Enable advanced API security features using Microsoft Defender for Cloud
APPLIES TO: Developer | Basic | Basic v2 | Standard | Standard v2 | Premium
Defender for APIs, a capability of Microsoft Defender for Cloud, offers full lifecycle protection, detection, and response coverage for APIs that are managed in Azure API Management. The service empowers security practitioners to gain visibility into their business-critical APIs, understand their security posture, prioritize vulnerability fixes, and detect active runtime threats within minutes.
Note
Currently, this feature isn't available in workspaces.
Capabilities of Defender for APIs include:
- Identify external, unused, or unauthenticated APIs
- Classify APIs that receive or respond with sensitive data
- Apply configuration recommendations to strengthen the security posture of APIs and API Management services
- Detect anomalous and suspicious API traffic patterns and exploits of OWASP API top 10 vulnerabilities
- Prioritize threat remediation
- Integrate with SIEM systems and Defender Cloud Security Posture Management
This article shows how to use the Azure portal to enable Defender for APIs from your API Management instance and view a summary of security recommendations and alerts for onboarded APIs.
Plan limitations
- Currently, Defender for APIs discovers and analyzes REST APIs only.
- Defender for APIs currently doesn't onboard APIs that are exposed using the API Management self-hosted gateway or managed using API Management workspaces.
- Some ML-based detections and security insights (data classification, authentication check, unused and external APIs) aren't supported in secondary regions in multi-region deployments. Defender for APIs relies on local data pipelines to ensure regional data residency and improved performance in such deployments.
Prerequisites
- At least one API Management instance in an Azure subscription. Defender for APIs is enabled at the level of an Azure subscription.
- One or more supported APIs must be imported to the API Management instance.
- Role assignment to enable the Defender for APIs plan.
- Contributor or Owner role assignment on relevant Azure subscriptions, resource groups, or API Management instances that you want to secure.
Onboard to Defender for APIs
Onboarding APIs to Defender for APIs is a two-step process: enabling the Defender for APIs plan for the subscription, and onboarding unprotected APIs in your API Management instances.
Tip
You can also onboard to Defender for APIs directly in the Defender for Cloud interface, where more API security insights and inventory experiences are available.
Enable the Defender for APIs plan for a subscription
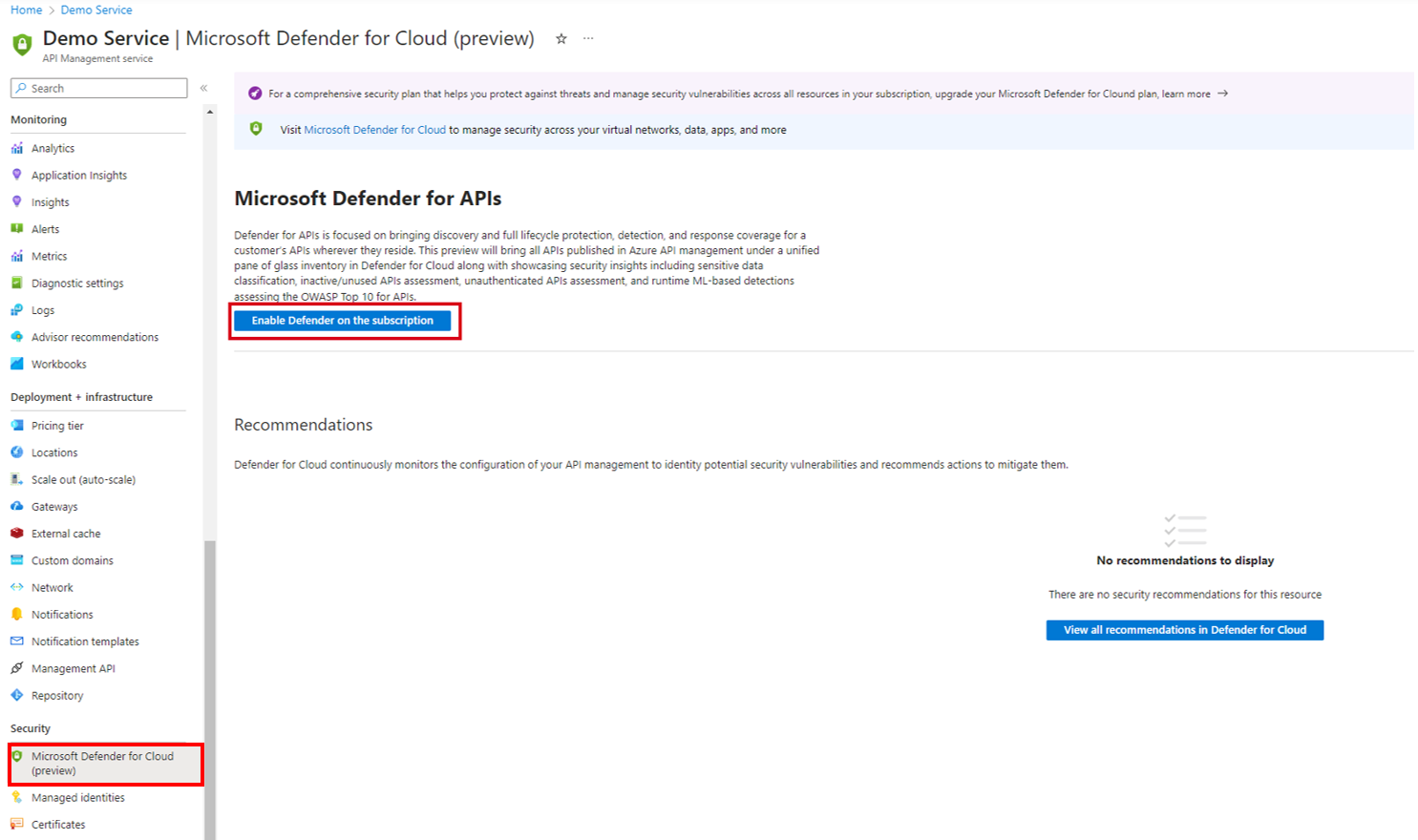
Sign in to the portal, and go to your API Management instance.
In the left menu, select Microsoft Defender for Cloud.
Select Enable Defender on the subscription.
On the Defender plan page, select On for the APIs plan.
Select Save.
Onboard unprotected APIs to Defender for APIs
Caution
Onboarding APIs to Defender for APIs may increase compute, memory, and network utilization of your API Management instance, which in extreme cases may cause an outage of the API Management instance. Do not onboard all APIs at one time if your API Management instance is running at high utilization. Use caution by gradually onboarding APIs, while monitoring the utilization of your instance (for example, using the capacity metric) and scaling out as needed.
In the portal, go back to your API Management instance.
In the left menu, select Microsoft Defender for Cloud.
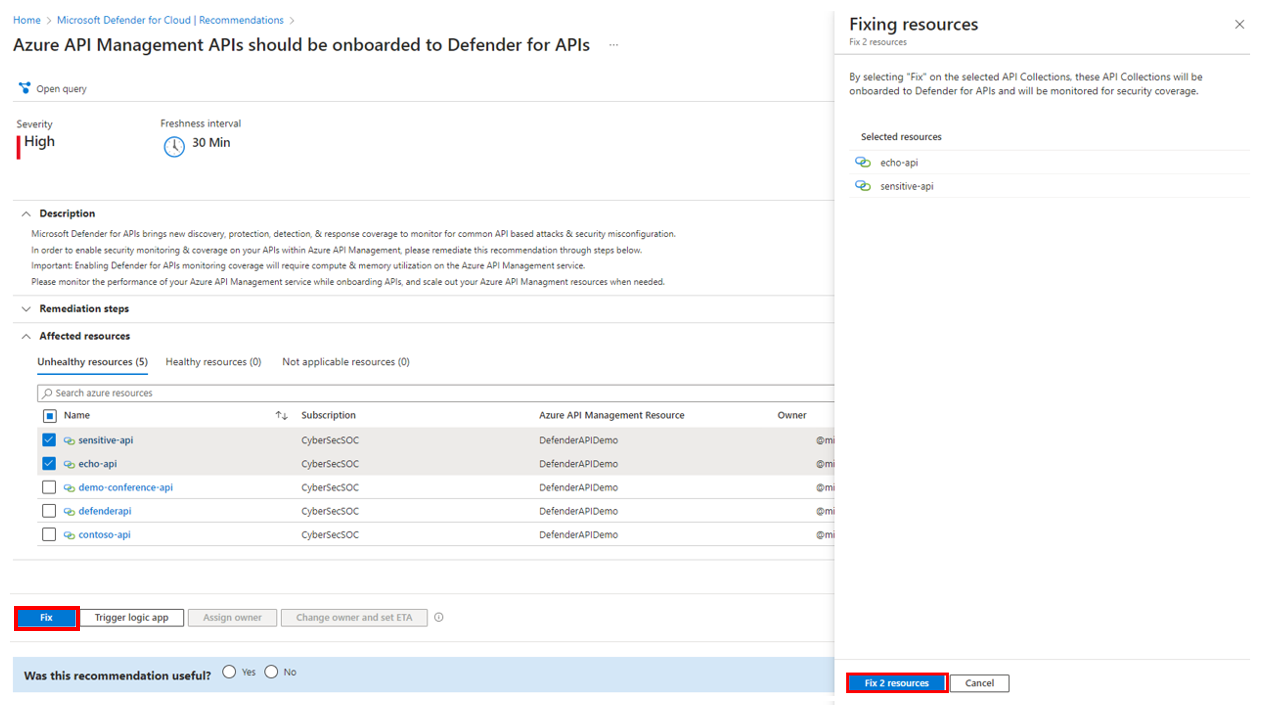
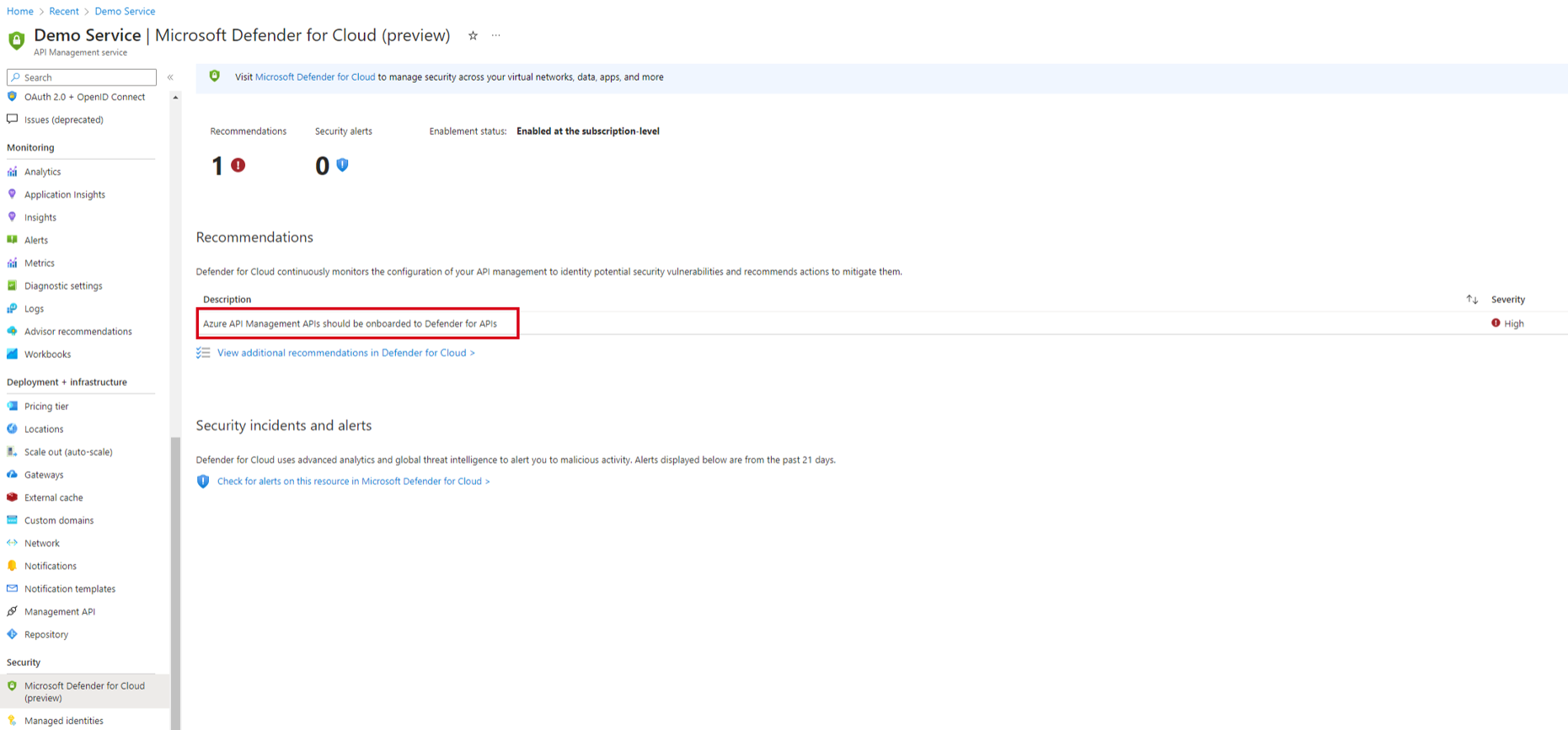
Under Recommendations, select Azure API Management APIs should be onboarded to Defender for APIs.
On the next screen, review details about the recommendation:
- Severity
- Refresh interval for security findings
- Description and remediation steps
- Affected resources, classified as Healthy (onboarded to Defender for APIs), Unhealthy (not onboarded), or Not applicable, along with associated metadata from API Management
Note
Affected resources include API collections (APIs) from all API Management instances under the subscription.
From the list of Unhealthy resources, select the API(s) that you wish to onboard to Defender for APIs.
Track the status of onboarded resources under Notifications.
Note
Defender for APIs takes 30 minutes to generate its first security insights after onboarding an API. Thereafter, security insights are refreshed every 30 minutes.
View security coverage
After you onboard the APIs from API Management, Defender for APIs receives API traffic that will be used to build security insights and monitor for threats. Defender for APIs generates security recommendations for risky and vulnerable APIs.
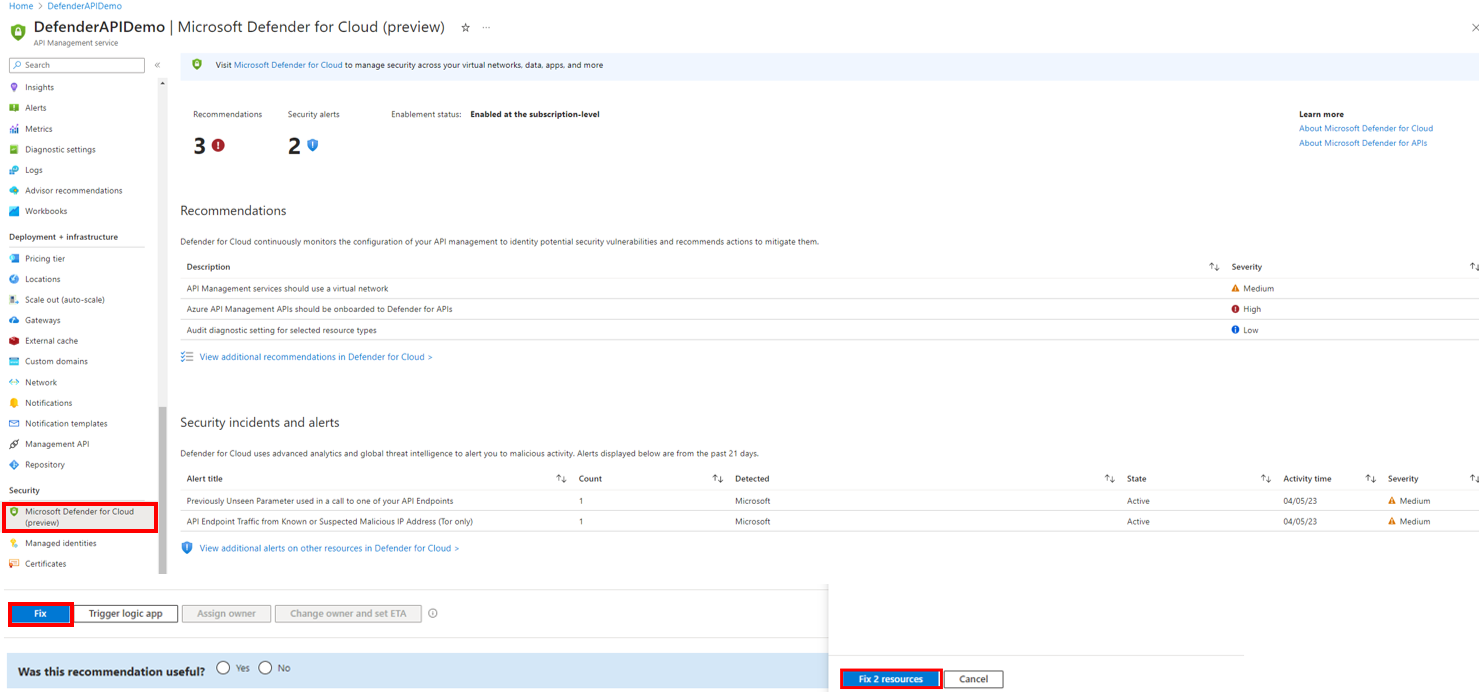
You can view a summary of all security recommendations and alerts for onboarded APIs by selecting Microsoft Defender for Cloud in the menu for your API Management instance:
In the portal, go to your API Management instance and select Microsoft Defender for Cloud from the left menu.
Review Recommendations and Security insights and alerts.
For the security alerts received, Defender for APIs suggests necessary steps to perform the required analysis and validate the potential exploit or anomaly associated with the APIs. Follow the steps in the security alert to fix and return the APIs to healthy status.
Offboard protected APIs from Defender for APIs
You can remove APIs from protection by Defender for APIs by using Defender for Cloud in the portal. For more information, see Manage your Defender for APIs deployment.
Next steps
- Learn more about Defender for Cloud
- Learn more about API findings, recommendations, and alerts in Defender for APIs Learn how to build a comprehensive API security strategy
- Learn how to upgrade and scale an API Management instance