Catatan
Akses ke halaman ini memerlukan otorisasi. Anda dapat mencoba masuk atau mengubah direktori.
Akses ke halaman ini memerlukan otorisasi. Anda dapat mencoba mengubah direktori.
Artikel ini mencantumkan beberapa contoh kondisi penetapan peran untuk mengontrol akses ke Azure Blob Storage.
Penting
Kontrol akses berbasis atribut Azure (Azure ABAC) sekarang tersedia secara umum (GA) untuk mengendalikan akses ke Azure Blob Storage, Azure Data Lake Storage Gen2, dan Azure Queues dengan menggunakan atribut request, resource, environment, dan principal pada tingkat kinerja akun penyimpanan standar dan premium. Saat ini, atribut permintaan daftar blob dan atribut permintaan cuplikan untuk namespace hierarkis sedang dalam PRATINJAU. Untuk informasi lengkap tentang status fitur ABAC untuk Azure Storage, lihat Status fitur kondisi di Azure Storage.
Lihat Ketentuan Penggunaan Tambahan untuk Pratinjau Microsoft Azure untuk persyaratan hukum yang berlaku pada fitur Azure dalam versi beta, pratinjau, atau belum dirilis secara umum.
Prasyarat
Untuk informasi tentang prasyarat untuk menambah atau mengedit kondisi penetapan peran, lihat Prasyarat kondisi.
Ringkasan contoh dalam artikel ini
Gunakan tabel berikut untuk menemukan contoh yang sesuai dengan skenario ABAC Anda dengan cepat. Tabel ini mencakup deskripsi singkat tentang skenario, ditambah daftar atribut yang digunakan dalam contoh menurut sumber (lingkungan, utama, permintaan, dan sumber daya).
Penanda Indeks Blob
Bagian ini mencakup contoh yang melibatkan tag indeks blob.
Penting
Meskipun Read content from a blob with tag conditions suboperasi saat ini didukung untuk kompatibilitas dengan kondisi yang diterapkan selama pratinjau fitur ABAC, suboperasi tersebut telah dihapus dan Microsoft merekomendasikan menggunakan tindakan Read a blob sebagai gantinya.
Saat mengonfigurasi kondisi ABAC di portal Microsoft Azure, Anda mungkin melihat TIDAK DIGUNAKAN LAGI: Membaca konten dari blob dengan kondisi tag. Microsoft merekomendasikan untuk menghapus operasi dan menggantinya dengan tindakan Read a blob.
Jika Anda menulis kondisi Anda sendiri di mana Anda ingin membatasi akses baca berdasarkan kondisi tag, silakan lihat Contoh: Membaca blob dengan tag indeks blob.
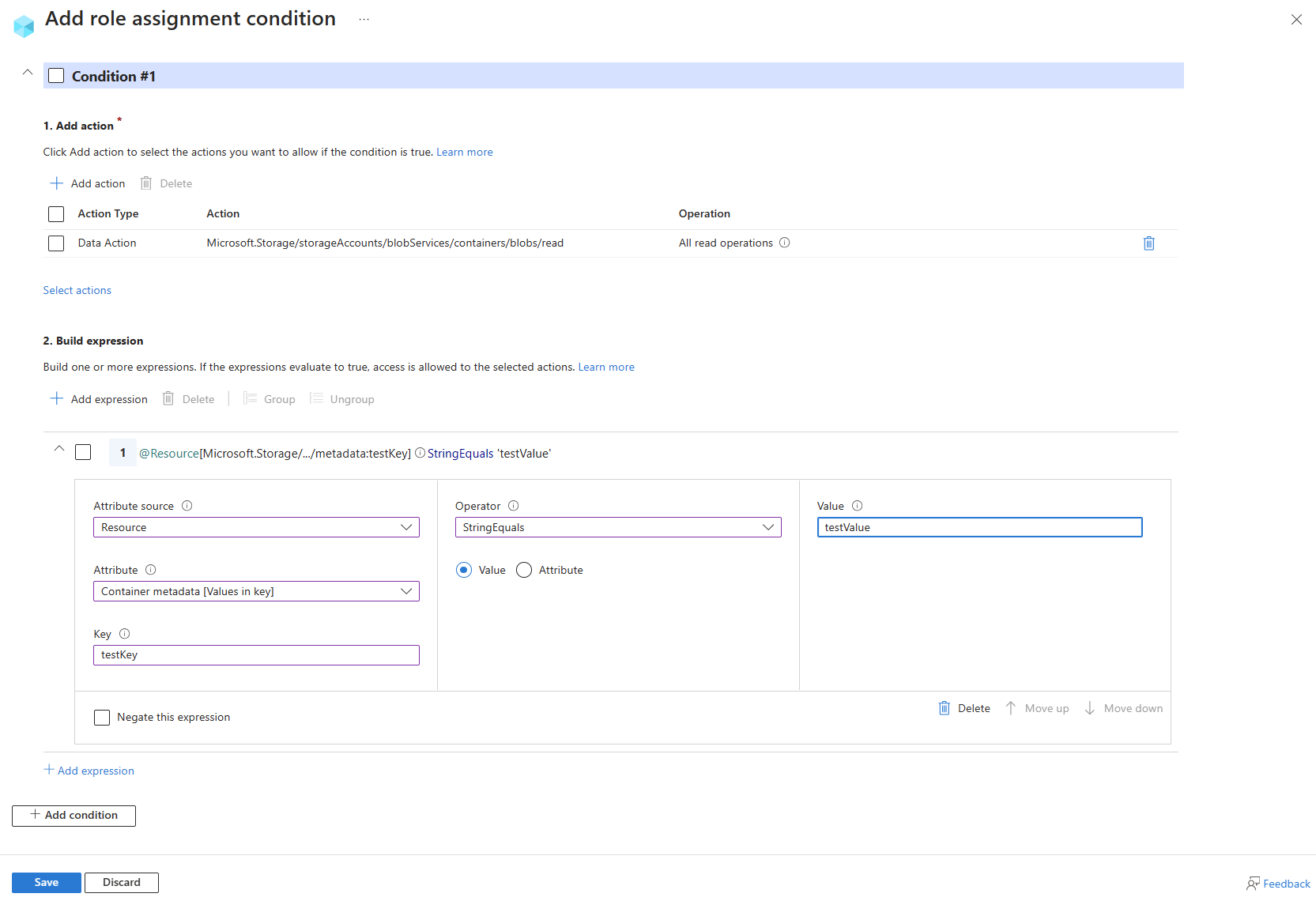
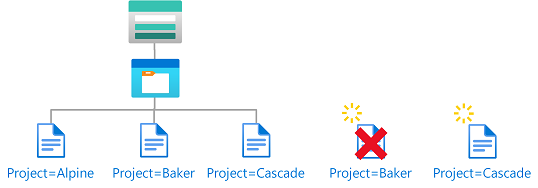
Contoh: Membaca blob dengan tag indeks
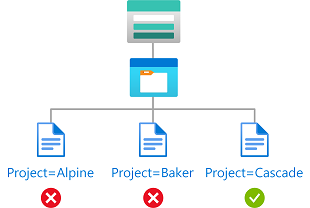
Kondisi ini memungkinkan pengguna untuk membaca blob dengan kunci tag indeks blob bernama Project dengan nilai Cascade. Upaya untuk mengakses blob tanpa tag kunci-nilai ini tidak diizinkan.
Agar kondisi ini efektif untuk prinsip keamanan, Anda harus menambahkannya ke semua penetapan peran untuk mereka yang menyertakan tindakan berikut:
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan editor visual portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Membaca sebuah blob |
| Sumber atribut | Sumber Daya |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] |
| Kunci | {keyName} |
| Pengoperasi | StringEquals |
| Nilai | {keyValue} |
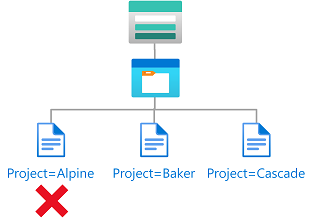
Contoh: Blob baru harus menyertakan tag indeks blob
Kondisi ini mengharuskan setiap blob baru harus menyertakan kunci tag indeks blob Project dan nilai Cascade.
Ada dua tindakan yang memungkinkan Anda membuat blob baru, jadi Anda harus menargetkan keduanya. Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan salah satu tindakan berikut:
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Menulis pada blob dengan tag indeks blob Menulis pada blob dengan tag indeks blob |
| Sumber atribut | Permohonan |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] |
| Kunci | {keyName} |
| Pengoperasi | StringEquals |
| Nilai | {keyValue} |
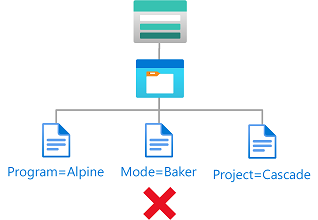
Contoh: Blob yang sudah ada harus memiliki kunci indeks tag blob
Kondisi ini mengharuskan setiap blob yang ada ditandai dengan setidaknya salah satu kunci tag indeks blob yang diizinkan: Proyek atau Program. Kondisi ini berguna untuk menambahkan tata kelola ke blob yang ada.
Ada dua tindakan yang memungkinkan Anda memperbarui tag pada blob yang ada, jadi Anda harus menargetkan keduanya. Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan salah satu tindakan berikut:
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/tags/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Menulis pada blob dengan tag indeks blob Menulis tag indeks blob |
| Sumber atribut | Permohonan |
| Karakteristik | Tag indeks blob [Kunci] |
| Pengoperasi | ForAllOfAnyValues:StringEquals |
| Nilai | {keyName1} {keyName2} |
Contoh: Blob yang sudah ada harus memiliki kunci dan nilai tag indeks pada blob
Kondisi ini mengharuskan setiap blob yang ada memiliki kunci tag indeks blob bernama Project dan nilai Cascade, Baker, atau Skagit. Kondisi ini berguna untuk menambahkan tata kelola ke blob yang ada.
Ada dua tindakan yang memungkinkan Anda memperbarui tag pada blob yang ada, jadi Anda harus menargetkan keduanya. Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan salah satu tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/tags/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Menulis pada blob dengan tag indeks blob Menulis tag indeks blob |
| Sumber atribut | Permohonan |
| Karakteristik | Tag indeks blob [Kunci] |
| Pengoperasi | ForAnyOfAnyValues:StringEquals |
| Nilai | {keyName} |
| Pengoperasi | Dan |
| Ekspresi 2 | |
| Sumber atribut | Permohonan |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] |
| Kunci | {keyName} |
| Pengoperasi | ForAllOfAnyValues:StringEquals |
| Nilai | {keyValue1} {keyValue2} {keyValue3} |
Nama kontainer blob atau jalurnya
Bagian ini mencakup contoh yang menunjukkan cara membatasi akses ke objek berdasarkan nama kontainer atau jalur blob.
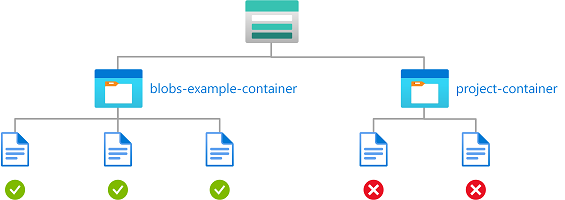
Contoh: Membaca, menulis, atau menghapus blob dalam kontainer dengan nama tertentu
Kondisi ini memungkinkan pengguna untuk membaca, menulis, atau menghapus blob dalam kontainer penyimpanan bernama blobs-example-container. Kondisi ini berguna untuk berbagi kontainer penyimpanan tertentu dengan pengguna lain dalam langganan.
Ada lima tindakan untuk membaca, menulis, dan menghapus blob yang ada. Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan salah satu tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/delete |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. Tambahkan jika akun penyimpanan yang disertakan dalam kondisi ini mengaktifkan namespace hierarkis atau mungkin diaktifkan di masa mendatang. |
Suboperasi tidak digunakan dalam kondisi ini karena suboperasi hanya diperlukan ketika kondisi ditulis berdasarkan tag.
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Hapus blob Membaca sebuah blob Menulis ke blob Membuat blob atau rekam jepret, atau menambahkan data Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama kontainer |
| Pengoperasi | StringEquals |
| Nilai | {containerName} |
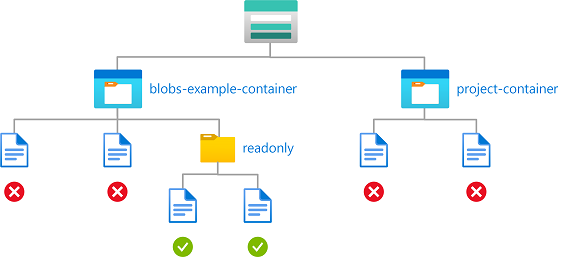
Contoh: Membaca blob dalam kontainer bernama dengan jalur
Kondisi ini memungkinkan akses baca ke kontainer penyimpanan bernama "blobs-example-container" dengan jalur blob "readonly/*". Kondisi ini berguna untuk berbagi bagian tertentu dari kontainer penyimpanan untuk akses baca dengan pengguna lain dalam langganan.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. Tambahkan jika akun penyimpanan yang disertakan dalam kondisi ini mengaktifkan namespace hierarkis atau mungkin diaktifkan di masa mendatang. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Membaca sebuah blob Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama kontainer |
| Pengoperasi | StringEquals |
| Nilai | {containerName} |
| Ekspresi 2 | |
| Pengoperasi | Dan |
| Sumber atribut | Sumber Daya |
| Karakteristik | Jalur blob |
| Pengoperasi | StringLike |
| Nilai | {pathString} |
Contoh: Membaca atau mencantumkan blob pada kontainer yang diberi nama dengan spesifik jalur.
Kondisi ini memungkinkan akses baca dan juga mencantumkan akses ke kontainer penyimpanan bernama blobs-example-container dengan jalur blob readonly/*. Kondisi #1 berlaku untuk tindakan baca tidak termasuk blob daftar. Kondisi #2 berlaku untuk mencantumkan blob. Kondisi ini berguna untuk berbagi bagian tertentu dari kontainer penyimpanan untuk akses baca atau daftar dengan pengguna lain dalam langganan.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. Tambahkan jika akun penyimpanan yang disertakan dalam kondisi ini mengaktifkan namespace hierarkis atau mungkin diaktifkan di masa mendatang. |

Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
Nota
Portal Microsoft Azure menggunakan prefiks='' untuk mencantumkan blob dari direktori akar kontainer. Setelah kondisi ditambahkan dengan operasi daftar blob menggunakan awalan StringStartsWith 'readonly/', pengguna yang ditargetkan tidak akan dapat melihat daftar blob dari direktori akar kontainer di portal Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Membaca sebuah blob Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama kontainer |
| Pengoperasi | StringEquals |
| Nilai | {containerName} |
| Ekspresi 2 | |
| Pengoperasi | Dan |
| Sumber atribut | Sumber Daya |
| Karakteristik | Jalur blob |
| Pengoperasi | StringStartsWith |
| Nilai | {pathString} |
| Kondisi #2 | Pengaturan |
|---|---|
| Tindakan |
Daftar blob Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama kontainer |
| Pengoperasi | StringEquals |
| Nilai | {containerName} |
| Ekspresi 2 | |
| Pengoperasi | Dan |
| Sumber atribut | Permohonan |
| Karakteristik | Awalan blob |
| Pengoperasi | StringStartsWith |
| Nilai | {pathString} |
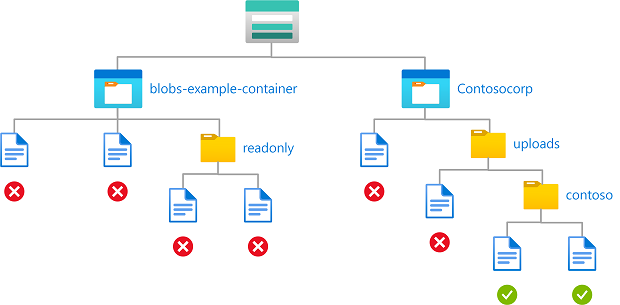
Contoh: Menulis blob di dalam kontainer bernama dengan menentukan jalur
Kondisi ini memungkinkan mitra (pengguna tamu Microsoft Entra) untuk meletakkan file ke dalam kontainer penyimpanan bernama Contosocorp dengan jalur unggahan/contoso/*. Kondisi ini berguna untuk memungkinkan pengguna lain memasukkan data ke dalam kontainer penyimpanan.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. Tambahkan jika akun penyimpanan yang disertakan dalam kondisi ini mengaktifkan namespace hierarkis atau mungkin diaktifkan di masa mendatang. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Menulis ke blob Membuat blob atau rekam jepret, atau menambahkan data Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama kontainer |
| Pengoperasi | StringEquals |
| Nilai | {containerName} |
| Ekspresi 2 | |
| Pengoperasi | Dan |
| Sumber atribut | Sumber Daya |
| Karakteristik | Jalur blob |
| Pengoperasi | StringLike |
| Nilai | {pathString} |
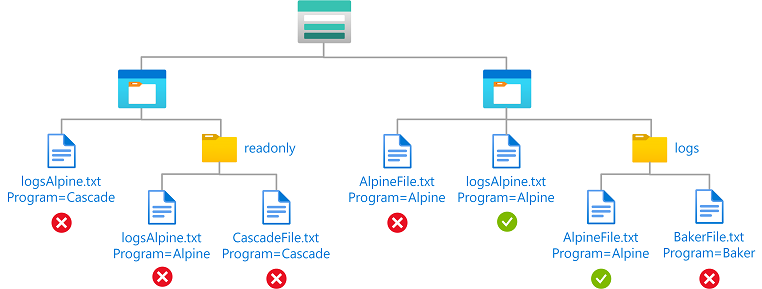
Contoh: Membaca blob dengan tag indeks blob dan jalur
Kondisi ini memungkinkan pengguna untuk membaca blob dengan kunci tag indeks blob Program, nilai Alpine, dan jalur blob log*. Jalur blob dari log* juga menyertakan nama blob.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Membaca sebuah blob |
| Sumber atribut | Sumber Daya |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] |
| Kunci | {keyName} |
| Pengoperasi | StringEquals |
| Nilai | {keyValue} |
| Kondisi #2 | Pengaturan |
|---|---|
| Tindakan | Membaca sebuah blob |
| Sumber atribut | Sumber Daya |
| Karakteristik | Jalur blob |
| Pengoperasi | StringLike |
| Nilai | {pathString} |
Metadata blob kontainer
Contoh: Membaca blob dalam kontainer dengan metadata tertentu
Kondisi ini memungkinkan pengguna membaca blob dalam kontainer blob dengan pasangan kunci/nilai metadata tertentu.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Membaca sebuah blob |
| Sumber atribut | Sumber Daya |
| Karakteristik | Metadata kontainer |
| Pengoperasi | StringEquals |
| Nilai | {containerName} |
Contoh: Menulis atau menghapus blob dalam kontainer dengan metadata tertentu
Kondisi ini memungkinkan pengguna untuk menulis atau menghapus blob dalam kontainer blob dengan pasangan kunci/nilai metadata tertentu.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/delete |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Menulis ke blob Hapus blob |
| Sumber atribut | Sumber Daya |
| Karakteristik | Metadata kontainer |
| Pengoperasi | StringEquals |
| Nilai | {containerName} |
Versi blob atau cuplikan blob
Bagian ini mencakup contoh yang menunjukkan cara membatasi akses ke objek berdasarkan versi blob atau rekam jepret.
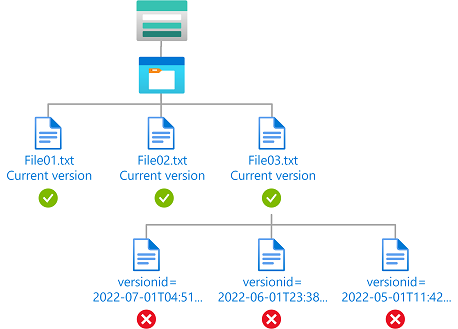
Contoh: Hanya membaca versi blob saat ini
Kondisi ini memungkinkan pengguna untuk hanya membaca versi blob saat ini. Pengguna tidak dapat membaca versi blob lainnya.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Membaca sebuah blob Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Sumber Daya |
| Karakteristik | Versi Saat Ini |
| Pengoperasi | BoolEquals |
| Nilai | Benar |
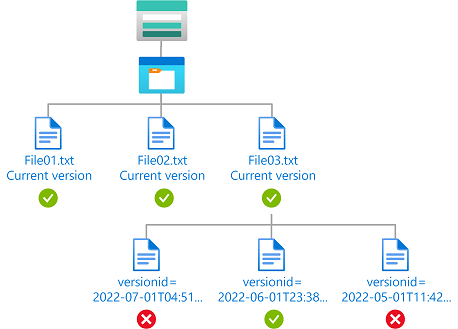
Contoh: Baca versi blob terkini dan versi blob tertentu
Kondisi ini memungkinkan pengguna untuk membaca versi blob saat ini serta membaca blob dengan ID versi 2022-06-01T23:38:32.8883645Z. Pengguna tidak dapat membaca versi blob lainnya. Atribut ID Versi hanya tersedia untuk akun penyimpanan di mana namespace hierarkis tidak diaktifkan.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Membaca sebuah blob |
| Sumber atribut | Permohonan |
| Karakteristik | ID Versi |
| Pengoperasi | DateTimeEquals |
| Nilai | <blobVersionId> |
| Ekspresi 2 | |
| Pengoperasi | Atau |
| Sumber atribut | Sumber Daya |
| Karakteristik | Versi Saat Ini |
| Pengoperasi | BoolEquals |
| Nilai | Benar |
Contoh: Menghapus versi blob lama
Kondisi ini memungkinkan pengguna untuk menghapus versi blob yang lebih lama dari 06/01/2022 untuk melakukan pembersihan. Atribut ID Versi hanya tersedia untuk akun penyimpanan di mana namespace hierarkis tidak diaktifkan.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/delete |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/deleteBlobVersion/action |
Diagram menunjukkan kondisi penghapusan akses ke versi blob lama.
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Hapus blob Menghapus sebuah versi dari blob |
| Sumber atribut | Permohonan |
| Karakteristik | ID Versi |
| Pengoperasi | DateTimeLessThan |
| Nilai | <blobVersionId> |
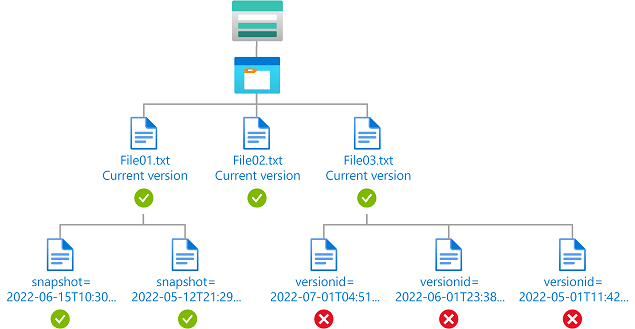
Contoh: Baca versi blob saat ini dan rekaman jepretan blob apa pun
Kondisi ini memungkinkan pengguna untuk membaca versi blob saat ini dan rekam jepret blob apa pun. Atribut ID Versi hanya tersedia untuk akun penyimpanan di mana namespace hierarkis tidak diaktifkan. Atribut Snapshot tersedia untuk akun penyimpanan di mana namespace hierarkis tidak diaktifkan dan saat ini dalam pratinjau untuk akun penyimpanan tempat namespace hierarki diaktifkan.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Membaca sebuah blob Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Permohonan |
| Karakteristik | Snapshot |
| Ada | Diperiksa |
| Ekspresi 2 | |
| Pengoperasi | Atau |
| Sumber atribut | Sumber Daya |
| Karakteristik | Versi Saat Ini |
| Pengoperasi | BoolEquals |
| Nilai | Benar |
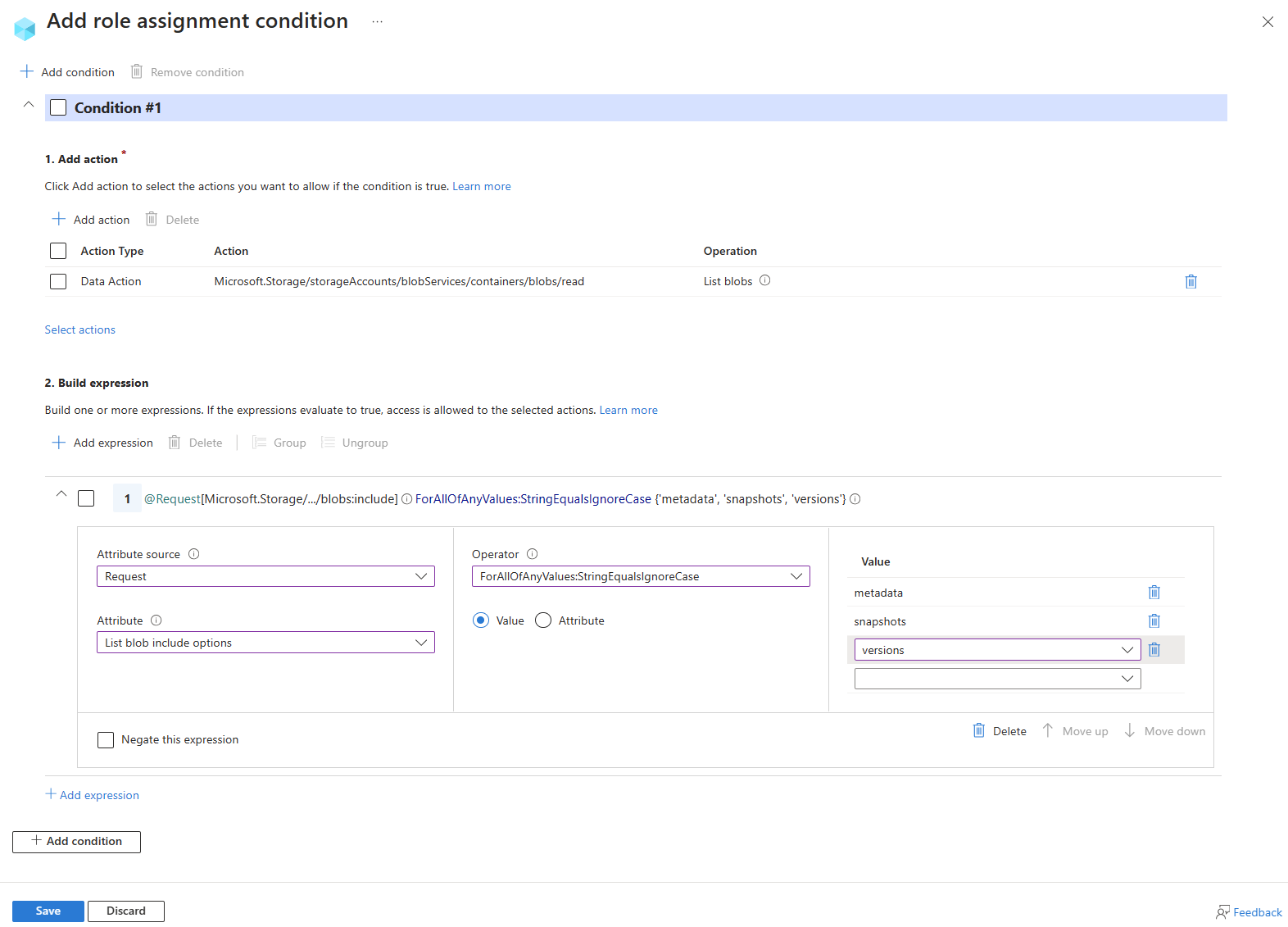
Contoh: Izinkan operasi pencatatan blob untuk menyertakan metadata blob, snapshot, atau versi
Kondisi ini memungkinkan pengguna untuk mencantumkan blob dalam kontainer dan menyertakan metadata, rekam jepret, dan informasi versi. Atribut Daftar blob yang disertakan tersedia untuk akun penyimpanan yang namespace hierarkis tidak diaktifkan.
Nota
List blobs include adalah atribut permintaan, dan berfungsi dengan mengizinkan atau membatasi nilai-nilai dalam include parameter saat memanggil operasi List Blobs. Nilai dalam include parameter dibandingkan dengan nilai yang ditentukan dalam kondisi menggunakan operator perbandingan lintas produk. Jika hasil perbandingan adalah benar, List Blobs permintaan diizinkan. Jika saat perbandingan bernilai false, permintaan List Blobs ditolak.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Daftar blob |
| Sumber atribut | Permohonan |
| Karakteristik | Daftar blob mencakup |
| Pengoperasi | ForAllOfAnyValues:StringEqualsIgnoreCase |
| Nilai | {'metadata', 'cuplikan data', 'versi'} |
Contoh: Membatasi operasi daftar blob dengan tidak menyertakan metadata blob
Kondisi ini membatasi pengguna untuk mencantumkan blob saat metadata disertakan dalam permintaan. Atribut Daftar blob yang disertakan tersedia untuk akun penyimpanan yang namespace hierarkis tidak diaktifkan.
Nota
List blobs include adalah atribut permintaan, dan berfungsi dengan mengizinkan atau membatasi nilai-nilai dalam include parameter saat memanggil operasi List Blobs. Nilai dalam include parameter dibandingkan dengan nilai yang ditentukan dalam kondisi menggunakan operator perbandingan lintas produk. Jika hasil perbandingan adalah benar, List Blobs permintaan diizinkan. Jika saat perbandingan bernilai false, permintaan List Blobs ditolak.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Daftar blob |
| Sumber atribut | Permohonan |
| Karakteristik | Daftar blob mencakup |
| Pengoperasi | ForAllOfAllValues:StringNotEquals |
| Nilai | {'metadata'} |
Namespace hierarkis
Bagian ini mencakup contoh yang menunjukkan cara membatasi akses ke objek berdasarkan apakah namespace hierarki diaktifkan untuk akun penyimpanan.
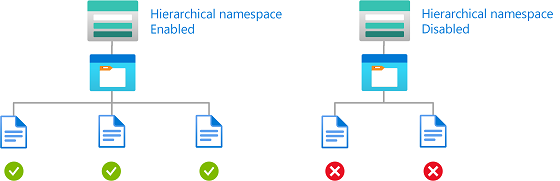
Contoh: Hanya membaca akun penyimpanan dengan namespace hierarki diaktifkan
Kondisi ini memungkinkan pengguna untuk hanya membaca blob di akun penyimpanan dengan namespace hierarki diaktifkan. Kondisi ini hanya berlaku pada cakupan grup sumber daya atau yang lebih tinggi.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Membaca sebuah blob Semua operasi data untuk akun dengan namespace hierarki diaktifkan (jika berlaku) |
| Sumber atribut | Sumber Daya |
| Karakteristik | Apakah namespace hierarki telah diaktifkan |
| Pengoperasi | BoolEquals |
| Nilai | Benar |
Ruang lingkup enkripsi
Bagian ini mencakup contoh yang menunjukkan cara membatasi akses ke objek dengan cakupan enkripsi yang disetujui.
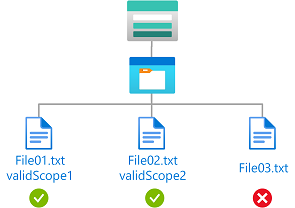
Contoh: Membaca blob dengan cakupan enkripsi tertentu
Kondisi ini memungkinkan pengguna untuk membaca blob yang dienkripsi dalam cakupan enkripsi validScope1 atau validScope2.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Membaca sebuah blob |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama cakupan enkripsi |
| Pengoperasi | ForAnyOfAnyValues:StringEquals |
| Nilai | <scopeName> |
Contoh: Membaca atau menulis blob di akun penyimpanan bernama dengan cakupan enkripsi tertentu
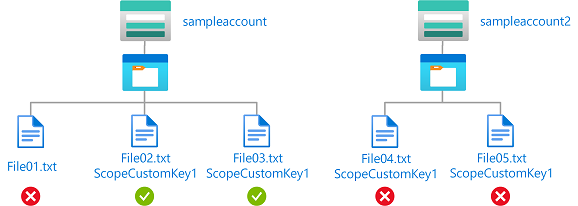
Kondisi ini memungkinkan pengguna untuk membaca atau menulis blob di akun penyimpanan bernama sampleaccount dan dienkripsi dengan cakupan enkripsi ScopeCustomKey1. Jika blob tidak dienkripsi atau didekripsi dengan ScopeCustomKey1, permintaan akan ditolak.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Nota
Karena cakupan enkripsi untuk akun penyimpanan yang berbeda bisa berbeda, disarankan untuk menggunakan storageAccounts:name atribut dengan encryptionScopes:name atribut untuk membatasi cakupan enkripsi tertentu agar diizinkan.
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan |
Membaca sebuah blob Menulis ke blob Membuat blob atau rekam jepret, atau menambahkan data |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama akun |
| Pengoperasi | StringEquals |
| Nilai | <namaAkun> |
| Ekspresi 2 | |
| Pengoperasi | Dan |
| Sumber atribut | Sumber Daya |
| Karakteristik | Nama cakupan enkripsi |
| Pengoperasi | ForAnyOfAnyValues:StringEquals |
| Nilai | <scopeName> |
Atribut utama
Bagian ini mencakup contoh yang menunjukkan cara membatasi akses ke objek berdasarkan prinsip keamanan kustom.
Contoh: Membaca atau menulis blob berdasarkan tag indeks blob dan atribut keamanan kustom
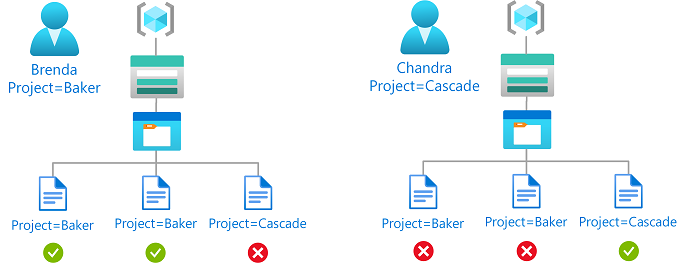
Kondisi ini memungkinkan akses baca atau tulis ke blob jika pengguna memiliki atribut keamanan kustom yang cocok dengan tag indeks blob.
Misalnya, jika Brenda memiliki atribut Project=Baker, dia hanya dapat membaca atau menulis blob dengan Project=Baker tag indeks blob. Demikian pula, Chandra hanya dapat membaca atau menulis blob dengan Project=Cascade.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Untuk informasi selengkapnya, lihat Mengizinkan akses baca ke blob berdasarkan tag dan atribut keamanan kustom.
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Membaca kondisi blob |
| Sumber atribut | Kepala sekolah |
| Karakteristik | <atributset>_<kunci> |
| Pengoperasi | StringEquals |
| Opsi | Karakteristik |
| Sumber atribut | Sumber Daya |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] |
| Kunci | <kunci> |
| Kondisi #2 | Pengaturan |
|---|---|
| Tindakan |
Menulis pada blob dengan tag indeks blob Menulis pada blob dengan tag indeks blob |
| Sumber atribut | Kepala sekolah |
| Karakteristik | <attributeset>_<key> |
| Pengoperasi | StringEquals |
| Opsi | Karakteristik |
| Sumber atribut | Permohonan |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] |
| Kunci | <kunci> |
Contoh: Membaca blob berdasarkan tag indeks blob dan atribut keamanan kustom multinilai
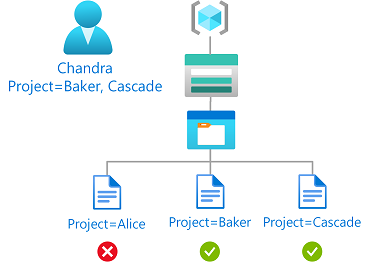
Kondisi ini memungkinkan akses baca ke blob jika pengguna memiliki atribut keamanan kustom dengan nilai apa pun yang cocok dengan tag indeks blob.
Misalnya, jika Chandra memiliki atribut Project dengan nilai-nilai Baker dan Cascade, dia hanya dapat membaca blob dengan tag indeks Project=Baker atau Project=Cascade.
Anda harus menambahkan kondisi ini ke penetapan peran apa pun yang menyertakan tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Untuk informasi selengkapnya, lihat Mengizinkan akses baca ke blob berdasarkan tag dan atribut keamanan kustom.
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan portal Microsoft Azure.
| Kondisi #1 | Pengaturan |
|---|---|
| Tindakan | Membaca kondisi blob |
| Sumber atribut | Sumber Daya |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] |
| Kunci | <kunci> |
| Pengoperasi | ForAnyOfAnyValues:StringEquals |
| Opsi | Karakteristik |
| Sumber atribut | Kepala sekolah |
| Karakteristik | <setsifat>_<kunci> |
Atribut lingkungan
Bagian ini mencakup contoh yang menunjukkan cara membatasi akses ke objek berdasarkan lingkungan jaringan atau tanggal dan waktu saat ini.
Contoh: Mengizinkan akses baca ke blob setelah tanggal dan waktu tertentu
Kondisi ini memungkinkan akses baca ke kontainer blob container1 hanya setelah pukul 13.00 pada tanggal 1 Mei 2023 Waktu Universal Terkoordinasi (UTC).
Ada dua tindakan potensial untuk membaca blob yang ada. Untuk membuat kondisi ini efektif bagi prinsipal yang memiliki beberapa penetapan peran, Anda harus menambahkan kondisi ini ke semua penetapan peran yang menyertakan salah satu tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
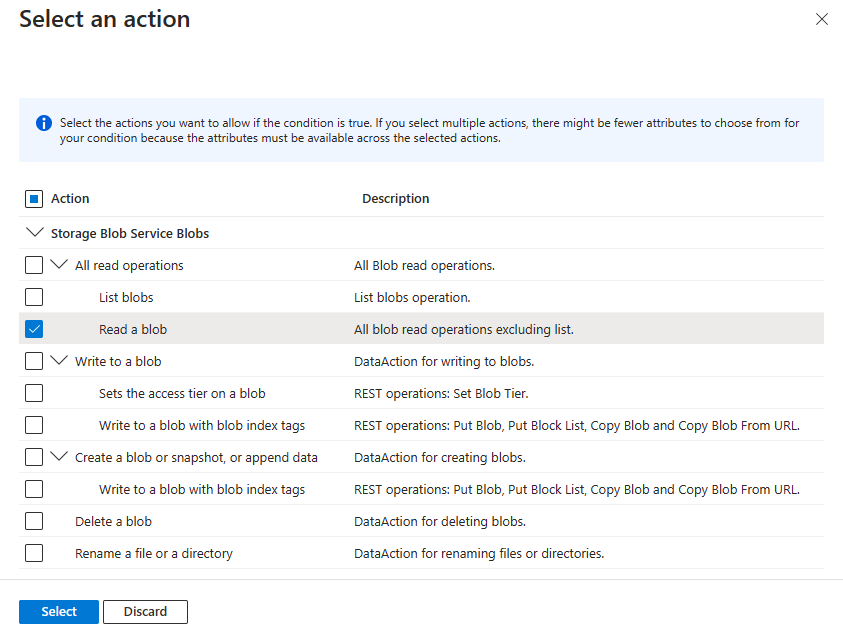
Menambahkan tindakan
Pilih Tambahkan tindakan, lalu pilih hanya suboperasi Baca blob seperti yang diperlihatkan dalam tabel berikut ini.
| Tindakan | Suboperasi |
|---|---|
| Semua operasi baca | Membaca objek blob |
Jangan pilih tindakan Semua operasi baca tingkat atas atau suboperasi lainnya seperti yang ditunjukkan pada gambar berikut:
Bangun Ekspresi
Gunakan nilai dalam tabel berikut untuk menyusun bagian ekspresi kondisi:
Pengaturan Nilai Sumber atribut Sumber Daya Karakteristik Nama kontainer Pengoperasi StringEquals Nilai container1Operator logika 'AND' Sumber atribut Lingkungan Karakteristik UtcNow Pengoperasi DateTimeGreaterThan Nilai 2023-05-01T13:00:00.000Z
Gambar berikut menunjukkan kondisi setelah pengaturan dimasukkan ke portal Microsoft Azure. Anda harus mengelompokkan ekspresi untuk memastikan evaluasi yang benar.
Contoh: Mengizinkan akses ke blob dalam kontainer tertentu dari subnet tertentu
Kondisi ini memungkinkan akses baca, tulis, tambahkan, dan hapus ke blob container1 hanya dari subnet default di jaringan virtualnetwork1virtual . Untuk menggunakan atribut Subnet dalam contoh ini, subnet harus mengaktifkan titik akhir layanan untuk Azure Storage.
Ada lima tindakan potensial untuk membaca, menulis, menambahkan, dan menghapus akses ke blob yang ada. Untuk membuat kondisi ini efektif bagi prinsipal yang memiliki beberapa penetapan peran, Anda harus menambahkan kondisi ini ke semua penetapan peran yang menyertakan salah satu tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/delete |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Menambahkan tindakan
Pilih Tambahkan tindakan, lalu pilih hanya tindakan tingkat atas yang diperlihatkan dalam tabel berikut ini.
| Tindakan | Suboperasi |
|---|---|
| Semua operasi baca | N/a |
| Menulis ke penyimpanan blob | N/a |
| Membuat blob atau rekam jepret, atau menambahkan data | N/a |
| Menghapus objek blob | N/a |
Jangan pilih suboperasi individual seperti yang ditunjukkan pada gambar berikut:
Bangun Ekspresi
Gunakan nilai dalam tabel berikut untuk menyusun bagian ekspresi kondisi:
Pengaturan Nilai Sumber atribut Sumber Daya Karakteristik Nama kontainer Pengoperasi StringEquals Nilai container1Operator logika 'AND' Sumber atribut Lingkungan Karakteristik Subnet Pengoperasi StringEqualsIgnoreCase Nilai /subscriptions/<your subscription id>/resourceGroups/<resource group name>/providers/Microsoft.Network/virtualNetworks/virtualnetwork1/subnets/default
Gambar berikut menunjukkan kondisi setelah pengaturan dimasukkan ke portal Microsoft Azure. Anda harus mengelompokkan ekspresi untuk memastikan evaluasi yang benar.
Contoh: Memerlukan akses tautan privat untuk membaca blob dengan sensitivitas tinggi
Kondisi ini mengharuskan permintaan untuk membaca blob di mana tag indeks sensitivitas memiliki nilai high harus melewati tautan privat (tautan privat apa pun). Ini berarti semua upaya untuk membaca blob yang sangat sensitif dari internet publik tidak akan diizinkan. Pengguna dapat membaca blob dari internet publik yang memiliki sensitivitas yang diatur ke beberapa nilai selain high.
Tabel kebenaran untuk kondisi sampel ABAC ini mengikuti:
| Perbuatan | Kepekaan | Tautan privat | Akses |
|---|---|---|---|
| Membaca blob | tinggi | Ya | Diperbolehkan |
| Membaca blob | tinggi | Tidak. | Tidak Diperbolehkan |
| Membaca blob | tidak tinggi | Ya | Diperbolehkan |
| Membaca objek blob | tidak tinggi | Tidak. | Diperbolehkan |
Ada dua tindakan potensial untuk membaca blob yang ada. Untuk membuat kondisi ini efektif bagi prinsipal yang memiliki beberapa penetapan peran, Anda harus menambahkan kondisi ini ke semua penetapan peran yang menyertakan salah satu tindakan berikut.
Tindakan Catatan Microsoft.Storage/storageAccounts/blobServices/containers/blobs/readMicrosoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/actionTambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan.
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan editor kondisi visual di portal Microsoft Azure.
Menambahkan tindakan
Pilih Tambahkan tindakan, lalu pilih hanya suboperasi Baca blob seperti yang diperlihatkan dalam tabel berikut ini.
| Tindakan | Suboperasi |
|---|---|
| Semua operasi baca | Membaca objek blob |
Jangan pilih tindakan Semua operasi baca tingkat atas dari suboperasi lain seperti yang ditunjukkan pada gambar berikut:
Bangun Ekspresi
Gunakan nilai dalam tabel berikut untuk menyusun bagian ekspresi kondisi:
Kelompok Pengaturan Nilai Grup #1 Sumber atribut Sumber Daya Karakteristik Tag indeks blob [Nilai dalam kunci] Kunci sensitivityPengoperasi StringEquals Nilai highOperator logika DAN Sumber atribut Lingkungan Karakteristik Apakah tautan privat Pengoperasi BoolEquals Nilai TrueAkhir Grup #1 Operator logika 'OR' Sumber atribut Sumber Daya Karakteristik Tag indeks blob [Nilai dalam kunci] Kunci sensitivityPengoperasi StringNotEquals Nilai high
Gambar berikut menunjukkan kondisi setelah pengaturan dimasukkan ke portal Microsoft Azure. Anda harus mengelompokkan ekspresi untuk memastikan evaluasi yang benar.
Contoh: Izinkan akses ke kontainer hanya dari titik akhir privat tertentu
Kondisi ini mengharuskan semua operasi baca, tulis, tambahkan, dan hapus untuk blob dalam kontainer penyimpanan bernama container1 dibuat melalui titik akhir privat bernama privateendpoint1. Untuk semua kontainer lain yang tidak bernama container1, akses tidak perlu melalui titik akhir privat.
Ada lima tindakan potensial untuk membaca, menulis, dan menghapus blob yang ada. Untuk membuat kondisi ini efektif bagi prinsipal yang memiliki beberapa penetapan peran, Anda harus menambahkan kondisi ini ke semua penetapan peran yang menyertakan salah satu tindakan berikut.
| Tindakan | Catatan |
|---|---|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/write |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/add/action |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/delete |
|
Microsoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/action |
Tambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan. Tambahkan jika akun penyimpanan yang disertakan dalam kondisi ini mengaktifkan namespace hierarkis atau mungkin diaktifkan di masa mendatang. |
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan editor kondisi visual di portal Microsoft Azure.
Menambahkan tindakan
Pilih Tambahkan tindakan, lalu pilih hanya tindakan tingkat atas yang diperlihatkan dalam tabel berikut ini.
| Tindakan | Suboperasi |
|---|---|
| Semua operasi baca | N/a |
| Menulis ke penyimpanan blob | N/a |
| Membuat blob atau rekam jepret, atau menambahkan data | N/a |
| Menghapus objek blob | N/a |
Jangan pilih suboperasi individual seperti yang ditunjukkan pada gambar berikut:
Bangun Ekspresi
Gunakan nilai dalam tabel berikut untuk menyusun bagian ekspresi kondisi:
Kelompok Pengaturan Nilai Grup #1 Sumber atribut Sumber Daya Karakteristik Nama kontainer Pengoperasi StringEquals Nilai container1Operator logika DAN Sumber atribut Lingkungan Karakteristik Titik akhir privat Pengoperasi StringEqualsIgnoreCase Nilai /subscriptions/<your subscription id>/resourceGroups/<resource group name>/providers/Microsoft.Network/privateEndpoints/privateendpoint1Akhir Grup #1 Operator logika 'OR' Sumber atribut Sumber Daya Karakteristik Nama kontainer Pengoperasi StringNotEquals Nilai container1
Gambar berikut menunjukkan kondisi setelah pengaturan dimasukkan ke portal Microsoft Azure. Anda harus mengelompokkan ekspresi untuk memastikan evaluasi yang benar.
Contoh: Izinkan akses pembacaan ke data blob yang sangat sensitif, hanya dari titik akhir privat tertentu dan oleh pengguna yang telah diberi tag akses
Kondisi ini mengharuskan bahwa blob dengan tag indeks sensitivitas yang diatur ke high hanya dapat dibaca oleh pengguna dengan nilai yang sesuai untuk atribut keamanan sensitivitas mereka. Selain itu, mereka harus diakses melalui titik akhir privat bernama privateendpoint1. Blob yang memiliki nilai berbeda untuk tag sensitivitas dapat diakses melalui titik akhir lain atau Internet.
Ada dua tindakan potensial untuk membaca blob yang ada. Untuk membuat kondisi ini efektif bagi prinsipal yang memiliki beberapa penetapan peran, Anda harus menambahkan kondisi ini ke semua penetapan peran yang menyertakan salah satu tindakan berikut.
Tindakan Catatan Microsoft.Storage/storageAccounts/blobServices/containers/blobs/readMicrosoft.Storage/storageAccounts/blobServices/containers/blobs/runAsSuperUser/actionTambahkan jika definisi peran menyertakan tindakan ini, misalnya Pemilik Data Blob Penyimpanan.
Kondisi dapat ditambahkan ke penetapan peran menggunakan portal Microsoft Azure atau Azure PowerShell. Portal memiliki dua alat untuk membangun kondisi ABAC - editor visual dan editor kode. Anda dapat beralih di antara kedua editor di portal Microsoft Azure untuk melihat kondisi Anda dalam tampilan yang berbeda. Beralih antara tab Editor visual dan tab Editor kode untuk melihat contoh editor portal pilihan Anda.
Berikut adalah pengaturan untuk menambahkan kondisi ini menggunakan editor kondisi visual di portal Microsoft Azure.
Menambahkan tindakan
Pilih Tambahkan tindakan, lalu pilih hanya suboperasi Baca blob seperti yang diperlihatkan dalam tabel berikut ini.
| Tindakan | Suboperasi |
|---|---|
| Semua operasi baca | Membaca objek blob |
Jangan pilih tindakan tingkat atas seperti yang ditunjukkan pada gambar berikut:
Bangun Ekspresi
Gunakan nilai dalam tabel berikut untuk menyusun bagian ekspresi kondisi:
| Kelompok | Pengaturan | Nilai |
|---|---|---|
| Grup #1 | ||
| Sumber atribut | Kepala sekolah | |
| Karakteristik | <attributeset>_<key> | |
| Pengoperasi | StringEquals | |
| Opsi | Karakteristik | |
| Operator logika | DAN | |
| Sumber atribut | Sumber Daya | |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] | |
| Kunci | <kunci> | |
| Operator logika | DAN | |
| Sumber atribut | Lingkungan | |
| Karakteristik | Titik akhir privat | |
| Pengoperasi | StringEqualsIgnoreCase | |
| Nilai | /subscriptions/<your subscription id>/resourceGroups/<resource group name>/providers/Microsoft.Network/privateEndpoints/privateendpoint1 |
|
| Akhir Grup #1 | ||
| Operator logika | 'OR' | |
| Sumber atribut | Sumber Daya | |
| Karakteristik | Tag indeks blob [Nilai dalam kunci] | |
| Kunci | sensitivity |
|
| Pengoperasi | StringNotEquals | |
| Nilai | high |
Gambar berikut menunjukkan kondisi setelah pengaturan dimasukkan ke portal Microsoft Azure. Anda harus mengelompokkan ekspresi untuk memastikan evaluasi yang benar.