SDK. Intune’s integration with the Microsoft Graph API allows any of the same functionality offered by the administrator console for Intune. Information such as device compliance state, compliance policy configuration, application protection policy settings and more can be found through the Microsoft Graph API. Additionally, you can automate tasks in Intune that further enhance your customer’s Zero Trust story. General guidance for Working with Intune in Microsoft Graph is available in the Microsoft Graph documentation repo. Here, we focus on scenarios related to Zero Trust.
Verify devices follow security and compliance standards
ISV solutions can use Intune’s device compliance and policy information to support the Zero Trust principle of Verify Explicitly. The compliance data about users and devices from Intune allows the ISV's application to determine a device's risk posture as it relates to use of the application. By doing these verifications, the ISV ensures that devices using the service are compliant with the customers’ security and compliance standards and policies.
The Microsoft Graph API allows ISVs to integrate with Intune through a set of RESTful APIs. These APIs are the same ones used by the Microsoft Intune admin center to view, create, manage, deploy, and report on all actions, data, and activity in Intune. Items of specific interest for ISVs supporting Zero Trust initiatives are the ability to view device compliance state and configure compliance rules and policies. See Microsoft's recommendations for using Microsoft Entra ID and Intune for Zero Trust configuration and compliance: Secure endpoints with Zero Trust. Intune’s compliance rules are foundational for device based Conditional Access support through Microsoft Entra ID. ISVs should also view the Conditional Access feature and APIs to understand how to complete scenarios for user and device compliance and Conditional Access.
Ideally as an ISV, your application connects to the Microsoft Graph APIs as a cloud application and establishes a service-to-service connection. Multitenant applications provide ISVs with centralized application definition and control and enable customers to individually consent to the ISV application operating against their tenant data. Review the information on Tenancy in Microsoft Entra ID for registering and creating single or multitenant Microsoft Entra Applications. Your application’s authentication can use Microsoft Entra ID for single sign-on.
After creating your application, you need to access the device and compliance information using the Microsoft Graph API. Documentation for using Microsoft Graph can be found at the Microsoft Graph dev center. The Microsoft Graph API is a RESTful set of APIs that follow ODATA standards for data access and querying.
Getting Device compliance state
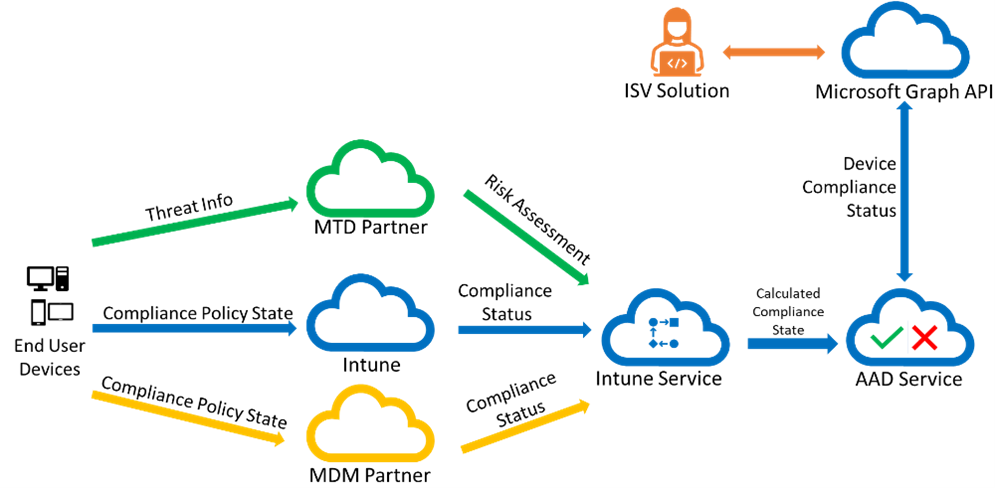
This diagram shows how device compliance information flows from the device to your ISV solution. End user devices receive policies from Intune, a mobile threat defense (MTD) partner, or a mobile device management (MDM) compliance partner. Once the compliance information is gathered from the devices, Intune calculates the overall compliance state of each device and stores that in Microsoft Entra ID. By using the Microsoft Graph API, your solution can read and respond to the device compliance state, applying the principles of Zero Trust.
When enrolled with Intune, a device record is created in Intune with other device details, including the device compliance state. Intune forwards the device compliance state to Microsoft Entra ID, where Microsoft Entra ID also stores the compliance state with each device. By making a GET on https://graph.microsoft.com/v1.0/deviceManagement/managedDevices, you can see all the enrolled devices for a tenant and their compliance state. Or you can query https://graph.microsoft.com/v1.0/devices to get a list of the Microsoft Entra registered and enrolled devices and their compliance state.
For example, this request:
GET https://graph.microsoft.com/v1.0/users/{usersId}/managedDevices/{managedDeviceId}
Returns:
HTTP/1.1 200 OK
Content-Type: application/json
Content-Length: 5095
{
"value": {
"@odata.type": "#microsoft.graph.managedDevice",
"id": "705c034c-034c-705c-4c03-5c704c035c70",
"userId": "User Id value",
"deviceName": "Device Name value",
"managedDeviceOwnerType": "company",
"enrolledDateTime": "2016-12-31T23:59:43.797191-08:00",
"lastSyncDateTime": "2017-01-01T00:02:49.3205976-08:00",
"complianceState": "compliant",
...
}
You can also retrieve a list of compliance policies, their deployments, and status of users and devices for those compliance policies. Information for calling Graph to get compliance policy information starts here: Get deviceCompliancePolicy - Microsoft Graph v1.0. A good background on device compliance policies and how they're used is here: Device compliance policies in Microsoft Intune - Azure.
After you identify a specific policy, you can query to get the state of a device for a particular compliance policy setting. For example, assuming a compliance policy was deployed to require a passcode on lock, query Get deviceComplianceSettingState for the specific state of that setting. This query indicates whether the device is compliant or noncompliant with the passcode lock setting. This same approach can be used for other device compliance policies that customers deployed.
Compliance information is foundational to Microsoft Entra ID’s Conditional Access feature. Intune determines the device compliance based on compliance policies and writes the compliance state to Microsoft Entra ID. Then, customers use Conditional Access policies to determine whether any actions are taken for noncompliance, including blocking the users from accessing corporate data from a noncompliant device.
Follow the least privilege access principle
An ISV integrating with Intune wants to ensure their application supports the Zero Trust principle to Apply Least Privilege Access. Intune integration supports two important methods of access control – delegated permissions or application permissions. The ISV's application must use one of the permission models. Delegated permissions give you fine grained control over the specific objects in Intune the application has access to but requires that an administrator sign-in with their credentials. By comparison, application permissions allow the ISV's app to access or control classes of data and objects, rather than specific individual objects, but doesn't require a user to sign in.
In addition to creating your application as a single-tenant or multitenant (preferred) application, you must declare the delegated or application permissions required by your application to access Intune information and perform actions against Intune. View information about getting started with permissions here: Configure app permissions for a web API.
Microsoft Defender for IoT
Operational technology (OT) network architectures often differ from traditional IT infrastructure, using unique technology with proprietary protocols. OT devices might also have aging platforms with limited connectivity and power, or specific safety requirements and unique exposures to physical attacks.
Deploy Microsoft Defender for IoT to apply Zero Trust principles to your OT network, monitoring traffic for anomalous or unauthorized behavior as traffic crosses sites and zones. Watch for threats and vulnerabilities specific to OT devices, mitigating risks as they're detected.
Speed operations by sharing Defender for IoT data across your security operations center (SOC) and other parts of your organization. Integrate with Microsoft services, such as Microsoft Sentinel and Defender for Endpoint, or other partner services, including both SIEM and ticketing systems. For example:
Forward on-premises alert data directly to SIEMs such as Splunk, IBM QRadar, and more. Splunk and IBM QRadar also support Event Hubs ingestion, which you can use to forward cloud alerts from Defender for IoT.
Integrate with ServiceNow's Operational Technology Manager to import Defender for IoT data to ServiceNow and risk-based action with production process context.
For more information, see:
- Get started with OT security monitoring
- Zero Trust and your OT networks
- Monitor with Zero Trust
- Defender for IoT integration catalog