אנונימיזציה של נתוני גילוי ענן
אנונימיזציה של נתוני גילוי ענן מאפשרת לך להגן על פרטיות המשתמשים. לאחר העלאת יומן הנתונים ל- יישומי ענן של Microsoft Defender, יומן הרישום מותן וכל פרטי שם המשתמש מוחלפים בשם משתמש מוצפן. באופן זה, כל הפעילויות בענן נשמרות אנונימיות. בעת הצורך, עבור חקירת אבטחה ספציפית (לדוגמה, הפרת אבטחה או פעילות משתמש חשודה), מנהלי מערכת יכולים לפתור את שם המשתמש האמיתי. אם למנהל מערכת יש סיבה לחשוד במשתמש מסוים, הוא יכול גם לחפש את שם המשתמש המוצפן של שם משתמש מוכר ולאחר מכן להתחיל לחקור באמצעות שם המשתמש המוצפן. כל המרה של שם משתמש מביקורת ביומן הפיקוח של הפורטל.
נקודות עיקריות:
- לא מאוחסן או מוצג מידע פרטי. רק מידע מוצפן.
- נתונים פרטיים מוצפנים באמצעות AES-128 עם מפתח ייעודי לכל דייר.
- פתרון שמות משתמש מתבצע באופן אד-הוק, לפי שם משתמש על-ידי פענוח שם משתמש מוצפן נתון.
- יכולות אנונימיות אינן נתמכות בעת שימוש בזרם "יישומי ענן של Defender Proxy".
כיצד פועלת אנונימיזציה של נתונים
קיימות שלוש דרכים להחלת אנונימיזציה של נתונים:
באפשרותך להגדיר את הנתונים מקובץ יומן רישום ספציפי לאנוניmized, על-ידי יצירת דוח תמונה חדש ובחירה באפשרות שנה אנונימיזציה של מידע פרטי.

באפשרותך להגדיר את הנתונים מהעלאה אוטומטית עבור מקור נתונים חדש לאנונימציה על-ידי בחירה באפשרות שנה אנונימיזציה של מידע פרטי בעת הוספת מקור הנתונים החדש.

באפשרותך להגדיר את ברירת המחדל ב- יישומי ענן של Defender כדי להפוך את כל הנתונים לאנונים משני דוחות התמונות מתוך קבצי יומן רישום שהועלו ודוחות רציפים מלקטי יומנים באופן הבא:
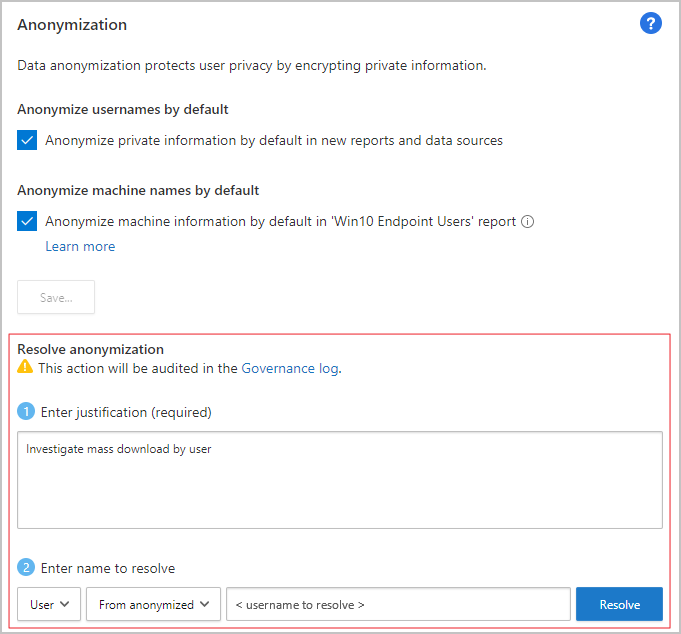
בתיבה פורטל Microsoft Defender, בחר הגדרות. לאחר מכן בחר אפליקציות ענן.
תחת גילוי ענן, בחר אנונימיזציה. כדי לשנות שם משתמש לאנוניmize כברירת מחדל, בחר באפשרות שנה אנונימית מידע פרטי כברירת מחדל בדוחות ובמקורות נתונים חדשים. באפשרותך גם לבחור באפשרות שנה את פרטי המכשיר כברירת מחדל בדוח 'נקודות קצה המנוהלות על-ידי Defender'.
בעת בחירת אנונימיזציה, ניתן יישומי ענן של Defender את יומן התעבורה ומחלצת תכונות נתונים ספציפיות.
יישומי ענן של Defender מחליף את שם המשתמש בשם משתמש מוצפן.
לאחר מכן הוא מנתח נתוני שימוש בענן ומפיק דוחות גילוי בענן בהתבסס על הנתונים ה אנונימיים.

עבור חקירה ספציפית, כגון חקירה של התראת שימוש חריגה, באפשרותך לפתור את שם המשתמש הספציפי בפורטל ולספק יישור עסקי.
הערה
השלבים הבאים פועלים גם עבור שמות מכשירים בכרטיסיה מכשירים .
כדי לפתור שם משתמש יחיד:
בחר את שלוש הנקודות בסוף השורה של המשתמש שברצונך לפתור ובחר באפשרות Deanonymize user.

בחלון המוקפץ, הזן את היישור לפתרון שם המשתמש ולאחר מכן בחר פתור. בשורה הרלוונטית, שם המשתמש שנפתר מוצג.
הערה
פעולה זו מביקורת.

ניתן להשתמש גם בדרך החלופית הבאה כדי לפתור שמות משתמש יחידים כדי לחפש את שם המשתמש המוצפן של שם משתמש מוכר.
בתיבה פורטל Microsoft Defender, בחר הגדרות. לאחר מכן בחר אפליקציות ענן.
תחת גילוי ענן, בחר אנונימיזציה. לאחר מכן, תחת אנונימיזציה ופתור שמות משתמש, הזן יישור לפתרון הבעיה.
תחת הזן שם משתמש כדי לפתור זאת, בחר מתוך אנונימיזציה והזן את שם המשתמש ה אנונימי, או בחר To anonymized והזן את שם המשתמש המקורי שברצונך לפתור. בחר פתור.
כדי לפתור שמות משתמש מרובים:
בחר את תיבות הסימון שמופיעות בעת ריחוף מעל סמלי המשתמשים על-ידי המשתמשים שברצונך לפתור, או, בפינה הימנית העליונה, בחר את תיבת הסימון בחירה בצובר .

בחר באפשרות Deanonymize user.
בחלון המוקפץ, הזן את היישור לפתרון שם המשתמש ולאחר מכן בחר פתור. בשורות הרלוונטיות, שמות המשתמש שזוהו מוצגים.
הערה
פעולה זו מביקורת.

הפעולה תיכלל ביומן הפיקוח של הפורטל.

השלבים הבאים
אם אתה נתקל בבעיות כלשהן, אנחנו כאן כדי לעזור. לקבלת סיוע או תמיכה עבור בעיית המוצר שלך, פתח כרטיס תמיכה.