כיצד יישומי ענן של Defender להגן על הסביבה האטלסית שלך
Atlassian היא פלטפורמת פיתוח מקוונת שיתופית ופיתוח תוכנה (כולל Confluence, Jira ו- Bitbucket). יחד עם היתרונות של שיתוף פעולה יעיל בענן, הנכסים הקריטיים ביותר של הארגון שלך עשויים להיחשף לאיומים. נכסים חשופים כוללים פרסומים, משימות וקבצים עם מידע שעשוי להיות רגיש, שיתוף פעולה ופרטי שותפות ועוד. מניעת חשיפה של נתונים אלה דורשת ניטור רציף כדי למנוע משחקנים זדוניים או משתתפי Insider שאינם מודעים לחשיפה של מידע רגיש.
חיבור Atlassian ל- יישומי ענן של Defender מספק לך תובנות משופרות לגבי הפעילויות של המשתמשים שלך ומספק זיהוי איומים עבור התנהגות חריגה. המחבר מכסה את כל המשתמשים בארגון המשתמשים בפלטפורמה האטלסית, ויציג פעילויות מפעילויות Confluence, Jira ופעילויות Bitbucket ספציפיות.
האיומים העיקריים כוללים:
חשבונות שנחשף לסכנה ואיומים פנימיים
מודעות אבטחה לא מספיקה
לא מנוהל הבא מכשיר משלך (BYOD)
שליטה ב Atlassian עם מדיניות
| סוג | שם |
|---|---|
| מדיניות זיהוי חריגות מוכללת |
פעילות מכתובות IP אנונימיות פעילות ממדינה נדירה פעילות מכתובות IP חשודות נסיעה בלתי אפשרית מספר נסיונות כניסה שנכשלו פעילויות ניהוליות חריגות פעילויות חריגות מתחזות |
| מדיניות פעילות | בנה מדיניות מותאמת אישית על-ידי הפעילויות האטלסיאניות. |
לקבלת מידע נוסף אודות יצירת מדיניות, ראה יצירת מדיניות.
הפיכת פקדי פיקוח לאוטומטיים
בנוסף לניטור אחר איומים פוטנציאליים, באפשרותך להחיל להפוך את פעולות הפיקוח הבאות של Atlassian לאוטומטיות כדי לפתור איומים שזוהו:
| סוג | פעולה |
|---|---|
| פיקוח על משתמשים | הודע למשתמש בהתראה (באמצעות Microsoft Entra מזהה) דרוש מהמשתמש להיכנס שוב (באמצעות Microsoft Entra מזהה) השעה משתמש (באמצעות Microsoft Entra מזהה) |
לקבלת מידע נוסף על תיקון איומים מאפליקציות, ראה פיקוח על אפליקציות מחוברות.
הגנה על אטלסיאן בזמן אמת
סקור את שיטות העבודה המומלצות שלנו לאבטחה ולשיתוף פעולה עם משתמשים חיצוניים, חסימה והגנה על ההורדה של נתונים רגישים למכשירים לא מנוהלים או מסיכונים.
ניהול תציבות אבטחה של SaaS
חבר את Atlassian כדי לקבל המלצות על הצבת אבטחה עבור Atlassian ב- Microsoft Secure Score. כדי לראות המלצות אבטחה עבור Atlassian ב- Microsoft Secure Score:
- רענן את המדיניות שלך על-ידי פתיחה ושמירה של כל מדיניות בפורטל האטלסיאני.
- ב- Microsoft Secure Score, בחר פעולות מומלצות וסנן לפי Product = Atlassian.
לדוגמה, המלצות עבור Atlassian כוללות:
- הפוך אימות רב-גורמי לזמין
- אפשר זמן קצוב להפעלה עבור משתמשי אינטרנט
- שיפור דרישות סיסמה
- אבטחת אפליקציות אטלסיאן למכשירים ניידים
- הגנה על נתונים של אפליקציה
לקבלת מידע נוסף, ראה:
חבר את אטלסיאן יישומי ענן של Microsoft Defender
סעיף זה מספק הוראות להתחברות יישומי ענן של Microsoft Defender המוצרים הקיימים שלך ב Atlassian באמצעות ממשקי ה- API של מחבר היישומים. חיבור זה מעניק לך ניראות על השימוש של הארגון שלך ב Atlassian ושליטה בו.
הערה
המחבר מכסה את כל המשתמשים בארגון המשתמשים בפלטפורמה האטלסית, ויציג פעילויות מפעילויות Confluence, Jira ופעילויות Bitbucket ספציפיות. לקבלת מידע נוסף על פעילויות אטלסיאניות, ראה פעילויות יומן ביקורת אטלסית.
דרישות מוקדמות
- התוכנית Atlassian Access נדרשת.
- עליך להיות חתום כמנהל מערכת של ארגון ב Atlassian.
קביעת תצורה של אטלסיאן
היכנס לפורטל מרכז הניהול אטלסיאן באמצעות חשבון מנהל מערכת.
עבור אל הגדרות - מפתחות> API ולאחר מכן צור מפתח API. (ניתן למצוא כאן גם תיעוד Atlassian ליצירת מפתחות API).
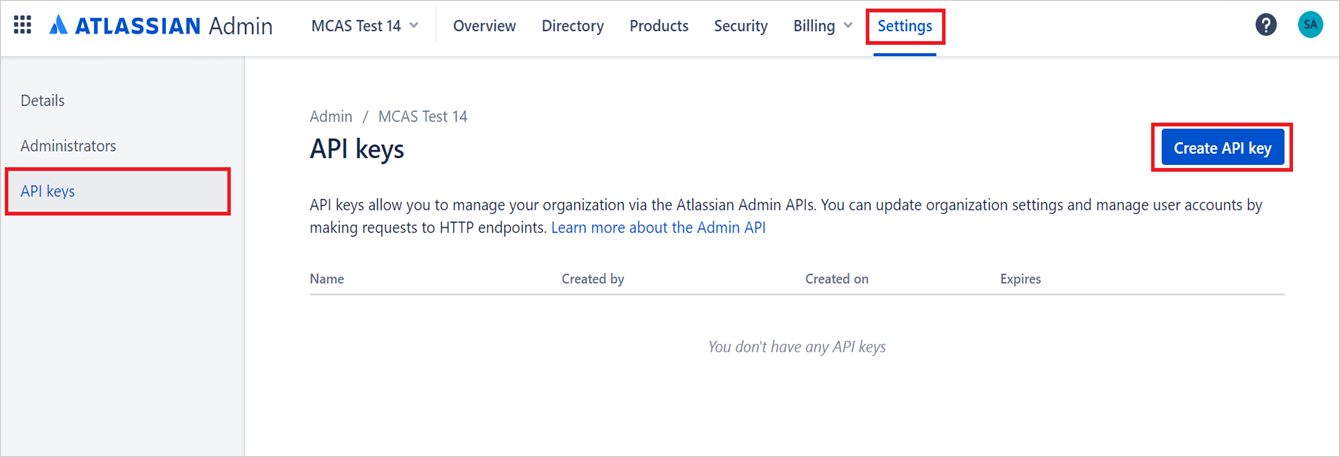
תן את הערכים הבאים למפתח ה- API:
שם: אתה יכול לתת כל שם. השם המומלץ הוא יישומי ענן של Microsoft Defender כך שתוכל להיות מודע לשילוב זה.
התוקף יפוג בתאריך: הגדר את תאריך התפוגה כשנה מתאריך היצירה (זהו הזמן המרבי של Atlassian עבור תאריך התפוגה).
הערה
בהתאם לדרישות ה- API של Atlassian, יהיה עליך ליצור כל שנה מפתח API עבור שילוב זה.

לאחר בחירת צור, העתק את מזהה הארגון ואת מפתח ה- API. תזדקק לו מאוחר יותר.
הערה
אמת את התחום שלך: כדי לראות את המשתמשים שלך ב- Atlassian ואת הפעילויות שלהם ב- יישומי ענן של Defender, עליך לאמת את התחום שלך. ב- Atlassian, תחומים משמשים כדי לקבוע אילו חשבונות משתמשים יכולים להיות מנוהלים על-ידי הארגון שלך. לא תראה את המשתמשים ואת הפעילויות שלהם אם התחומים שלהם אינם מאומתים בתצורה האטלסית. כדי לאמת תחומים ב- Atlassian, ראה אימות תחום לניהול חשבונות.
קביעת תצורה של יישומי ענן של Defender
בתיבה פורטל Microsoft Defender, בחר הגדרות. לאחר מכן בחר אפליקציות ענן. תחת אפליקציות מחוברות, בחר מחברי אפליקציות.
בדף מחברים של אפליקציות, בחר +חבר יישום ואחריו Atlassian.
בחלון הבא, תן למופע שם תיאורי ובחר הבא.

בעמוד הבא, הזן את מזהה הארגון ואת מפתח ה- API ששמרת קודם לכן.
הערה
- החיבור הראשון עשוי להימשך עד ארבע שעות כדי לקבל את כל המשתמשים ואת הפעילויות שלהם.
- הפעילויות שיוצגו הן הפעילויות שנוצרו מהרגע שבו המחבר מחובר.
- פעילויות מ יומן הביקורת "גישה אטלסית" מובאות על-ידי אפליקציות Defender for Cloud. פעילויות אחרות אינן מובאות כעת. ראה יומני ביקורת מוצרים.
- לאחר שמצב המחבר מסומןכ'מחובר', המחבר פועל ותקין.
ביטול ותחדש של מפתחות API
Microsoft ממליצה להשתמש במקשים קצרים או באסימונים קצרים לחיבור אפליקציות כשיטות עבודה מומלצות לאבטחה.
אנו ממליצים לרענן את מפתח ה- API של האטלסיאן כל 6 חודשים כשיטות עבודה מומלצות. כדי לרענן את המפתח, בטל את מפתח ה- API הקיים וצור מפתח חדש.
כדי לבטל מפתח API, נווט אל admin.atlassian.com>>ה- API של ההגדרות, קבע את מפתח ה- API המשמש לשילוב ובחר בטל.
צור מחדש מפתח API בפורטל הניהול של Atlassian באמצעות השלבים המתוארים לעיל.
לאחר מכן, עבור אל הדף מחברים של אפליקציות בפורטל Microsoft Defender וערוך את המחבר:

הזן את מפתח ה- API החדש שנוצר ובחר התחבר אטלסיאן.
בתיבה פורטל Microsoft Defender, בחר הגדרות. לאחר מכן בחר אפליקציות ענן. תחת אפליקציות מחוברות, בחר מחברי אפליקציות. ודא שמצב מחבר היישומים המחובר מחובר.
הערה
כברירת מחדל, מפתח ה- API חוקי למשך שנה אחת, והוא פג באופן אוטומטי לאחר שנה.
תוכן קשור
אבטחת שיתוף פעולה עם משתמשים חיצוניים על-ידי אכיפת פקדי הפעלה בזמן אמת
זהה איומים בענן, חשבונות שנחשף לסכנה ותוכנות Insider זדוניות
דרג מגבלות ומגבלות
מגבלות קצב כוללות 1000 בקשות לדקה (לכל מפתח API/מופע מחבר).
לקבלת מידע נוסף אודות מגבלת ה- API של Atlassian, ראה ממשקי REST API של מנהל Atlassian.
המגבלות כוללות :
פעילויות יוצגו ב- יישומי ענן של Defender רק עבור משתמשים בעלי תחום מאומת.
מפתח ה- API כולל תקופת תפוגה מרבית של שנה אחת. לאחר שנה אחת, תצטרך ליצור מפתח API נוסף מהפורטל מרכז הניהול Atlassian ולהחליף אותו עבור מפתח ה- API הישן במסוף יישומי ענן של Defender.
לא תוכל לראות ב- יישומי ענן של Defender אם משתמש הוא מנהל מערכת או לא.
פעילויות המערכת מוצגות עם שם החשבון של המערכת הפנימית של האטלסיאן .
השלבים הבאים
אם אתה נתקל בבעיות כלשהן, אנחנו כאן כדי לעזור. לקבלת סיוע או תמיכה עבור בעיית המוצר שלך, פתח כרטיס תמיכה.